Malicious and High-Risk Android Apps Hit 1 Million: Where Do We Go from Here?
In 2012, we predicted that the number of malicious and high-risk Android apps would reach 1 million this year. That came true with still three months to spare before the end of 2013.
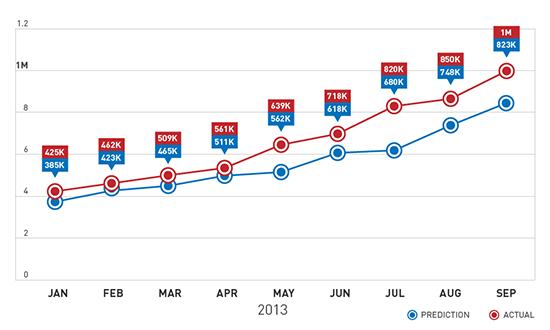
What 1 Million Means
Based on Trend Micro™ Mobile App Reputation data, 80% of the 1 million apps are malicious in nature. Two-thirds of these are premium service abusers, malicious apps that subscribe devices to high-cost services without user consent. The remaining 20% are high-risk apps that exhibit dubious behavior. Most of these apps are adware. They not only aggressively push ads but also steal information unique to the mobile device like serial number, OS version, and International Mobile Station Equipment Identity (IMEI) number.
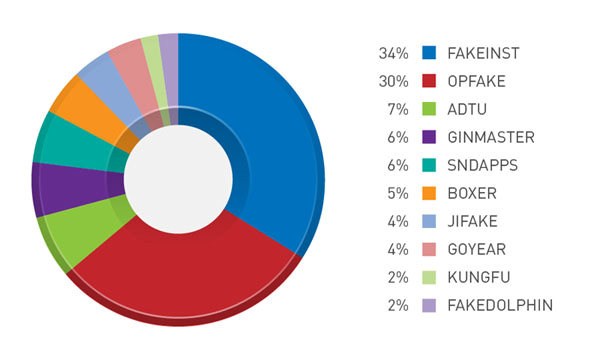
Figure 1: Top mobile malware families
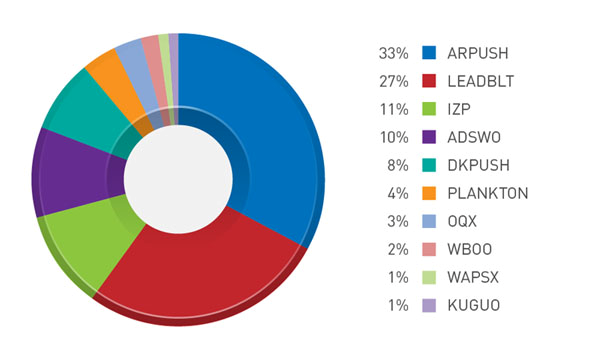
Figure 2: Top mobile adware families
Google says that dangerous Android malware are extremely rare and that only 0.5% of reported Android malware come from Google Play™. But this does not account for the malicious apps that users often mistake for legitimate apps in third-party download sites.
Some malicious apps also find their way to users’ mobile devices through other means like SMS or email spam as well as search engine results tainted with blackhat SEO. In prior incidents targeting Russian users, cybercriminals hid premium service abusers behind blackhat-SEO-tainted search results.
The fact that the mobile malware count reached the 1-million mark is something everyone should be concerned about. While the latest Android OS version may be secure, the platform still has a fragmentation problem. A large chunk of the Android user base still uses vulnerable OS versions. As of this writing, only 1.5% of all activated Android devices use the latest version of the OS, which makes the rest at risk of mobile malware infection.
Mobile Phishing and Other Web Threats
The tail end of 2012 exposed users to mobile Web threats, most notably mobile phishing. Financial service websites like PayPal were spoofed during the holiday season. This trend continued well into the first quarter of 2013 when phishing sites mimicking legitimate mobile banking websites asked for users’ log-in information and scanned copies of their government-issued IDs.
Other Web threats include scams using WhatsApp—the cross-platform messaging mobile app—as a social engineering lure. WhatsApp also served as a spam lure designed to trick users into downloading and installing premium service abusers. The spam lure works on both jail-broken iOS and vulnerable Android devices.
Since Web threats are not solely dependent on mobile device platforms, any mobile user with access to the Internet is at risk.
KSAPP, the Android Backdoor
Reports of a 1-million-strong smartphone botnet in China came to the fore at the beginning of 2013, causing a media uproar. Around the same time, we reported aboutANDROIDOS_KSAPP, a family of Android malware that receive and execute commands from a remote malicious user. This is the mobile equivalent of a backdoor. The malware can also automatically update its script to evade detection.
Fake Gaming Apps
2012 was plagued by fake gaming apps, which later became the status quo in the first quarter of 2013. Highly anticipated sequels to popular games like “Temple Run 2” were blatantly spoofed even before their release. Fake apps that supposedly offered cheats for the popular puzzle game app “Candy Crush Saga” also surfaced. These apps aggressively pushed ads and gathered personal information from infected devices.
Vulnerability Exploitation
Cybercriminals exploited Android vulnerabilities in the second quarter of 2013. They created OBAD, a malware family that constantly pesters mobile users to activate their device administrator features. This gives OBAD root privileges and lets cybercriminals gain full control of infected devices.
Halfway through 2013, 99% of Android devices were said to suffer from the Android Master Key vulnerability, which allowed malicious code to modify installed apps without user consent. In South Korea, cybercriminals exploited this vulnerability by creating a malicious update to a popular mobile banking app. The said update turned legitimate copies of the app into Trojans.
The rising trend of malicious apps taking advantage of Android vulnerabilities endangers the security of most Android users. As mentioned, the Android fragmentation issue still persists. As long as a considerable chunk of Android users are unable to upgrade their outdated OS versions, existing vulnerabilities will remain viable targets for cybercriminals.
FAKEBANK
Another threat to mobile banking this year was FAKEBANK. Unlike other mobile banking threats, FAKEBANK does not Trojanize legitimate banking apps. It instead imitates the mobile banking app the device owner uses. This technique is similar to that of PC banking Trojans that keep track of a user’s browsing habits then spoofs his banking website to steal his log-in credentials. FAKEBANK’s existence, along with this year’s other mobile banking threats, prove that cybercriminals see the mobile platform as a cash cow waiting to be milked.
After the 1 Million
After hitting the 1-million mark, the number of malicious and high-risk Android app detections is still rising. The volume will continue to rise alongside the release of new devices like smartwatches and new OS versions like KitKat.
New trends will also come to the fore. Fraud attacks will soon adopt a “trust chain” modus operandi wherein cybercriminals will exploit a user’s trusted contacts to get his friends to download malware. Attacks targeting financial services like mobile banking threats will become a much bigger problem. Cybercriminals will continue to target vulnerabilities and use advanced techniques to make malware detection and removal harder to do.
Surpassing the 1-million milestone means individuals and businesses that use the Android platform need to be even more cautious. Installing security solutions and enforcing usage policies should not be an exception, they should become the norm.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One