Calibrating Expansion: 2023 Annual Cybersecurity Report
Calibrating Expansion
2023 Annual Cybersecurity Report
Our continuous surveillance and research of the threat landscape in 2023 showed patterns suggesting that cybercriminals are learning to prioritize substance over size as they take advantage of the expanding attack surface. Our customer data shows increasing endpoint detections that suggest threat actors are calibrating their operations to deviate from big-batch attacks and instead focus on a narrower range of targets but with higher victim profiles for maximum gain with minimum effort. As they continue to double down on tried and tested techniques and find more ways to abuse legitimate processes for stealth, they are also delegating and streamlining operations, making rapid substitutions to takedowns — all of which result in constant, bolder, more operative schemes. SOCs and enterprises must refine their processes and protocols to make their defenses be able to combat persistence with efficiency.
Our cybersecurity annual report presents the most notable stories in 2023, together with usable data highlights from our telemetry and insights from experts on threats that cover ransomware, cloud and enterprise, the risk landscape, and advanced persistent threats (APT).
* * *
CAMPAIGNS
Cybercrime organizations expand scope and improve efficiency
Advanced persistent threats are dealing a one-two punch, with some gangs doubling down on tried and tested techniques while others expand and explore new tactics.
APT34 continues to make up for simple routines by rapidly creating new malware and tools allowing them to deploy successive cycles. Meanwhile, Pawn Storm launched a credential phishing campaign against various governments in Europe that can be related to some of the Net-NTLMv2 hash relay campaigns. Void Rabisu is also making its main malware ROMCOM backdoor leaner and meaner: they stripped it down, with additional components loaded with specificity to its targets — all while the gang encroaches on target areas usually associated to APT groups typically thought to be state-sponsored.
Meanwhile, Earth Lusca has expanded its Linux arsenal with SprySOCKS backdoor, and Earth Eastries uses Zingdoor as part of its routine to ensure that the backdoor cannot be unpacked easily, while PowerShell downgrade attacks and novel DLL sideloading combinations are used to evade detection.
The efficiency with which cybercriminal groups are evolving and adapting suggests that they are building an industry not unlike traditional organizations in size, revenue, and operations. Our study earlier this year details how cybercrime businesses are operating in the same frameworks as traditional businesses.
RANSOMWARE
Ransomware gangs enhance operations with efficient tactics, bolder schemes, and quick swaps
Ransomware groups are working smarter instead of harder: in 2023, several families have been observed maximizing remote and intermittent encryption, as well as abusing unmonitored virtual machines to bypass Endpoint Detection and Response (EDR).
Remote encryption
Observed in
• Akira
• BlackCat
• BlackMatter
• LockBit
• Royal
Intermittent encryption
Observed in
• NoEscape
• Ransomware Play
• BlackBasta
• Agenda
• BlackCat
VM abuse to bypass EDR
Observed in
• Akira
• BlackCat
Gangs are also launching bolder attacks: Prolific groups were some of the most active in 2023: Clop exploited major vulnerabilities, and BlackCat launched a new variant, while also making its extortion public by leveraging the Security and Exchange Commission’s 4-day disclosure requirement to incentivize its victim to communicate more quickly with them. They are making quick pivots too: After Qakbot’s takedown, BlackBasta turned to affiliate Water Curupira’s Pikabot to launch a spam campaign.
Meanwhile, major player Cerber reemerged by exploiting Atlassian Confluence vulnerability to deploy its payload, while previously known infostealers RedLine and Vidar are now also dropping ransomware payloads, suggesting that threat actors behind them are making their techniques multifunctional. While big fish LockBit continued to launch high-profile attacks in 2023, the gang struggles to maintain its previous glory after suffering from several logistical, technical, and reputational problems; as the new year rolled in, they launched a new version in an effort to stay relevant.
EMERGING THREATS
AI clears the way for amateur cybercriminals, creating novel playgrounds for seasoned actors
Imminent danger in emerging threats lies in innovations that enable day-to-day enterprise transactions and processes: application programming interfaces (API) face several security challenges that can be leveraged by malicious actors. Berkley Packet Filtering of BPF-enabled malware could be seen in the horizon, while our deep dive into exposed container registries revealed significant security gaps. Overall vendor security is under the microscope as distributed energy generation (DEG) grows more prominent, as well as Message Queuing Telemetry Transport (MQTT).
While large language models still have extensive limitations in fully automating malware creation, the speed of learning from previous prompts holds promise in adaptability and enhancing efficiency in the future. Though it still requires significant prompt engineering, error handling, model fine-tuning, and human supervision to produce usable output, with AI, it is becoming dangerously easier to be a cybercriminal as previous barriers such as language and coding skill are virtually broken.
AI in 2023, however, showed great promise in social engineering: its automation proved most useful in mining datasets for actionable information, while generative AI have made phishing virtually effortless with error-free and convincing messages as well as persuasive audio and video deepfakes.
42%
Of enterprise-scale organizations surveyed actively use AI in their businesses*
40%
Of respondents say their organizations will increase investment in AI**
1 in 5
Organizations report a skills gap to use AI or automation tools*
*IBM Global AI Adoption Index 2023
**The State of AI in 2023: McKinsey Global Surveys
RISK LANDSCAPE
Cybercriminals maximize post-pandemic interconnectivity and abuse legitimate tools
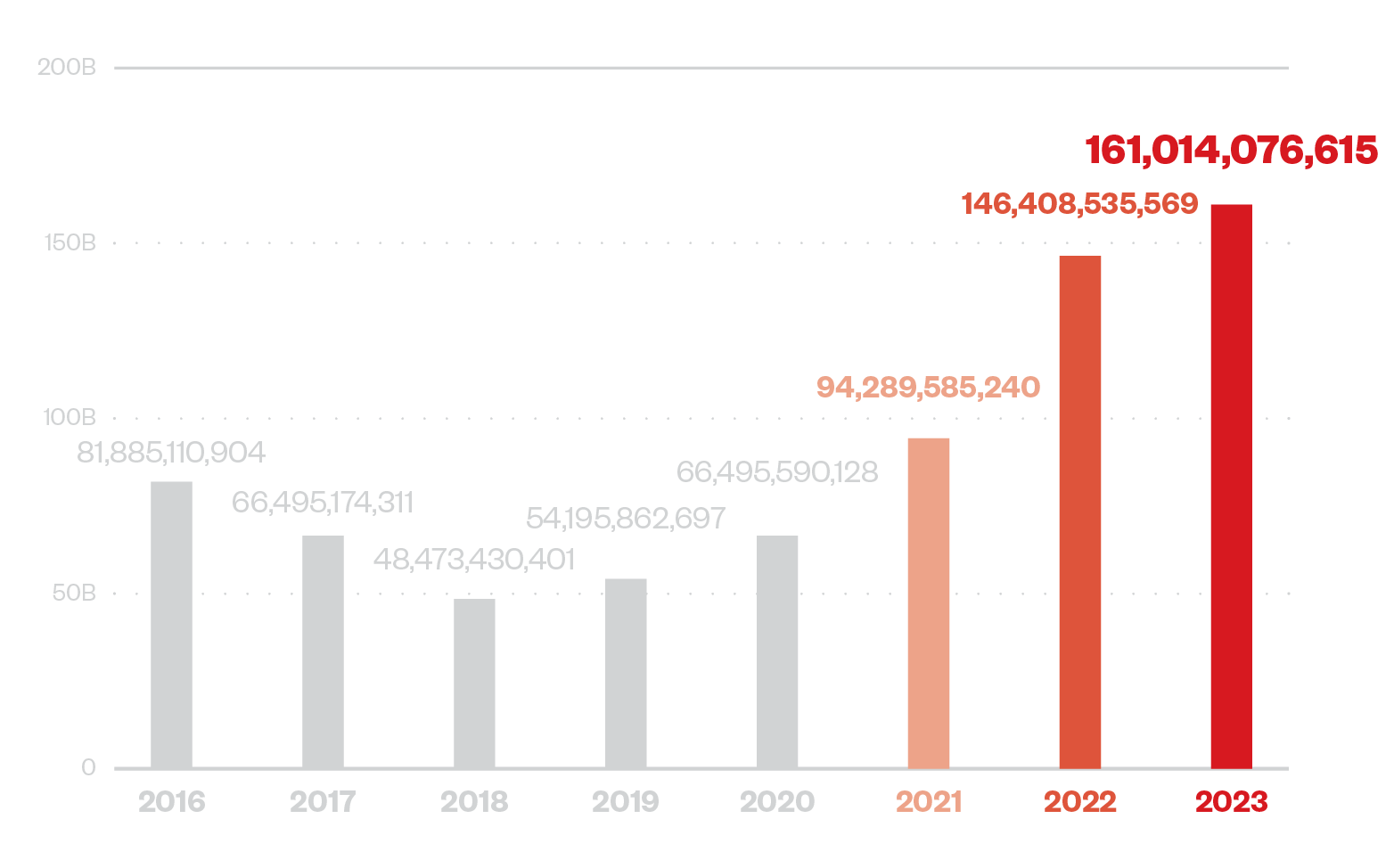
2023 continues the dramatic climb in Smart Protection Network (SPN) counts on overall threats blocked, peaking anew on the uptrend that started in the wake of the pandemic. A closer look at the downtrend on early detection filters (Email Reputation Service, Web Reputation Service) suggests that cybercriminals could be deprioritizing wider targets to focus on better infiltration as seen in the continuous surge in endpoint detections (File Reputation Service).
ERS
2022 79.9 B ↑
2023 73.9 B ↓
WRS
2022 2.5 B ↓
2023 2.4 B ↓
FRS
2022 60.9 B ↑
2023 82.1 B ↑
Vulnerabilities remain a huge concern for SOCs as 2023 headlines featured legitimate file-sharing services abused, while trusted methods of credential verification such as multi-factor authentication can be bypassed as in the case of EvilProxy attacks. Well-known messaging platforms, such as Skype and Teams, are also being utilized by cybercriminals, in this case DarkGate, to deliver VBA loader script to victims.
Meanwhile, threat actors are abusing legitimate processes, as in the case of AsyncRAT’s misuse of aspnet_compiler.exe. Infostealers RedLine and Vidar, as well as an attack that suggests the return of Genesis Market, are also abusing EV code signing for defense evasion. Personal and actionable data such as crypto wallets and browser and mail credentials continue to be the prime target for cybercriminals. Data shops in the dark web will remain a staple, with RedLine and Vidar coming out on top in in-the-wild popularity levels. Individuals and organizations should maximize tools that help keep your data and identity safe as life post-pandemic brings most transactions online.
THREAT LANDSCAPE IN BRIEF
161014076615
OVERALL NUMBER OF THREATS BLOCKED IN 2023
73.8B
BLOCKED EMAIL THREATS
2.3B
BLOCKED MALICIOUS URLs
82.1B
BLOCKED MALICIOUS FILES
87.5B
EMAIL REPUTATION QUERIES
4.1T
URL REPUTATION QUERIES
2.3T
FILE REPUTATION QUERIES
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One