Exposed Video Streams: How Hackers Abuse Surveillance Cameras
By: Trend Micro Forward-Looking Threat Research (FTR) Team
 Internet Protocol (IP) surveillance cameras afford certain conveniences in homes and businesses primarily owing to their accessibility. With these devices, it’s possible for, say, parents to remotely check on their children in their homes or company personnel to see what’s going on in and around their business premises. However, their usability tends to come at the expense of security, resulting in such issues as vulnerabilities and configuration errors. More seriously, this trade-off has also led to some consequences that we’ve observed, with hackers gaining access to cameras to record videos, selling access to cameras to other parties, or even using cameras to snoop around shops and scoop credit card information from unsuspecting customers.
Internet Protocol (IP) surveillance cameras afford certain conveniences in homes and businesses primarily owing to their accessibility. With these devices, it’s possible for, say, parents to remotely check on their children in their homes or company personnel to see what’s going on in and around their business premises. However, their usability tends to come at the expense of security, resulting in such issues as vulnerabilities and configuration errors. More seriously, this trade-off has also led to some consequences that we’ve observed, with hackers gaining access to cameras to record videos, selling access to cameras to other parties, or even using cameras to snoop around shops and scoop credit card information from unsuspecting customers.The matter of exposed surveillance cameras is, understandably, no concern
Despite the sensitivity of the images and information caught on exposed cameras, though, we believe that this activity is not the doing of sophisticated hackers. For one thing, services related to the abuse of IP surveillance cameras and other devices connected to the internet of things (IoT) are often advertised not in
Underground actors and script kiddies’ role
It appears that this activity is being done by hackers, whether experienced ones or script kiddies, for the sake of fun. Information on exposed cameras or cameras with known passwords is widely shared on the “Fun” sections of underground forums or in dedicated prank groups in certain social networks. In one post on a forum
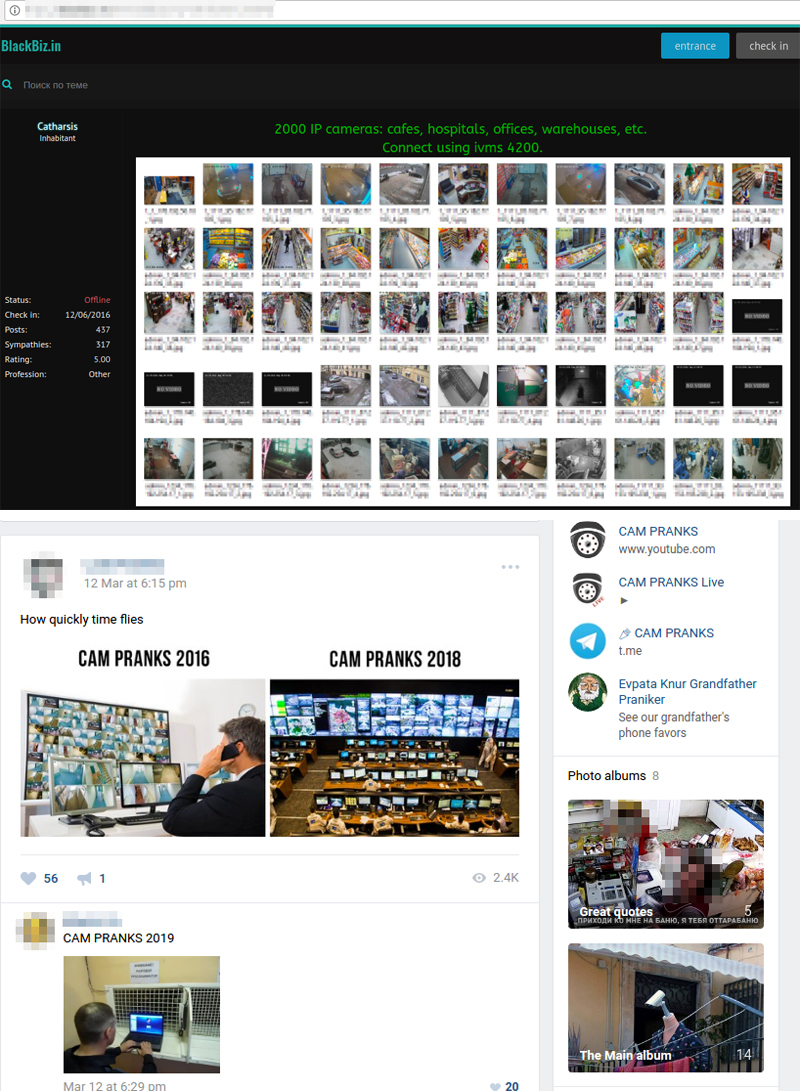
Figure 1. Sample posts dedicated to exposed cameras
Hackers usually perform camera pranks by playing different audio recordings or even interacting with people in the videos. Videos of the camera pranks are often shared on dedicated social networking groups, messaging app chatrooms, and YouTube channels, where they rack up hundreds of thousands, even millions, of views. Some pranks are done based on requests in comments on previous videos, with some having catchy titles such as “announcement of a nuclear war in the United States”
If we look into the script-kiddie-level area of the exposed camera market, specifically the dedicated groups on social networks, a couple of major points become apparent: Cameras that expose personal lives and streaming cameras from paid adult sites are in high demand, and cameras related to physical security are shared for free and used as warm-up or group promotion tools.
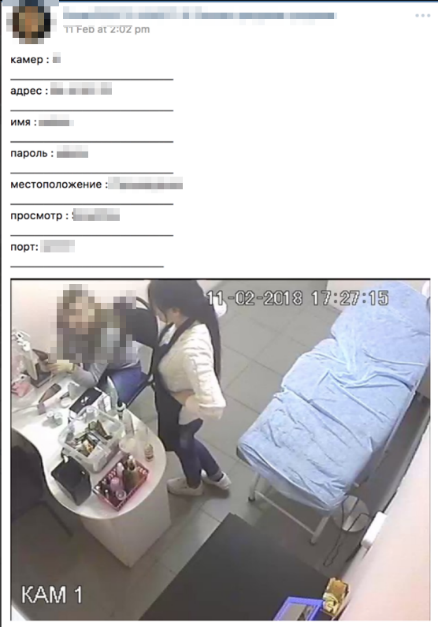
Figure 2. Sample post showing an exposed camera
Amid all the fun and games, however, there are underground actors and script kiddies who actually mean business. Apart from just pulling pranks at the expense of others, there is also a money-making side for these hackers. Effectively, some underground actors are helping script kiddies in automating the process of hacking into and exposing the video streams of cameras or even exploiting these IoT devices for malicious activities such as distributed denial-of-service (DDoS) attacks, covert cryptocurrency mining, and even financial crimes.
Software used
Most of the stages in the life cycle of exposed devices are automated to be done at scale. At some stages, well-known services or even legitimate pieces of software are used by the actors.
They often use their own software, like SquardCam, together with well-known penetration testing tools, like
Figure 3.
There are also step-by-step guides available on underground forums, dedicated groups in social networks, and YouTube channels. Because of the accessibility of these guides, almost anybody who wants to jump on the exposed camera bandwagon can easily do so.
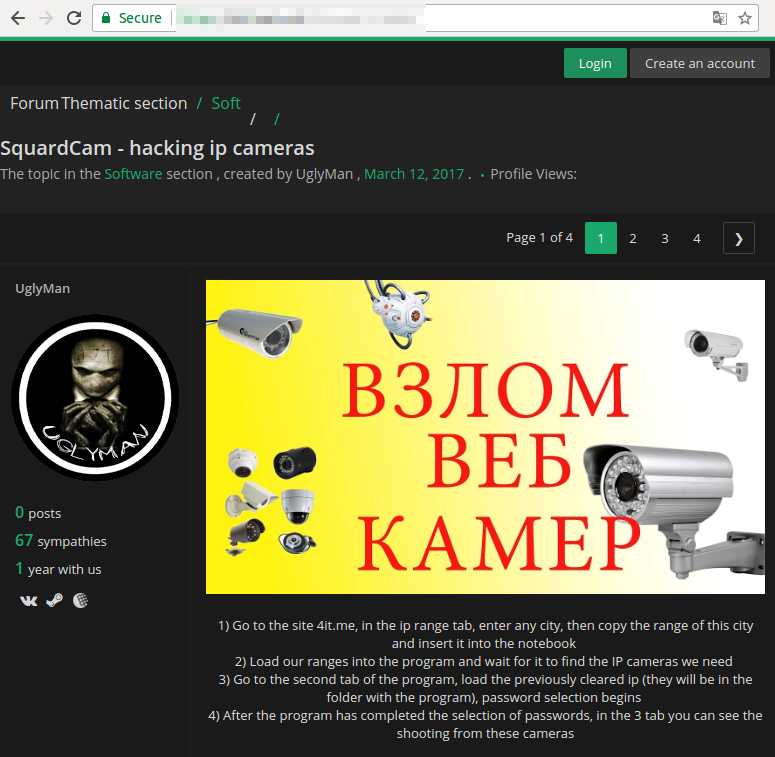
Figure 4. Posting for
Shopping process and opportunities
There are plenty of “camera shops” and paid groups dedicated to exposed cameras on social networks. One business model involves paid group memberships, which normally cost several U.S. dollars for each member. For example,
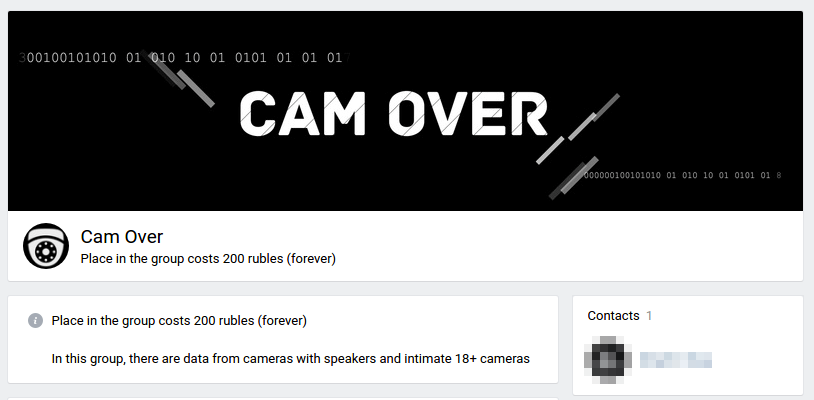
Figure 5. VK camera group offering paid membership
The prevalent approach, though, is the pay-per-camera (PPC) or pay-per-package (PPP) model. Under this model, prices usually range from US$1.5 to US$5 per
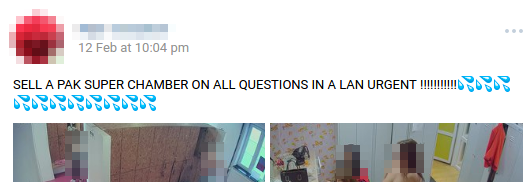
Figure 6. Posting for camera pack related to adult content streaming
Some camera shops and groups allow purchasing of prerecorded videos instead of just selling access to cameras. This service opens an opportunity for malicious actors to use exposed cameras to extort or blackmail victims, or to exploit the devices in other crimes and activities such as espionage and data exfiltration operations.
Possible use and consequences
Considering that IP cameras are IoT devices, there are several obvious ways they can be abused. Among these is cryptocurrency mining, which is a relatively innocuous way to monetize compromised resources. However, more serious consequences can arise from the use of vulnerable devices as intermediate points for attacks on third-party infrastructures, which may be launched to hide forensic traces, exfiltrate data, or since cameras usually have good internet connectivity, cause
Underground actors are well aware of the possible impact of exposed cameras on the security of private lives, financial transactions, and even critical infrastructures. In fact, opportunities to cause disruption with exposed cameras are often discussed among them, including efforts to target vulnerable devices and extort ransom from victims.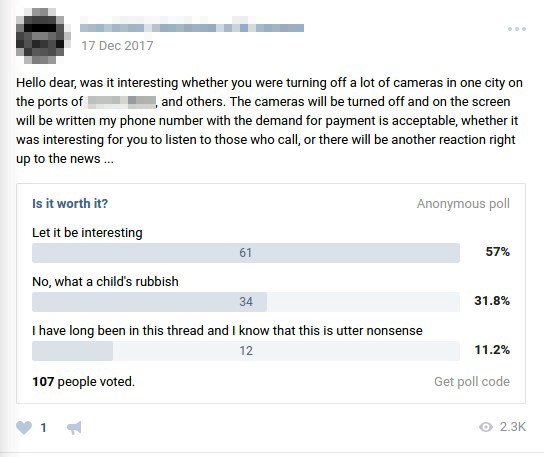
Figure 7. Poll for turning off cameras in a city and asking for ransom from victims
In the example
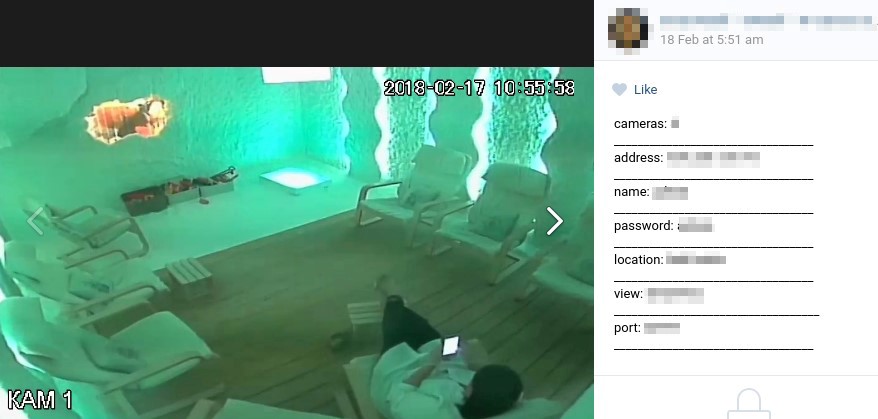
Figure 8. Posting for an exposed camera in a spa salon
Exposed cameras in places such as beauty salons, saunas, and medical institutions open a way to extort celebrities and other public personalities, whereby cybercriminals will threaten to publish their otherwise private videos unless they pay up.
Cameras in stores and financial institutions can also be hacked to expose personally identifiable information (PII) and payment details. For example, the exposed camera featured in the posting below is said to be suitable for collecting credit card data. There are also requests in underground forums directed at individuals who would be willing to watch videos from exposed cameras and document PII and payment details in exchange for about US$15 per second of video

Figure 9. Posting for
Of course, exposed cameras can affect the physical security of enterprise buildings and critical infrastructures. We’ve also found many exposed cameras in meeting rooms, managers’ rooms, security guards’ rooms, crisis management centers, and government buildings. It’s worth noting that in the exposed camera market, actors may choose to pay a certain amount to see someone naked, but they may be willing to pay several times more in order to have access to a board meeting room — considering the higher stakes associated with the sensitive information that can be gathered from such an exposed setting.
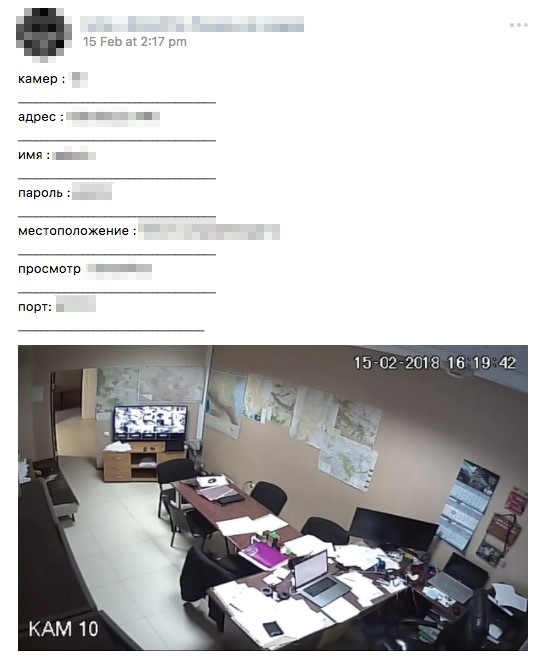
Figure 10. Posting for
Best practices against exposed cameras
Our findings serve as a reminder that manufacturers and vendors of cameras
Recommendations for device manufacturers and vendors include:
- Implementing a “security by design” approach, which requires security features and measures to be built into devices beginning in the earliest stages of the development process.
- Constantly monitoring the firmware and patching vulnerable system components, using firmware over-the-air (FOTA) updates if necessary.
- Applying secure boot to ensure that devices boot using only trusted software and to prevent compromised devices from functioning.
- Minimize the possibility of vulnerabilities being introduced into systems by incorporating the principle of least functionality, whereby any unused or unnecessary ports, protocols, and services are disabled.
- Enforcing the changing of devices’ default credentials, preferably upon initial setup by users.
For users, best practices include:
- Changing the default password of any new device with a strong password that has at least 15 characters and a mix of uppercase and lowercase letters, numbers, and special characters.
- Disabling unnecessary network ports or protocols such as Universal Plug and Play (UPnP), which can allow devices connected to the network to open ports to external networks without warning.
- Applying new firmware updates and security patches as soon as they’re available to minimize the chance of vulnerability exploits.
Because of a thriving underground market and
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One