The Future of Ransomware
 Download The Near and Far Future of Ransomware Business Models
Download The Near and Far Future of Ransomware Business Models

Organizations and governments have repeatedly examined whether their defenses, recovery preparations, and legislations are sufficient for ransomware attacks, and have become more active in responding to high-profile compromises. In response to these counteroffensives, ransomware groups have shown that specific triggers cause them to adjust their criminal business models. Law enforcement making more arrests and sanctions on cryptocurrency exchanges and ransomware gangs are just some of the most poignant developments that have prompted pivots.
In our research, “The Near and Far Future of Ransomware Business Models,” we break down the current state of ransomware in the cybercriminal landscape, the potential triggers of change for ransomware groups, and the possible directions these groups lead their respective illicit business models to. Notable offline geopolitical events such as the ongoing Russia-Ukraine war, or technological developments in infrastructure such as the expanding cloud adoption, can trigger an initial roster of gradual changes (evolutions) that can be furthered into more drastic transformations (revolutions). The next sections provide a brief overview of our findings and insights.
Brief ransomware history

Figure 1. Timeline of ransomware changes
In our research, ransomware’s history provides varying insights into the longevity and changes of cybercriminal business models. The timeline offers a perspective on specific points: changes on threat actors’ objectives of extortion, the mass market deployments to prioritize quantity in returns, law enforcement’s potential responses and actions, the development of currency and money laundering facilitation platforms vis-à-vis attacks’ expansion, and cybercriminals’ accumulation of skillsets and technical learning curves in relation to other cybercrimes, among others. Compared to traditional theft- and resale-based cybercrime business models in terms of popularity, this summarized history of ransomware ran in parallel and surpassed other business models through the years.
The differences in previous ransomware deployments’ goals wherein users were simply threatened and files were encrypted, to the targeted attacks with multiple extortion avenues, are staggering in terms of downtime, ransom, and recovery costs. At present, we consider the most dangerous ransomware attacks to involve targeted intrusions with ransomware payloads. From this standpoint, we see ransomware actors and their business models as having been anything but static. These attacks also shed light on the fact that defense solutions should not focus on the final payload’s delivery and execution but as far left to the infection chain as possible.
Ransomware today
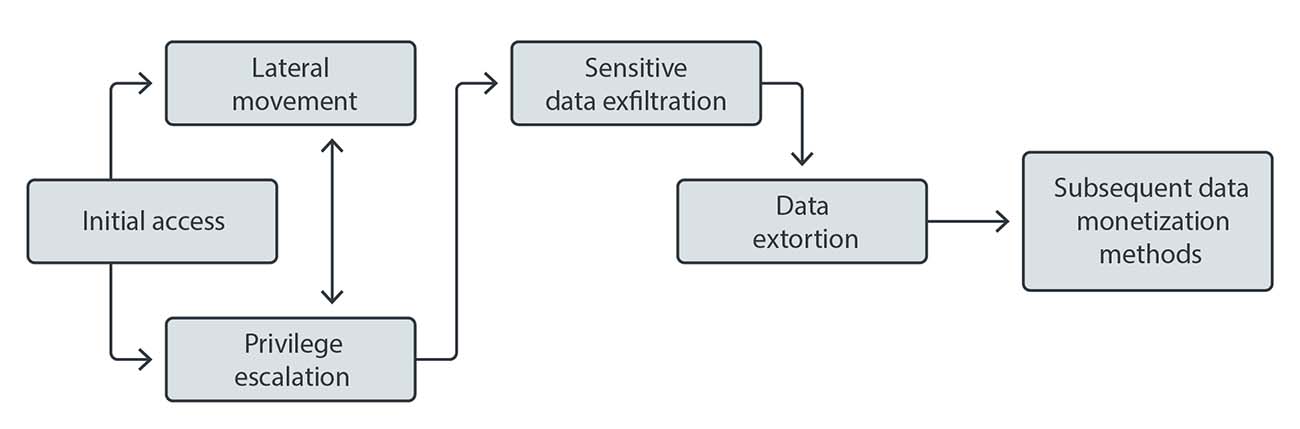
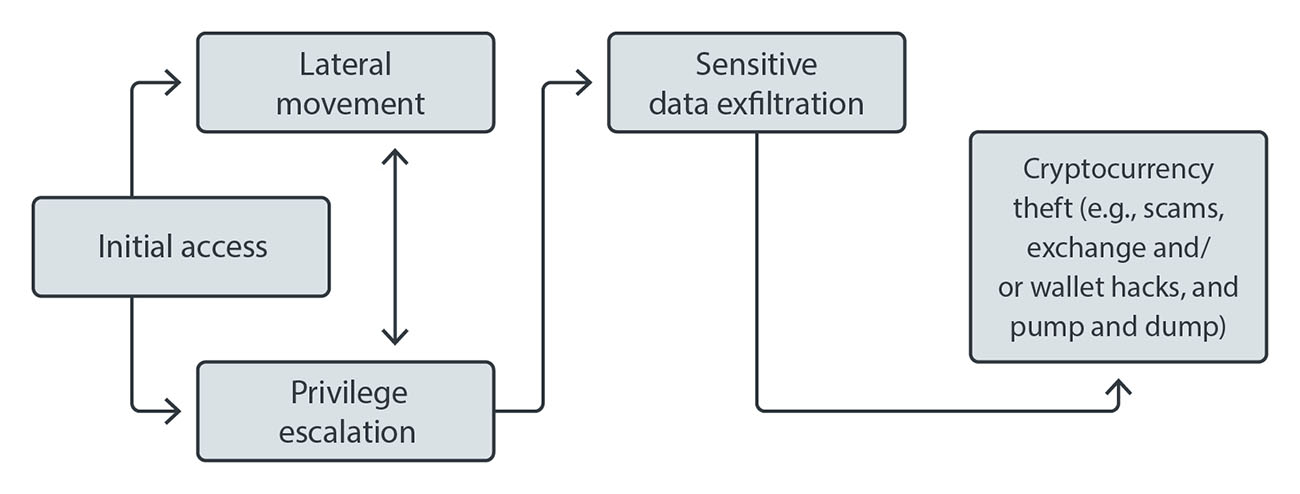
Today’s modern ransomware routines have building blocks that threat actors change at different points of their attack deployments, dependent on the research done on and the environment of the targets. Click on the buttons to know more about these building blocks.
Initial access
Entry into the network can be established in multiple ways: previous infections from mass emails with backdoor payloads, social engineering, vulnerabilities in internet-facing computer servers, and purchase of data from the underground, among other means.
Lateral movement
Attackers go deeper in the network for access to systems with standard or customized hacking tools.
Privilege escalation
Attackers go deeper in the network for access to systems with available or customized hacking tools.
Sensitive data exfiltration
Stolen data is analyzed to determine the ransom amount and checked whether the victim has cyber insurance policies in place.
Backup systems’ disruption
Attackers disrupt systems to lower the chances that victims can recover their files and processes from backup systems.
Ransomware payload deployment
Attackers deploy the ransomware payload to encrypt files and shut down systems.
Primary extortion methods
Attackers extort victims for more money on top of demanding payment to decrypt files, by threatening to release data to the public, launch distributed denial of service (DDoS) attacks, or shame them on social media.
Secondary extortion methods
Attackers extort victims for more money on top of demanding payment to decrypt files, by threatening to release data to the public, launch distributed denial of service (DDoS) attacks, or shame them on social media.
Money laundering
Attackers get their money via cryptocurrency once the ransom is paid, hiding the recipients’ real identities in the process.
Figure 2. Modern ransomware ecosystem’s building blocks
Key points for impact
Our research highlights five key points that can have significant effects on ransomware, but emphasize these three that will affect organizations, finance, law enforcement, and legislation. We believe these three can substantially push ransomware actors to further blur the lines of cybercrime and real world threats:
When compelled, ransomware actors will adapt and adopt other criminal business models – online or offline – that monetize initial access, such as short and distort scheme or other forms of stock fraud, business email compromise (BEC), and cryptocurrency theft, among others.
Defending against initial access brokers and arresting them will be key in the fight against ransomware.
Sanctions, cloud adoption, and the hardening of networks will trigger ransomware actors to evolve but not revolutionize their business model.
The next sections of this overview will further discuss these points for impact. The remaining key points affect cybersecurity and organizations on the technical level, and we briefly go over these topics in our blog entry, “Ransomware Business Models: Future Pivots and Trends”. For a summary of the business insights and other key points that we identified, download our executive primer.
Triggers
Much like business owners, ransomware actors consider themselves entrepreneurs despite their venture’s illegal nature. Hence, changes surrounding their current disposition can push them to rethink their respective business models. We list some of the triggers that can spark the gradual changes (evolutions) and radical deviations (revolutions) in the ransomware landscape. For the full list, download our report here.
Increase in Successful Law Enforcement Activities Against Ransomware Groups
A well-concerted and simultaneous takedown of ransomware groups can be a trigger for ransomware groups to change their illicit business models. Considering government announcements that more resources would be allocated for pursuing these groups, a successful and collaborative implementation from intelligence agencies, security researchers, and international law enforcement can cause paranoia among groups yet to be apprehended. On the opposite end of the spectrum, a failure from law enforcement to arrest all members of one ransomware group can result in bolder ransomware attacks as the remaining members rise up the ranks.
Government Regulations on Cryptocurrency
The creation and popularity of cryptocurrency undeniably made a mark for ransomware groups thanks to the anonymity it offers, as well as for the ease in cross-border transfers it allows. Regulating cryptocurrencies can make a dent and significantly reduce the monetary incentives for ransomware attackers, and this is already being considered by governments worldwide. Despite legislations’ concerns on cryptocurrency regulation centered on stabilizing markets and improving money flows, other crimes surrounding cryptocurrencies, such as money laundering, will be affected and could cause ransomware groups to move to other criminal activities.
Ransomware Groups’ Poor Operations Security That Result in Compromise
Known ransomware as a service (RaaS) groups such as REvil and Conti have been reported to have multiple operational security (OpSec) mistakes, allowing security researchers to infiltrate and observe groups’ servers and networks on multiple occasions. Some of these breaches may have hindered law enforcements’ active investigations, and while none of these reported infiltrations have led to arrests, groups shut down operations when they realize they have been hacked. This could lead them to either rebuild their operations’ infrastructure from scratch or lead them to find another criminal business model altogether.
Evolutions
Gradual changes from the current ransomware models will result as reactions to various developments, a seemingly circulatory cycle as legitimate entities act on previous ransomware attacks and tweaks. In this section, we list three of the 10 small changes that can prompt ransomware business model variations. To find the full list and incidents where these insights were based on, download our report here.
Replacing the Ransomware Payload With Data Monetization
Shifting to the monetization of exfiltrated data can be an easy switch for these ransomware groups. They can work with data miners to sift through monetizable data in infected machines and servers during intrusion or after exfiltration. Many of the current RaaS groups already have the tools for these types of activities. Ransomware groups can also form new partnerships with other threat actors engaged in specific cybercriminal activities that can fully exploit specific information such as financial data, personal records, or strategic information.
While this activity has been one of the longest running business models among cybercriminals, ransomware actors have yet to include this as a staple in their respective operations. Despite this initially appearing as a step back to theft-based business models, the level of expertise these threat actors have gained in the last decade sets this strategic move apart from previous years’ extortion pivots: The wider experience in network intrusion and fast data triage have and will make these cybercriminals an even more significant threat than ever, potentially even more so than some automated malware previously documented. Pivoting to this direction will also allow them to stay under law enforcement’s radar as there are no overt and direct exchange with victims unless they want to or are discovered.
Targeting Cloud Environments
As organizations continue to move to the cloud, ransomware actors might target cloud administrators’ panels and administrator accounts. As we observe threat actors like TeamTNT targeting cloud infrastructures and platforms such as malicious cryptocurrency mining via vulnerabilities, it is likely that ransomware actors will also look at these environments as new targeting and hunting grounds for profit. We see these groups potentially diverting in two phases:
• First, criminals will adapt their current business models to work in cloud environments, treating instances as standard data to be encrypted.
• Second, they will gain maturity in understanding their targets and cloud environments, and create more cloud-specific ransomware families designed specifically with unique cloud services in mind, creating new forms of ransomware attacks.
Following these consecutive movements, and depending on their own developments as the use of the infrastructure matures, ransomware groups will enact even more evolutions in the constant game of offense and defense.
Adding Zero-Day Research to Remove The Need For Access Brokers And Affiliates
Current ransomware teams explore options for access such as having separate teams to pen test entry vectors to potential victims’ networks, purchase legitimate credentials from sellers in the underground, or use known exploits for vulnerabilities in any of the software being used by the target. One possible track is for these ransomware groups to allocate resources in developing their own vulnerability research and exploitation teams. Moreover, considering the availability of these skills are scarce, another possible income source is when these groups also offer “first to refuse” agreements with known exploit developers: interested parties will pay to have a first look at the exploit and get the right to buy them first before the “product” is offered to the developer’s other clients. Regardless of the exact procedure of acquiring the exploit, attacks using these initial access zero-day exploits will lead to successful attacks due to the required time needed for corporate patch cycles.
Revolutions
The collection of small evolutions can eventually lead to bigger, more significant changes that can prove more profitable or beneficial to their respective objectives. At the same time, these revolutions that ransomware groups will find themselves engaging in will still utilize their core skillsets and networks. To get the full list of the seven identified revolutions and the potential direction of these changes, download our report here.
Key Ransomware Players Working For Government
In the past, hackers and cybercriminals arrested may have been recruited by the government to become ethical hackers and to apply their skills for information security purposes. However, we see a potential direction wherein nation state actors make a deal with arrested threat actors and encourage them to hack on behalf of the said country. The skillsets required in intrusions favored by nation state actors can also make use of the skills currently used by big game hunting ransomware players and business models. Even more important than profit, these cybercriminals might look at these deals as a matter of survival to avoid the negative consequences that can happen to them while in the same country.
Leveraging The Same Kill Chain to Manipulate The Stock Market
“Short and distort” is an unethical and illegal market manipulation scheme wherein a trader buys a stock option on a short position and spreads fake information or rumors about the company with the aim of driving the stock price down. In the case of ransomware groups, cybercriminals can get into the targeted organization’s system and look at all connected machines for “useful” sensitive information for as long as they can stay undetected. During the said time for data scanning, these groups are buying stock options to short the company. When the time is right, they launch destructive malware or ransomware in the victim’s network, leading to disruptions in operations and public announcements of the compromise, causing stock prices to go down. While there have been studies that breaches or ransomware infections do not concern investors in the long term, there has also been evidence that stock prices temporarily go down on the days of incidents. Even if the drop is temporary, the potential losses to the company – or profits for the cybercriminals – can be in the millions.
Supply Chain Compromise as a Service
While supply chain attacks are not new, these incidents have come under the spotlight in recent years due to the realization that all organizations outsource specific tasks and software to other companies and software. Supply chain compromise used for targeted ransomware attacks have also increased in the last few years, which makes a compromise on any software supplier a potential channel for ransomware actors to push for malicious components in supposedly legitimate updates. In this way, ransomware actors can resort to compromising as many organizations as possible and maximize their extortion returns by removing outsourced initial access suppliers from their business models. Supply chain attacks as another entry vector is scalable and repeatable for finding new victims and income source.
Insights
We can trace the current ransomware models as an amalgam of other threats that extorted money from users and organizations in the past. Groups involved in cybercriminal activities design and operate these threats as business components and plans that can yield them more profit in the most efficient ways possible. Specific triggers can make these ransomware groups change their business models as the legitimate and targeted victims react and adjust to their previous attacks. In the same vein, these gradual evolutions are expected as cybercriminals also compete with one another: more efficient and scalable processes, more payloads for new platforms, and increased monetization opportunities, among others. On top of this, broader changes in the geopolitical or economic status quo can drive even bigger changes in business models and groups at scale. Regardless of the depth of differences, by keeping in mind that ransomware as we know it is expected to constantly change, defenders and security practitioners will have to constantly study, prepare, and strategize their organizations’ defenses.
Read our insights and recommendations in the paper, “The Near and Far Future of Ransomware Business Models.”





Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One