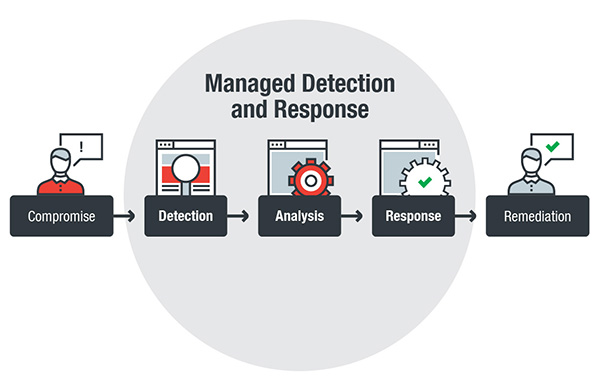
Managed detection and response enables a proactive approach to security with its ability to detect and fully analyze threats and promptly respond to incidents. With the scale and complexity of today’s threats — whether cyberespionage- or cybercrime-driven — the stakes are high. Organizations recognize this: global spending on cybersecurity has increased, driven by regulatory compliance and the need to build or improve detection and response capabilities.
Here’s a closer look at the challenges that enterprises face when adopting a more robust cybersecurity strategy:
Traditinal security solutions, which tend to respond to threats reactively and provide monitoring of only a single vector, are no longer enough against the wide range of threats in the current threat landscape. In the first half of 2018, Trend Micro blocked over 20.4 billion threats. Cryptocurrency-mining malware, for instance, surged by 141 percent. Some recent threats have also showed attackers combining the capabilities, evasion techniques, and persistence mechanisms of different malware tools. Among them: adding file encryption to banking trojans and cryptocurrency-mining malware, lying dormant, and using other devices — routers, printers, scanners, and other internet-of-things devices — to gain a foothold on the system or server.
The SANS Institute reported that actively hunting threats — which involves iteratively detecting and analyzing threats and intrusions — can measurably improve information security programs and speed and accuracy in incident response, at least for large enterprises.
However, many organizations may not have the resources or capability to actively hunt threats. Running a security operations center (SOC), for instance, or using endpoint detection and response (EDR) tools, require expertise.
Even if a large organization has the financial resources to set up an SOC or invest in security tools, it doesn’t necessarily translate to effective information security and risk management.
How can MDR address this challenge?
MDR provides organizations the security needed to thwart not only evasive threats, but their related activities such as establishing command-and-control (C&C) communications, lateral movement, and evasion techniques that can bypass standard security defenses.
MDR provides threat hunting services across the organization’s environments, sweeping for indicators of compromise or attack to better thwart similar threats. MDR also enables organizations to leverage a security provider’s in-depth research and threat intelligence that can provide context and actionable insights into an attack — so that organizations can promptly identify and respond to it.
A good MDR service provider should have the ability to analyze details of system and network-based behaviors and events (both in kernel and user levels) as well as network metadata that organizations can access and track to better understand a threat’s kill chain.
Many organizations adopt new or additional technologies to support their growth. For threat actors, this means more doorways to an organization’s sensitive and mission-critical data. Threats can affect organizations in ways that can be challenging to predict.
There is a disparity in what enterprises need and the staff they actually have. This gap is increasingly widening: It’s estimated that by 2022, there will be 1.8 million open positions in cybersecurity. And despite digital security being a priority, only 65 percent of surveyed organizations had an actual expert to tackle their cybersecurity. This is especially true for enterprises whose size cannot justify the costs of employing dedicated cybersecurity specialists.
The seemingly overwhelming tasks of securing a company can put a strain on IT staff, which typically also manage day-to-day operations — monitoring and keeping networks, servers, and systems up and running .
For enterprises using EDR solutions, the challenge lies in being able to fully maximize or efficiently utilize these tools. They need the skills to do so. And while advanced security solutions such as machine learning-based solutions and EDR technologies help, they are not silver bullets. They are only as effective as the people who use them.
How does MDR address this challenge?
MDR provides a suitable combination of people, process, and technology. MDR addresses the challenges in manpower and costs involved by providing on-demand access to full-time threat analysts, investigators, and incident response experts.
Security alerts, logs, and data, by themselves, don’t really provide context. They may notify about a security incident, but it is up to the organization and its security staff to make sense of them, find out what happened, and determine what to do about it. MDR alleviates the burden of threat hunting, investigation, and correlation, log aggregation, alert triage, and security data analysis. A good MDR service provider is able to do continuous event monitoring and alerting and investigate events or incidents once they are validated.
There should be regular service reviews that identify significant events and incidents and help fine-tune how detection and response capabilities are deployed. This can include collaboration between the MDR provider and customer in terms of reviewing a network packet captured from a firewall or intrusion detection and prevention system, for instance, or identifying the entry point a fileless cryptocurrency-mining malware used to get into the servers.
A
security alert may warn about detection of malware on an endpoint, but it may not specify if it came from an exploit, spam email, or malicious website, if it was injected on a system process, or if it has already spread across systems connected to an affected network.
Validating alerts can take a considerable amount of time and resources; and teams may end up prioritizing the wrong alerts, running after false positives, or sifting through redundant notifications across different security tools.
With the high volume of alerts, it can be challenging to determine which needs to get prioritized and quickly addressed. For example, 37 percent of surveyed bank security chiefs noted that their banks process over 200,000 security alerts each day. A recent survey also noted that 79 percent of cybersecurity personnel feel inundated by the volume of security alerts, not to mention the workload of managing vulnerabilities in their IT infrastructure.
The significance of relieving alert fatigue is exemplified by the data breach at Target, where hackers stole 70 million credit card records. While the incident sounded alarms, they were overlooked for months as its security team was receiving similar notifications that turned out to be false positives. The impact: US$292 million in financial losses.
How does MDR address this challenge?
MDR eases alert fatigue by correlating numerous alerts, identifying what needs to get prioritized and addressed.
MDR provides advanced threat correlation, which analyzes threat data from endpoints and networks to paint a clearer picture of an attack: where it came from, how it spread, and if it already affected the network and systems connected to it. Validated threat alerts shouldn’t come as simple notifications, either. A good MDR service provider furnishes incident cases that include indicators of compromise or attack, affected hosts, and recommended mitigation strategies.
A tangible example of this is MDR’s automated threat correlation determining if an alert that seems relatively benign is actually part of a bigger attack. It can reduce the “dwell time” of threats, by ascertaining if a device (i.e., printers and scanners) that doesn’t normally have security mechanisms in place is infected with malware or is showing anomalous behavior.
By freeing up resources allotted to dealing with alerts, an organization’s IT or security team can focus on what matters most — mitigating risks and quickly responding to threats.
Organizations contend with challenges that can undermine the effectiveness of their security posture: the increasing sophistication of threats and complexities in managing the IT infrastructure, a shortage in cybersecurity talent, and inundation of security alerts. Managed detection and response helps by bridging gaps in an enterprise’s cybersecurity posture through a comprehensive technology stack handled by dedicated researchers and analysts.
Trend Micro Solutions
Trend Micro’s managed detection and response (MDR) service provides alert monitoring, alert prioritization, investigation and threat hunting services. By applying artificial intelligence models to customer endpoint data, network data, and server information, the service will be able to correlate and prioritize advanced threats. Threat researchers investigate prioritized alerts to determine the extent and spread of the attack. They work with customers to provide detailed remediation plans. This service allows customers to investigate security alerts without the need to hire qualified incident response staff.
Backed by 30 years of experience in threat research, Trend Micro’s MDR service provides access to experts who are proficient with live response and are familiar with products that can provide meaning to security incidents that happen to organizations and their industries. Trend Micro’s MDR service is backed by specialists who protect an organization’s IT environments through a comprehensive security technology stack. Our experts have the necessary tools and technologies to analyze threats and assist organizations in maintaining a good security posture.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One