Ransomware Recap: Kristina, Waffle, and a Christmas-themed Variant Take Center Stage
More ransomware families and variants were discovered in the wake of the Bad Rabbit outbreak. New families include ones labeled as Kristina, Waffle, Foxy, and a holiday-themed "Christmas" ransomware, while new variants from old families also make an appearance.
Kristina
Detected by Trend Micro as Ransom_ANITSIRK.A, Kristina comes from a new ransomware family that encrypts 234 file types that include .mobileconfig, which contains all configurations of iPhone devices, as well as .savedsearch – a file extension associated with the Spotlight real-time search service installed in Apple Mac OS X (macOS). The discovery of Kristina’s encryption of .mobileconfig and .savedsearch files comes as a surprise since the ransomware only runs on a Windows environment.
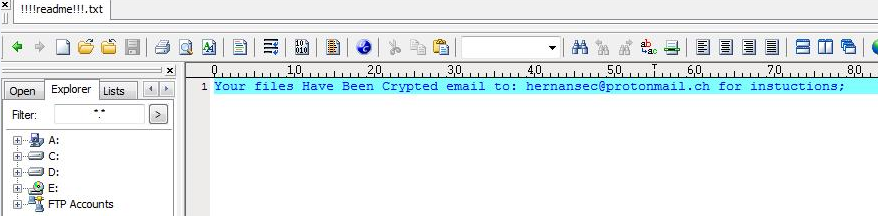
Figure 1. Kristina ransom note
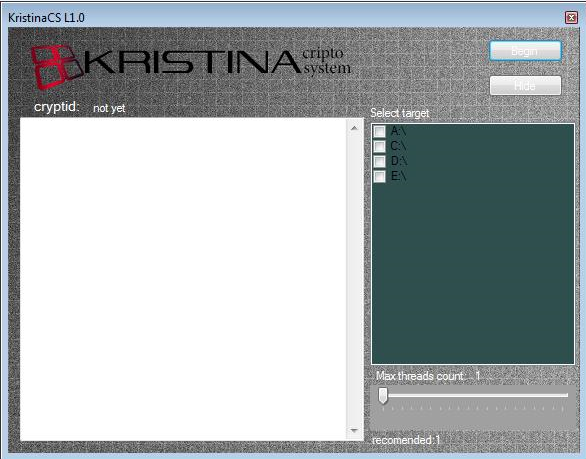
Figure 2. Kristina’s GUI
Kristina encrypts files using the AES encryption algorithm, and appends the file name with a .crypt12 extension.
Waffle
Waffle ransomware (Ransom_WAFFLE.A) was discovered using cryptographic algorithms to alter targeted data. This ransomware is distributed via spam emails with an attached Microsoft Word document disguised as a legitimate message from a trusted entity.
A macro script is executed when users open the malicious attachment, installing Waffle into the Temp folder with administrative privileges.
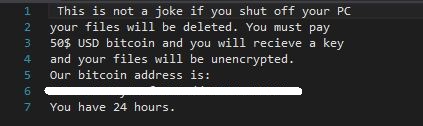
Figure 3. Waffle ransom note
Waffle encrypts file types such as Microsoft Office documents, as well as certain video and audio files. Its ransom note demands US$50 (0.00697 BTC) for a decrypt tool.
Christmas
Christmas ransomware (Ransom_SAMX.A) is a new ransomware family created from an open-source platform. Christmas arrives in the system as Christmas.exe but appears to be in its early stages of development as it still not capable of encrypting files. This ransomware, however, sports a creatively grim ransom note:

Figure 4. Christmas ransom note
Foxy
Detected as Ransom_FOXY.A, HiddenTearFoxy comes from a new ransomware family that encrypts 42 file types that include .torrent, .java, as well as Microsoft Office documents and video and audio files.
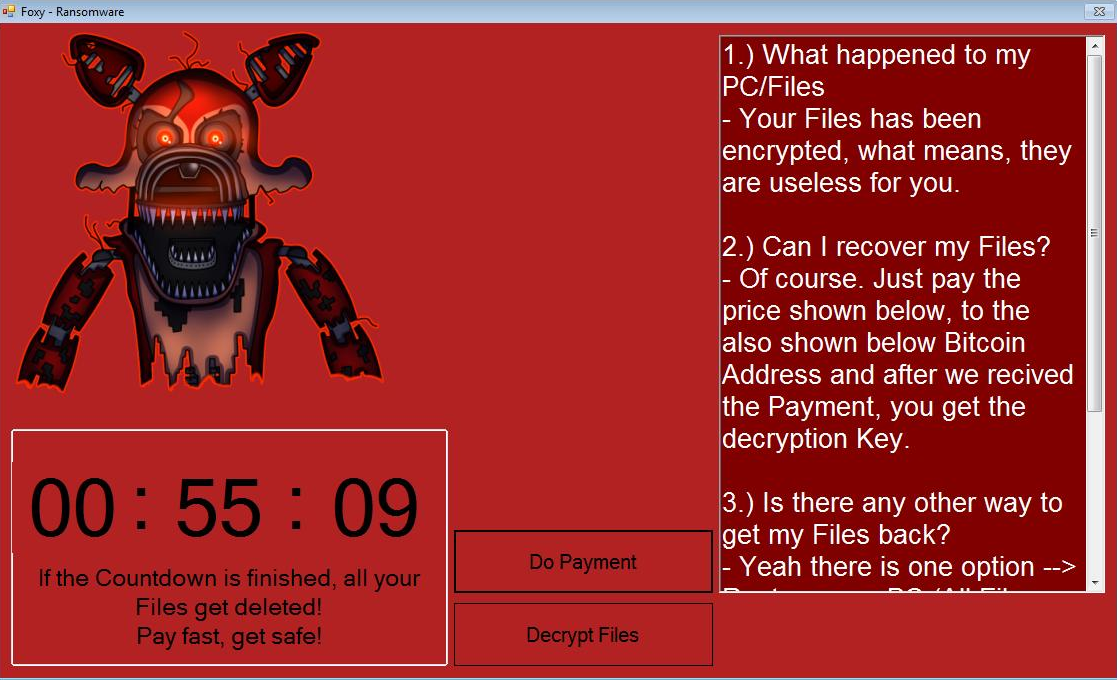
Figure 5. Foxy ransom note
This ransomware encrypts files using the AES algorithm and appends them with a .nightmare extension name.
New Variants from Old Families
Along with the discovery of variants from new ransomware families, Trend Micro was also able to detect new variants from old families such as Jigsaw (Ransom_JIGSAW.WF), Crysis (Ransom_CRYSIS.FFRY), Magniber (Ransom_MAGNIBER.O), WannaCry (Ransom_WCRY.SM2), HiddenTearLOS (Ransom_CRYPTEAR.SM0), and Sad (Ransom_SAD.A).
Users and enterprises can adopt these best practices to defend against the risk of ransomware infection. A multi-layered approach is also key to defending all possible gateways from threats like ransomware, whether they originate from new or old families.
Trend Micro Ransomware Solutions
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevent ransomware from ever reaching end users.
At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimize the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
Using a combination of technologies such as deep packet inspection and threat reputation, the TippingPoint provides organizations with a proactive approach to security, including the tools to combat ransomware. It gives high accuracy, comprehensive contextual awareness, in-depth analysis of network traffic, and the visibility and agility necessary to keep pace with today's evolving security landscape.
In addition, Trend Micro XGen™ security provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints. Smart, optimized, and connected, XGen™ powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One