Trickbot’s Updated Password-Grabbing Module Targets More Apps, Services
 Trickbot has been one of the most active banking trojans in 2019. The malware is constantly being improved with new and updated modules, and the threat actors behind it are still churning out new ones. Researchers from Security Intelligence have reported on a sudden increase of Trickbot’s activities in Japan, and Trend Micro researchers have found updates to the password-grabbing (pwgrab) module and possible changes to the Emotet variant that drops Trickbot.
Trickbot has been one of the most active banking trojans in 2019. The malware is constantly being improved with new and updated modules, and the threat actors behind it are still churning out new ones. Researchers from Security Intelligence have reported on a sudden increase of Trickbot’s activities in Japan, and Trend Micro researchers have found updates to the password-grabbing (pwgrab) module and possible changes to the Emotet variant that drops Trickbot.
Previous Trickbot reports involved behavior that compromises services and platforms to collect credentials from browser, Outlook, WinSCP, and Filezilla. Trend Micro’s latest report of changes to its pwgrab module found additional credential-stealing capabilities for remote access applications such as remote desktop protocol (RDP), virtual network computing (VNC), and PuTTY platforms. The most recent iterations (detected by Trend Micro as TrojanSpy.Win32.TRICKBOT.TIGOCER) targeted a slew of credentials from TeamViewer, OpenSSH, OpenVPN, Git, KeePass Password Manager, SSH private key files, SSL certificate files, and Bitcoin wallet files.
[Read: Trickbot’s bigger bag of tricks]
Trickbot manages to enumerate open windows to search for active TeamViewer processes to record the user ID and password listed in the window.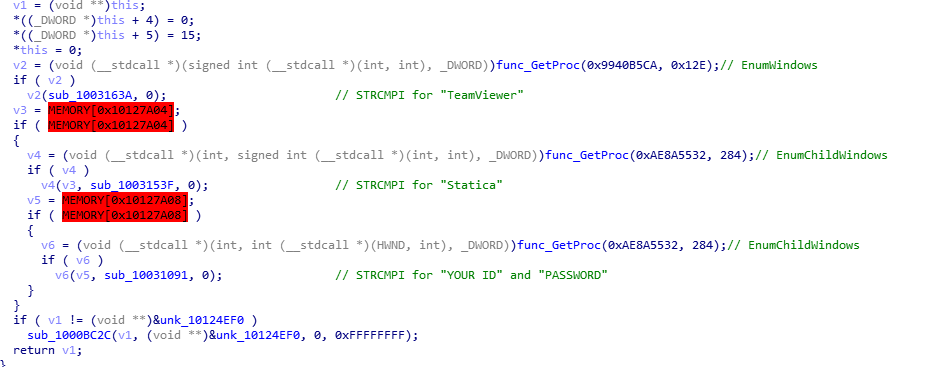
Figure 1. Trickbot targeting TeamViewer
Similar to its routine with RDP, Trickbot uses the CredEnumerate() application programming interface (API) to list all locally-stored Git credentials in the system, parsing the output to identify previous and currently used git credentials.
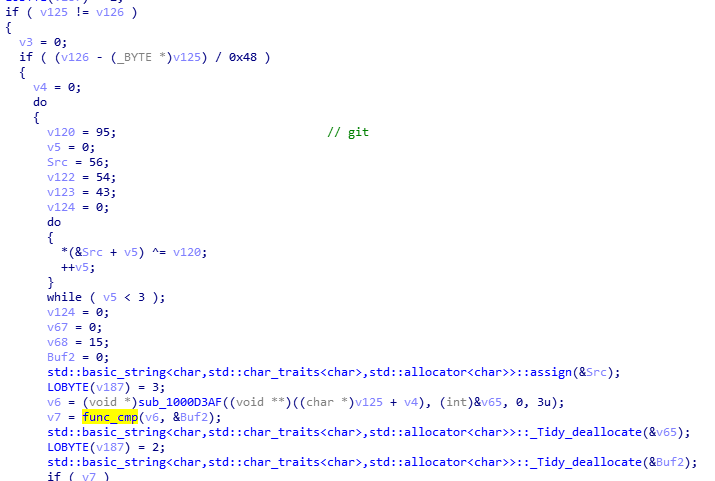
Figure 2. Trickbot targeting Git
[Read: The latest Trickbot campaign uses an obfuscated JavaScript file]
The updated module can steal Git credentials stored in the %USERPROFILE% directory by searching for the file .git-credentials and files in the \.config\git\credentials folder.
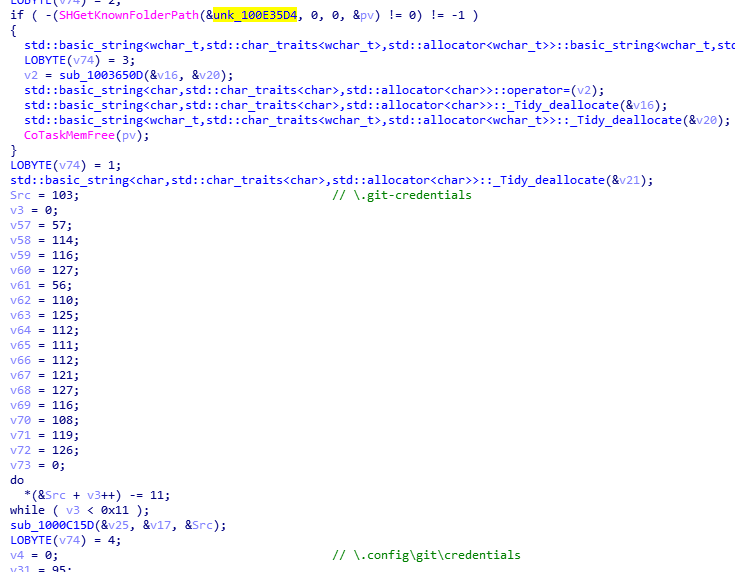
Figure 3. Scanning for stored Git credentials
For OpenSSH, Trickbot manages to search for files under the %USERPROFILE%\.ssh folder to acquire credentials. It matches the strings DSA PRIVATE KEY, RSA PRIVATE KEY, and OPENSSH PRIVATE KEY in the files to scan for and steal private key credentials.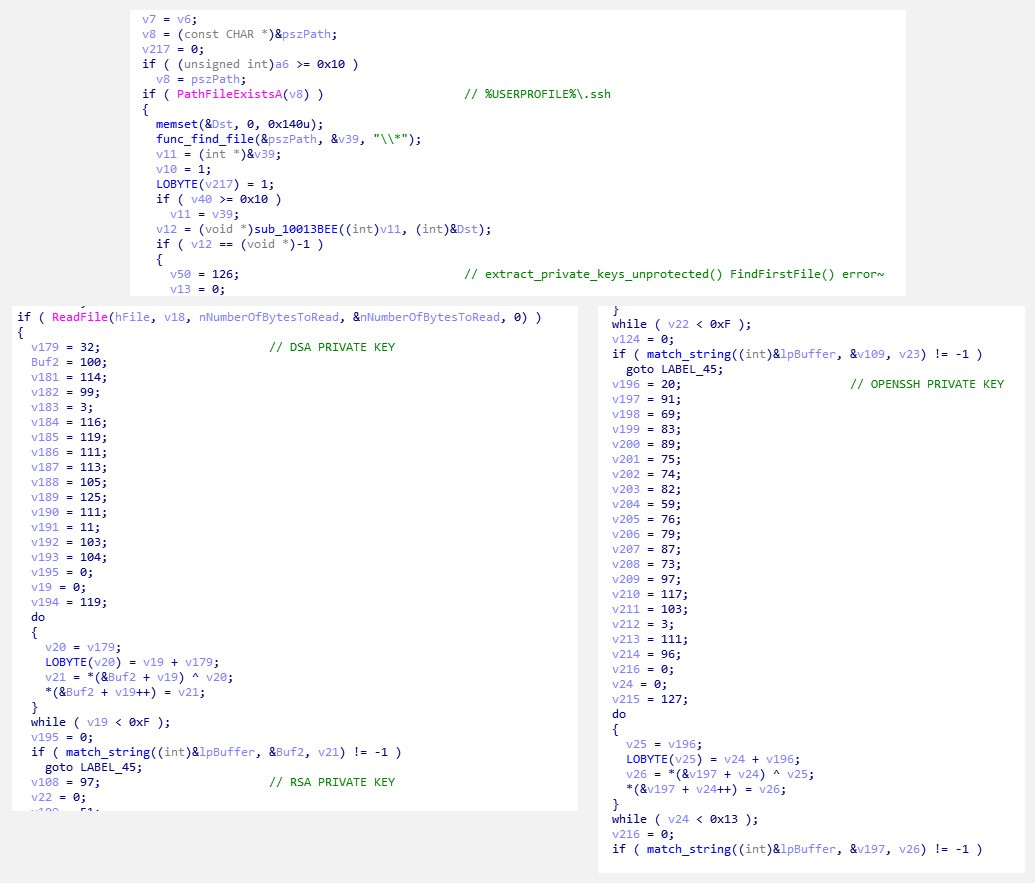
Figure 4. Targeting OpenSSH
Targeting OpenVPN, Trickbot queries the registry key HKEY_CURRENT_USER\Software\OpenVPN-GUI\Configs, which contains user preferences and saved credentials used for OpenVPN connections.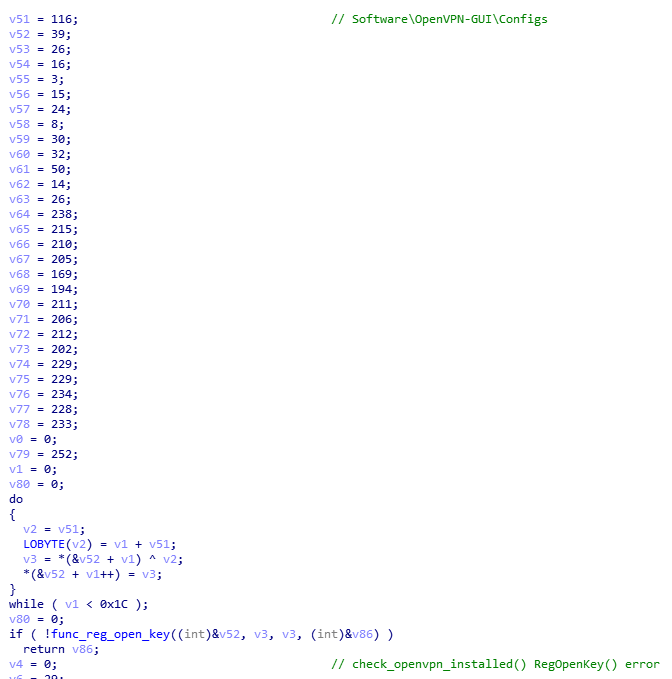
Figure 5. OpenVPN queries
[Read: Trickbot watch: Arrival via redirection URL in spam]
As KeePass Password Manager is a free and open source application, researchers found that the Trickbot sample module searches for the file %APPDATA%\KeePass.config.xml, and parses through the xml to get the DataBasePath (.kdbx).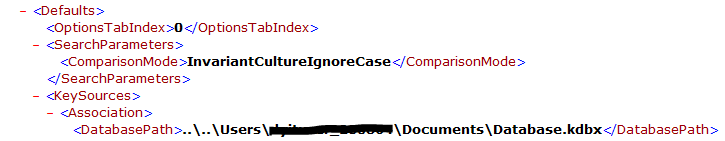
Figure 6. Parsing through KeePass
The updated module also steals what it calls “Precious Files,” which are private keys (.ppk), SSL certificates (.p12 and .pfx), and crypto wallet files (.dat). Trend Micro researchers noted these with interest as the first three file types can be used for future targeted attacks, while the crypto wallet files can be used for its intrinsic value online.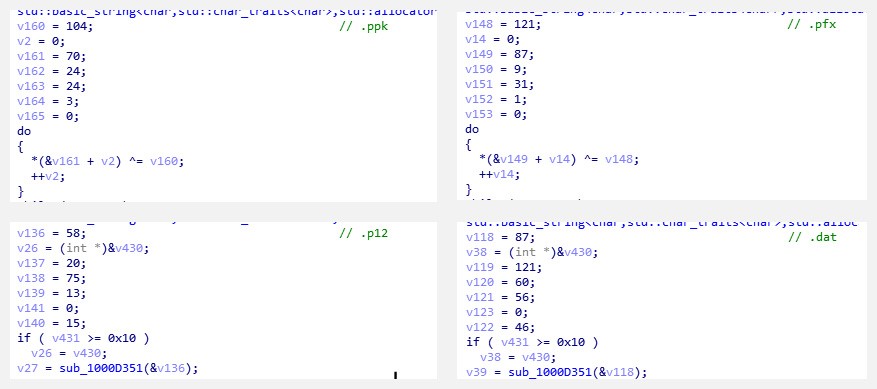
Figure 7. “Precious Files”
The module queries for .ppk, .pfx and .p12 files in the %USERPROFILE%\Documents, %USERPROFILE%\Downloads, and %USERPROFILE%\.ssh, while .dat files of bitcoin and litecoin are targeted in %APPDATA%\bitcoin and %APPDATA%\litecoin folders.
Trend Micro solutions
Because of its modular nature, Trickbot can and will surely morph into something more in order to add to its features, and cybercriminals will surely look into other possible iterations to make a profit. To address this challenge, enterprises can look into sourcing third-party security services offering managed detection and response (MDR), such as Trend Micro™ Managed XDR, which offers a wide scope of visibility and expert security analytics by integrating detection and response functions across networks, endpoints, emails, servers, and cloud workloads. Organizations will have access to the whole knowledge base of Trend Micro, including prior analysis of other Trickbot variants and other similarly sophisticated threats.
Moreover, enterprises can benefit from security technology that employs a multilayered approach to mitigate the risks brought by threats like Trickbot. Trend Micro XGen™ security provides a cross-generational blend of threat defense techniques to protect systems from all types of threats, including banking trojans, ransomware, and cryptocurrency-mining malware. It features high-fidelity machine learning on gateways and endpoints, and protects physical, virtual, and cloud workloads. With capabilities like web/URL filtering, behavioral analysis, and custom sandboxing, XGen security protects against today’s threats with various capabilities: bypassing traditional controls; exploiting known, unknown, or undisclosed vulnerabilities; or stealing or encrypting personally identifiable data. Smart, optimized, and connected, XGen security powers Trend Micro’s suite of security solutions.
Additional insights by Augusto Remillano II and Carl Maverick Pascual
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization
- Agentic Edge AI: Development Tools and Workflows

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One