Malware in Apps’ Clothing: A Look at Repackaged Apps
All it takes is one popular app to start a chain reaction. Case in point: Flappy Bird.
This app captivated the public, spawning countless articles, parodies, and videos. Despite having more than 50 million downloads, the developer abruptly took the game down from app stores, triggering an even bigger wave of interest and publicity. The takedown resulted in the emergence of similar apps in app stores and even auctions for devices with the app installed.
Unfortunately, its popularity also took a malicious turn, as we soon found fake versions of Flappy Bird circulate online. Most of these fake versions were premium service abusers, which sent messages to premium numbers, causing affected users to incur unwanted billing charges.
Popularity Comes at a Price
Trojanized or repackaged apps are popular means for cybercriminals to gain new victims. Bad guys take legitimate apps and add malicious code to them before distribution. Malicious code can lead to a range of behaviors, from simple premium service abuse to more complicated data theft or anti-malware deactivation. To users, repackaged apps may seem normal. The truth though is that they run malicious routines in the background.
In “Beyond Apps: 2013 Mobile Year-End Review,” we noted that some of the top malware were repackaged apps. The top 2 malware families of the year, FAKEINST and OPFAKE, were premium service abusers that came in the form of repackaged apps.
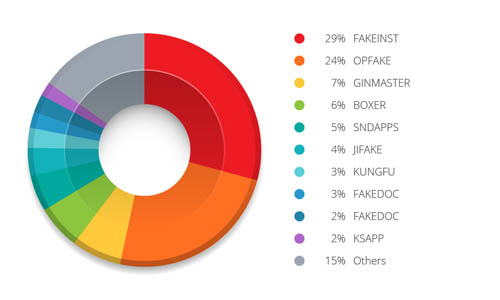
Figure 1: Top malware families of 2013
Repackaged apps hold a certain appeal for bad guys because they are sure to attract users (read: victims). By constantly monitoring mobile threats and trends, we have seen cybercriminals take advantage of the most popular apps. Examples include messaging apps like KakaoTalk and gaming apps like Plants vs. Zombies 2. Bad guys have also used repackaged apps to infect devices with malware that mine for cryptocurrencies like Bitcoin and Dogecoin.
Dressing Up Malware
Cybercriminals take great pains to make sure their repackaged apps are downloaded and installed by users. These are almost always near-identical in appearance to legitimate versions. That’s one reason why so many people fall for them. Bad guys can mimic the icons of popular apps. Some even take it a step further by spoofing the legitimate developer’s name to add a sense of “legitimacy.” Back in 2011, we saw a rogue developer spoof Rovio Mobile Ltd., the Angry Birds developer. At first glance, the fake app’s developer’s name looked like “Rovio Mobile Ltd.” A closer look though revealed that the “L” in “Mobile” was actually an “I.” In lowercase, the developer’s name was actually “rovio mobiie ltd.”
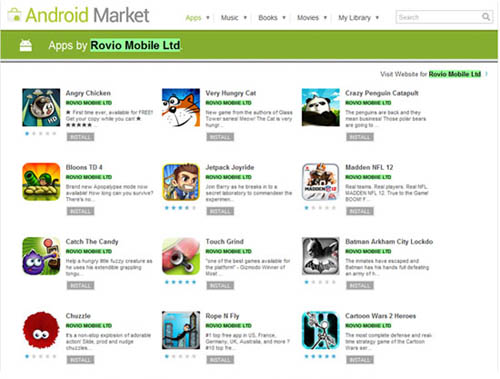
Figure 2: Apps offered by the fake Rovio Mobile Ltd.
With all the techniques bad guys use, it can be all too easy to be misled by a repackaged app and install it without much thought or scrutiny.
The Role of Third-party App Sites
Because of the security measures Google employs now, users are more likely to encounter repackaged apps in third-party app stores or random sites. Cybercriminals favor these types of sites because uploaded or hosted apps are rarely checked or scanned for malicious activity. As we noted in “Russian App Fraud: The Case Against App Searches,” cybercriminals will use different means—text messages or mobile ads—to lure users to these sites.
What do users see when they visit such a site? As research revealed, a whole lot of malware. One third-party app store, for instance, was home to more than 500 OPFAKE variants. These contained potentially malicious advertising code and were premium service abusers.
These sites also do a little “repackaging” to gain more visitors. We encountered one site that mimicked Google Play, perhaps in an attempt to appear more legitimate. The site hosted several repackaged apps, including—curiously enough—a fake version of the Google Play app that led back to it.
Abuse of Trust
Repackaged apps rely on misplaced trust. Users trust that these are legitimate apps that will not harm their devices (and their data)—which are proven wrong in the end. Before downloading any app, follow these steps:
- Carefully choose your download sites. A good rule of thumb is to only rely on official app stores, as these often do security checks for hosted or uploaded apps. Third-party app stores and random sites do not offer the same level of security.
- Check app details. Find out who developed it. There are, however, a lot of copycat developers. Popular apps may have a little icon that says “top developer,” which could help point you to the correct, legitimate version. Reviews can also help you weed out fake or malicious apps.
- Check app permissions. Malicious or suspicious apps often require more permissions than they need.
- Install a security solution that detects malware and other potential mobile threats. It’s not your sole responsibility to look out for repackaged apps. App stores and developers should also be concerned. While repackaged apps may not directly affect them, they can soil their reputations. Though you can avoid certain app stores or specific developers, app stores should impose strict—if not stricter—guidelines for scanning potentially malicious or fake apps. Developers should also report or flag any repackaged app they see. They should also remember to use secure coding practices and perhaps, precautionary steps to ensure that their codes are harder to exploit.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One