Soon, smart technologies will be universal. Embedded sensors will be heavily woven into the city’s fabric so that public services and infrastructure work together more efficiently. This opens up a multitude of possibilities for citizens.
It’s a vision of utopia, but it comes with a price. By going smart, cities also welcome new risks. If not planned correctly, cities could put their operations, their citizens' privacy, and public safety at risk. How then should local governments and urban developers go about securing their smart cities?
How Are Cities Around the World Getting Smarter?
What does it take to build a smart city? More than half of the world’s population live in urban areas, but not all of these locales can be considered smart. Smart city implementations vary from region to region. We have surveyed a number of currently existing smart cities and how they are adopting smart technologies to address urban challenges.How Are Cities Around the World Getting Smarter?
Two hundred and fifty million Chinese citizens are packing up and moving in. As part of their country’s Four Modernizations campaign, they will be relocated to urban areas, raising the number of city residents to 900 million by 2025. This spike in urban population is bound to cause inefficiencies in energy consumption and waste management, among other issues. To address these challenges, the country’s public and private sectors have begun investing in smart technologies. This will make China one of the countries with the highest concentration of smart cities in the world.
But what exactly does it take to build a smart city?
More than half (54%) of the world’s population live in urban areas; not all of these locales can be considered “smart.” The International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) refer to a smart city as the “system of systems.” It improves public services through the merging of critical infrastructure like energy and transportation systems, and new technologies such as sensor networks and infrastructure.
A Survey of Smart Cities Worldwide
The ways smart cities are implemented vary from region to region. Each one is designed to meet certain needs specific to their citizens or take advantage of technologies readily available to them. We have surveyed a number of currently existing smart cities and how they are adopting smart technologies to address challenges. Please note that the locations listed below are just a small sampling of all smart cities found across the globe.
Songdo IBD, South Korea
Songdo International Business District (IBD) is the world’s first smart city. It was built from the ground up with the aid of smart technologies. Its residents have access to real-time video communication that lets them remotely attend English classes, consult doctors, or even work from home. It’s also equipped with nearfield communication (NFC), both passive and active radio frequency identification (RFID), physical and biometric sensors, and 3-D and closed-circuit television (CCTV) cameras. It also uses standard protocols for data security like Secure Sockets Layer (SSL), firewall, public key infrastructure (PKI), and intrusion detection system (IDS), to name a few.
Songdo IBD developed three water networks—freshwater, sewage, and treated water—for its residents’ use. It also uses natural gases to generate heat and has a pneumatic trash collection system (an underground centralized vacuum-powered tube system).
Perhaps what makes Songdo IBD a prime example of a ubiquitous city is its use of smart card house keys that also serve as a means to pay for subway transportation and parking meter fees, watch films, and more. These cards are not linked to user identities and can be easily canceled and reset in case of loss. But such pervasiveness may raise privacy concerns–similar to how residents opt for fitted smart systems in every home and business, omnipresent CCTV cameras, and even using Global Positioning System (GPS) bracelets on children. As with anything involving the Internet of Things (IoT), especially on this scale, it is a matter of weighing convenience and privacy.
Yokohama, Japan
After the Great East Japan Earthquake in 2011, Japan’s National Policy Unit defined a “Green Policy” to address concerns about national energy security and efficiency. These plans include the installation of home energy management systems (HEMS) in all households by 2030. And it’s not that far off. The Yokohama Smart City Project (YSCP)—Japan’s initiative to expand its smart grid—already shows a high preference for HEMS, almost 4,200 HEMS, 37 MW solar panels, and 2,300 electricity vehicles (EVs) have so far been installed, translating to a carbon dioxide reduction of 39,000 metric tons.
The introduction of HEMS allowed households and buildings in Yokohama to save power and spend less on electricity by throttling high-volume appliances at peak hours and optimizing the use of in-house energy through real-time data, resulting in increased energy and grid security. Despite that, based on a report by the EU-Japan Centre for Industrial Cooperation, data security is not assured in this centralized system.
Singapore
Singapore is set to become a smart nation. It plans to address its aging population and urban density through developments in big data, cybersecurity, urban logistics, and smart health assistance provision, among others.
On-demand mobility is at the forefront of Singapore’s plans, with efforts to provide autonomous vehicles like self-driving taxis. Its commuters can also book bus seats with routes generated by travel patterns and crowd-sourced suggestions.
The National Research Foundation (NRF) also launched the Virtual Singapore project, an elaborate 3-D model of the whole country, that aims to help decision-makers, planners, and researchers develop tools that will address complex challenges in the country.
Sensor networks–comprised of security cameras and air quality, temperature, humidity, traffic, and speed detectors–will also be installed to give behavioral feedback so issues can be readily addressed.
All of these projects rely on the smart city’s cornerstone―data. The data collected will let officials prevent crime, determine traffic density, and issue emergency alerts.
The Netherlands
Amsterdam is well on its way with its civil innovation efforts. The city boasts of food delivery services via solar-powered tricycles and crowd-sourced parking lots. Even better, three cities in the Netherlands already have noteworthy smart projects.
Nijmegen piloted the Smart Emission project aided by a low-cost citizen-sensor network. Partner citizens deployed sensors in public, from roundabouts and sidewalks to the front of houses. These sensors gather real-time data—air quality, noise level, humidity, and air pressure—which is then visualized on a map and readily provided to locals 24/7.
Rotterdam, meanwhile, installed a sustainable water management system called Rain Radar, which interprets how much rain has fallen in specific areas. This system allows the water board to store or direct excess water in playgrounds, underground water tanks, and canals to prevent flooding. Since the city is very vulnerable to flooding, being six meters below sea level and suffering acute rainfall that cause severe damage, small-scale facilities have also been developed. Green roofs, flood-control water plazas, and car parks with huge underground water storage aim to address flooding.
In Oosterworld, Almere lies an off-grid village called ReGen, where a typical day can mean harvesting salad greens from seasonal gardens, gathering eggs from a communal farm, and having food waste collected for composting. ReGen was designed to be a self-sustaining living space that recycles waste, produces its own energy and food, and does not emit pollution. It boasts of homes, greenhouses, aquaponics gardens, livestock, solar cells, and water storage, among others.
Jaipur, India
Jaipur will be one of the 100 smart cities set to be completed by 2022. Already, we are seeing active citizen engagement through dedicated sites, social media accounts, and face-to-face meetings. According to citizen polls, top concerns to address include transportation, mobility, heritage, and tourism. This has led to the deployment of routers and access points that provide Wi-Fi hot spots and video surveillance cameras, along with interactive kiosks and parking slots near shopping places and landmarks. Apart from free map and mobile phone-charging services, these kiosks also offer scanning, printing, and document uploading.
China
China plans to have 386 smart cities, with its Four Modernizations—agriculture, industry, national defense, and science and technology—integrated into their construction. Mobile apps developed by state-owned and private companies will play a major role in this process. These apps will be used for public transportation, doctor appointments, and bill payments in the future.
Urban planners in China also initiated an Urban Data Lab to collect government information, existing urban plans, mobile phone metadata from carriers, and behavioral data from location-based services. The information is used to analyze citizens’ spatial behaviors to help urban planners make more reasonable city plans and policies, like calculating typical commute times and recreational patterns.
Despite worries of possible sensitive data abuse, a project called City Brain aims to show how technological solutions can positively impact a densely populated country like China. The project involves more than 50,000 video cameras that require a continuous stream of computing power. Developers are expecting to eventually evolve each city into an artificial intelligence (AI) community later on.
Jun, Spain
Jun is a small town that has been running its municipal council on Twitter since 2011. It is a good example of a small city that addresses civic concerns through social media. All of its public offices and officials are thus required to have a Twitter account. Twitter can be used to report crimes, find lost dogs, book doctor appointments, and even touch base with local government officials.
Paperwork, so to speak, is also done via Twitter. Anyone can tweet about a broken lamppost so city officials can immediately respond by tagging the electrician. Once fixed, the electrician can reply to the tweet to say the problem has been addressed.
Twitter use also allowed the town to trim down its police force from four officers to just one. With free Wi-Fi access, citizens no longer have to physically file complaints, requests, or queries. Of course, it is possible that such social media use can be abused. Attackers may try to hack official accounts to either spam followers or intervene in public operations through misleading announcements or posts. Immediate countermeasures are required in case said abuses take place.
Building a smart city entails generating vast amounts of data and making particular datasets more accessible to relevant organizations and government bodies. Consequently, generating big data to optimize a city can pose potential security and privacy issues that may stem from improper data analysis, sharing, and use.
While attacks on smart cities are still relatively unheard of, it is clear that citywide smart technologies that handle and process citizen and infrastructure data have to be secured. Organizations and governments involved in the creation of smart cities should be able to provide continued and sustainable developments that benefit their citizens while ensuring their cities’ security.
US Cities Exposed in Shodan
Shodan is an online search engine that catalogs cyber assets or internet-connected devices. An in-depth analysis of Shodan data reveals how some of the biggest US cities fare in terms of exposed cyber assets. The research answers what factors have led to this exposure, what this means in terms of security, and how can users protect their data.Security Considerations for Smart City Sectors
For cities looking to adopt these technologies across all their public-facing sectors, the benefits are promising, but they also come with many risks. Here, we run through a variety of existing smart solutions many cities use for each of their critical sectors, and the kind of attacks local governments should be prepared for.Security Considerations for Smart City Sectors
Smart technologies have their pros and cons. And for cities looking to adopt these technologies across all their public-facing sectors, the benefits are promising.
In the summer of 2015, Legionnaires, the deadly bacterial disease, plagued New York City and claimed a dozen lives. It was contracted by inhaling vapor containing the bacteria. In less than a month, the outbreak was over. City health officials were able to trace the source—a contaminated cooling tower. Free software called SaTScan had helped them monitor and map the disease outbreaks so they could stop the epidemic.
But building a smart city is a double-edged sword. The benefits come with risks. Early in April 2017, a hacker was able to set off a series of emergency sirens which rattled the citizens of Dallas, Texas. The emergency response system, which was originally designed to alert people of impending disaster, had become a cause of unnecessary panic.
Here, we shall run through a variety of existing smart solutions cities use for each of their critical sectors, and the kind of attacks local governments should be prepared for.
Smart Energy
For better energy efficiency, energy management systems (EMS) are placed in homes, buildings, and factories throughout the city. These systems are responsible for monitoring and regulating power consumption.Security Risks
- Cause instability in the city's power supply, affecting critical functions
- Launch ransomware attacks on EMS or steal energy
- Disrupt EMS communications
- Sniff smart meter data and steal citizen information
Smart Transportation
Smart transportation systems, used in conjunction with mobile apps and sensor-based services, are put in place to ensure smooth flow of traffic and to provide citizens with better commuting options and parking spaces.Security Risks
- Cause potential vehicular accidents
- Exploit vulnerabilities to get free rides or hold vehicles hostage
- Interrupt and manipulate transportation services
- Compromise user data
Smart Environment
Sustainable living in the city is bolstered by monitoring air pollutants, optimizing trash collection, and proper handling of waste. Sensor networks detect real-time conditions to help cities make accurate and efficient environmental decisions.Security Risks
- Hack smart valves to cause waste water overflow
- Hold system devices hostage
- Manipulate commands and impair system responses
- Take advantage of sensors to track activity
Smart Connectivity
Smart infrastructures and applications thrive on stable connectivity for seamless communication. The technologies are enabled by different networks, including Wi-Fi, cellular networks, and other wireless protocols.Security Risks
- Hold systems or devices hostage
- Disrupt network communications causing downtime for connected systems
- Intercept communications to sniff out information and credentials
Smart Governance
Municipalities use security cameras and single-entry portals to efficiently provide citizens with security and basic public services. Open government data (OGD) is made available for transparency in governance.Security Risks
- Hold systems or devices hostage
- Turn connected devices into bots
- Gather intelligence on targets via surveillance feeds
- Smart
Energy - Smart Transportation
- Smart Environment
- Smart Connectivity
- Smart Governance
Energy Sector
The smart grid is perhaps the first thing that comes to mind when thinking about city-wide energy management. It’s an umbrella term that encompasses several interconnected components. The most basic are smart meters—those nifty devices that record energy consumption and automatically send back the data to power companies.
A number of smart cities, particularly in Japan, have adopted energy management systems (EMS) to help lower their carbon emissions and improve energy efficiency. In households, home energy management systems’ (HEMS) are used to monitor power consumption and remotely control connected appliances. HEMS and other subsidiary energy management systems like building energy management systems (BEMS) and photovoltaic (PV) systems can all be coordinated through a community energy management system (CEMS) for centralized energy optimization and saving.
Left unsecured, each of these components can be abused by attackers in many different ways. Smart meters, for example, can be sniffed for data which can be used to profile home users. Unsecure HEMS can be targets of brute-force attacks, which may lead to the exploitation of other connected devices in citizens’ homes.
Jamming the signal of smart meter transmissions may also impair demand-response on a household scale. If attackers are able to take advantage of the way these energy management systems communicate with each other, they can launch distributed denial-of-service (DDoS) attacks that target larger systems in the city and hamper the supply of critical services.
Transportation Systems Sector
Smart cities that use intelligent transportation system (ITS) solutions aim to solve daily traffic management concerns like vehicle congestion and underutilized public transport. Traffic flow is normally regulated through a centralized system of connected traffic lights and sensors. This system can automatically assess when to change the phasing of lights to reduce delay in intersections and pedestrian waiting time.
Commuting is made more efficient through smart public transport systems. Some cities have even installed metro trains that are grade of automation 4. This means that these trains are fully automated and can run without onboard staff. Many metro trains and buses in smart cities follow strict timetables which commuters can access via apps. The same apps can be used to book and pay for tickets.
Many more mobile apps work in conjunction with publicly available smart vehicles. A bike app used in several Chinese cities is able to find nearby bicycles that can be unlocked and used just by scanning a QR code printed on it. A similar principle is applied to shared scooters. A mobile app helps locate the nearest available scooter, settles the payment, and unlocks the scooter for use. Some smart cities even implement car sharing, which allows drivers to rent standby vehicles over a short period of time. Global positioning system (GPS) gives these rental companies a means to track these vehicles to prevent theft.
Parking can also be reserved and paid for via free mobile apps and websites that provide real-time tallies of available parking spaces—some even come with their own charging stations.
The trouble with having so many transport options linked to apps is the presence of vulnerabilities. If these get exploited, attackers can abuse the apps to steal bikes or get free rides and parking spots. These transport systems can also get hit with ransomware, as with what happened to the San Francisco Municipal Transportation Agency. Their downtime resulted in passengers getting free rides until systems were restored.
Smart traffic lights can also be prone to hacking. Traffic signals operating on open and unencrypted protocols can be hacked to always be greenlit. Smart cars which are enabled by over-the-air (OTA) updates are able to communicate with these traffic lights. If the lights get hacked, the cars are likewise susceptible to remote vulnerabilities and false OTAs. This allows attackers to hijack smart vehicles in some capacity, hit them with ransomware, or simply push wrong traffic information to drivers.
Environmental Systems Sector
Smart environment technologies may not be as evident as the other smart systems deployed in the smart cities but they collectively make the municipality more habitable. A good example of such technology is Chicago’s Array of Things (AoT). The project, which uses trackers mounted on traffic light poles, provides real-time, actionable data that can be used to improve air quality throughout the city.
Often overlooked city services like waste management can also be automated through sensor-equipped smart trash cans and pneumatic waste systems which suck garbage into a centralized location. These foster faster trash collection. There are also embedded sensor networks in sewer systems that regularly monitor outfalls and report sewer pressure. With that kind of data, the network is able to control smart valves which prevent sewer blockages or overflows.
If attackers were to hack a smart sewage system and open all the smart valves, they could release untreated wastewater into bodies of freshwater. This can be hazardous to citizens’ health. It has already been proven that an unprotected treatment plant control system can be vulnerable to hacking due to poor configuration and lack of interface access restrictions. Real-world attacks on these systems are plausible.
Communications Sector
Without reliable connections provided by wireless technology, smart city infrastructures and applications will fail to perform their intended functions. Seamless communications is a requirement. Several of the smart technologies mentioned above utilize cellular networks for communication. These include general packet radio service (GPRS)-enabled smart sewer systems, 3G-enabled public transportation, LTE-enabled smart traffic lights, and vehicle-to-infrastructure (V2I) technologies.
Attackers can disrupt such network communications and smart device synchronization by conducting DDoS attacks. A signal jammer, additionally, may drain smart device batteries as cellular modules try to reconnect to the network several times. Intercepting the communications may also allow hackers to analyze transmitted data about the system, the instructions set, the IP address or phone number of cloud service or backend servers, and even hardcoded credentials.
The availability of public Wi-Fi is also a key characteristic of many smart cities. Implementations like LinkNYC, a New York-based communications network launched in 2016, seek to turn old payphone booths into 7,500 Wi-Fi-enabled kiosks that let citizens check maps and city services, make free domestic calls, and charge their mobile phones.
Privacy concerns, though, inevitably surface as many public Wi-Fi networks require users to input their email addresses and register using their mobile phones. Moreover, public Wi-Fi is usually an “open network” wherein the data transmitted to and fro user devices is unencrypted.
Government Sector
Municipalities aiming for centralized governance use smart technologies to provide better public service to their citizens, ensure public safety, and guarantee transparency in all government-related affairs.
To make public services more efficient, some local governing bodies like the Bristol City Council have created single-entry portals which give residents an easier way to pay for council fees, order new trash bins, renew permits, and file complaints all without additional paperwork.
For public safety, many cities have installed public security cameras. Rio de Janeiro, for example, has the “Center of Operations”, where over 80 screens show real-time traffic feeds, weather reports, and videos collected from 500 municipal cameras. More than 20 operators have access to 360˚ image views.
To foster better transparency, some smart cities proactively publish open government data (OGD) online. Singapore’s viz.sg, for example, is able to provide data visualizations on government budget, known Dengue and Zika outbreaks, and taxi density, to name a few. Non-governmental organizations (NGOs) and private firms can use these datasets and partner with their respective governments to design projects that can further benefit local citizens.
Given all the available data processed through these channels, the challenge is to ensure the privacy and security of citizens without sacrificing the steady deployment of public services. With OGD, it’s important for governments to screen the data and remove any of their citizens’ personally identifiable information (PII). Failure to do so can put citizens at risk. For instance, a publicly available dataset of bicycle journey data contains information on unique customer identifiers, locations, and journey timestamps. By overlapping the data with Facebook, Twitter, or Foursquare check-ins, it is possible to identify and track the whereabouts of specific individuals. The same issue is applicable when you have live surveillance of the city.
The security of a smart city very much depends on two key factors—the limitations of the technologies used (e.g. computing power of devices) and how they are implemented (e.g. level of encryption.) If these factors are set aside in the development of a smart city, it gives attackers an opening.
As previously discussed in our smart homes series, attackers have different motivations for launching attacks on connected systems. Given how much more they can gain or damage, it is more likely for them to target a smart city’s critical sectors than they would individual homes.
Threat actors normally follow these steps when launching their attacks:
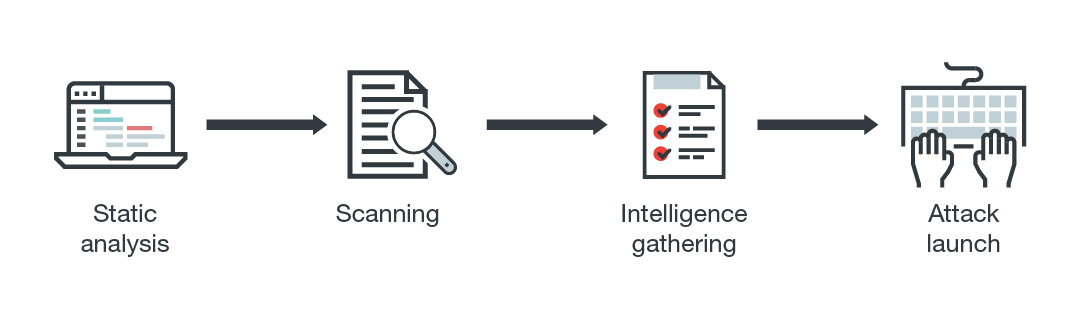
- Step 1: Static analysis: Using publicly available firmware, codes, and apps, they do a static analysis of devices and systems and see what vulnerabilities can be exploited.
- Step 2: Scanning: Attackers do a scan of exposed systems and devices within the smart city so they can identify their targets or points of entry.
- Step 3: Intelligence gathering: They gather any relevant information such as access credentials via phishing, data mining, and other means.
- Step 4: Attack launch: Once attackers have all the components they need, they can perform several kinds of attacks. They can, for example, manipulate codes and processes, infect systems with malware, brick devices, and so on
Knowing these steps, we shall be discussing how cities can deter these threats and implement safe and secure technologies in the final segment of this series.
10-Step Cybersecurity Checklist for Smart Cities
While studying the security concerns of smart cities, we have noted how the absence of well-defined standards and regulations, can turn projected benefits into unforeseen problems. In order to guide smart city developers, we have come up with a quick 10-step cybersecurity checklist they can refer to when implementing smart technologies.10-Step Cybersecurity Checklist for Smart Cities

We have already discussed how smart cities are being designed to fit the culture and needs of citizens worldwide. We have also delved into how smart technology implementations in critical sectors can be attacked. We have also learned how the absence of well-defined security standards and regulations, can turn projected benefits into unforeseen problems.
In order to guide smart city developers, we have come up with a quick 10-step cybersecurity checklist they can refer to when implementing smart technologies.
-
Perform quality inspection and penetration testing
Smart technologies have to undergo strict inspection and testing before any kind of city-wide implementation. This step allows the implementing body to catch any security issues (e.g. data leaks) or maintenance concerns (e.g. service malfunctions) before any smart device, infrastructure, or service is made available to the public.
Municipalities should hire independent contractors to run penetration tests on a regular basis. Since penetration testing only puts emphasis on vulnerability scanning, standard product testing procedures such as quality assurance (QA) or quality testing (QT) should also be mandatory. QA focuses on spotting defects in smart technologies, while QT zooms in on their functionality.
-
Prioritize security in SLAs for all vendors and service providers
Smart city adopters should draft service level agreements (SLAs) that list the security criteria smart technology vendors and service providers need to meet. It should be clear to both parties that non-compliance to the specified conditions has corresponding penalties. The criteria could include a guarantee on the data privacy of citizens, a 24x7 response team in case of problems, or the abovementioned regular penetration testing and security audits.
-
Establish a municipal CERT or CSIRT
When any security incident involving smart implementations arise, a dedicated municipal computer emergency response team (CERT) or computer security incident response team (CSIRT) should be readily available to respond. These teams need to be adept at performing appropriate countermeasures in case of attacks, or service recovery in case of system failures. These teams may also be in charge of vulnerability reporting and patching, vendor coordination, and sharing best security practices.
-
Ensure the consistency and security of software updates
Once software and firmware updates are available for the devices used in smart cities, they should be deployed immediately. Both municipalities and vendors must make sure that updates are delivered in a secure manner—with encryption and digital signatures—to ensure software integrity. Digital signatures are used to verify if the updates are authentic and not corrupted or tampered with before installation.
-
Plan around the life cycle of smart infrastructures
Smart infrastructures have longer service life than of the run-of-the-mill consumer products. However, it is important that municipalities create detailed procedures they need to take once the infrastructure becomes obsolete and vendor support for it ends. End-of-support may lead to serious vulnerabilities that can be exploited and attacked.
Smart city adopters should also consider the physical state of these infrastructures. Years of deployment, lack of maintenance, and overuse can wear them out. By planning around an infrastructure’s life cycle, it will be easier for municipalities to fix or replace them in the future.
-
Process data with privacy in mind
As a rule of thumb, any data collected in a smart city should be anonymized in order to protect the privacy of citizens, especially if it’s going to be published as open government data (OGD). If any portions of the dataset have no relevance to smart city projects, they should be completely discarded.
Access to sensitive data should be restricted to only those accredited by the municipality, such as service providers who are bound by SLAs. A clear information-sharing plan should be in place. This should cover what data can be shared, to whom, and what privacy controls will be implemented for the data. The plan must also include data backup provisions and a recovery strategy in case of disasters.
-
Encrypt, authenticate, and regulate public communication channels
All communications—both wired and wireless—should be protected against eavesdropping, interception, and modification, especially if the data contains sensitive information. Strong cryptography should be in place while encryption keys should also be well-kept and protected.
All smart communication systems should at least require a username and password to be accessed. Strong authentication mechanisms such as one-time passwords, biometrics, and two- or multi-factor authentication can be adopted to enhance security.
Municipalities should also regulate communication protocols and traffic to decrease the risk of knocking a centralized system or several interconnected devices offline. Unnecessary functions and features on smart communication systems should be disabled. This limits their attack surface and deters attackers from abusing them.
-
Always have a manual override ready
Despite the allure of fully automated smart systems, keeping the ability of a manual override is still very important. In case of a serious system malfunction or compromise by a malicious actor, the manual override offers municipalities the ability to perform incident response regardless if there is no internet connection or if the attacker locks out their remote access capabilities.
-
Design a fault-tolerant system
When smart infrastructures and applications continue to operate properly even if one or more of its components fail, you have a fault-tolerant system. Smart city services may experience reduced response or performance, but the system ensures continued functionality rather than failing completely. This will require redundancy techniques (hardware, software, and time) to tolerate operational faults and perform needed functions.
-
Ensure the continuity of basic services
In the unfortunate scenario where all systems fail, citizens should always have access to basic utilities (e.g. electricity, water) and services (e.g. emergency response). If the primary electric delivery system fails, for example, there has to be an alternative source of power.
Cities will get smarter over time. This is inevitable as governments slowly move towards techno-utopianism. Whether these cities are built from the ground up or built around and over established metropolises, it is always important to balance functionality with security. Cities are created by citizens to meet the needs of its citizens. It’s only right to protect them.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One