Narrowed Sights, Bigger Payoffs: Ransomware in 2019
by Janus Agcaoili and Miguel Ang
The ransomware threat has been present for years, evolving to try and outpace new security solutions and profit from compromised victims. This evolution continues into 2019: New data shows that the volume of threats seem to have dropped, and the scope of targets has changed. Malware creators have adopted new evasion tactics, refined their objectives, and are experimenting with new distribution methods.
With these new techniques come real costs for victims — ransom payment, repair and restoration, and mitigation costs. In such a volatile threat landscape, what should stay constant are the safeguards against all forms of ransomware. Being aware of new developments, finding the right security, and staying prepared are essential as ransomware continues to be a serious danger to users and enterprises across the world.
What has changed?
Ransomware has typically been spread through spam emails, with other popular distribution methods being malicious URLs hosting ransomware and exploit kits. The main goal was quantity — malware distributors wanted to find the easiest and fastest way to infect as many as possible. But in recent years, cybercriminals have taken a different approach. In 2017, the most infamous and widely spread ransomware, WannaCry and Petya, used the exploit EternalBlue to spread.
In 2019, the use of spam and exploits continues; but attacks have taken a more targeted approach. Unlike with WannaCry, the current ransomware families are targeting and spreading through local networks rather than over the internet. It appears that cybercriminals are aiming for higher-value targets, focusing their efforts on finding a victim and moving laterally through its network. Attackers might deploy RDP brute-force attacks, or leverage an already compromised system to try and look for a valuable target such as the domain controller, and then spread from there.
According to some news outlets, these recent ransomware attacks have had higher payouts per victim, and this is probably because the nature of newer attacks is to infect as many endpoints of a victim as possible. This causes a much bigger disruption for targeted enterprises, motivating them to pay the ransom.
Here are some recent ransomware, and their notable elements:
|
|
Unique techniques and tactics used in 2019 |
Enterprise impact |
|
It was seen introduced into the system via remote code execution of CMD or the system administration tool PsExec, indicating that the attacker was performing lateral movement in the system and perhaps looking for a high-value target in the network.
|
LockerGoga hit a series of industrial and manufacturing firms, disrupting operations on a massive scale. |
|
|
It was seen being spread via a compromised active directory in the network and may have been the result of a previous infection. The attacker may have intentionally targeted the active directory to spread the ransomware, a tactic not typically seen in ransomware attacks.
|
The Clop ransomware claimed to target entire networks instead of individual devices. |
|
|
Reports show that this ransomware spreads via a compromised domain controller within the victim’s network. It drops a core ransomware, a batch file (launcher), and a renamed PsExec (for remote execution) on other computers on the network. It then tries to execute on the infected machines.
|
Researchers saw a spike in MegaCortex activity early in May. The ransomware was detected targeting large enterprises networks. |
|
|
Security researchers observed that hackers were able to compromise an enterprise host and gain access to the domain controller. Through this access, they used the enterprise’s systems management software to spread GandCrab across the network.
|
The GandCrab operators claimed to have earned around US$2 billion from ransomware payments; and with their “success” the team behind the ransomware also announced that they are retiring.
|
|
|
|
The malware TrickBot was used for lateral movement via the EternalBlue vulnerability and harvested credentials, and the attackers were able to deploy the Ryuk ransomware to as many machines as possible. Another incident shows how attackers gained administrative access and used Powershell to move laterally to infect targets.
|
The FBI revealed that over 100 enterprises have suffered from Ryuk attacks since 2018, mostly logistics and technology companies and small municipalities. |
Table 1. Techniques and impact of 2019 ransomware
Aside from the notable tactics above, these strains of ransomware have also been implementing different techniques to try and evade security solutions. Clop, MegaCortex, and some versions of LockerGoga are digitally signed using valid certificates — giving them a veil of legitimacy and allowing them to enter and operate on some systems. This also indicates that there was a previous compromise or some organizations lost access to their signing keys.
Another technique, used by LockerGoga and MegaCortex, is making use of instance-based encryption. The malware spawns a child process to do the encryption for a limited number of files then terminates and repeats the process. This technique could be a defense mechanism against certain security solutions that might terminate the child process and a way to leave the core ransomware running and able to spawn another child process for the encryption routine.
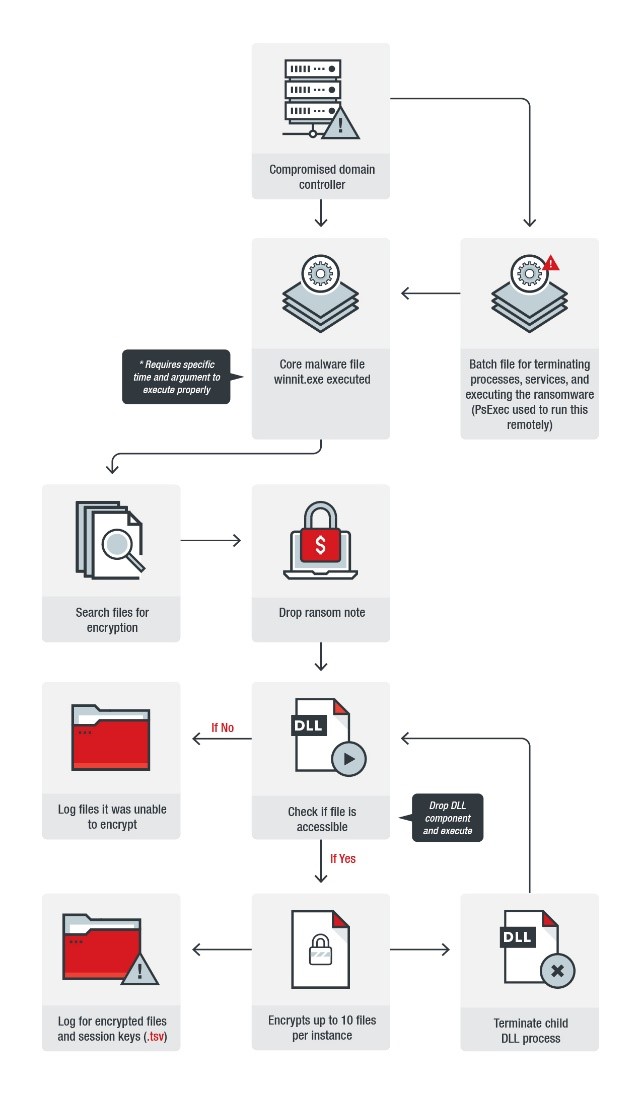
Figure 1. MegaCortex infection chain
Ransomware in numbers from 2016-2019
Ransomware data collected from 2016 to 2019 shows how ransomware has changed. Broadly, the number of new families has been on the decline but the number of threats seems to be picking up pace again. However, the details of the ransomware families, as well as new techniques that they have been using, present a clearer picture of ransomware in 2019.
|
Overall ransomware threats |
|
|
2016 |
1,078,091,703 |
|
2017 |
631,128,278 |
|
2018 |
55,470,005 |
|
2019 (Jan to Apr) |
40,916,812 |
Table 2. Ransomware threat detections from 2016 to early 2019
Total ransomware threat detections in the first four months of 2019 is almost equal to the total for 2018. A possible reason for the acceleration is that current ransomware is more effective in infecting endpoints as compared to 2018. As discussed above, current ransomware incidents show that cybercriminals are deploying targeted ransomware: They try and attack large enterprises and gain access to the local network. Once in, they try to spread their payload to all connected endpoints. In the past, the ransomware might not have been as successful. In 2018, with increased awareness of the threat and users implementing better security solutions, ransomware might not have gotten past the download stage. Malicious documents from email attachments were likely detected and then blocked.
|
|
New families |
|
2016 |
247 |
|
2017 |
327 |
|
2018 |
222 |
|
2019 (Jan to Apr) |
40 |
Table 3. Comparison of new ransomware families detected from 2016 to early 2019
At the time of writing, there were 40 new ransomware families found in the first four months of 2019. As the year progresses, we might be seeing these families adopt techniques leveraged by widespread ransomware like GandCrab, Clop, LockerGoga, and MegaCortex.
How to defend against ransomware
Ransomware is a recognized and well-studied threat, so there are several known best practices that businesses and users can adopt to better protect themselves: Regularly back up files, keep the system and applications updated, enforce the principle of least privilege, and implement defense in depth, that is, arraying security at each online perimeter, from gateways, networks, endpoints, and servers.
The new tactics being used by ransomware in 2019 are more sophisticated and may need more advanced security solutions. Ransomware like Ryuk, MegaCortex, and GandCrab, which abuse regularly used tools and applications within enterprise networks, can be detected and blocked by deploying a behavior monitoring mechanism on endpoints. This helps prevent and limit data leakage and malware infection by monitoring and blocking malicious behaviors and routines associated with malware, as well as unusual modifications to the OS or software/applications. A good behavior monitoring system looks not only into an application’s behaviors but also anomalies in the process chain, like how Explorer launches Command Prompt to invoke a malicious PowerShell script.
Trend Micro ransomware solutions
Enterprises can benefit from a multilayered approach to best mitigate the risks brought by ransomware. At the endpoint level, Trend Micro™ Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimize the impact of this threat. Trend Micro Deep Discovery™ Inspector detects and blocks ransomware on networks, while the Trend Micro Deep Security™ platform stops ransomware from reaching enterprise servers — whether physical, virtual, or in the cloud. Trend Micro Deep Security, Vulnerability Protection, and TippingPoint provide virtual patching that protects endpoints from threats that exploit unpatched vulnerabilities to deliver ransomware.
Email and web gateway solutions such as Trend Micro Deep Discovery Email Inspector and InterScan™ Web Security prevent ransomware from ever reaching end users. Trend Micro’s Cloud App Security (CAS) can help enhance the security of Office 365 apps and other cloud services by using cutting-edge sandbox malware analysis for ransomware and other advanced threats.
These solutions are powered by Trend Micro XGen™ security, which provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints. Smart, optimized, and connected, XGen powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One