
Learn more about zero trust:
- ZTNA vs VPN: Secure Remote Work and Access
- What is Secure Web Gateway’s (SWG) Role in Zero Trust?
- Reduce SaaS App Risks with Cloud Security Broker & Zero Trust
- Data Exfiltration Prevention with Zero Trust
With the massive shift in how we work and connect to work most organizations turned to their VPN solution to secure remote users connecting to corporate apps and resources.
Alongside this work transformation, digital transformations continued to move resources to cloud locations, and adoption of SaaS applications to remove infrastructure management all together. With these changes, it quickly became clear that VPN solutions were falling short with issues of performance, user experience, availability, and flexibility becoming ever more impactful.
These limitations are further compounded with the emphasis on implementing zero trust models to secure the ever-expanding attack surface.
Enter the explosion of interest in service edges, especially around Secure Access Service Edge (SASE) capabilities, where Zero Trust Network Access (ZTNA), Secure Web Gateway (SWG), and Cloud Access Security Broker (CASB) capabilities combine for a powerful solution to deliver security in this changing world.
What is SASE?
Pronounced “sassy”, SASE is designed to provide secure access to applications and data based on a strong identity. Built on the principles of zero trust, SASE includes capabilities from two discrete areas – network (SD-WAN, VPN) and security (SWG, CASB, FWaaS, ZTNA) – covering the underlying network infrastructure and the application of network security as a layer across this infrastructure.
While both areas are important considerations, they are often addressed separately as each should operate independently of the other in terms of implementation and outcomes.
Why SASE?
What started out as a temporary business solution to the pandemic is here to stay. ESG’s 2021 SASE Trends report found that 62% of respondents will work remotely or in a hybrid manner. To support this “new normal,” enterprises have adopted the cloud in staggering numbers—98% of respondents stated they use public cloud services.
Now, CISOs and security leaders are tasked with securing a growing attack surface in complex, distributed network environments. Users require secure connections and access to critical apps hosted in various private and public networks to meet business needs—whenever, wherever. Such scalability demands from remote workers has caused organizations to adopt a zero-trust approach to identity-based access via SASE architecture.
And, according to ESG’s report, early implementors of SASE have reported overwhelmingly positive results, including:
- Faster network or security problem resolution
- Reduced security solution costs
- Ease of management
- Better alignment of network and security policies
- Fewer security incidents
SASE Core Elements
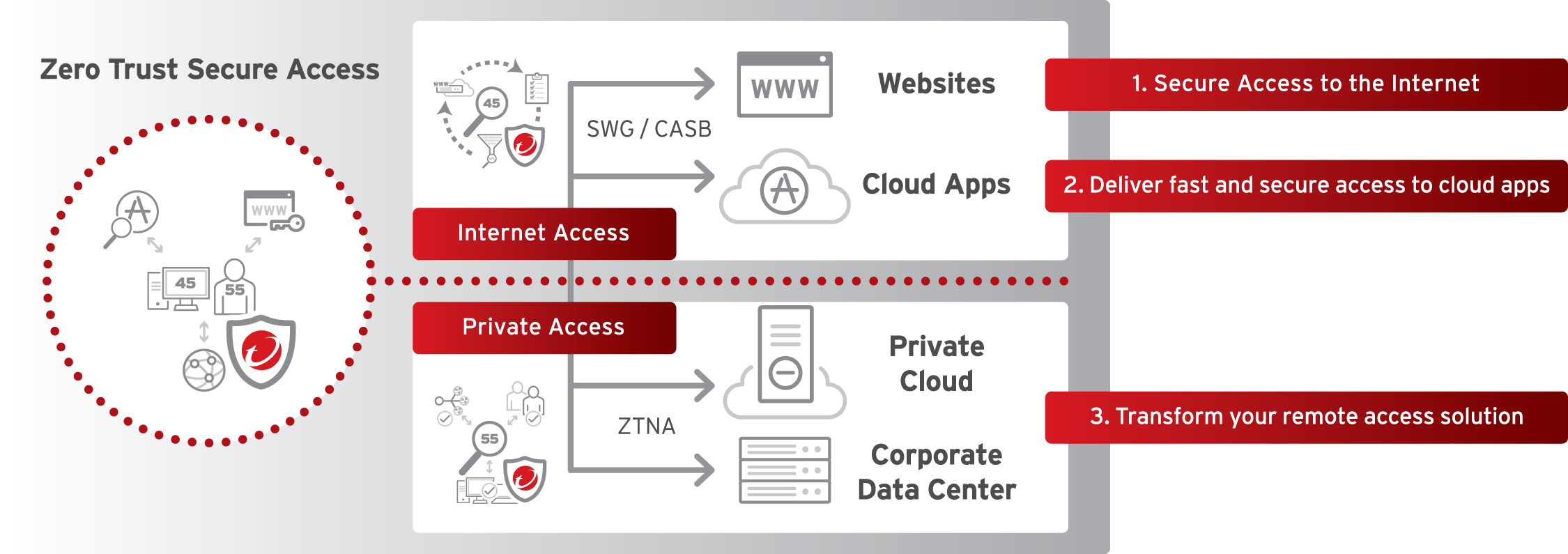
Zero Trust Network Access (ZTNA)
Amongst the core elements of the SASE architecture is ZTNA, which follows the motto “never trust, always verify” or “assume breach” by authenticating and verifying all access requests and continuing to monitor the user or device for suspicious behavior.
ZTNA gateways are largely considered a superior solution to VPN for connectivity flexibility, performance, and granular security control. In fact, 62% of respondents in ESG’s report said they’re actively expanding/planning to expand their ZTNA usage to move away from VPN.
Secure Web Gateway (SWG)
Businesses are often faced with the challenge of blocking threats without negatively impacting device performance and user productivity. SWG solutions address this by preventing unsecured internet traffic from entering an internal network of an organization using a sophisticated blend of URL filtering, SSL/TLS inspection, and other threat defenses.
Typically, a SWG is running independently of other products in the security stack but integrating the solution within a SASE architecture allows for automated access decision making, rich telemetry, and reporting visibility alongside simple and consistent policy control.
Cloud access security broker (CASB)
While it’s become the norm for organizations to rely on public cloud apps to drive their day-to-day operations, security challenges remain. Most notably, lack of visibility and control across the digital attack surface, which can lead to exfiltration of sensitive data from business-critical SaaS apps. CASB solutions address these issues by sitting between the user and cloud, auto-monitoring and assessing risk, and applying security policies through APIs.
When integrated within the SASE architecture, CASB can provide more granular protection that goes beyond the SWGs’ capabilities of blocking apps or traffic. When added to the underlying SWG, CASB can determine if traffic is risky or malicious, discover traffic flows between users and apps, and implement deeper controls from the SWG if potential risk is surfaced.
How to implement SASE
Convergence is key to successfully apply the SASE architecture principles. While ZTNA, SWG, and CASB solutions can function on their own, integrating them leads to more streamlined, powerful security across the digital attack surface.
Implementing SASE can seem overwhelming; consider starting with these three steps to ease your journey:
1. Create a SASE strategy. It’s not all about converging technologies; ESG found the biggest challenge when implementing SASE to be getting cross-functional teams to agree on a strategy and vendor. To remove strategic barriers, Gartner suggests establishing a joint network and security team to establish the overall strategy, adoption timeline, and SMART goals.
2. Discover and assess infrastructure and skills gaps. Adopting SASE doesn’t mean you have to clean house; by discovering and assessing existing network infrastructure and resources, you can identify what can stay and what net new solutions are needed for your edge. Make sure you have the personnel to execute and manage SASE deployment or explore using a managed service to augment resources.
3. Choose the right SASE vendors and solutions. According to Gartner, the limited number of comprehensive SASE offerings and lack of security services capability maturity can hinder SASE implementation. Look for a partner who understands you may want to diversify your security stack—their security offerings should be internally integrated but also play nicely with robust third-party integration, ensuring you’ll have the most comprehensive visibility across the attack surface.
Next steps
Learn more about Trend Micro™ Zero Trust Secure Access



