Oracle Java 7 Security Manager Bypass Vulnerability (CVE-2013-0422)
DESCRIPTION
A remote code execution vulnerability exists in the following versions of Java:
- Java Development Kit 7 Update 10 and earlier
- Java Runtime Environment 7 Update 10 and earlier
The vulnerability allows attackers to remotely execute arbitrary code in a vulnerable system. To exploit this vulnerability, an attacker must lure users to access a compromised website or a malicious webpage, where a malicious Java applet targeting the vulnerability is hosted. The execution of the malicious applet within the browser of the unsuspecting user then allows the attacker to execute arbitrary code in the vulnerable system. Users with vulnerable systems may find themselves infected with ransomware, which Trend Micro detects as TROJ_REVETON.RJ and TROJ_REVETON.RG. Exposure to such malware may result in financial loss.
Note that Java Development Kit and Java Runtime Environment versions 6, 5.0 and 1.4.2, and Java Standard Edition Embedded JRE releases are not affected by this vulnerability.
TREND MICRO PROTECTION INFORMATION
It is strongly advised to download Java's latest update, which patches the vulnerability targeted by this attack. The patch increments the latest version of Java 7 to Update 11, and may be downloaded from the official Java website.
Java may be part of some applications that you are using regularly. If you must use Java, some useful tips are available on using Java safely.
If you need to disable Java, you may perform the following steps:
Disabling Java in Internet Explorer:
To prevent any Java app, signed or unsigned, from running in Internet Explorer:
- Open the Java Control Panel. IE users can do this by clicking Start, then clicking on the Control Panel option.
- Look for the Java icon to open the Java Control Panel. You can use the Search field to make this easier.
- Double-click the Java icon. This brings up the Java Control Panel.
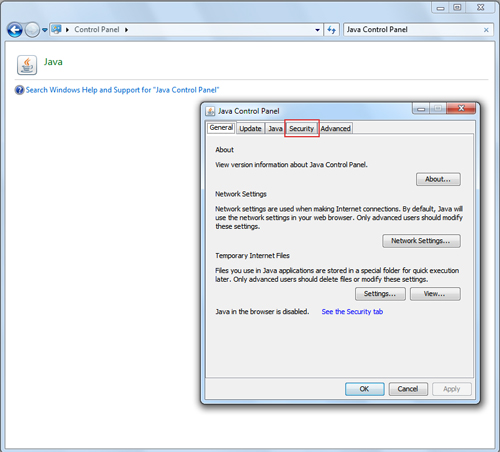
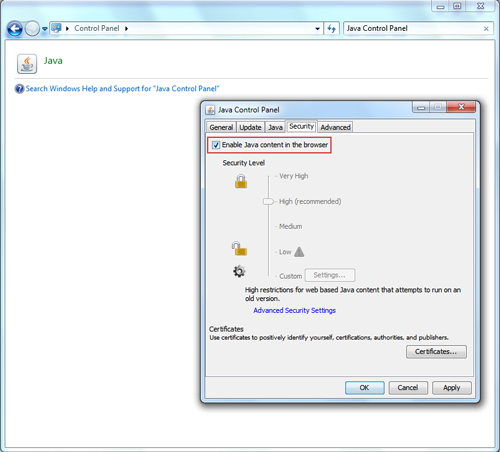
- In the Java Control Panel, go to the Security tab.�
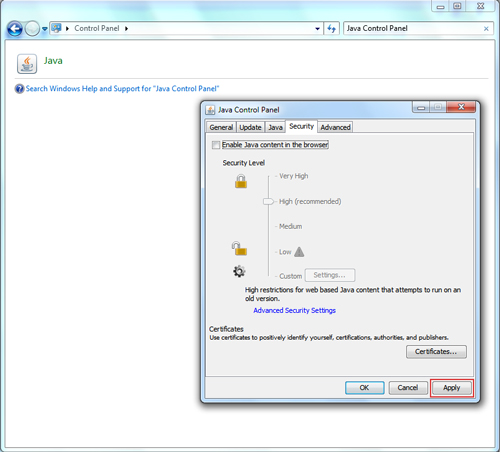
- In the Security tab, un-check the Enable Java content in the browser. This option disables the Java plug-in from running in your browser.
- Click Apply. When the Windows User Account Control (UAC) dialog appears, allow permissions to make the changes.
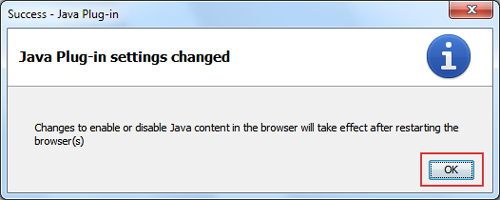
- Click OK in the Java Plug-in confirmation window.
- Restart Internet Explorer for the changes to take effect.
Find out how to open the Java Control Panel, which varies depending on your operating system and browser, through this Oracle page.
Setting the Security Level of Unsigned Apps
A security level has been added to the Java Control Panel, accessible through its Security tab. This enables you to control the browser's behavior when it attempts to run unsigned apps. You can select Low, Medium, High or Very High security settings.
The default security level is High, where you are prompted before an unsigned Java app runs in the browser. You are given an option to update Java first if it is below the security baseline.
You may also choose to let unsigned apps to not run by setting the slider to Very High.
Trend Micro Solutions
Trend Micro Deep Security shields networks through the following Deep Packet Inspection (DPI) rules. Trend Micro customers using OfficeScan with Intrusion Defense Firewall (IDF) plugin are also protected from attacks using these vulnerabilities.
| MS Bulletin ID | Vulnerability ID | DPI Rule Number | DPI Rule Name | Release Date | IDF Compatibility |
| CVE-2013-0422 | 1004771 | Identified Malicious Java JAR Files | 12-Jan-13 | YES | |
| 1005177 | Restrict Java Bytecode File (Jar/Class) Download | YES |
SOLUTION
AFFECTED SOFTWARE AND VERSION
- Java Development Kit Update 10 and earlier
- Java Runtime Environment Update 10 and earlier
Featured Stories
 Beware of MCP Hardcoded Credentials: A Perfect Target for Threat ActorsPoor secret management in MCP servers can lead to serious consequences, including data breaches and supply chain attacks. This article examines the reality of these unsecure configurations and offers practical recommendations that minimize the chances of exposure.Read more
Beware of MCP Hardcoded Credentials: A Perfect Target for Threat ActorsPoor secret management in MCP servers can lead to serious consequences, including data breaches and supply chain attacks. This article examines the reality of these unsecure configurations and offers practical recommendations that minimize the chances of exposure.Read more Lessons in Resilience from the Race to Patch SharePoint VulnerabilitiesIn this article, Trend Micro discusses how the fast-moving attacks using CVE-2025-53770 and CVE-2025-53771 have underscored the essential role of virtual patching and reliable intelligence in protecting organizations against evolving threats.Read more
Lessons in Resilience from the Race to Patch SharePoint VulnerabilitiesIn this article, Trend Micro discusses how the fast-moving attacks using CVE-2025-53770 and CVE-2025-53771 have underscored the essential role of virtual patching and reliable intelligence in protecting organizations against evolving threats.Read more Unveiling AI Agent Vulnerabilities Part V: Securing LLM ServicesTo conclude our series on agentic AI, this article examines emerging vulnerabilities that threaten AI agents, focusing on providing proactive security recommendations on areas such as code execution, data exfiltration, and database access.Read more
Unveiling AI Agent Vulnerabilities Part V: Securing LLM ServicesTo conclude our series on agentic AI, this article examines emerging vulnerabilities that threaten AI agents, focusing on providing proactive security recommendations on areas such as code execution, data exfiltration, and database access.Read more Unveiling AI Agent Vulnerabilities Part IV: Database Access VulnerabilitiesHow can attackers exploit weaknesses in database-enabled AI agents? This research explores how SQL generation vulnerabilities, stored prompt injection, and vector store poisoning can be weaponized by attackers for fraudulent activities.Read more
Unveiling AI Agent Vulnerabilities Part IV: Database Access VulnerabilitiesHow can attackers exploit weaknesses in database-enabled AI agents? This research explores how SQL generation vulnerabilities, stored prompt injection, and vector store poisoning can be weaponized by attackers for fraudulent activities.Read more
