By the Numbers: Are Your Smart Home Devices Being Used as Cryptocurrency Miners?
Most people are familiar with malware that encrypt files for ransom or attempts to steal information, but now cybercriminals are devoting resources to directly chasing cryptocurrency. This way, they can bypass any obstacles and directly go for a decentralized—and rapidly appreciating—currency that guarantees anonymity.
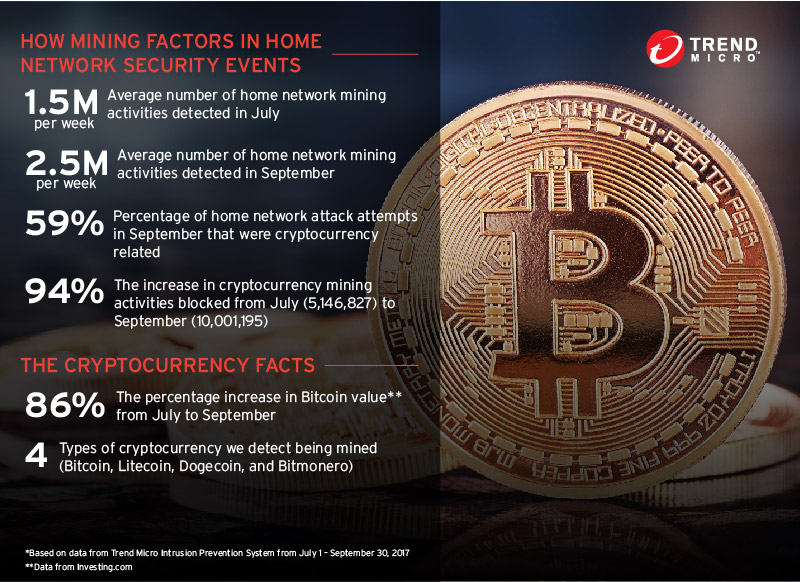
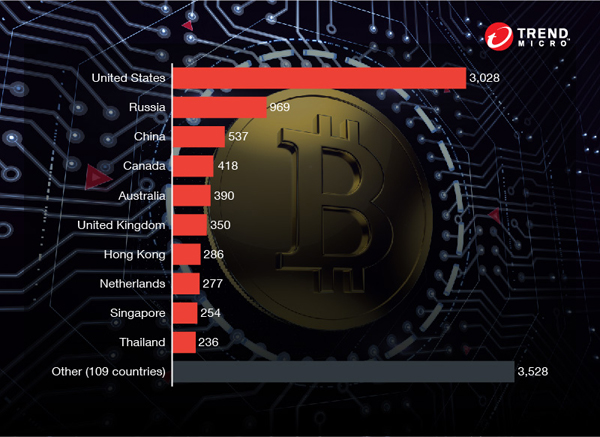
Trend Micro data shows that more and more home devices are being compromised—in fact, we detected over 90% more home network mining activities in September compared to July. Historically, compromised devices are comprised of unsecured Internet of Things (IoT) devices that can become part of botnets that can be used for distributed denial-of-service attacks. Now, these devices, which include home routers, IP cameras, and even smartphones, are being turned into cryptocurrency miners.
Often the owners aren’t even aware that their devices have been compromised. A slight performance lag may be the only hint that the device is being used to line criminals’ pockets.
The rising trend of cryptocurrency mining malware
Bitcoin value has seen a meteoric rise over the past few months, from a value of roughly US$1,000 in April to over $4000 at the time of writing. A number of cybercriminal attempts to mine cryptocurrency were discovered around the time the currency started to appreciate. One example used the known cryptocurrency mining malware RETADUP. It first hit South America in May 2017 and attacks are still ongoing. The collective computing power from the infected machines, and the rising value of cryptocurrencies, allow for significant profits. In August 2017, we saw a cryptocurrency miner using the same exploit used in the WannaCry and Petya outbreaks to spread filelessly.
[READ: Security 101: The Impact of Cryptocurrency-Mining Malware]
As many have noted, it takes a huge amount of power and resources to mine cryptocurrency, and the rising value will only motivate attackers to pursue it directly using more aggressive means. With attacks like ransomware, criminals only receive the amount that the victim is able or willing to pay. Mining cuts out the middleman and allows them to take the profit directly.
How do Bitcoin Miners Arrive in the Home?
Most IoT devices are known to be vulnerable to a range of malware types. Most famously, the malware
Mirai compromised millions of IoT devices (mostly home devices), creating the largest botnet ever recorded. A new variant with mining capabilities began to spread in April 2017.
[READ: Protecting Home Networks: Start by Securing the Router]
Unsecured home routers are typically used as the malware's entry point into a network. Most of the smart devices are connected to your router, and as such the router becomes the “doorway” to your home. If the router is compromised, the other devices connected to it could easily be compromised and turned into bots used to mine cryptocurrency.
Typically these routers come with default credentials (usernames and passwords) that are easily bypassed. The first step is to change the default credentials and use more complicated passwords. Here are other tips:
- Update your device with the latest patches so that they are protected against the latest vulnerabilities
- Enable the device’s firewall (for home routers), or deploy intrusion detection and prevention systems to mitigate incursion attempts
- Use available security solutions to protect your router
As cryptocurrency miners creep into the home, more and more smart devices are turned into unwilling accomplices. Cybercriminals steal resources to fund their operations or simply get rich. As the currency continues to gain legitimacy and rise in value, we should expect cybercriminals to ramp up their mining activities. To better protect users from IoT malware and similar threats, the Trend Micro™ Smart Home Network solution features web protection and deep packet inspection capabilities.
October 27, 2017 4:50PM
Updated image with the latest data from Trend Micro Intrusion Prevention System
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One