 Download Uncovering DRBControl: Inside the Cyberespionage Campaign Targeting Gambling Operations
Download Uncovering DRBControl: Inside the Cyberespionage Campaign Targeting Gambling Operations
In 2019, Talent-Jump Technologies, Inc. reached out to Trend Micro about a backdoor they discovered during an incident response operation. We provided further intelligence and analysis on the backdoor, which we learned was being used by an advanced persistent threat (APT) actor that we dubbed "DRBControl." The threat actor is currently targeting users in Southeast Asia, particularly gambling and betting companies. Europe and the Middle East were also reported to us as being targeted, but we could not confirm this at the time of writing. Exfiltrated data was mostly comprised of databases and source codes, which led us to believe that the group's main purpose is cyberespionage.
The campaign uses two previously unidentified backdoors. Known malware families such as PlugX and the HyperBro backdoor, as well as custom post-exploitation tools were also found in the attacker's arsenal. Interestingly, one of the backdoors used file hosting service Dropbox as its command-and-control (C&C) channel. We disclosed our findings to Dropbox, which expired the tokens used in the campaign in August 2019 and has since been working with Trend Micro on the issues.
OPERATION DRBCONTROL
A newly identified threat actor behind a cyberespionage campaign targets gambling and betting entities by using publicly available and custom tools to elevate privileges and perform lateral movements. One of the deployed malware uses Dropbox as a way to communicate and exfiltrate data from targets.
Targets
DRBControl targets gambling and betting operations in Southeast Asia.
GAMBLING
BETTING
The threat actors behind the campaign use a variety of post-exploitation tools, such as a clipboard stealer, network traffic tunnel, brute-force tool, and password dumpers.
Operations
The first-stage intrusion uses spear-phishing .DOCX files. DRBControl distributes three versions of the infecting documents.
- The campaign primarily takes advantage of two backdoors, both of which use DLL side-loading through the Microsoft-signed MSMpEng.exe file.
- The type 1 backdoor already has nine versions, all developed between May to October 2019. All versions use the file hosting service Dropbox as their C&C channel.
- The type 2 backdoor uses a configuration file that has the C&C domain and connection port, as well as the directory and filename where the malware is copied. The file also sets its persistence mechanism.
- In most cases, IP addresses could be resolved only for subdomains hardcoded in malware samples; no IP address was linked to the domain names themselves.
- Known malware families (e.g., PlugX RAT, Trochilus RAT, and HyperBro backdoor) and software Cobalt Strike were also utilized in the campaign.
Network Activities
Connections with Other APT Campaigns
Different malware identified with Winnti and Emissary Panda campaigns. Links to the Winnti group range from mutexes to domain names and issued commands. The HyperBro backdoor, which appears to be exclusive to Emissary Panda, was also used in this campaign.
Key Findings:
- The earliest documented spear-phishing activity against targets was identified in May 2019. The attack targets organizations' support teams.
- The campaign has several relations to well-known APT groups Winnti and Emissary Panda, whose previously observed campaigns involved self-developed tools and espionage targets.
- The cyberespionage campaign appears to be targeting gambling and betting companies. It utilizes newly identified backdoors, one of which allowed the perpetrators to use multiple Dropbox repositories for harvested information.
The DRBControl campaign attacks its targets using a variety of malware and techniques that coincide with those used in other known cyberespionage campaigns. The threat actors maintain a diverse infrastructure and take advantage of post-exploitation tools to further their operations.
The campaign not only uses file hosting service Dropbox as its C&C channel, but also for the delivery of different payloads. Dropbox repositories were also found to store information such as commands and post-exploitation tools, target user's workstation information, and stolen files.
Clipboard stealer
EarthWorm network traffic tunnel
Public IP address retriever
NBTScan tool
Brute-force tool
Elevation of privilege vulnerability tool
Password dumpers
UAC bypass tools
Elevation of privilege vulnerability tool
Password dumpers
UAC bypass tools
Code loaders
Post-exploitation tools used by DRBControl
Conclusion
Unlike largely indiscriminate attacks that focus on typical forms of cybercrime, targeted attacks differ in terms of how threat actors actively pursue and compromise specific targets (i.e., through spear phishing) for lateral movement in the network and sensitive information extraction. Understanding attack tools, techniques, and infrastructure, as well as the links to similar attack campaigns, provides the context necessary to assess potential impact and adopt defensive measures. Trend Micro users can thwart advanced persistent threats with security that provide actionable threat intelligence, network-wide visibility, and timely threat protection.
Read our detailed findings in our research paper, "Uncovering DRBControl: Inside the Cyberespionage Campaign Targeting Gambling Operations," which looks into the malware that DRBControl uses, its relations to known APT groups, other noteworthy points of their activities, and indicators of compromise.
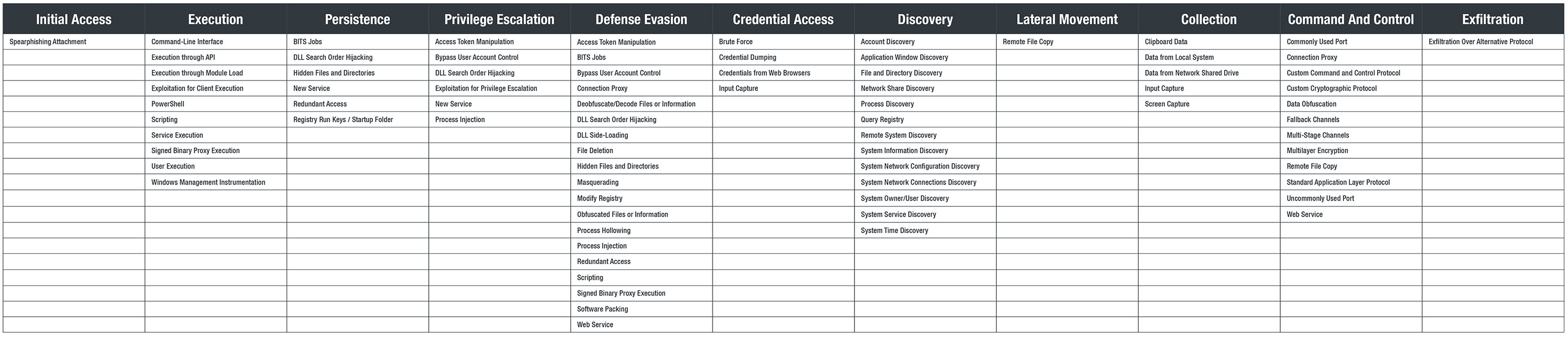
MITRE ATT&CK Matrix

Download Uncovering DRBControl:
Inside the Cyberespionage Campaign Targeting Gambling Operations
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One