The learning journey of a CISO—or any professional in cybersecurity—is never over. Every time you level up your skills, you see new possibilities for doing things faster, smarter, or more effectively. At the same time, the threat landscape is always changing, yet the need for risk visibility remains essential. The more of your attack surface you can see, the more vulnerabilities you discover. The more powerful your solutions and capabilities become, the more opportunities you have to protect your organization and outpace threat actors.
In other words, cybersecurity maturity is a never-ending journey. Even so, it follows a distinct progression from reactive “firefighting” towards increasingly proactive and strategic ways of managing risk. The questions posed in this blog are meant to help you figure out which stage of the cybersecurity journey you’re at today—and what you need to do to take the next step.
The three pillars of cybersecurity maturity
In general, each stage of cybersecurity maturity is determined by three things:
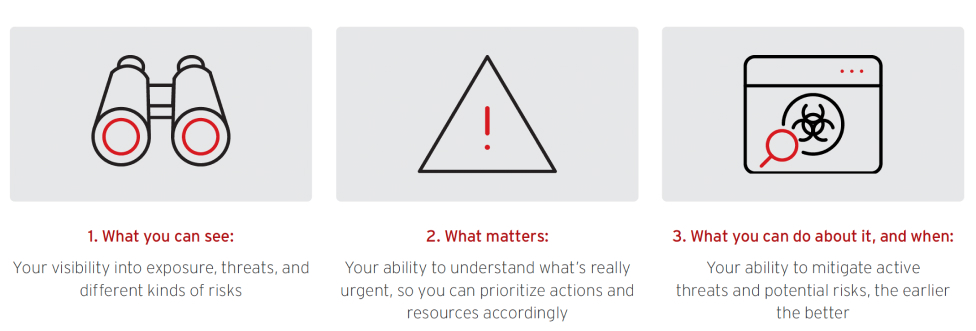
As organizations mature their cybersecurity, their capabilities related to each of these three pillars deepen and strengthen.
Stage one: Reactive mode
Virtually every organization starts off stuck playing whack-a-mole with threats as they break into the enterprise environment, responding to situations after the fact. Organizations in reactive mode have low visibility. They don’t have a complete handle on the assets and data they need to protect, they can’t see their complete attack surface in sufficient detail, and they don’t fully understand the threats they face. Because of these factors, their ability to prioritize and mitigate threats tends to be heavily constrained.
Here are some key indicators that you’re in reactive mode:
- Your security teams are overwhelmed by incidents and alerts
- You have too many tools serving up siloed data
- You manage IT assets with spreadsheets and your inventories are incomplete, out of date, or both
- You rely exclusively on common vulnerability and exposure (CVE) scores to decide what to patch
Stage two: Tactical mode
The first step out of reactive mode is start integrating security and IT workflows—increasing visibility and responsiveness by knocking down silos—and to adopt some way of prioritizing vulnerabilities and threats. In other words, it’s about getting a better handle on your attack surface.
While this is surely an improvement in terms of cybersecurity maturity, tactical mode is still largely reactive and slow-moving.
Here are some telltale indications that you’re in tactical mode:
- Security and IT have fewer silos, though they still exist
- Cybersecurity processes are still mostly manual
- Security patches still tend to be out of date, not caught up to the real-world threat landscape
- Prioritization isn’t consistent or based on any real assessment of risk, but instead on external measures like common vulnerability scoring
Stage three: Risk driven
As the term implies, the next major milestone in the cybersecurity maturity journey is to orient more of your overall approach towards identifying and addressing risk. In tandem with this—and because risk assessment is an intensive, continuous activity—you’ll need to increase automation within your security operations. Specifically, you’ll want solutions and capabilities that can give you a real-time view of attack surface conditions.
You’ve reached the risk-driven stage if you have:
- Risk-based security frameworks and prioritization approaches
- Automated cyber risk scoring and cyber risk quantification, which give objective measures of relative risk and the potential damage each risk could do
- Automated remediation
- Automated compliance management
Stage four: Proactive mode
The first two stages of cybersecurity maturity have a lot to do with increasing your visibility. Being risk-driven builds on those visibility gains to radically improve your ability to prioritize threats and cybersecurity activities.
Proactive mode consolidates all of the previous stages and emphasizes continuous mitigation. This means discovering and assessing risks, and taking strategic steps to minimize them—not only by dealing with threats and vulnerabilities but also by changing your attack surface conditions to reduce your exposure to risk. This gives you the ability to anticipate risks and address them preemptively before they can do any damage.
Here’s how to tell if you’re in proactive mode:
- Your protection measures are highly automated, taking advantage of machine learning and AI
- Your cybersecurity activities are aligned strategically with your business objectives
- Cybersecurity is part of risk management at the corporate board level
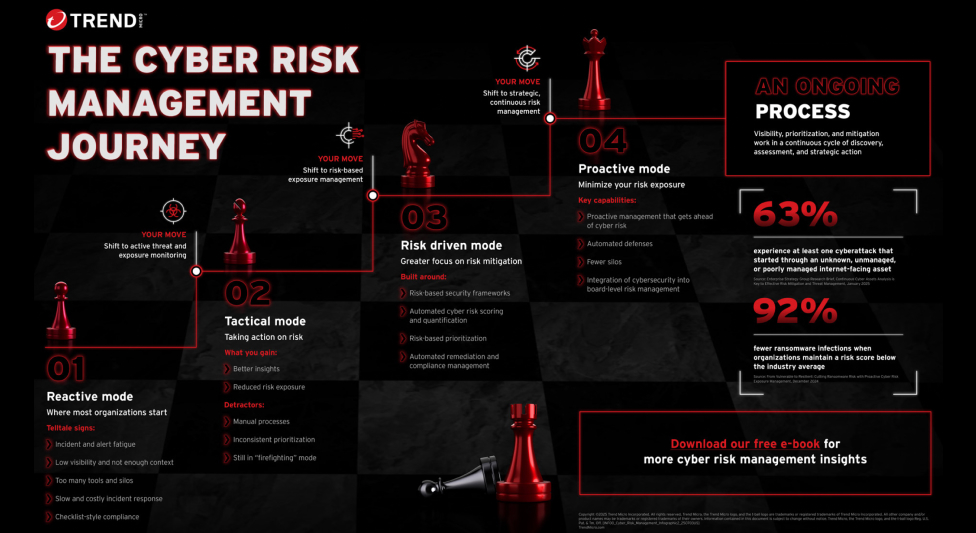
Cybersecurity maturity is a process
Because cybersecurity maturity is an ongoing journey, breaking it up into four neat stages is a little artificial. As an organization moves along the continuum, it’s likely that you’ll experience aspects of some stages occuring at the same time. That said, treating these stages as markers or milestones can help you make progress and gain more desired traits.
It’s also important to note that the more mature your cybersecurity approach becomes, the more continuous your risk management activities will be. That’s evident here and reflected as well in industry-leading frameworks like Gartner’s continuous threat exposure management (CTEM) program.
The other important takeaway is that it doesn’t matter where you’re starting in a cybersecurity maturity journey. What matters is leveraging a path that can lead you out of reactive mode and toward a more proactive, strategic way of managing cybersecurity risk.
Next steps
To continue your cybersecurity maturity learning journey, feel free to consult the following resources:

