Security teams face a number of pressing challenges. Take alert overload: in the 2023 State of Enterprise DFIR survey, 64% of respondents stated that alert and investigation fatigue contributed to their feeling stressed. An unsurprising statistic given that on average, SOC teams receive 4,484 alerts everyday (that’s one every 6.42 seconds in an eight-hour workday).
At the core of this issue is disconnected and inefficient threat detection and response solutions. Many security professionals will leverage a SIEM to collect logs and alerts from multiple, disparate security tools.
There are two issues that can arise: one, cyberattacks rarely stay in siloes and two, SIEMs are great at collecting data, but not all of them can effectively correlate that data. Hampered visibility and lack of context often leads to noisy false positives, which slow down investigative efforts. Help Net Security found that SOC teams spend nearly three hours manually triaging alerts.
Enter: extended detection and response (XDR).
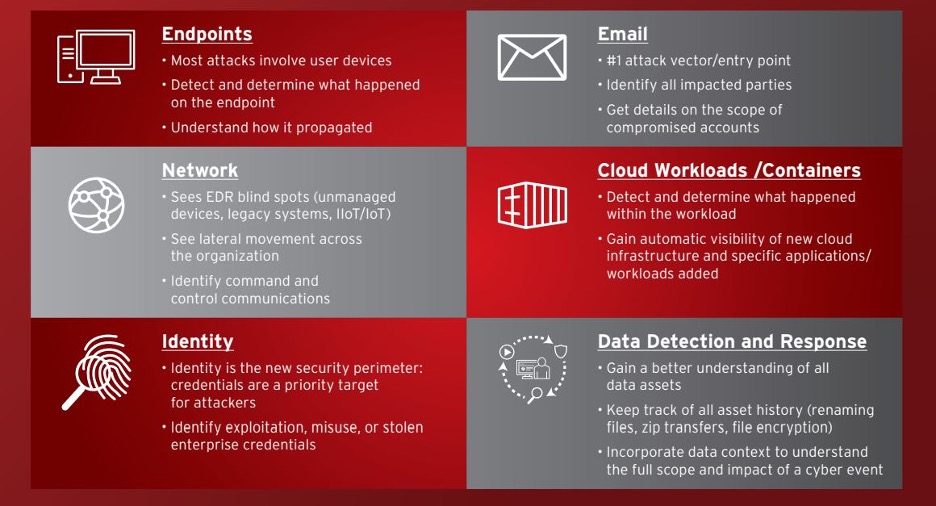
What is XDR?XDR is the evolution of endpoint detection and response (EDR). It goes beyond the single-layer EDR approach by collecting and correlating data in real-time across multiple security layers like email, server, cloud workload, network, and endpoint.
Correlating related activities to reduce high-confidence detections reduces the overwhelming volume of false positives and enables faster threat detection and response. ESG found organizations that adopted XDR experienced significant improvement in their overall security posture, ability to detect advanced threats, investigation times, and ability to keep up with alert volumes. Adopting and fine-tuning XDR capabilities improves security efficiency, streamlines security operations, and bolsters staff productivity.
Explore more SOC best practices: Steering Clear of Security Blind Spots
Taking the right XDR approachThe approach you take will depend on the needs of your organization. There is no one way to achieve an XDR capability, and not all XDR solutions or approaches are created equal. The three most common XDR approaches are:
- Native (Comprehensive): This approach leverages its own foundation for many of its data sources and manages the full XDR process within a single platform.
- Open: Delivers certain XDR capabilities via a collection of third-party integrations.
- Hybrid: Uses native sources in tandem with third-party and API integrations for correlated detection, integrated investigations, and multi-layer response.
Of the three, opt for a vendor with a strong foundation of native telemetry (i.e. telemetry from tools that they built) with a path forward for integrating your existing sources of telemetry. . Native XDR offers significant advantages in its ability to leverage deep activity data to optimize analytical models for correlated detection. While Open XDR has an advantage over Native in that it can collect data across a broader option of sources, in many cases it is only looking at alert data which limits the context it provides and analysis that can be done. Also, a vendor with robust detection models for security layers out of the box makes it easier for teams to get up and running and eliminates the complexity of configuring a product that relies heavily on third-party integrations.
Integrating investigations for greater detection effectiveness
The key is to unite third-party and API integrations with sensors deployed on email, server, cloud workloads, and network layers. Correlated detection provides the context needed to answer the following critical questions:
- How did the users or hosts become compromised?
- What was the first point of entry?
- What or who else is part of the same attack?
- Where did the threat originate?
- How did the threat spread?
- How many other users are potentially vulnerable to the same threat?
Not all threats originate at the endpoint. According to IBM Cost of a Data Breach Report 2023, phishing and stolen or compromised credentials were the two most common initial attack vectors. XDR should enable you to detect email threats, including compromised accounts sending internal phishing emails. Upon a detection, XDR should also sweep mailboxes to identify who else received the email, so that it can be quarantined or deleted to prevent the spread
Furthermore, network detection and response (NDR), fills EDR blind spots. Real time activity data collected on traffic flow and behaviors plus perimeter and lateral connections help analysts discover how the threat is communicating and moving across the network. With this knowledge, security professionals will be able to block the host and URL as well as disable the Active Directory account to limit the scope of an attack.
Cloud workloads, servers, and containers are critical to business operations, so monitoring activity at this layer is necessary to reduce critical incidents. XDR collects and correlates activity data such as user account activity, processes, executed commands, network connections, files created/accesses, and registry modifications to tell the entire story beyond the alert. This enables security teams to drill down into what happened within the cloud workload and how the attack propagated.
Operationalize threat intel from XDR
According to ESG’s SOC Modernization and the Role of XDR report, the top SOC initiative for 2022 was to “improve operationalization of threat intelligence.” Incorporating threat intel is an integral part of the SOC function in the face of increasingly sophisticated and successful cyberattacks. The more you can understand the attacker’s maneuvers and objectives, the more resilient and responsible an organization can be.
The MITRE ATT&CK Framework is invaluable for mapping specific attack campaigns, threat groups, and individual attack activities. Despite its ubiquity, many organizations are still figuring out how to leverage the framework consistently.
From an XDR solution perspective, you can use TTPs to develop detection rules and models, while ensuring threat intel is directly inserted into the investigation of events. This surfaces the identity of a particular attack campaign and provides visibility into the full campaign lifecycle.
The TTPs can also be used to develop threat hunting criteria or provide proactive views of identified TTPs in the environment that can be leveraged as a starting point for targeted investigations.
Lastly, leveraging the MITRE ATT&CK framework can be used to identify security gaps and prioritize activities to lower risk and improve resiliency.
Key XDR considerations
While sensor coverage is important, there’s a lot more to consider when choosing an XDR vendor to ensure you receive the best threat detection and response capabilities. Consider asking the following questions:
1. Is the product API-friendly? Some vendors don’t integrate their APIs with SIEM and SOAR. The more XDR is integrated, the greater the ability it provides to automate and orchestrate tasks, enabling workflows across the ecosystem. Also, a vendor with an XDR solution that integrates into a cybersecurity platform will provide security professionals with a much-needed single pane of glass view across the entire attack surface.
2. Does the product visualize an end-to-end understanding of an attack? Some XDR solutions may only provide a snapshot of an attack. Security teams need visibility of managed and unmanaged assets and encrypted network traffic to understand where the attack originated and how it spread. By extending network telemetry and correlating against network events via NDR, teams can establish the full attack chain and strengthen your security posture.
3. How is the user experience? Finding (and keeping) skilled staff remains a challenge. Avoid security solutions that have a steep learning curve and poor support. A vendor who wants you to succeed (not just sell you a product) will have in-app tutorials, an online help center, and even direct feedback loops or feature requests built-in.
4. Are they looking ahead? Make sure the vendor is committed to improving their product to not only address the evolving threat landscape, but making it easier for your teams to do so. Do they have a strong strategy for how to greatly reduce the burden on your security teams with AI? Don't be afraid to ask tough questions to make sure it's not smoke and mirrors. Bonus points for vendors who have a strategy on how to secure your organization’s usage of AI tools.
5. Are the alerts actionable? As we mentioned earlier, legacy SIEM will spit out a ton of alerts, but they’re often useless. You have to do a lot of detection engineering to force your legacy SIEM to work for you. The right XDR solution will provide actionable alerts thanks to cross-layer correlation and detection models that are ready out-of-the-box. It should also prioritize alerts based off the risk score and severity of impact to accelerate response times
6. What is the pricing structure? Look for vendors who offer pricing models that are favorable to shifting business dynamics. Most vendors commonly charge by bundles or seat-based subscriptions which can leave you paying for unused sensors in case your employees leave or are laid off. Consider more flexible licensing options that allow you to adjust allocations on-demand, while removing fixed costs and any losses due to underutilized licenses.
7. Are managed services offered? Staff shortages and budget constraints can hinder threat detection and response efforts. A vendor who can offer managed services to augment your existing team with expert threat hunting, 24/7 monitoring and detection, and rapid investigation and mitigation can be invaluable. You can gain expertise and competencies while alleviating your overstretched teams to work on higher priority programs.
8. Has the product received industry analyst accolades? Everyone loves to say they’re #1, so make sure you check out reports from reputable industry analysts to validate the vendor’s claims. Shameless plug, see how Trend is viewed by the industry.
Getting the board on board with XDRWhile statistics show that cybersecurity spend continues to increase, that is no guarantee your budget will grow in-line. Getting the green light on cybersecurity investments can be challenging, so framing the benefits of XDR in a financial and risk context is critical. Here are some of the things to consider when making a case for XDR:
Investing in security solutions = investing in the business. According to IBM’s Cost of a Data Breach 2022, organizations using XDR saved nearly 10% on average in breach costs and shortened the breach lifecycle by 29 days. Less operational downtime and financial impact are music to the C-suite’s ears.
Reduce cyber insurance premiums.Underwriters are looking for EDR, but demonstrating that you go beyond the endpoint with XDR to reduce cyber risk can help you lower costly cyber insurance premiums.
Next steps
For more information on XDR and cyber risk management, check out the following series or click here to see how Trend Vision One(TM) – XDR can ensure attackers have nowhere left to hide.