By Trend Micro Mobile Team
We observed an uptick in attacks targeting bank customers in India, the common entry point being a text message with a phishing link. The SMS content urges the victims to open the embedded phishing link or malicious app download page and follow the instructions: To fill in their personally identifiable information (PII) and credit card details to allegedly get a tax refund or credit card reward points. As of this writing, we observed five banking malware families involved in these attacks, namely Elibomi, FakeReward, AxBanker, IcRAT, and IcSpy.
We analyzed that the bank customers targeted include account subscribers of seven banks, including some of the most well-known banks located in the country and potentially affecting millions of customers. Common among these routines include the abuse of the legitimate banks’ logos, names, and affiliated brands and services to convince victims that their respective phishing sites are affiliated. This blog entry will discuss three of the identified banking malware families and their latest changes (as IcRAT and IcSpy have been documented): Elibomi is an old malware that has evolved into a fully equipped banking trojan, while FakeReward and AxBanker are newly discovered banking trojans. Bank clients are advised to remain vigilant against these kinds of threats, and to protect their information and devices from malware infections.
Elibomi returns with more functions
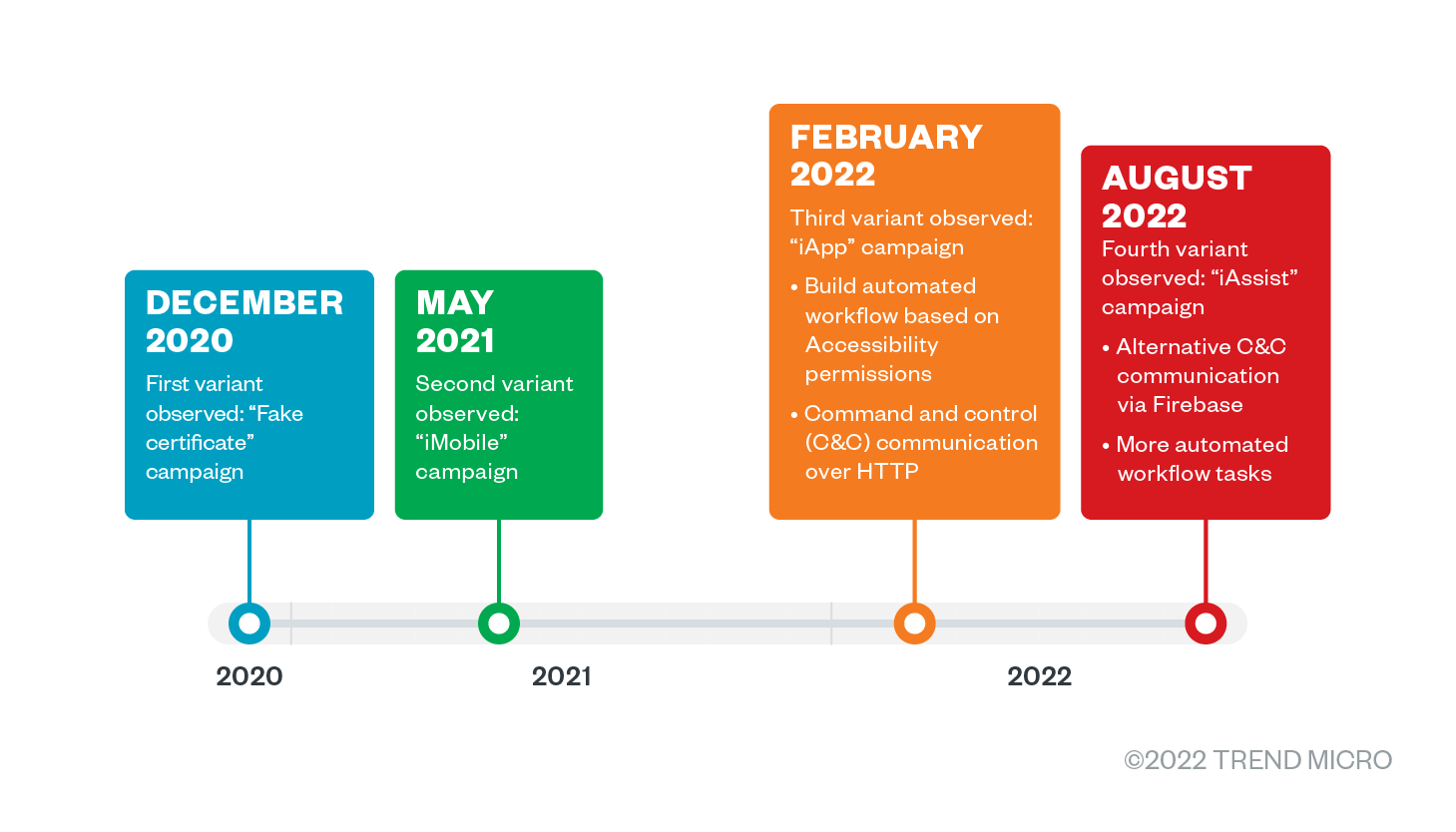
Elibomi’s first and second variants, “fake certificates” and “iMobile” campaigns, appeared towards the end of 2020 and remained active in 2021, designed to steal victims’ PII and credit card information. During the early months of 2022, we observed a phishing campaign dropping a new variant of Elibomi with a package name that ended with “iApp.” From this variant on, the routine changed drastically: the threat actors added automation to workflow tasks via Accessibility permissions such as automated clicking, granting of permissions, and capturing screenshots.
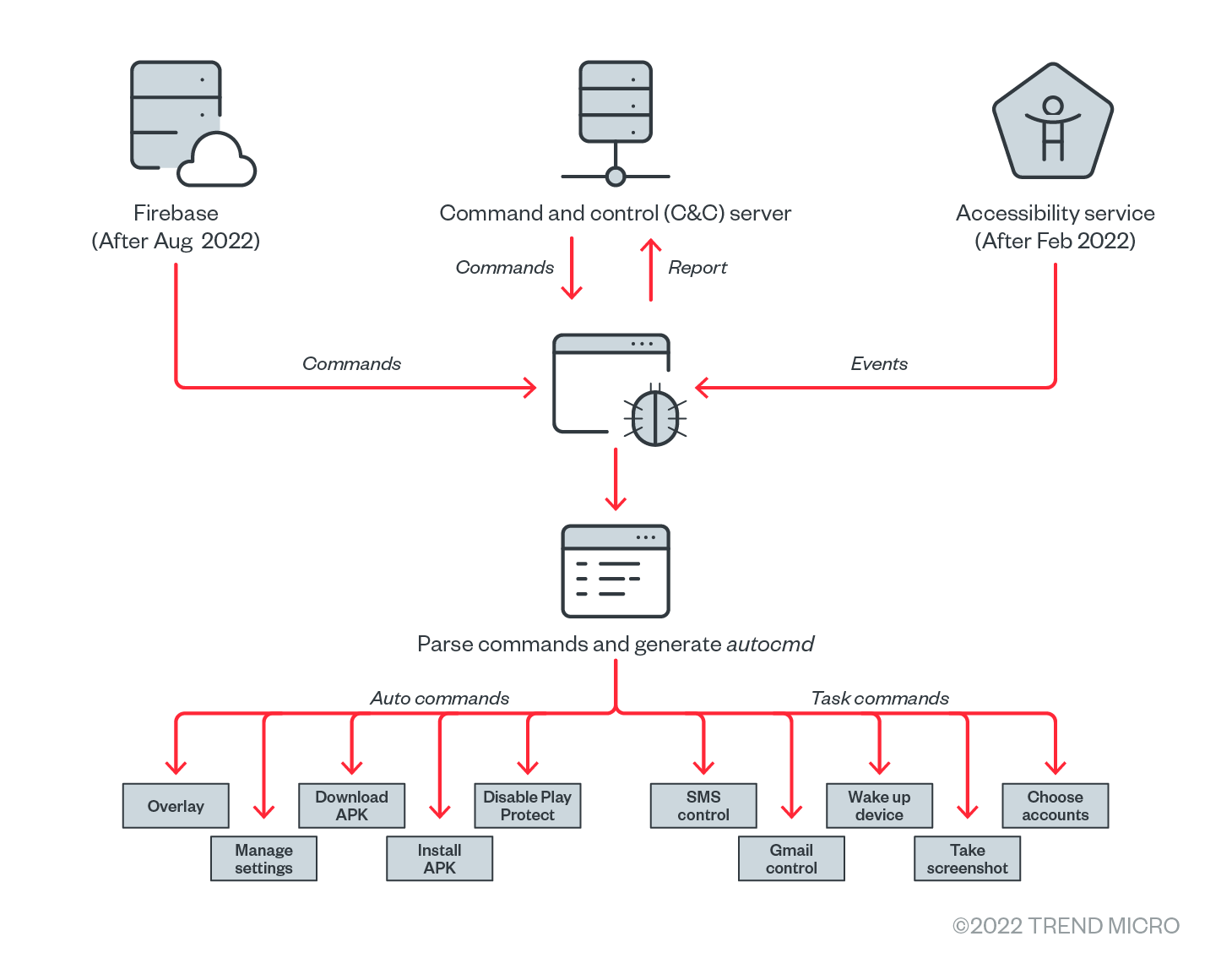
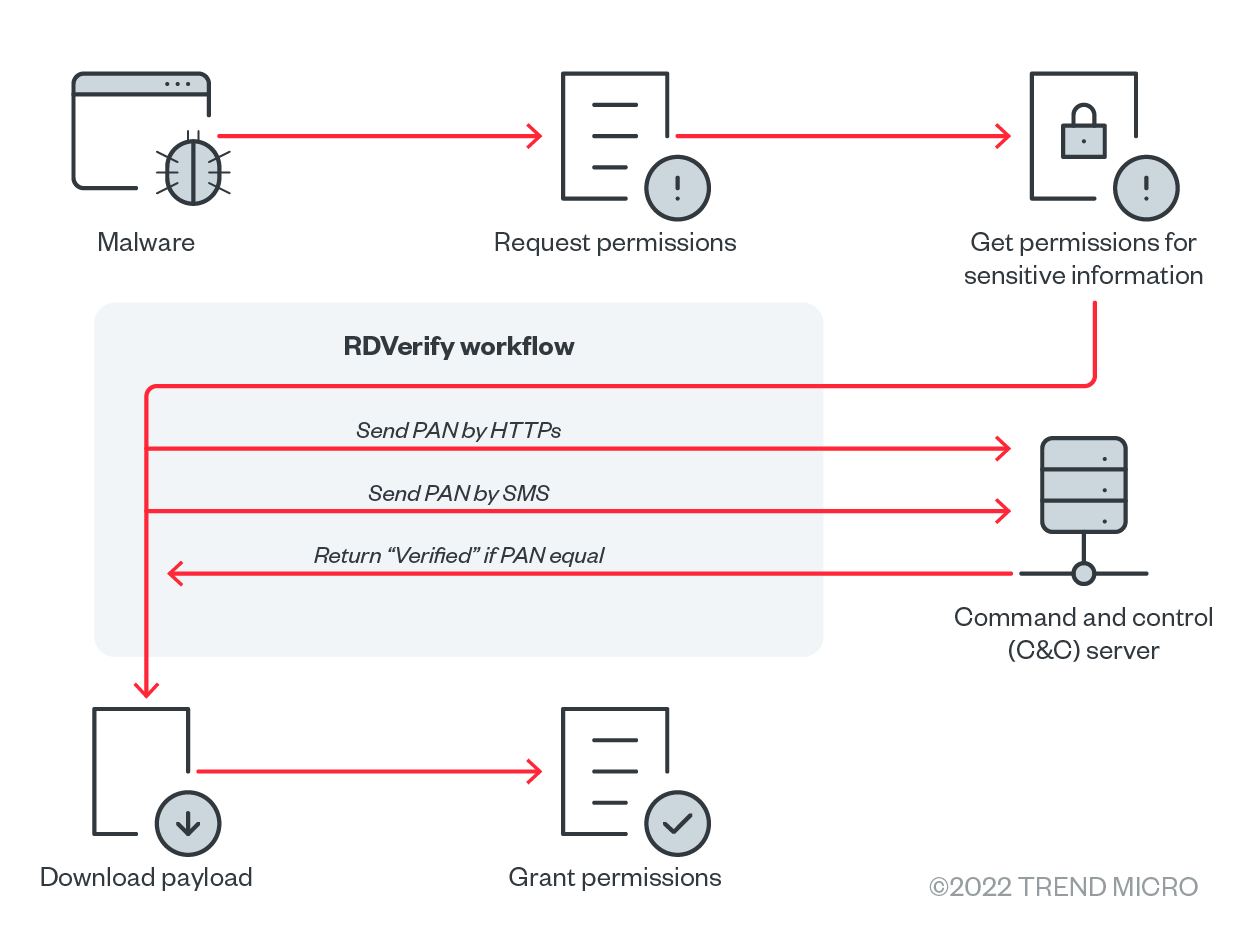
More recently, we found a fourth variant of Elibomi delivered from the same phishing site with a package name ending with “iAssist.” This variant added the cloud-hosted real-time database Firebase as an alternative command and control (C&C) server and an environment check tool called RDVerify for detection evasion. In the next sections, we detail the different commands and functions that the third and fourth variants of Elibomi are capable of, as well as the implications of these updates. It is also worth noting that an update has again been observed in October on the latest iterations, as documented by security researchers from Cyble.
Overview: Elibomi’s automated variants
Due to the automated workflow framework of the latest variants, we called the third (“iApp” campaign) and fourth (“iAssist” campaign) automated variants and break down the commands and functions we found from their respective routines.
Sophisticated command format
Looking into the routines of the third and fourth variants, Elibomi implements a sophisticated and lengthy command list and has three types of commands to conduct malicious activities: Task command, server command, and auto command. The succeeding section breaks down the three commands we found.
Task command
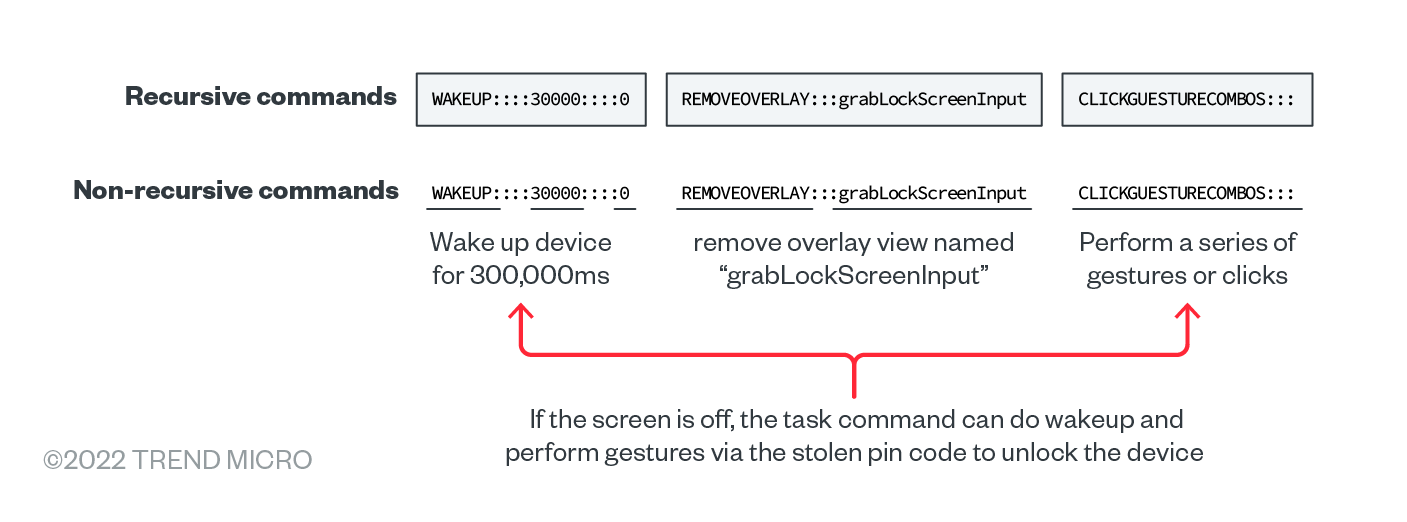
We found that the task command was the main command among the three, enumerating the specific malicious activities needed in the routine. It is capable of being a recursive command for complex tasks, or a non-recursive command function:
- As a non-recursive command: A single command that contains the command name and corresponding operands. This can be split by “:::” to get the sub-terms.
- As a recursive command: A combination of non-recursive commands that can be split by “,” or “-” to get non-recursive commands.
As an example, should a specific aspect of Elibomi’s routine require unlocking the device without the user becoming aware of it, the malware can use this recursive command to accomplish three tasks: wakeup, remove the screen overlay, and make the gesture combination for the unlock screen pin or pattern.
Server command
This command returns the execution result to the backend server. For example, “D:::Unlock has been executed - ##-##” shows and communicates with the server that the task command was able to unlock the device successfully.
Auto command
The auto command plays a vital role in Elibomi’s automated workflow, describing how Elibomi uses Accessibility to conduct the malicious behaviors step by step. For example, auto command is responsible for how Elibomi enables the Media Projection automatically. When the attackers get the Accessibility permissions granted and receive the task command MEDIAPROJECTION, Elibomi will generate the auto command <SCREENCLICK:Button:start now|ok|accept|allow> to click on “START NOW” in the MediaProjection dialog box.
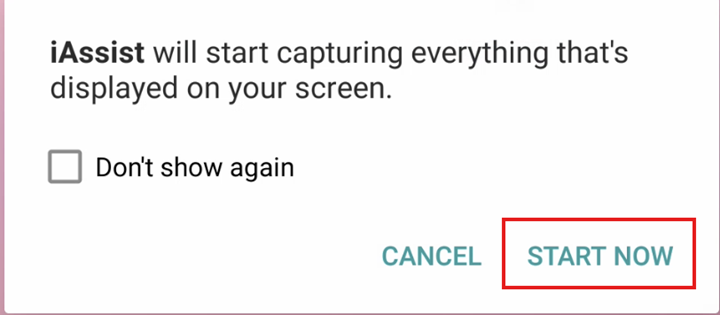
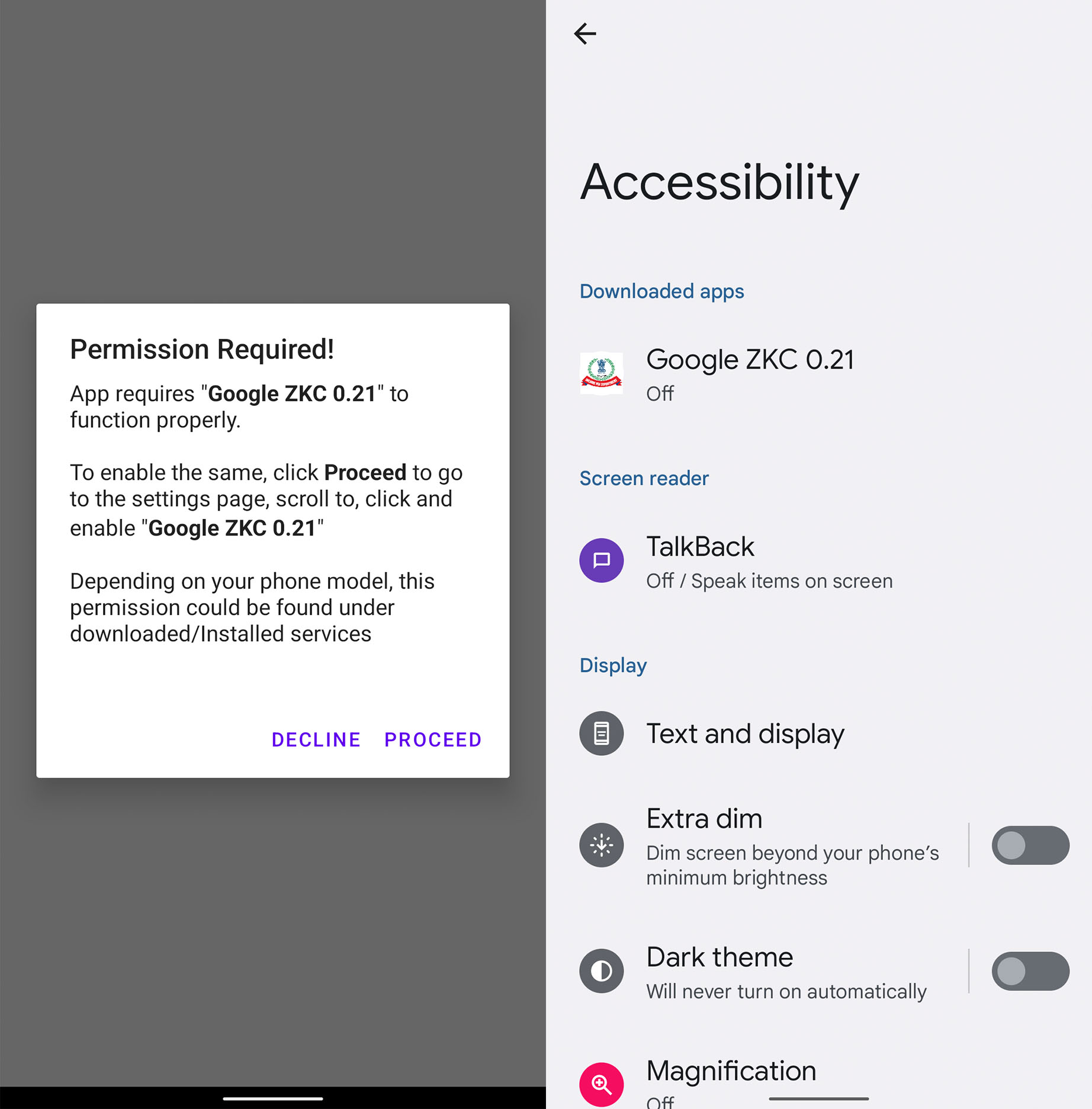
A fully automated malware
Analyzing the routines that the two latest variants of Elibomi are capable of, this malware can interact with the device’s user interface (UI) automatically without the user knowing. To become a “fully automated malware,” Elibomi will show a message upon launch that pushes the user to enable Accessibility permissions by disguising itself as a Google application. It then proceeds to show a dialog box upon launch as if there is an urgent need to grant Accessibility permissions to push the user to allow the said request.
The following is the full list of malicious tasks that have been added to Elibomi’s automation workflow in the latest automated variants:
| Task | Related Task Command | Related Auto Command |
|---|---|---|
| Get MediaProjection permission | EXECUTORSEQUENCE::: PERMISSIONFOLLOWUP#222#MEDIAPROJECTIONPERMISSION | CLICK:Button:start now|ok|accept|allow:-:-::SCREENCLICK:Button:start now|ok|accept|allow:-:-::CLICK:Button:start now|ok|accept|allow:-:-::SCREENCLICK:Button:start now|ok|accept|allow:-:- |
| Allow Write settings | EnableSettingsSequence | fullforwardswipe:Switch:-:-:-::fullforwardswipe:Switch:-:-:-::fullforwardswipe:Switch:-:-:- |
| Get SMS-related permissions | EXECUTORSEQUENCE::: PERMISSIONFOLLOWUP#222# SMSPERMISSION | CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:- |
| Set itself as default SMS app | PERMISSIONS:::REVOKEDEFAULTSMS STARTSMSSEQUENCE |
CLICK:Button:yes|ok|accept|allow:-:-::SCREENCLICK:Button:yes|ok|accept|allow:-:-::CLICK:Button:yes|ok|accept|allow:-:-::SCREENCLICK:Button:yes|ok|accept|allow:-:- |
| Allow Install App from Unkown Source | REQUESTINSTALLPERMISSION | CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:- |
| Disable battery optimization | IGNORE_BATTERY_OPTIMIZATIONS | CLICK:Button:ok|accept|allow:-:-::SCREENCLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::SCREENCLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-" |
| Install additional APK and grant permission for the payload | DOWNLOADAPK EXECUTORSEQUENCE:::INSTALLAPK EXECUTORSEQUENCE:::OPENAPPCOMPONENTandGRANTPERMISSIONS |
CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:-::CLICK:Button:ok|accept|allow:-:- |
| Get all accounts | SCREENSHOT GLOBAL_ACTION_BACK |
N/A |
| Disable Google Play Protect | DISABLEPLAYPROTECT | N/A |
| Read or delete emails from Gmail | GMAILSEQUENCE | click:android.widget.Button:Empty:-:- |
| Prevent disable Accessibility | GLOBAL_ACTION_BACK | N/A |
| Prevent Uninstall | GLOBAL_ACTION_BACK | N/A |
| Prevent enabling of Google Play Protect | GLOBAL_ACTION_BACK | N/A |
| Unlock device | WAKEUP | N/A |
Table 1. List of malicious tasks added to the two latest variants of Elibomi
Elibomi affects Android 12 and lower, and can automatically grant the attackers sensitive permissions, enable/disable sensitive settings such as enable installation of apps from unknown sources, and disable GooglePlay protect. Android 13 is not affected as Google restricts the Accessibility permission in the latest version.
Video 1. How Elibomi’s latest campaign operates in the user’s mobile device
Overlay mechanisms
For both iApp and iAssist campaigns, Elibomi implements an overlay by adding a view to the current window as an evasion technique from users, instead of having an overlay on other apps such as bank applications to steal users’ credentials.
Wait screen overlay
In order to evade visual detection from users, Elibomi will show a waiting screen after gaining Accessibility permissions for service. However, it already executes an automated workflow in the background to grant sensitive permissions to the attacker.
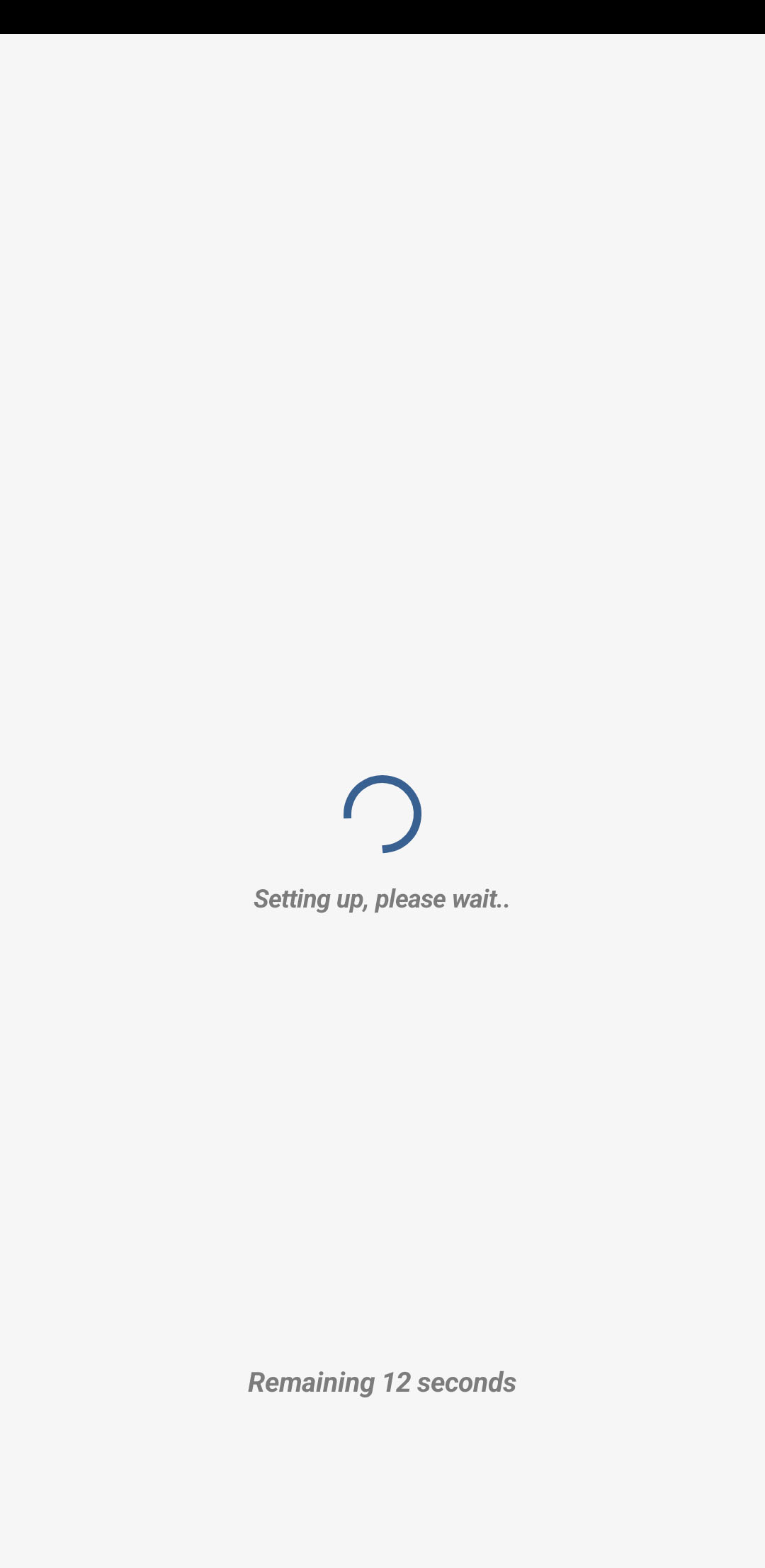
Elibomi uses another window type called “TYPE_ACCESSIBILITY_OVERLAY” instead of request “SYSYTEM_ALERT_WINDOW” permission to add an additional view to the current window.
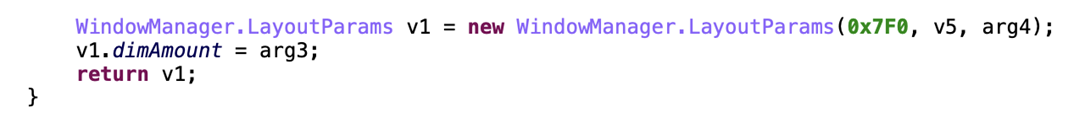
Fake pin overlay
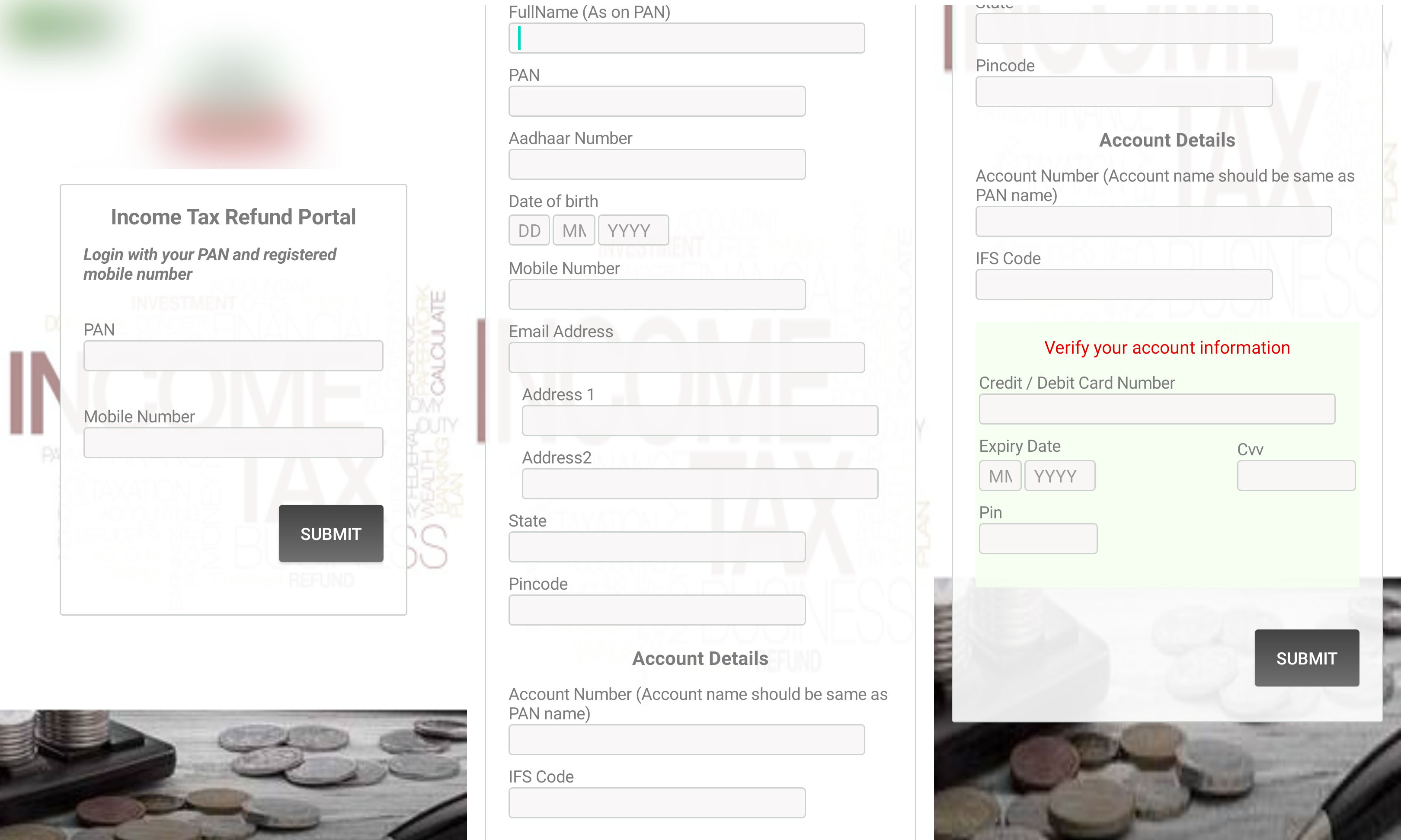
To unlock the device automatically, Elibomi is capable of stealing the pin code or pattern saved by the user by showing an overlay screen to the victim and “listening” for the user’s actions to record their gestures and clicks.
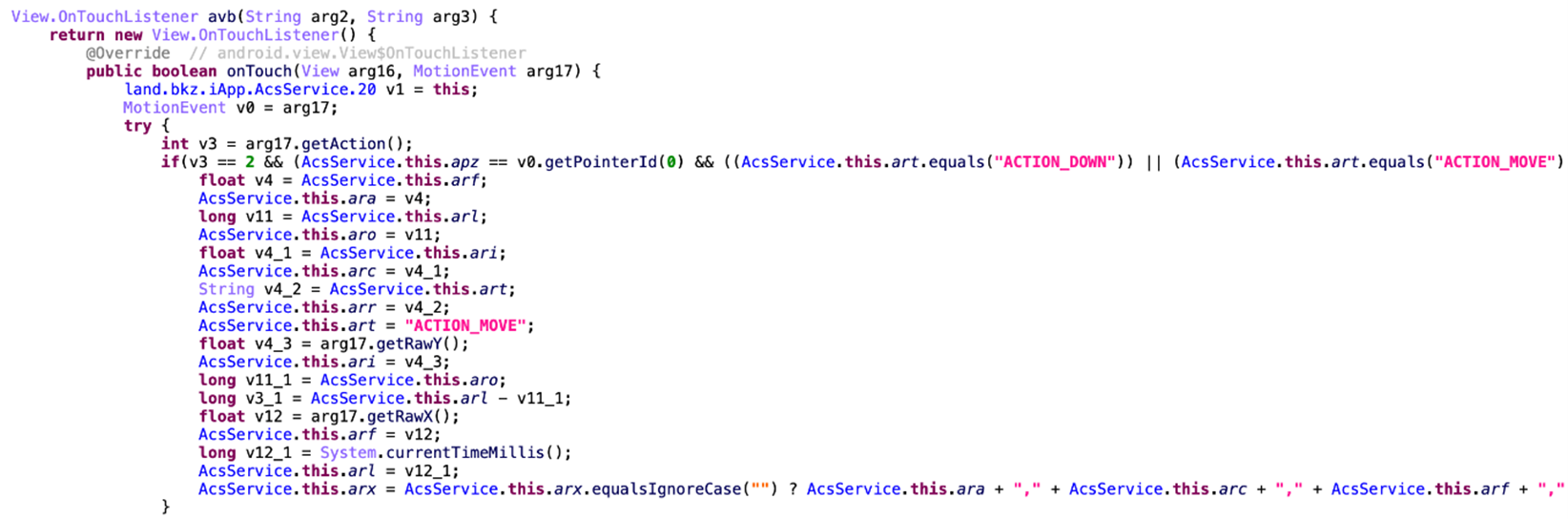
Not just Android
From our scanning online, we found the cybercriminals extending their phishing campaign not only on Android but have also ventured to other platforms such as email. Comparing previous phishing sites, it appears that they have created different themes to induce victims to fill in their sensitive information. The type of stolen data is nearly the same as what they require users to put on the Android platform.
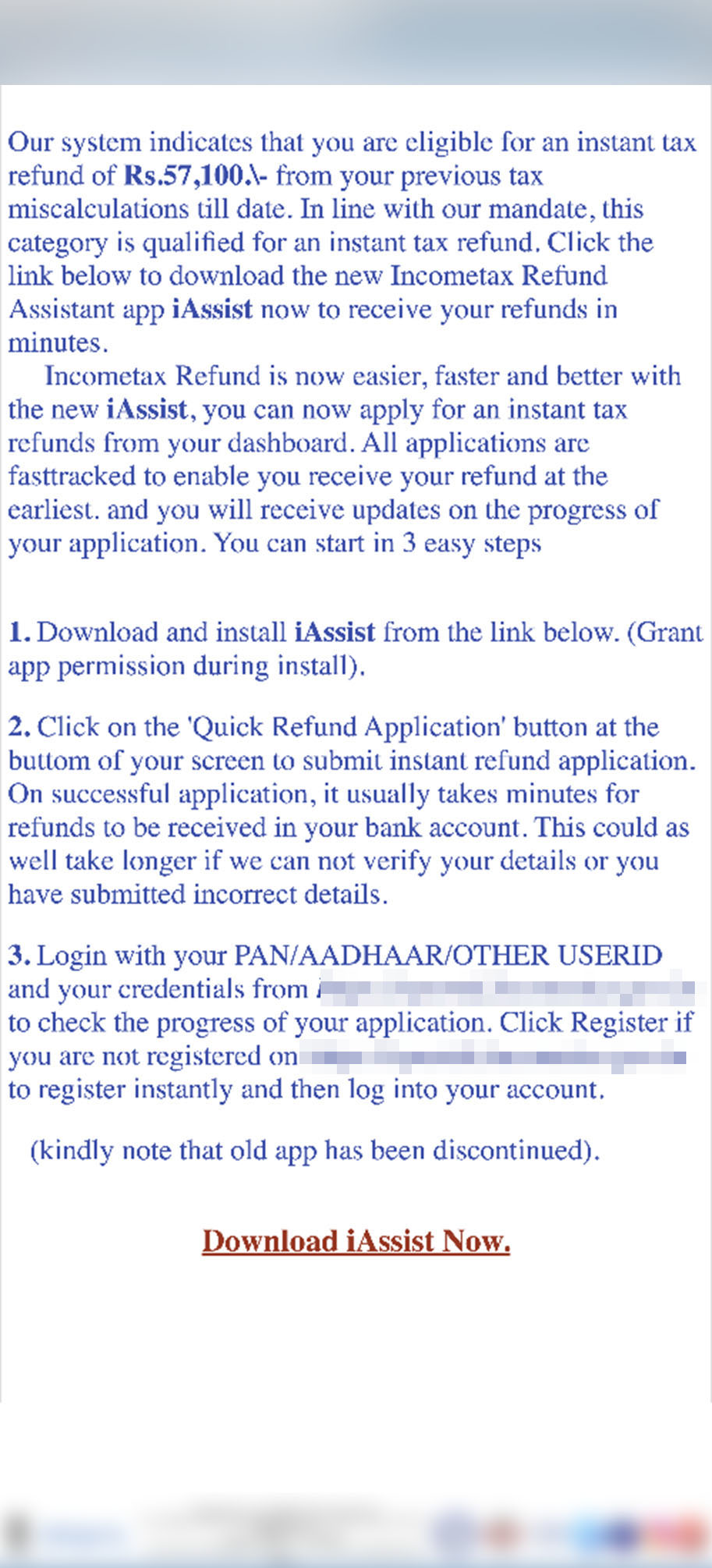
“iAssist” campaign as a fast-evolving Elibomi variant for more profit
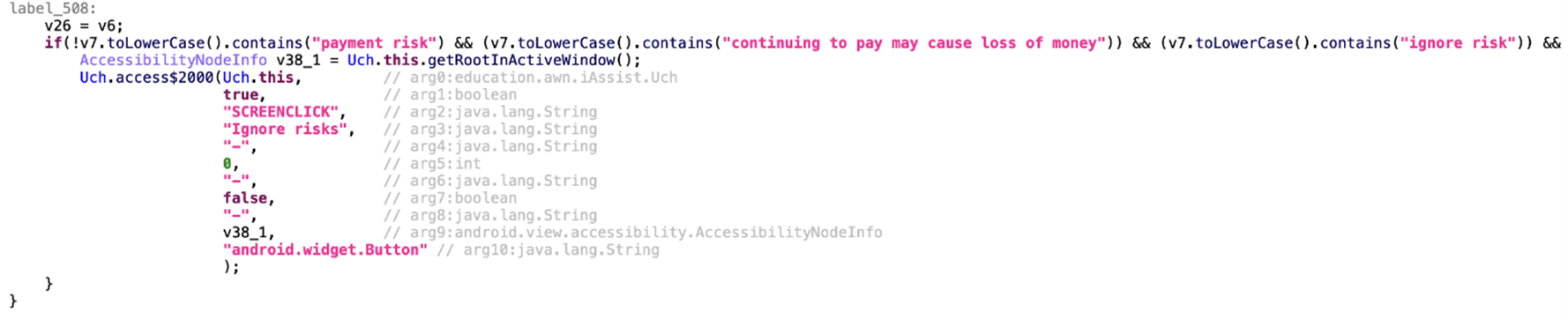
In the fourth variant, we noted one interesting task added to their automated workflow. While the Accessibility permission detects the payment risk notification string that sends the message “continuing to pay may cause loss of money” to appear on the UI, it will click on “Ignore risk” to dismiss the alert dialog. This warning usually appears if there is a risk of payments or transfers occurring while using a bank app, and can indicate that the cybercriminals behind this malware can consistently update or enhance Elibomi to automatically conduct money transfers from the victim’s device without them noticing.
FakeReward: Targeting three banks’ customers in India
In August, we found a campaign we named FakeReward targeting customers of three of the largest banks in India wherein the threat actors registered several domains similar to the legitimate domains to confuse victims. These phishing websites were pretending to be the official websites of these three banks, even abusing the companies’ names and logos to complete their look.
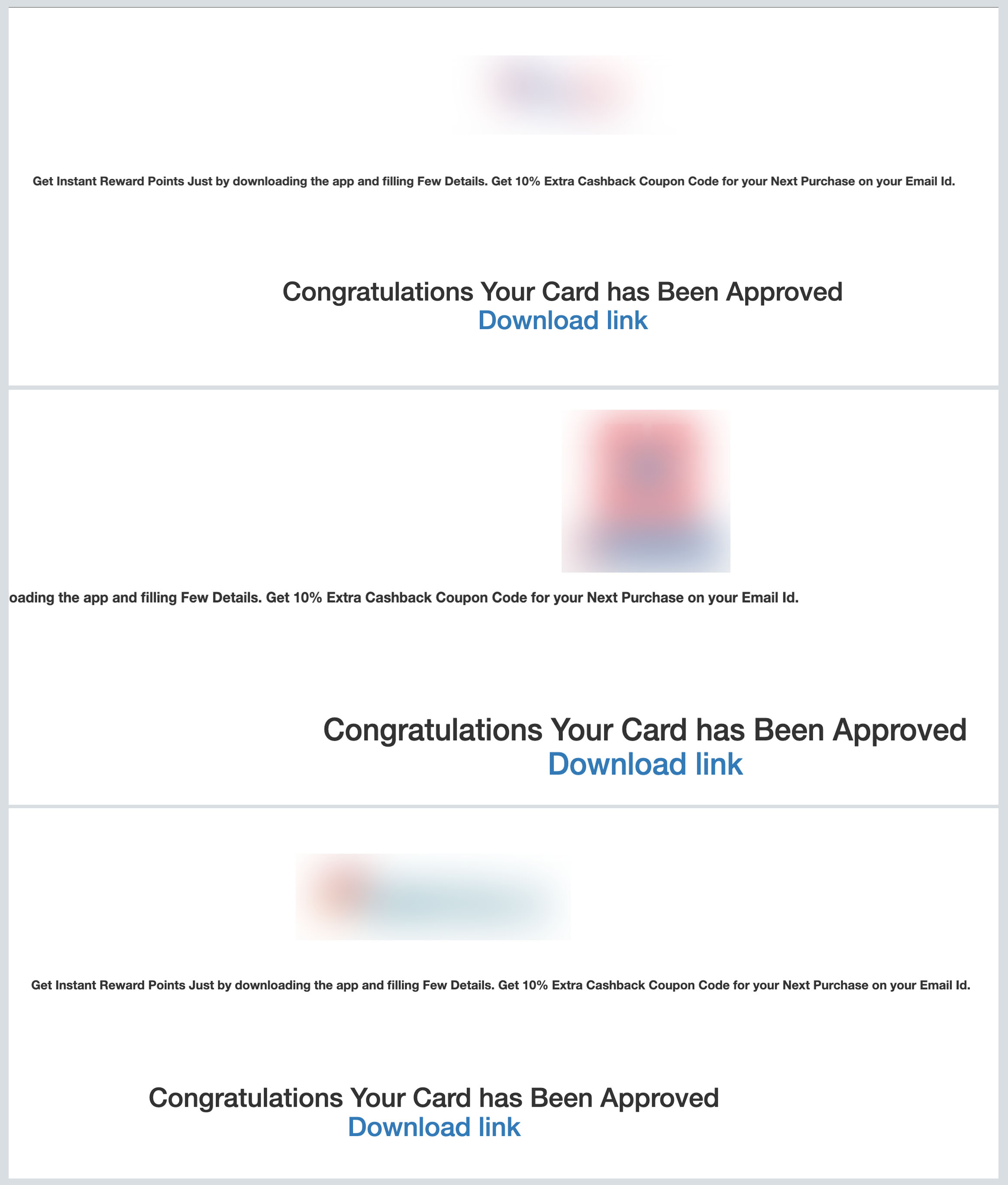
The FakeReward banking trojan shows a page to request SMS permissions upon launching. Once granted, the malware will collect all text messages to the device and upload it to a remote server, then set up a monitor to listen to incoming SMS messages and sync it to the remote server. We released an initial social media thread on the said campaign to warn security teams and their respective bank customers to be vigilant against this malware.
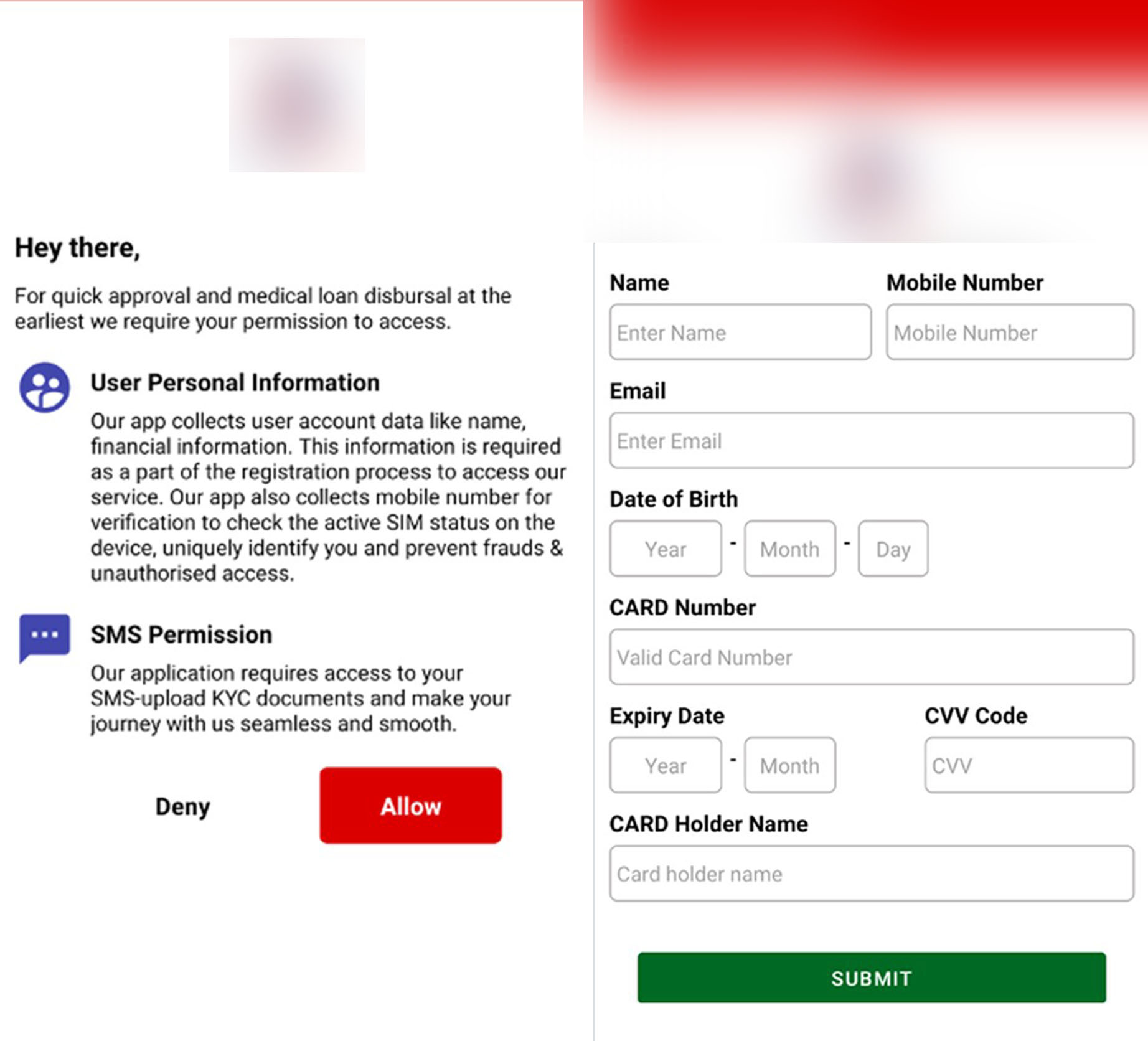
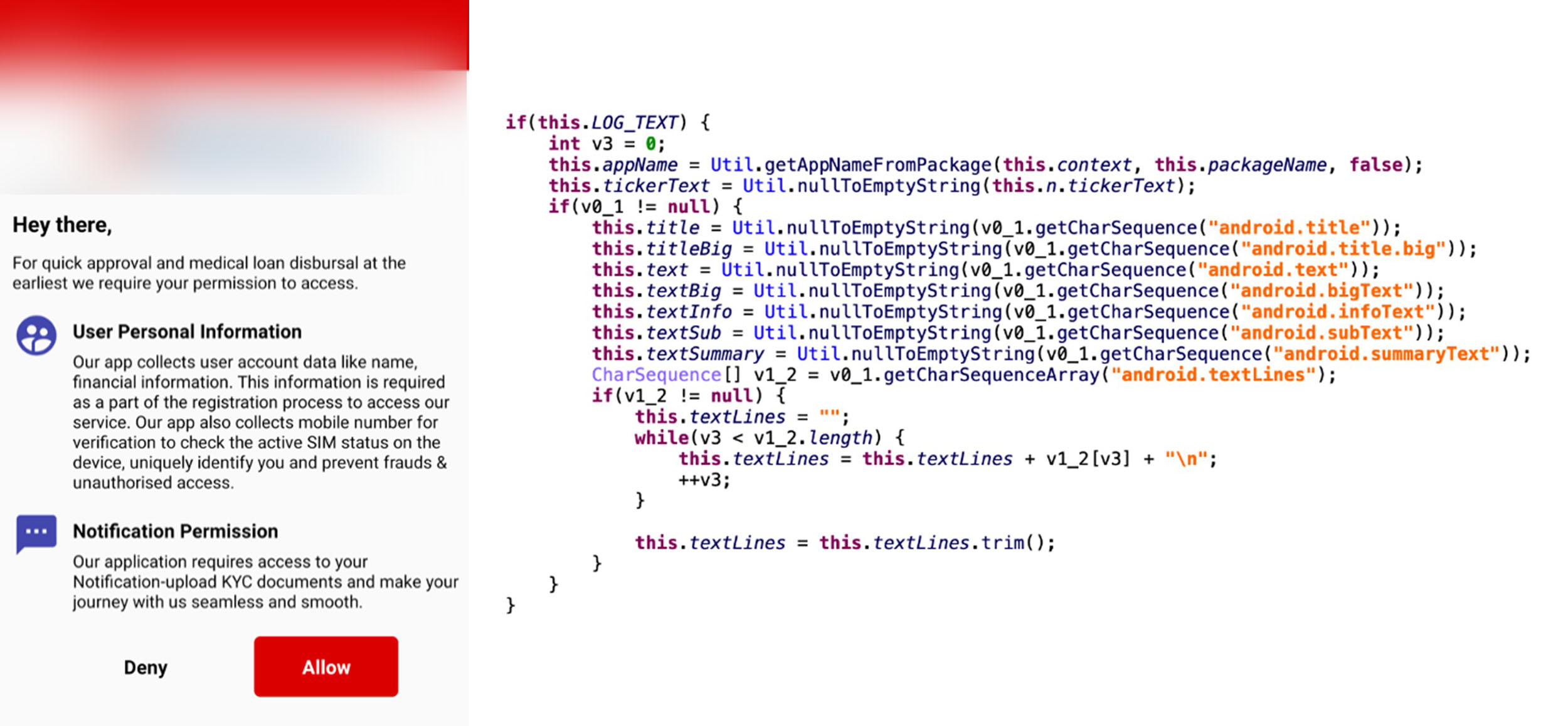
Latest changes
In its recent update, FakeReward malware tries to request a notification permission to extract text messages instead of directly requesting access for SMS permissions.
Security researchers from K7 Security Labs and MalwareHunterTeam have also found samples of at least five other FakeReward variants. We noted the increase in the number of families and variants of FakeReward malware targeting users in India that appear the same when examined using tactics, techniques, and procedures (TTPs) but show differences in codes. Trend Micro customers are protected from all these emerging phishing families and variants.
Potential connection between FakeReward and IcRAT
During our investigation, we found an interesting coincidence: FakeReward and IcRAT started targeting the customers of one bank nearly at the same time. Moreover, we also found the phishing websites of these two malware families to be nearly similar, making us believe that the cybercriminals behind these two malware families are connected.
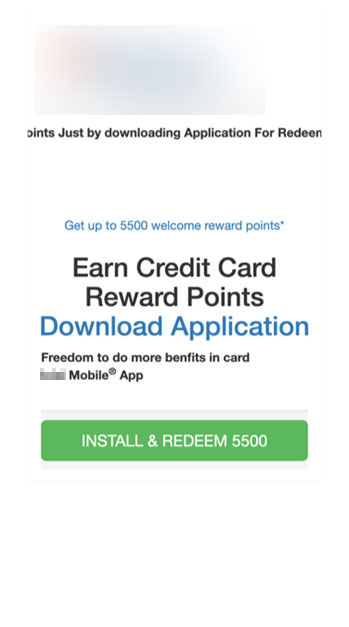
AxBanker: Fake app targeting bank’s customers
In addition to FakeReward banking malware targeting the customers of two banks, we also found another banking trojan targeting the customers of another major Indian bank that has been active since late August. The website has a similar phishing theme wherein customers “Get Reward Points” to attract victims to download and install the app.
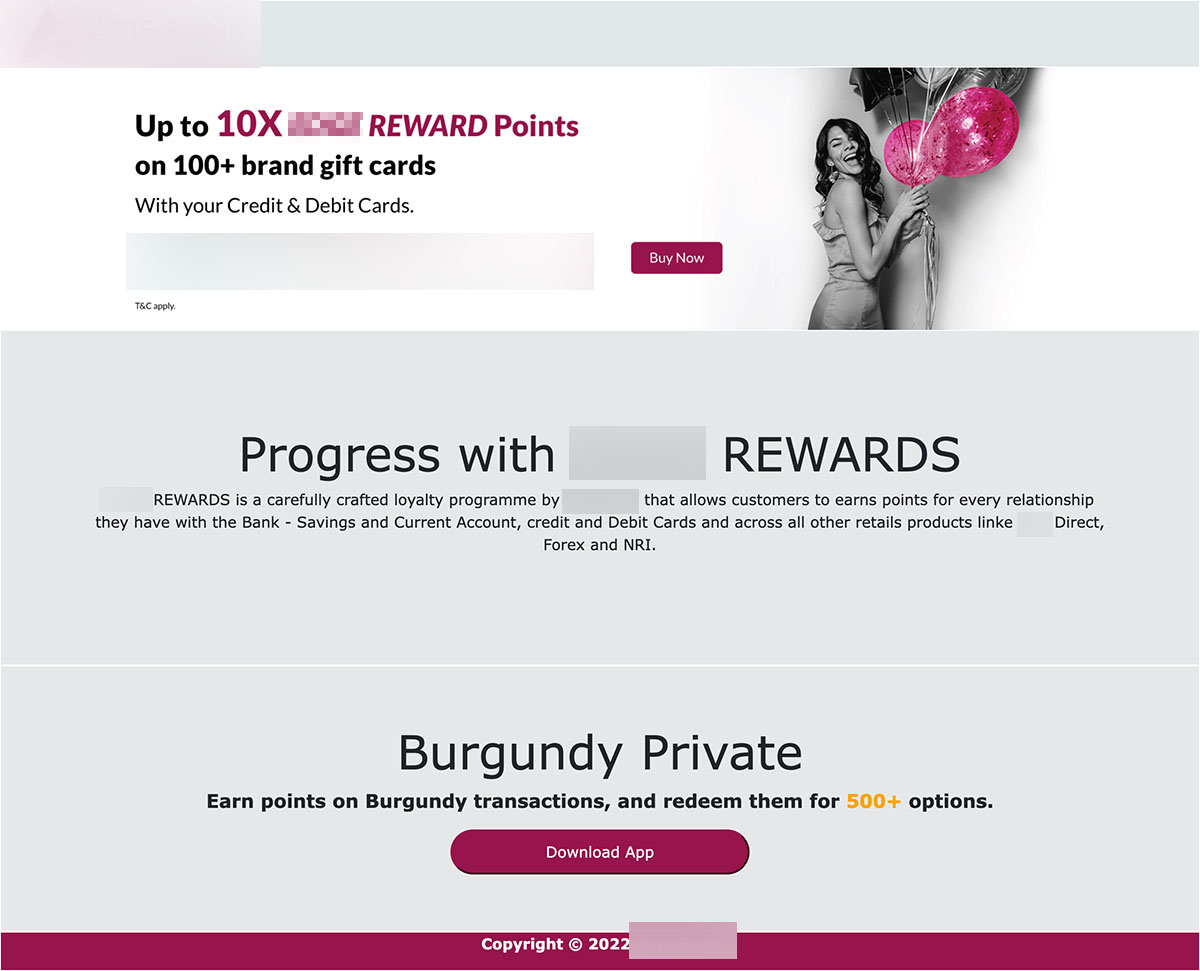
Once the malware is installed and launched, it will request SMS permissions in order to capture and upload incoming SMS to a remote server. The malware will then show several fake pages to collect the victim’s personal data and credit card information.
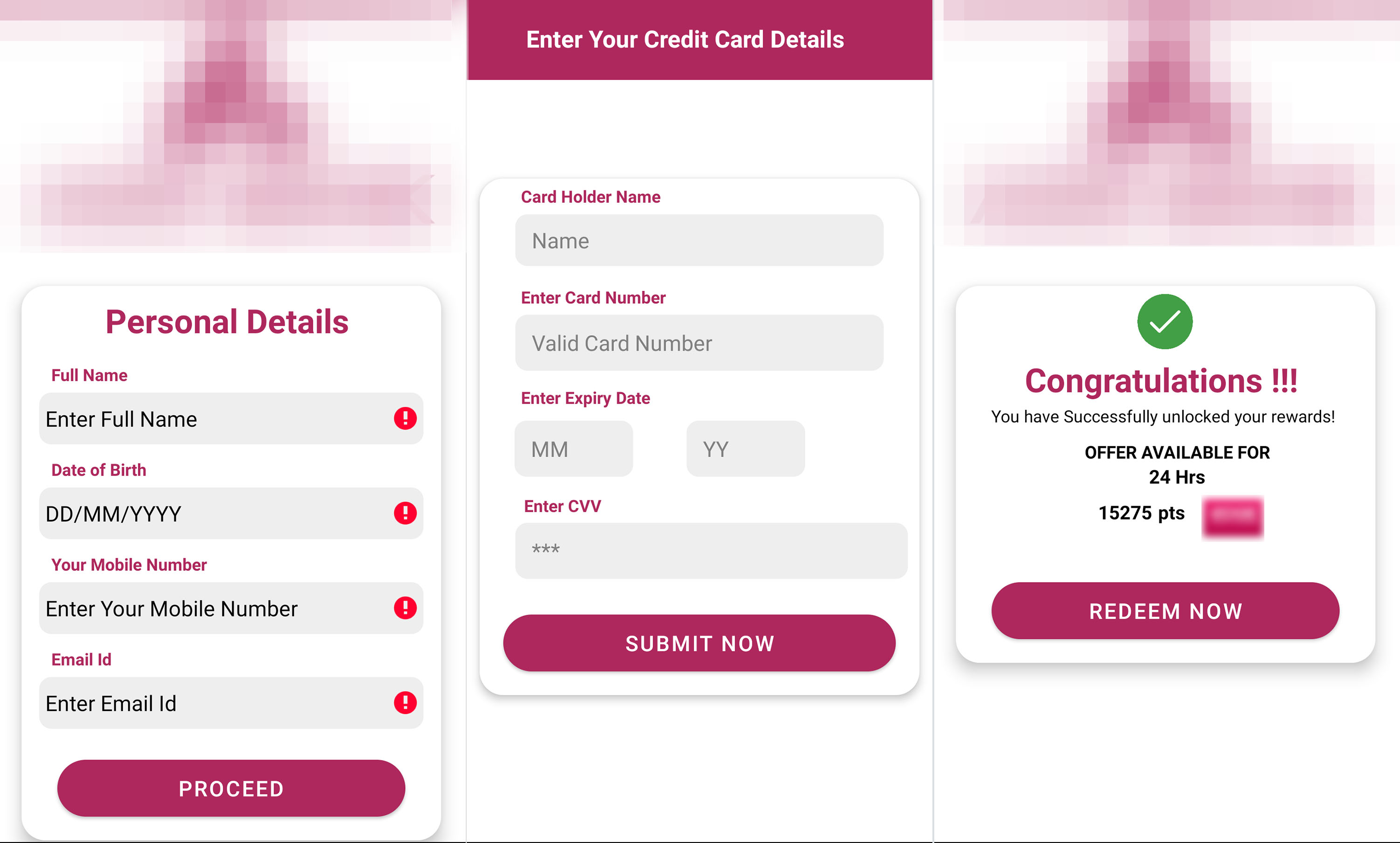
Conclusion
While the types of stolen data and phishing themes are similar, we don’t have enough evidence to conclude that the cybercriminals behind all of these banking malware families are connected but are aggressive in developing further. In the case of the threat actors behind Elibomi, these cybercriminals are likely knowledgeable and adept in Android development based on the automation of tasks pertaining to Accessibility permissions. Meanwhile, the threat actors behind FakeReward appear to have deployed phishing malware prior to this campaign based on their capability of hiding their tracks: the phishing domains used operate for only three to four days at a time before becoming inaccessible. In addition, a quick scan shows that only a few security engines have been able to pick up on its new variant.
Our monitoring also shows that while no other customers outside India have been targeted by these malware families, phishing campaigns in the country have significantly increased and are increasingly becoming adept at detection evasion. One possible reason for this uptick is the growing number of new threat actors entering the India underground market, bringing with them profitable business models, and interacting with other malicious players to learn, exchange ideas from, and establish connections. Users and bank customers are advised to remain vigilant and follow these best practices:
- Check the text message’s sender. Legitimate companies and organizations have official contact channels from where they send notifications and promotions.
- Do not download and install applications from unknown sources. Choose to download the official bank apps from official platforms.
- Do not enter sensitive personal information in untrusted apps or websites. Contact banks and organizations through their known channels to ask if they have ongoing promotions or announcements like the message received.
- Double check the dialog boxes’ requests and messages before granting sensitive permissions such as Accessibility to untrusted apps.
Trend Micro solutions
Trend Micro Mobile Security Solutions can scan mobile devices in real time and on demand to detect malicious apps, sites, or malware to block or delete them. These solutions are available on Android and iOS, and can protect users’ devices and help them minimize the threats brought by these fraudulent applications and websites.
Indicators of Compromise (IOCs)
For a full list of the IOCs, find it here.

