Corporate security teams are now facing multiple cybersecurity issues, including complex data privacy and compliance requirements, in addition to the rapidly advancing Digital Transformation.
Trend Micro, in collaboration with 451 Research, a part of S&P Global Market Intelligence, conducted a survey on the private wireless network, including 5G, across the manufacturing, power supply, oil and gas, and healthcare industries in Germany, Spain, the U.K, and the U.S, published in June 2022.
Security Expectations for Private Wireless Networks
The survey identifies security improvement as the most important aspect in private wireless networks.
Figure 1
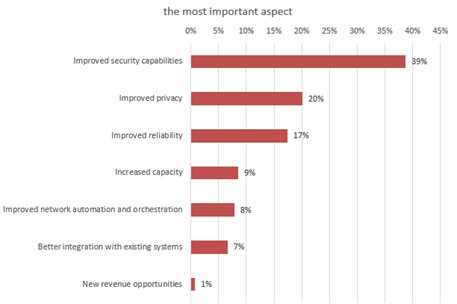
Q: When you are considering private wireless networks, what is the most important aspect?
Base: n = 408 Source: 451 Research custom study
Respondents are most concerned about exposure of data carried on the wireless network, followed by compromise of the network equipment and attacks on devices connected to the network. (Figure 2)
Figure 2
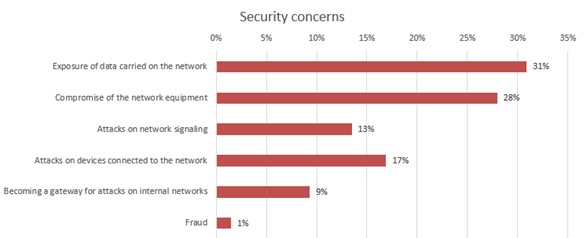
Q: What are your security concerns about private wireless networks?
Base: n = 408 Source: 451 Research custom study
The security of a private 5G network, which is one of the main options for wireless networks, occupies an important position in the formulation of 5G specifications, and many security improvements have been realized as the generation goes up from 4G to 5G.
Table 1
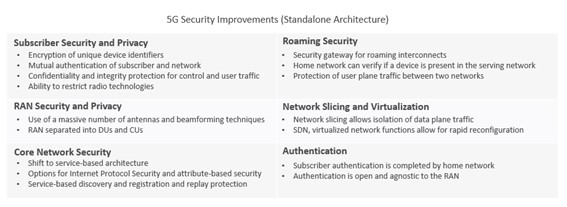
Source: CISA 5G Security Evaluation Process Investigation Version 1
It's also true that "private" networks which aren't shared with others strengthen the boundaries of security. Given the so-called common security specifications of 5G, there is no doubt these are more secure than traditional wireless networks when evaluating a private 5G network itself.
However, from the perspective of corporate security, this factor alone cannot be used to validate a security implementation of enterprise 5G. The complexity of 5G networks (telecom network uniqueness, enhanced mobile broadband [eMBB], ultra-reliable and low-latency communication [URLLC], massive machine type communication [mMTC]) expands attack surfaces in enterprise networks in the first place, making it difficult to define system boundaries.
Expectations for Partnership
This situation can be inferred from the results of the survey. The study shows that companies expect technology cooperation with established partners to move to 5G private wireless. The most common choices for expectations of partnerships were major network operators (24%), followed by major telecommunications equipment vendors (20%). Enterprises may expect to connect with established partners which have deeper technical experience their organizations don’t possess. The trend shifts with larger organizations, which gravitate increasingly toward systems integrators. For organizations with $1 billion to $1.5 billion in revenue, systems integrators are the preferred partner. For organizations of that size, Siers may already be an established technology partner.
On the other hand, the most promising security partners were the IT security partners currently involved. (Figure 3) They also expect security partners to have industry-specific security experience and understanding rather than telecom-specific security experience. This shows the desire to apply industry-specific security solutions to private wireless networks, rather than private wireless network-specific security.
Figure 3
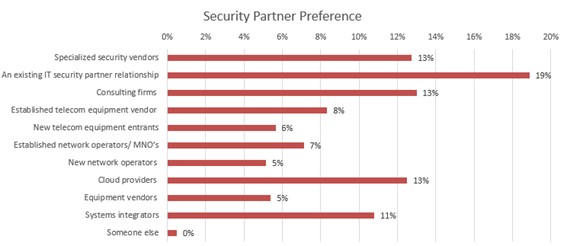
Q: What type of security partner is most attractive to you?
Base: n = 408 Source: 451 Research custom study
Figure 4
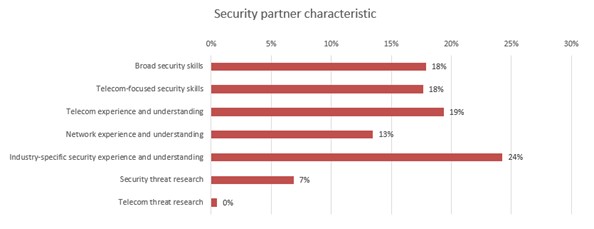
Q: What is the most important characteristic of a security partner for private wireless?
Base: n = 408 Source: 451 Research custom study
Expectations for Integrated Security
As a use case for private wireless networks, industry-specific ICS/OT environments such as “manufacturing monitoring and automation” and “manufacturing control” are being considered in addition to conventional IT environments. Approximately 80% of respondents expect the existing security system to be integrated with a private wireless network security system. (Figure 5)
Figure 5
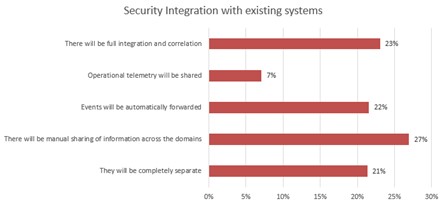
The study shows that while enterprises are aware of security characteristics in implementing private wireless networks, they want to integrate existing security systems with private wireless networks.
To read the executive summary of this survey, visit https://resources.trendmicro.com/IoT-5G-Networks-Report.html
Methodology
This report was commissioned by Trend Micro and leverages data from a survey conducted in the U.S., Germany, the U.K. and Spain. The survey consisted of about 400 respondents from the mentioned countries with job titles of director and above, across the manufacturing, power supply, oil and gas, and healthcare industries.
Sample titles of respondents include:
– VP/director of IT operations/CIO
– Director of IT, network operations/network architect/datacenter infrastructure and planning, network planning, 5G strategy planning, network virtualization, edge computing/MEC strategy and other equivalent roles.
We queried decision makers who are aware of their company’s private 5G wireless networking strategy and implementation plans, deployment plans and security concerns.
Trend Micro provides industry-specific security solutions that include IT, OT, and CT (Communication Technology) represented by Private 5G.
https://www.trendmicro.com/en_us/business/solutions/iot/ics-ot.html
Trend Micro 5G Security for Enterprises
https://www.trendmicro.com/en_us/business/solutions/iot/enterprise-5g-iot.html

