Trend Micro conducted a study on the state of industrial cybersecurity in the oil and gas, manufacturing, and electricity/energy industries in 2022. Based on the results of a survey of over 900 ICS business and security leaders in the United States, Germany, and Japan, we will discuss the characteristics of each industry, the motivations and environmental factors that will drive future cybersecurity improvements. We will also introduce Trend Micro's proposals based on the industry's current state, focusing on manufacturing & production.
Here is for the oil and gas industry
Here is for the electricity
Here is for the manufacturing
The environment surrounding the electric power industry has changed significantly over the past 10 years, and especially since the adoption of the SDGs to aim for sustainable energy, there is a pressing need to review the supply chain and entire system of the energy industry on a national scale.
A stable supply of electricity supports many industries and lifestyles, including manufacturing, restaurants, transportation such as trains, and households. The impact of power supply instability and outages is more widespread than in other industries.
Due to the nature of electricity, it is not possible to store large amounts of electricity cheaply, so it is essential to match supply and demand (production). To adjust supply according to demand, we have introduced mechanisms such as DR (Demand Response) and VPP (Virtual Power Plant) and are actively utilizing ICT.
In addition, the modernization of power generation, transmission, and distribution systems (digitization, network connection, use of general-purpose software and IT, etc.) is progressing, and at the same time, cyber risks are increasing.
In the United States, ahead of other industries, the Cyber Security Capability Maturity Model (ES-C2M2) was published in 2014 and has been used as a self-assessment procedure. In addition, NERC has decided on a new standard (CIP-012-1) for the protection of communications between large-scale power system control centers, and as a result, guidelines for security measures such as new supply chain risk measures have been introduced.
In addition, in Europe, where electricity is supplied between EU member states, the increase in security threats is not a risk for a single country, but energy and other critical infrastructure operators are required to take security measures (NIS Directive). Security measures are being implemented one after another. Here, we would like to share with you some excerpts from a report conducted by Trend Micro that show trends specific to the electric power industry.
Agenda
1 Characteristics and Considerations of the Electricity/energy Industry Regarding Cyberattacks
1.1 The amount of damage caused by cyberattacks is large
1.2 Causes of system outages
1.3 Current status for security system improvement
1.4 Drivers of Security Improvements
1 Characteristics and Considerations of the Electricity/energy Industry Regarding Cyberattacks
1.1 The amount of damage caused by cyberattacks is large
The amount of damage caused by cyberattacks was $3,378K (Monetary loss due to interruption of ICS/OT system due to cyberattack in last 12 months), which is the same as Oil & Gas. This is 1.8 times the amount of the manufacturing industry. In addition, system downtime was long, and 56% of respondents answered that the outage period was 3 days or longer, exceeding the majority.
As mentioned above, electricity is cheap and cannot be stored in large quantities, and the risk of supply shortages increases if system outages are prolonged. In addition, it is difficult to stop production (production) in the middle, and even if an incident occurs, it cannot be stopped immediately. It may take several days to several months, or even years, to perform scheduled inspections. Also, considering that electricity is the infrastructure of our lives, there is a risk that it will have a greater impact on society as a whole than the amount of damage caused by the electric power industry.
1.2 Causes of system outages
The number one cause of system outages was “Exploitation of external published applications or cloud service” at 31.3%. The second was "Compromise of internet accessible device" and "Malware infection due to legitimate web browsing", both at 29.7%. Outages due to the use of removable media and phishing were the lowest compared to other industries.
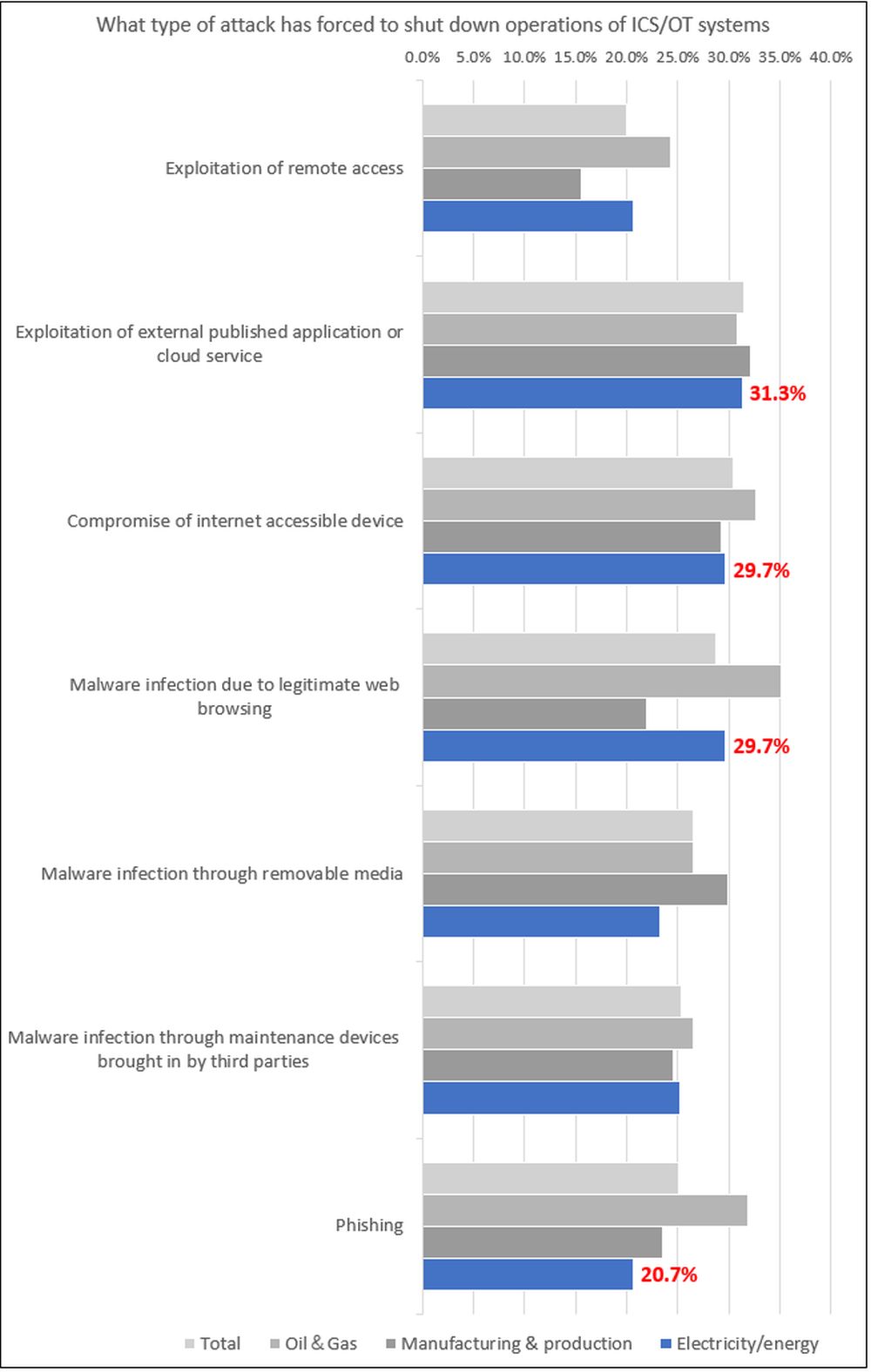
Figure1. Q4_1 ~ Q4_7 How has your organization dealt with the following types of cyberattacks? (NB: Multiple choices allowed)
This result suggests that the office terminals used in the IT area or OT area became an intrusion point. IT and security guidelines should be more advanced than other industries, but it seems that security measures are still not sufficient. I believe that interconnection with the IT environment is progressing along with the modernization of the OT environment. At this time, instead of implementing countermeasures individually, assuming that threats invading the IT (email, web) environment will spread to the ICS/OT environment, network segmentation, appropriate access control, and the internal route, we need a mechanism to detect anomalies.
1.3 Current status for security system improvement
Next, when asked if the organization has improved cybersecurity after incidents, 55% of the respondents answered “We always/usually make improvements”, just over half. Forty-three percent of respondents said, "We sometimes make improvements."
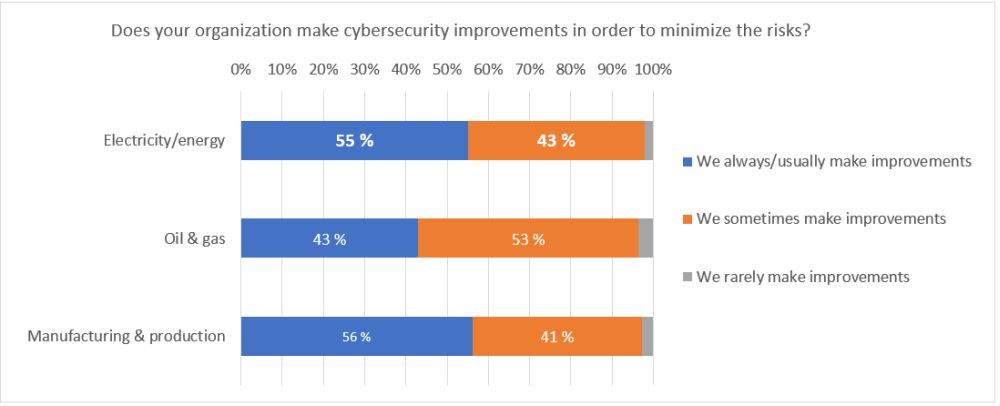
Figure2. Q10:Thinking about the last 12 months, post-incident, does your organization make cybersecurity improvements to minimize the risks of future attacks? (N=829)
Considering the impact that power system outages have on society as a whole, the percentage of respondents who answered "We always/usually make improvements" remained in the majority, which I think is extremely low. One of the reasons for this is the fact that we are facing the issue of equipment operation. Power generation systems (nuclear power, thermal power, hydropower) and power transmission facilities are difficult to shut down easily and must be done systematically. Since electricity cannot be accumulated during this shutdown, it is necessary to carefully calculate the timing and duration of planned shutdowns, making it difficult to modify the system solely for security reasons.
In addition to the difficulty of facilities, it is also possible that the continuity of power supply is prioritized and risks (balance between supply and demand, social unrest) are tolerated. However, the idea of taking countermeasures after suffering damage may not be able to fully evaluate risks and threats. In particular, the situation in Russia and Ukraine, which began in February this year, has had a wide variety of impacts on the energy industry. (At the time of the survey, it had not yet started and was not reflected in the survey results.)
In this way, security measures in an industry that is intricately related to society require careful consideration and careful introduction in a short period to maximize the effect.
1.4 Drivers of Security Improvements
We analyzed how the reasons for implementing cybersecurity measures have changed by dividing them into "past*" and "next 3 years", focusing on the items with the largest rate of change. As a result, the strongest driver was "Because we implemented or plan to implement a cloud system", which increased by 3.2 points. Prioritization, which was previously 3rd, has risen to 1st. Next, “Because we implemented or plan to implement a private 5G system” increased by 1.3 points, rising from 7th to 4th place. Looking at each country, Germany saw a remarkable change in the cloud, rising by 10.7 points. In Japan, responding to security incidents and planning for 5G increased by the same 4.7 points. Demands, plans for 5G, and penetration test results each increased by 3.0 points.
*As of the survey (February to March 2022)
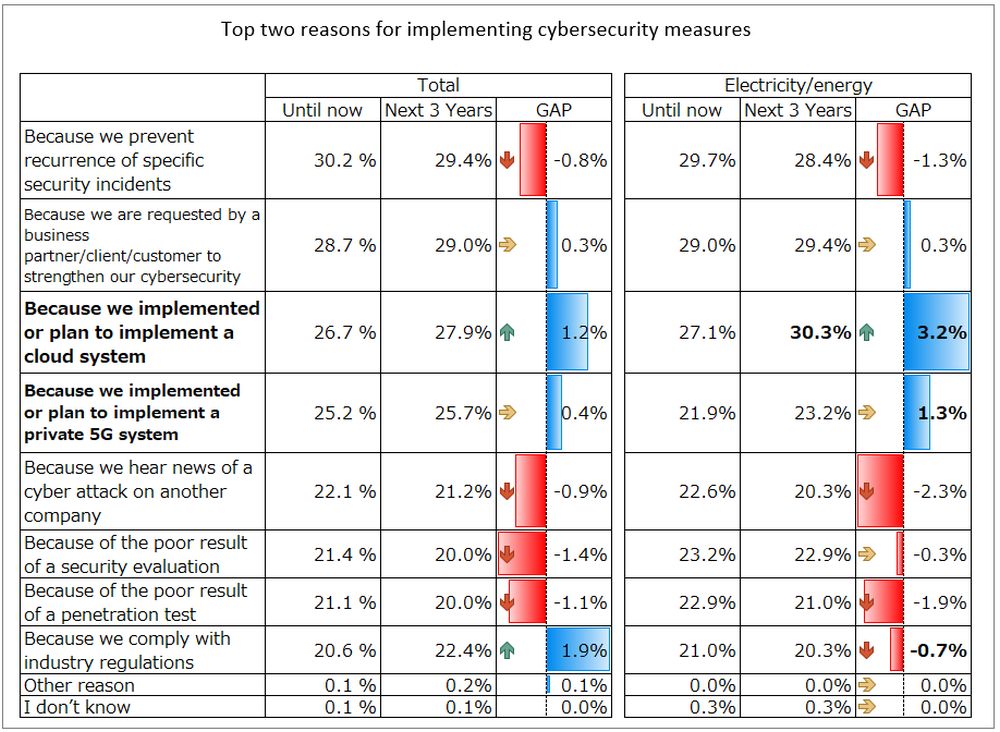
Figure3. Q19. Until now, what has been your organization’s top two reasons for implementing cybersecurity measures to protect your ICS/OT systems?
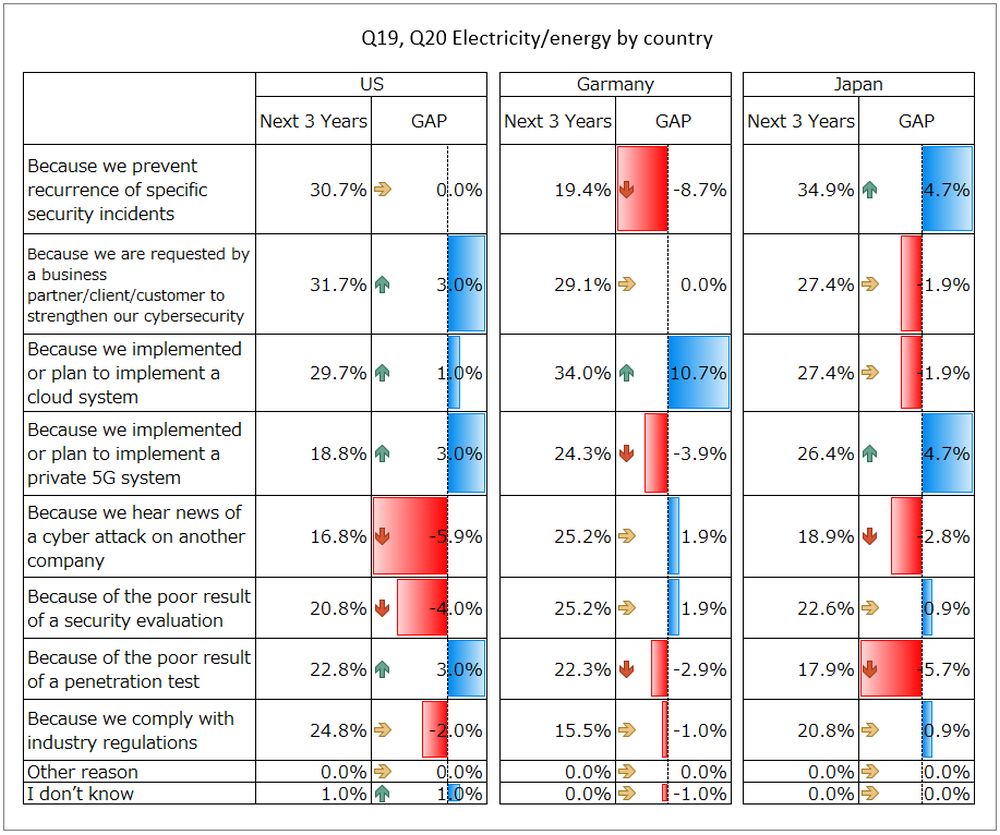
Figure4. Q19. Until now, what has been your organization’s top two reasons for implementing cybersecurity measures to protect your ICS/OT systems?
Q20.What do you believe your organization’s top two reasons for implementing cybersecurity measures to protect your ICS/OT systems are over the next three years?(NB: Multiple choices allowed)
Unlike other industries, the results showed that the drivers of security measures differed from country to country.
Germany's cloud ambitions are not limited to the electric power industry, but also the oil & gas and manufacturing industries. This is because the independent decentralized inter-company data linkage mechanism (GAIA-X), which has been considered and implemented since around 2016, will start full-scale activities in 2021, and the mobile communication strategy by the German government, it is believed that this is due to factors such as investment in the Digital Europe Program that is being promoted in the United States.
This is because the independent decentralized inter-company data linkage mechanism (GAIA-X), which has been considered and implemented since around 2016, will start full-scale activities in 2021.
It is thought that the German government's mobile communications strategy and investment in the digital Europe program promoted throughout the EU are behind this.
Although there have been no reports of incidents such as large-scale power outages against the electric power industry in Japan, cyberattacks against critical infrastructure are increasing around the world. However, it has been reported that the Japanese infrastructure industry, including electric power, is behind in developing countermeasures against security risks, and that risk awareness is low.
A survey in October 2022 reported that 877 locations were at high risk of being victimized by cyberattacks. In the past, information systems and power control systems were perceived to be low risk because their networks were separated. As the integration of power control systems and information systems progresses, prompt action is required.
2 Trend Micro Proposal
Summary
- The electric power industry has a long outage period due to security incidents, and as a result, the amount of damage in terms of money is large. In addition, the range of impact of power outages is very wide, extending to the entire society, including people's lives.
- Although the majority of companies are continuously working to improve security, it cannot be said to be sufficient, considering that the safe operation of electric power infrastructure has a significant impact on the safety of society. Since the timing of improvement is limited, it must be planned and implemented efficiently.
- Although we are proactive in introducing new technologies such as 5G and cloud, we must be aware that the number of companies and products involved will increase accordingly, and security management requirements such as analysis of new attack surfaces will increase.
- As the previously separated control system and information system continue to be integrated, IT tools, services, and vendors will coexist, resulting in a complex system. It is necessary to visualize the security risks of the entire environment and implement measures for safe operation.
Based on this result, Trend Micro proposes to organize and address cyber security challenges in the electric power industry as follows:
- It is important to carry out actual assessments for each system and take measures in order of priority, but currently, the following two points are the main issues:
1. Close the entrance of threats in the existing system and establish a recovery method. It is recommended to create a security plan together with the BCP plan. Leverage scheduled outages to maximize opportunities for limited periods.
2. When introducing a new system or new technology such as 5G, security measures are incorporated from the planning stage. Perform threat and risk analysis holistically rather than locally. In addition, damage can be minimized by visualizing and dealing with risks that change dynamically during operation, and by constructing a system that can detect incidents at an early stage and respond quickly.
And to achieve these goals, we will proceed with strong leadership from management.
The details of IT/OT security in the Electric Utility industry and Trend Micro's proposal are described in detail here.
A full version of these findings can be downloaded here. It details the challenges faced by manufacturing, power, and oil and gas companies, their causes, and the state of industrial cybersecurity.

Want to know more about trends? Contact us.

