Cloud
Why Organizations Should Take Cloud-Based Cryptocurrency-Mining Attacks Seriously
One of the recent trends we’ve observed is the rise of cloud-based cryptocurrency-mining groups that exploit cloud resources, specifically the CPU power of deployed cloud instances, to mine cryptocurrency.
With cloud-based systems becoming a key component of organizations’ operations and infrastructures, malicious actors have been turning to the cloud, taking advantage of weaknesses in cloud security to perform various malicious activities — ranging from data exfiltration and cyberespionage to distributed denial-of-service (DDoS) attacks.
One of the recent trends we’ve observed is the rise of cloud-based cryptocurrency-mining groups that exploit cloud resources, specifically the CPU power of deployed cloud instances, to mine cryptocurrency (with monero being their cryptocurrency of choice because of the CPU mining–friendly returns). We discuss this trend in detail in our research paper “A Floating Battleground: Navigating the Landscape of Cloud-Based Cryptocurrency Mining.”
Cost and consequences
At first glance, it’s easy to think of a cryptocurrency-mining attack as more a nuisance than a serious attack, compared to other forms of intrusion such as ransomware, since it involves resource consumption rather than theft or encryption of sensitive data. However, the actual cost of a mining attack can often be underestimated.
Using a system we built to estimate the resource consumption and cost of a cloud-based cryptocurrency-mining attack, we found that it cost approximately US$20 per month to run a system at about 13% utilization. This jumped over sixfold to US$130 per month when at 100% utilization, which is what one would expect from a mining attack. Note that this is just for a single machine. Organizations, especially large ones, usually deploy multiple cloud instances, leading to a huge spike in resource consumption and expenses.
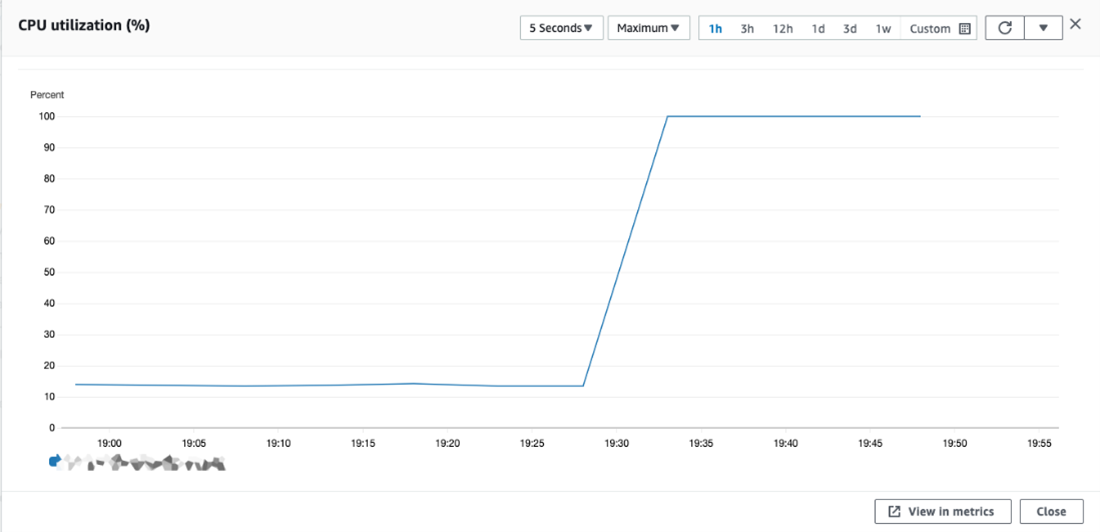
But that’s just the tangible cost of a cryptocurrency-mining attack. There are also indirect consequences that an affected organization might encounter, such as the disruption and slowdown of operations that could result in loss of revenue or even damage to the reputation of the organization because of the inconveniences brought upon its customers.
Cloud-based capture-the-flag
The major players in the cloud-based cryptocurrency mining landscape are diverse in terms of their tools, techniques, and even the way they interact with the public. While some of these groups are more basic in their approach, others are constantly refining their ability to exploit vulnerabilities and other gaps in security to enter target systems.
On one hand, there’s Outlaw, which prefers to stick with what it knows — compromising internet-of-things (IoT) devices and Linux servers via brute-force attacks or by exploiting known vulnerabilities — and add only minor changes to its campaigns. On the other hand, TeamTNT, a malicious actor group that relies heavily on credential theft for lateral movement and abusing configured services, has been steadily improving its sophistication. Other groups, including prolific ones such as Kinsing and 8220, use tools like rootkits and botnets, while also having a sizeable pool of exploitable vulnerabilities.
A large part of what drives cloud-based cryptocurrency-mining groups to evolve is competition with one another. Since cloud instances count as limited resources, each group has to ensure that its cryptocurrency miner is the one that is using up these resources. It’s therefore not surprising that the skills and infrastructures of some malicious actors in this sphere are quite advanced.
Raising red flags
On its own, cryptocurrency mining has relatively small profit margins because the currency earned via mining is offset by resource expenditure. Illicit mining alleviates this by offloading all costs onto the victim, allowing the attacker to reap the full benefits of the mining process. But the true monetary gains could come from secondary markets: More advanced malicious actors could use their resources to act as access brokers, offering their infrastructures, tools, and services to other actors who could come in and do more extensive damage.
In any case, organizations shouldn’t take the presence of cryptocurrency-mining malware in a system only at face value that there is malware in the system. Organizations should also consider what it means in terms of their cloud security. The presence of cryptocurrency-mining activities should be a warning sign — the proverbial canary in a coal mine — to organizations that their cloud infrastructures are vulnerable to attacks. They should take the detection of cryptocurrency mining seriously since this might be the only time that they might be able to respond while the actual impact is still relatively minimal.
Fortunately, organizations can take proactive measures to bridge the security gaps in their cloud deployments. These range from following general security and cloud best practices such as timely patching and avoiding cloud API exposure to the internet, to specific recommendations such as implementing rules that monitor systems for any red flags. Cloud security products can also assist organizations with filtering their network traffic to minimize attack surfaces.
To learn more about the cloud-based cryptocurrency-mining threat landscape, read our full report “A Floating Battleground: Navigating the Landscape of Cloud-Based Cryptocurrency Mining.”

