Proactive security delivered
One platform for the new era of managed security
Build and deliver high-margin proactive security services across your customer bases – all while efficiently operating your managed security business from an all-in-one, optimised platform.
Trend Vision One™ equips service providers with seamless channel-ready functionality to the only AI-powered enterprise cybersecurity platform that centralises cyber risk exposure management, security operations, and layered protection.
Stop reacting and start predicting
Eliminate blind spots. Leverage native sensors and third-party integrations to build a comprehensive view and detailed asset inventory of your digital estate across diverse IT environments.
Focus on what matters most. Enable proactive, informed actions with intelligent risk prioritisation, threat impact analyses, and clear, contextual guidance to accelerate remediation.
Prevent attacks before they happen. Rapidly address evolving risks with automated actions, generative AI-guided remediation, and configurable playbooks to orchestrate across security controls.
Consolidate and improve operational efficiency
Consolidate and simplify security management. Take a platform approach to streamline security management, remove complexity, and reduce costs by consolidating your tech stack.
Automate and orchestrate security operations (SecOps). Unify SIEM, SOAR, and XDR via our Trend Vision One™ platform to untangle SecOps, break silos, and reduce tool sprawl. Automated playbooks further boost efficiency.
Bridge Cybersecurity Talent Gaps. Expand your team’s expertise. Trend Companion™ , our AI-powered cybersecurity advisor, thinks like an analyst. It will guide your team through an investigation, suggest next steps, and create automations through playbooks for the future.
Translate risk into revenue
Lead as an advisor with new expertise. By demonstrating clear risk reduction over time, establish your company as a trusted advisor and build stronger, more profitable customer relationships.
Unlock differentiated services. Move beyond traditional security services and unlock differentiated, new revenue streams in growing risk-based security markets.
Expand business more efficiently. Easily scale and cross-sell complementary security solutions with a modular platform.

Powered by Trend Vision™ One
Trend Vision One™ Cyber Risk Exposure Management (CREM)
Take control of risk
Gain visibility and actionable risk insights to proactively predict threats and prioritise mitigation.
Unified Security Operations
See more, act faster
Leverage SIEM, SOAR, XDR, EDR, and more for in-depth threat management.
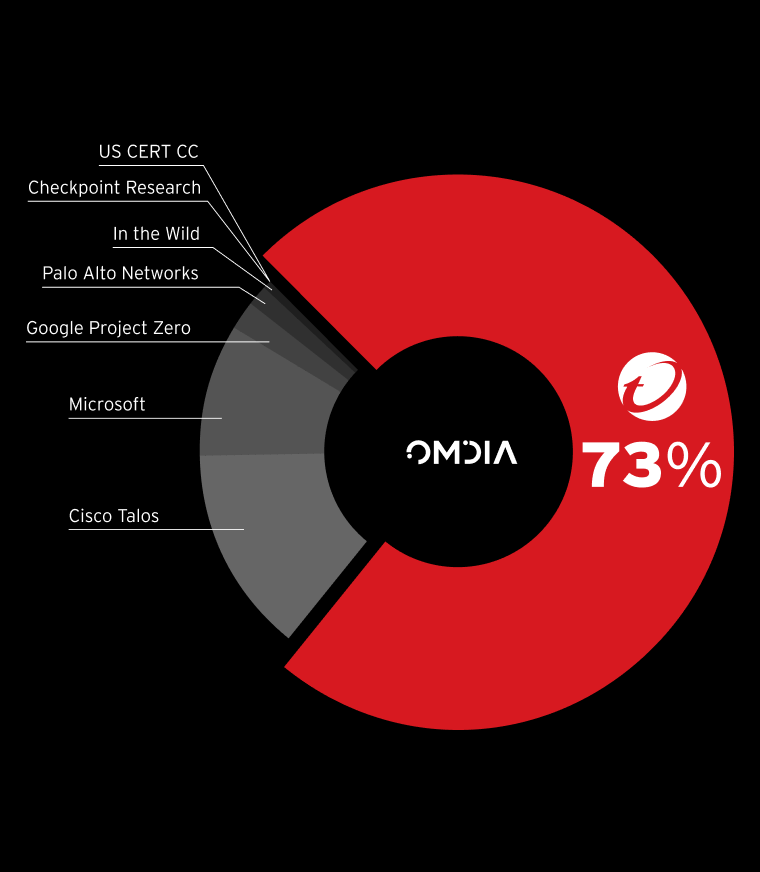
Trend Micro™ Threat Intelligence
Outsmart threats
Stay ahead of adversaries with Threat Intelligence, a globally trusted source of expertly curated threat insights within Trend Vision One.
Comprehensive security coverage
Secure everything, risk nothing
Protect endpoints, networks, cloud, email, and more, all from a single, optimised platform.
Partner-centric tools
Seamless management
Streamlined multi-tenant management and integrations with over 100 third-party applications empower partners to scale services effortlessly within Trend Vision One.
Built for diverse service providers
Gain the tools and capabilities needed to deliver security services across a wide range of partner business models, supporting managed service providers (MSP), managed security service providers (MSSP), digital forensics and incident response (DFIR), and more.
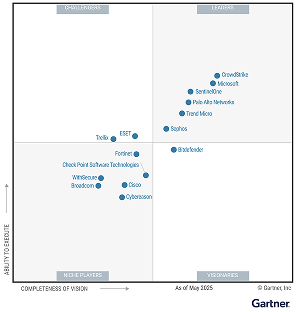
Proven vision, technology, and execution
Get started today