Understand your data. Act with intent.
The first Agentic SIEM that thinks in language - not just logs
powered with
Agentic SIEM
Designed to ingest limitless data and deliver real-time detection, compliance-ready retention, and smarter response.
XDR
Unify native and third-party telemetry in one console, powered by the industry’s broadest sensor coverage from endpoint to identity and beyond.
Agentic SOAR
Reduce manual effort and drive faster, smarter actions with AI-guided, intelligent SOC workflows.
In a race against threats, your SOC wins.
Achieve seamless SecOps
Our SecOps capabilities are part of Trend Vision One™, the only enterprise cybersecurity platform designed to reduce stress and reignite passion for security teams. Harness the broadest native sensor coverage to deliver actionable insights, centralised visibility, richer context, and faster response. Integrate Agentic SIEM and SOAR seamlessly with your existing stack.
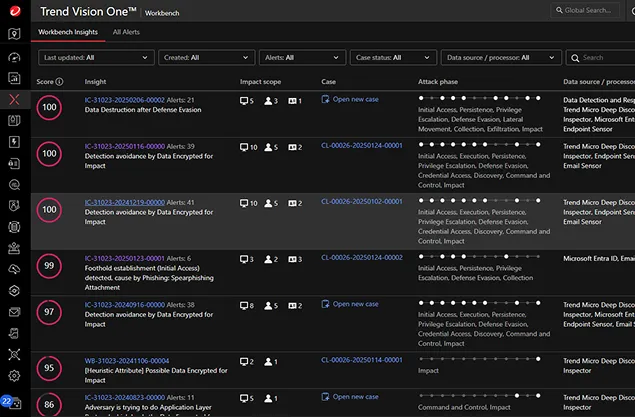
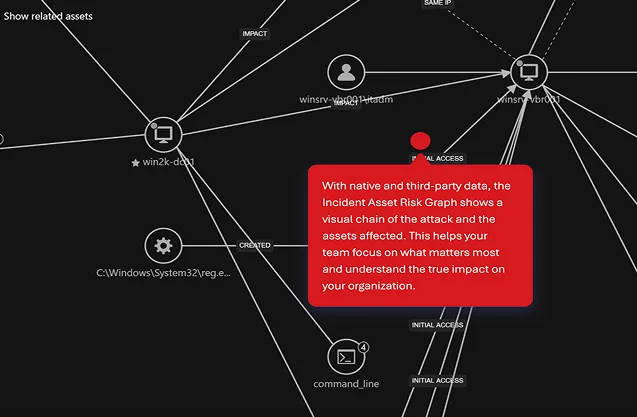
Turn data silos into actionable insights
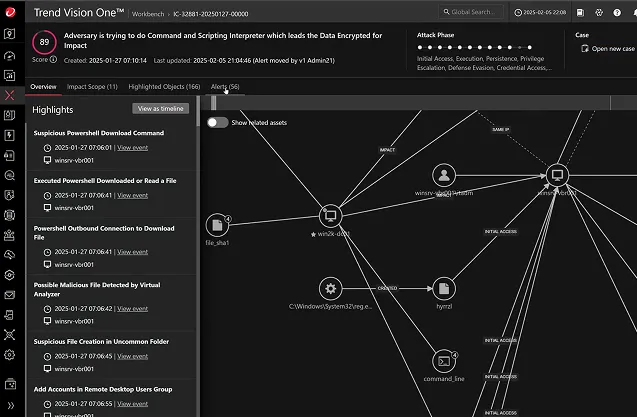
Get the complete picture with end-to-end visibility across the entire attack chain—uncover root cause, assess impact, and anticipate what’s next. Correlate low-confidence alerts and events to detect complex, multi-layer attacks faster. Act with precision using prioritised, actionable insights based on severity, impact, and attack phase.
Automate and accelerate SOC response
Respond from anywhere in the platform—no more tabbing between tools. Built-in AI-powered playbooks automate response to reduce manual work and accelerate action. Limit the effectiveness of threats and empower your team to stay ahead.
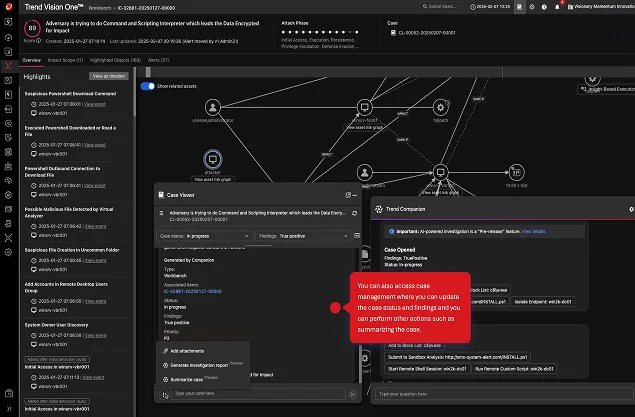
Compliance clarity, delivered automatically.
Make compliance effortless with built-in support for log retention, auditing, and regulatory reporting. Generate board and auditor ready compliance reports directly from the data already ingested into Trend Vision One with one single console.
See everything. Understand more. Make smarter moves with AI.
The power of proactive SecOps
Stop reacting. Start preventing. By integrating with Cyber Risk Exposure Management (CREM), SecOps cuts through alert noise and prioritises what matters most. CREM’s asset and vulnerability risk scores remove the guesswork to enable teams to focus on the real threats. Experience a contextual foundation no other vendor can match today.
Built on an unmatched XDR foundation
The only Agentic SIEM powered by award-winning native XDR. Built on the industry’s broadest native sensor coverage and a modern, agentic architecture, it closes the gaps legacy SIEMs leave behind. Investigations move faster, detections get sharper, and operations are ready for what’s next — all in one console.
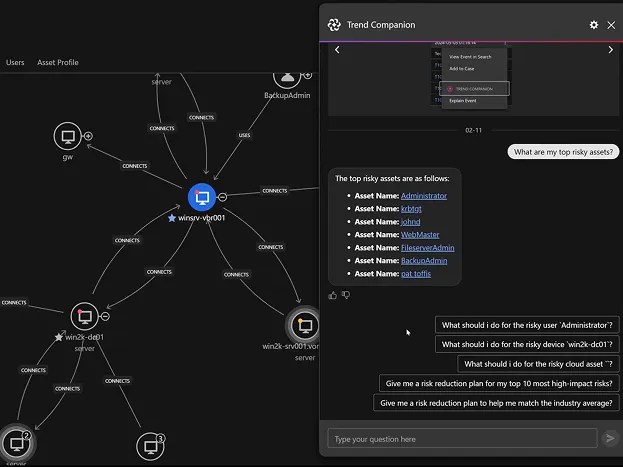
AI-powered SecOps
Our AI Companion thinks like an analyst—guiding investigations, suggesting next steps, and creating automations to reduce manual work. Combined with advanced SOC automation and tight third-party integrations, empower your team to move faster, pinpoint threats more accurately, and stay focused on what matters.
One home for your security telemetry
Break down silos by correlating native and third-party data to power XDR with precise, high-fidelity insights – all in a single, unified view. Incidents, attack paths, vulnerabilities, and threats come together seamlessly. Streamlined workflows and clear investigation reports speed detection and response, supercharging SOC efficiency.
Powerful native threat coverage across every layer
EDR
XDR for Endpoints (EDR)
Provides deep visibility and threat prevention for endpoints and servers by automatically correlating data across multiple security layers for faster detection, improved investigation, and shorter response times.

NDR
XDR for Networks (NDR)
Attackers love unmanaged assets because they’re the perfect place to hide. Everything from routers to laptops to smart thermostats are connected to your network. Find and protect every device with NDR.

ITDR
XDR for Identity (ITDR)
With the added benefit of identity threat detection and response (ITDR), you know who your riskiest and most privileged users are. Once a clever disguise, compromised identities are now beacons alerting you to threat activity.

EmDR
XDR for Email (EmDR)
Extend detection and response even further to email accounts by examining user email, threat logs, and user behavior for greater visibility into suspicious activity.

CDR
XDR for Cloud (CDR)
Legacy EDR only tells part of your cloud’s story. Who's watching your workloads, containers, K8s clusters, and VMs? You are with CDR.

DDR
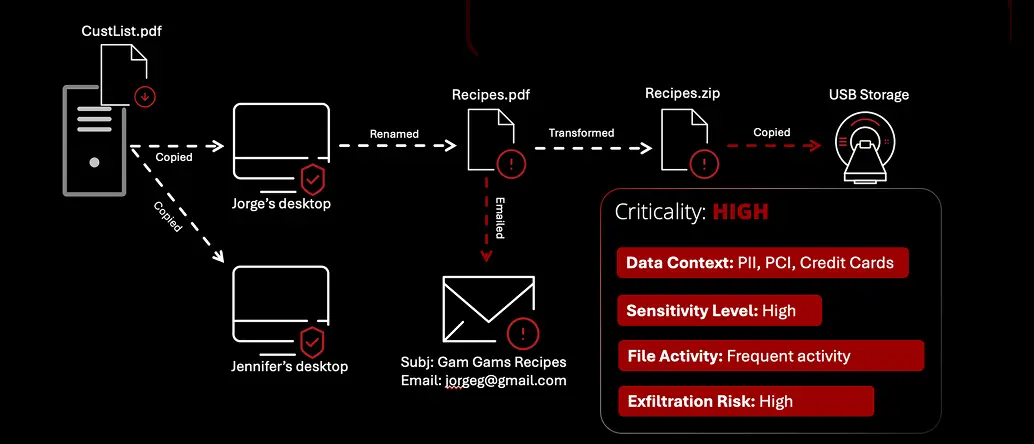
XDR for Data (DDR)
Gain visibility, context, and response to sensitive data as it moves throughout the environment.
Even if the data is somehow compromised, give SOC the tools needed to find how it was exfiltrated and what it was before.
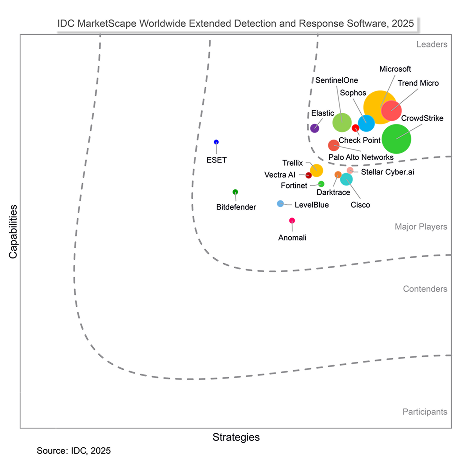
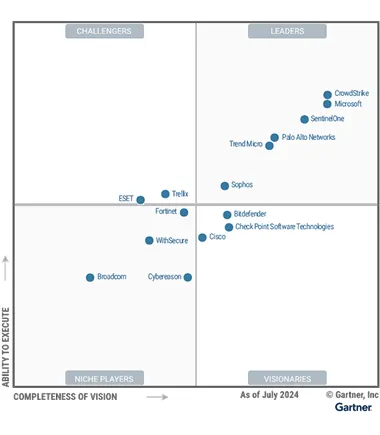
Market-leading performance