APT & Targeted Attacks
How Red Team Exercises Increases Your Cyber Health
Delve into the world of red team exercises, their vital role in enhancing organizational security through simulated cyberattacks, including tactics like phishing and lateral movement within networks, and understand the need for regular testing and improvement to counter evolving threats effectively.
Last year, we shared information on the differences between red team exercises and how organizations may get benefits from each type of activity. External red teaming, assumed breach, and purple teaming each have distinct characteristics that can influence which exercise is suitable for an organization's requirements. Regular execution is essential to validate and improve the security framework, including individuals, procedures, and technologies.
According to The SANS Institute, “ransomware attacks continue to pose a growing danger to all companies, with both existing and new criminal groups on the rise.”
Since 2021, Trend Micro has published a series of spotlights offering threat information on the most infamous ransomware families used in threat actor activities. Ransomware gangs have collaborated and evolved to exacerbate the harm to businesses using ransomware as a service (RaaS) and double extortion tactics.
We will examine common tactics, techniques, and procedures (TTPs) in more depth by analyzing an external red teaming exercise as a case study.
This exercise often follows the following Cyber Kill Chain framework developed by Lockheed Martin:
- Reconnaissance. Collecting data about the target and the tactics for the attack
- Weaponizing. Developing malware by leveraging security vulnerabilities
- Delivery. Delivering weaponized malware via a phishing email or other medium
- Exploitation. Delivering malicious code into the organization’s system
- Installation. Installing a backdoor or remote access Trojan with malware that provides access to the intruder
- Command and control (C&C) - Gaining control over the organization’s systems and network
- Actions on objective - Gathering, encrypting, and extracting confidential information from the organization’s environment
The following are fundamental steps that may be performed according to the Cyber Kill Chain. These steps may vary depending on the organization's needs and requirements:
- Collecting email addresses from social networks like the corporate homepage, LinkedIn, Hunter.io, or other sources
- For external phishing, after we have information on the target, we create a domain that fits the narrative of the phishing email and often includes a link to get login credentials
- If phishing is not permitted due to corporate policies, the external exercise will focus on services reconnaissance, including cloud providers, without harvesting emails
- We explore weaponization by concentrating on remote code execution (RCE) vulnerabilities to get access to a shell or similar tools, mostly to demonstrate potential ways to compromise the customer's network
- Use the service that delivers the payload of the C&C application.
- We use the same technologies often employed by attackers for C&C purposes
- Following the initial phase, we continue into activities around objectives that are generally the same as ransomware operators or the majority of advanced persistent threats (APTs)
This stage is not set in stone, and when the initial objectives are fulfilled, if there is still time in the simulation, the client may request the team pursue other goals, such as a backup network, Citrix, VMware VCenter servers, or a Microsoft Azure/Amazon Web Services (AWS) environment.
Understanding phishing tactics
Phishing may take several forms. This includes a link to download and execute a payload (to obtain credentials/access), delivering the payload directly attached (which is more likely to be discovered depending on the danger), and most recently, employing a QR code that will allow the payload to be download while still circumventing security controls.
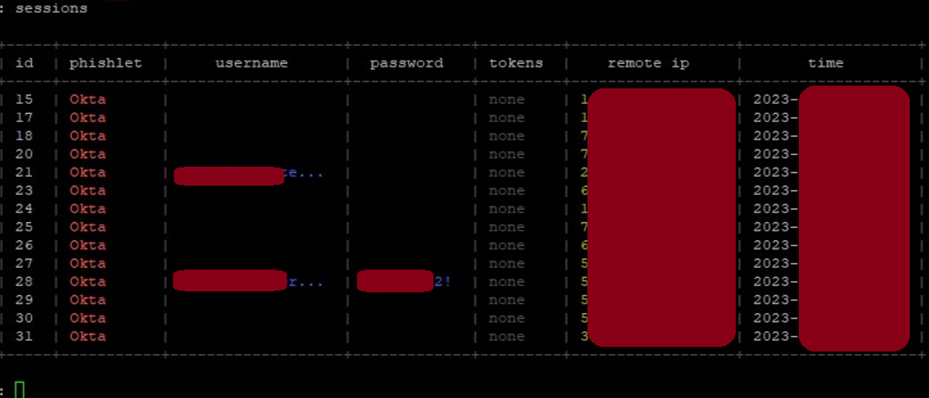
To accomplish the objectives, everything must align well. This includes the target audience, business, and the narrative that supports the desired action of clicking on a link or downloading/executing a threat. This phase provides a chance to enhance the user's understanding and the product's capacity to prevent this danger at an early stage. It’s crucial to emphasize that the red team participation is not a phishing exercise, as that is only one of the stages.
It also must be noted that, to enhance user education comprehensively, it’s crucial to implement a consistent awareness campaign. Red teaming is a comprehensive exercise that goes beyond user education.
Enhancing security through red teaming
Some organizations believe that users are susceptible to falling for a phishing effort and may eventually experience a security breach. These organizations assume a breach and often prioritize the testing of internal systems and processes via a red team exercise. If so, we highly suggest implementing a periodic awareness program to enhance the user's knowledge and general alertness.
Once connected to the network, the focus may shift based on the objectives outlined in the following statement of work (SoW) steps:
- Evading security measures on the localhost
- Elevating local administration rights
- Obtaining local hashes/passwords
- Discovering other systems and resources while adhering to rules of engagement (RoE) and out-of-scope assets
- Moving laterally within the network
The team may need to repeat some procedures at additional servers to escalate our privileges throughout the network, based on the credentials/hashes discovered in step 3. Having specific tools to query the Microsoft Active Directory (AD) environment is crucial for gaining control over the network/domain. This is achieved by using techniques like:
- DCSync
- Establishing a user in the admin. group
- Generating group policy objects (GPO)
- Exfiltrating testing data
- Setting up a virtual machine in Azure
- Planting a file in the domain controller as a flag
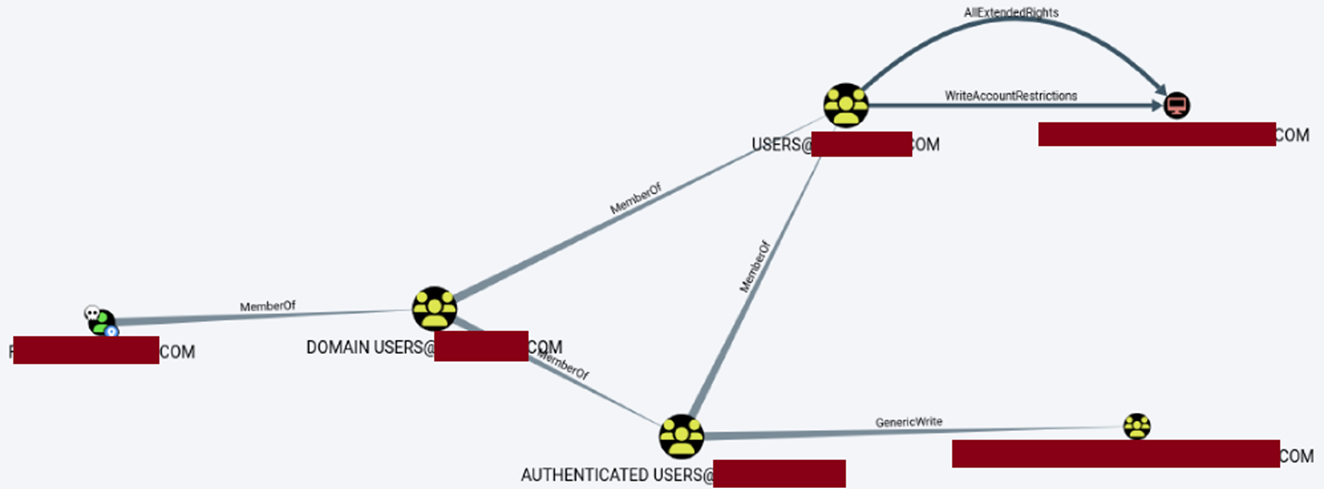
Customer-established objectives should be carefully implemented since they often address the primary challenges in everyday operations and the customer seeks to validate their method for protecting these objectives.
Exploring red teaming
A red team exercise can help mitigate vulnerabilities and weaknesses as well as discover outdated or often-used passwords within the system.
Consider the severity of a scenario when a guess or password-spray attack uncovers over 500 people using the same password. The fact that security tools and procedures have generally improved and are continuously evaluated, the following still needs to be addressed:
- Public shares with sensitive data
- Weak service account passwords
- AD services weak permissions
- Credential guard not enabled
- No protection against NT Lan Manager (NTLM) relay attacks
- Critical vendor security product disabled
- Protection of the entire environment has not been enabled
Making the attacker’s life more difficult
Not all the items mentioned are present in every situation, although some may be discovered for various reasons related to the customer's internal processes. Our findings from each phase are presented at the conclusion of the engagement to enhance customer security posture.
The illustration below demonstrates typical processes for simulating a threat actor in a network to assess the effectiveness of security controls.
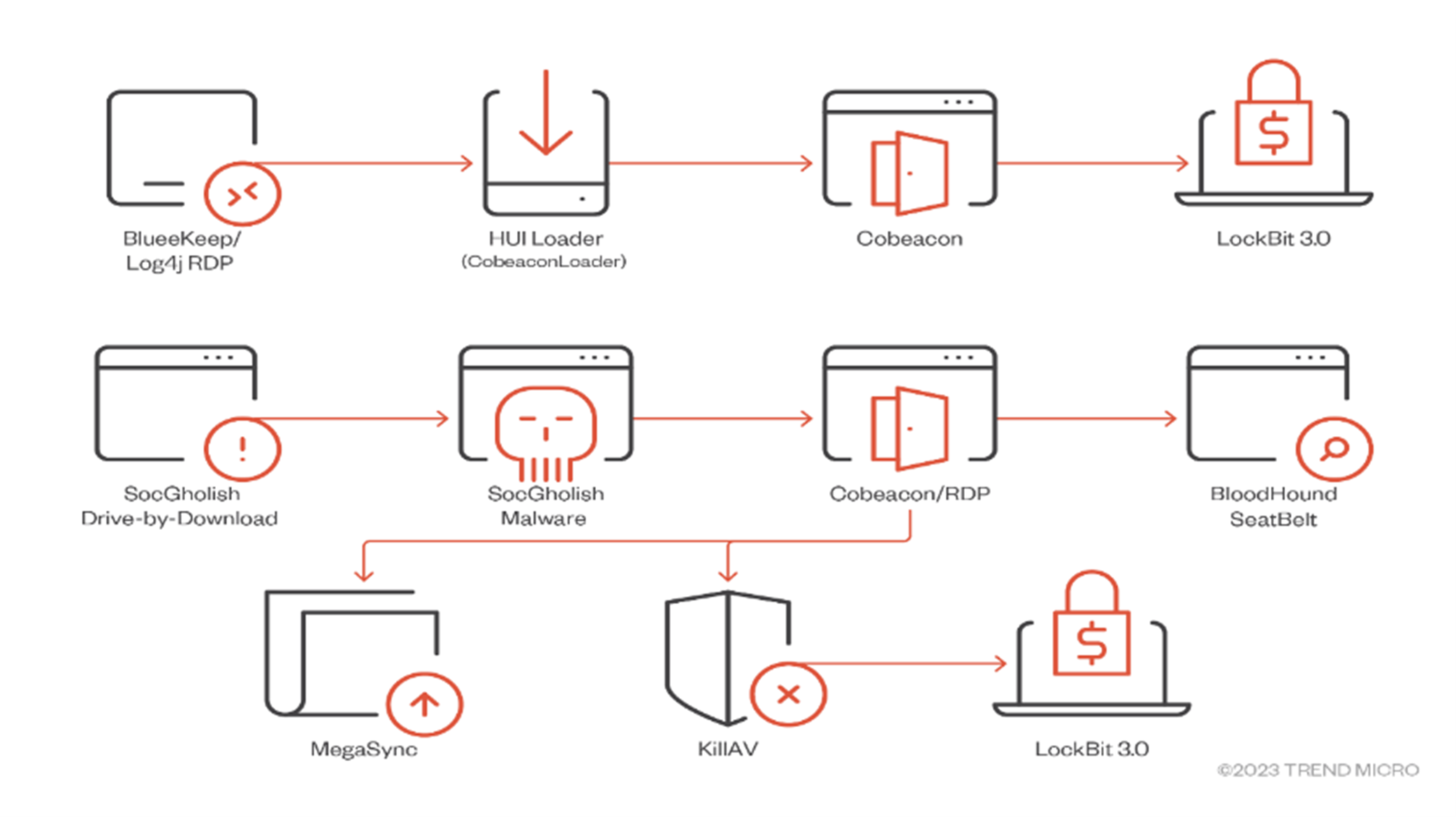
Figure 3 shows that LockBit is now in its third version, which was upgraded in June 2022, but the TTPs remain comparable, and the Cyber Kill Chain is still applicable. No matter which threat actor the customer wants us to simulate, the tools do not need to be very specific. The primary goal of the exercise is to test the blue team's protection tools/procedures against the common (or in some cases, specific) TTPs used in threat actor’s attacks.
Threats are always developing because cybercriminals are consistently improving their toolset. That’s why it’s important for red team exercises to also improve constantly. It is strongly recommended that exercises be performed at least twice a year to check that earlier findings have been resolved and that the business behind the exercise is strengthening its barriers.
Common targets during organizational infiltration
Attacks differ among organizations, as do the goals of the threat actors. This is why "organization data" is now considered one of the most vital resources. Attackers frequently exploit networks to extract valuable data for double extortion or other illicit purposes. This underscores the importance of assessing your tools, procedures, and team's readiness through a Red Team exercise. Ensuring preparedness can significantly improve your ability to withstand and mitigate common attacks effectively.
Are you interested in red teaming or purple teaming?
In an era of escalating cyber threats, organizations must adopt proactive measures to safeguard their digital assets and infrastructure. Trend Red Teaming offers a strategic approach to evaluating and fortifying organizations’ security postures by simulating real-world cyberattacks.
Discover how Red Teaming can empower your organization to enhance its security posture and resilience against cyber threats. Contact us to learn more about our tailored cybersecurity solution.

