AI-Powered Enterprise Cybersecurity Platform

Proactive security starts here
Trend Vision One is the only enterprise cybersecurity platform that centralises cyber risk exposure management, security operations, and robust layered protection – empowering you to predict and prevent threats, accelerating proactive security outcomes.
Visibility
Eliminate security blind spots with a comprehensive view of your entire digital estate.
Prioritisation
Focus on what matters most - our platform evaluates and ranks security issues based on business impact and urgency.
Mitigation
Elevate security into a strategic partner for innovation by moving beyond reactive threat response toward strategic risk management to support the business.
Supercharge your defense with the first proactive cybersecurity AI
Seamlessly integrated with Trend Vision One™, Trend Cybertron – the industry’s first proactive cybersecurity AI – empowers you to stay ahead of threats and eliminate gaps before they’re exploited. It combines specialised AI to detect, predict, and prevent attacks, maximising the impact of your security operations. Backed by 35 years of threat intelligence and 20 years of AI innovation, it enables you to take a truly proactive stance against today’s most sophisticated cyber risks.
70%
Reduction in cybersecurity costs
99.6%
Reduction in daily alerts
65%
Reduction in dwell time
92%
Reduction in cyber risk

Economic valuation from ESG
See how Trend Vision One delivers measurable ROI.
Take control of your cyber risk with Cyber Risk Exposure Management (CREM)
Cyber threats evolve rapidly. Your security approach should, too. Reduce your cyber risk footprint with continuous monitoring, predictive capabilities, and actionable insights.
- Identify and prioritise security risks
- Predict and neutralise threats before they escalate
- Translate risks into business impact
Attackers have nowhere left to hide with security operations (SecOps)
Speed up investigations and stop adversaries with the broadest perspective and better context - hunt, detect, investigate, and respond swiftly and decisively.
- Context-rich detection for faster response
- AI-driven threat hunting and analytics
- Automated workflows for improved efficiency
Connect the dots with comprehensive
protection across your IT environment
Ensure your cybersecurity posture is ahead of the curve with industry-leading protection

Endpoint Security
Secure every endpoint laptops, PCs, mobile, servers, and workloads against sophisticated threats. Gain centralised visibility, threat correlation, and rapid response to contain attacks before they spread.

Cloud Security
Comprehensive security for rapid prediction, protection, and response to threats. Enhance visibility, cloud risk management, and operational efficiency on your cloud and hybrid cloud security journey.

Network Security
Gain unparalleled network insight, detect threats, protect unmanaged devices, and prevent attacks. Accelerate real-time threat prevention, intrusion detection, and zero trust access controls.

Email Security
Proactively manage human risks and stop threats with speed, ease, and accuracy. Stay ahead of phishing, BEC, ransomware, and scams with AI-powered email security.

Identity Security
Eliminate breaches in today's boundaryless workplace with complete visibility, intelligent prioritisation, and automated mitigation of identity risks.

AI Security
Safeguard your AI stack and strengthen your security with proactive AI capabilities that identify and eliminate vulnerabilities before attacks happen.

Data Security
Comprehensive protection for sensitive data spanning on-premises and cloud environments.
Predict, prevent, and protect with elite actionable threat intelligence
Stay ahead of emerging threats with deep insights from Trend™ Research, one of the world’s largest cybersecurity research networks.
Global threat visibility
Access context-rich visibility into active attacks, threat actors, and global trends from Trend’s research network.
Real-time threat detection
Predict and prevent attacks using AI-driven analytics to identify emerging threats before they impact your business.
Proactive defense strategies
Stay ahead of adversaries with industry leading Trend Zero Day Initiative™ (ZDI) intelligence, detecting and mitigating vulnerabilities before they can be exploited, up to 3 months ahead of a patch.
Our expertise is your security advantage
Augment your security teams with services that deliver peace of mind. Focus on strategic priorities while improving overall security efficiency.
Managed detection and response (MDR)
The expertise, technology, and resources you need to detect threats in real time across all security layers.
Incident response services
Expert assistance to contain, remediate, and recover from attacks.
Comprehensive 24/7 support
Priority issue resolution, on demand training, and expert guidance.
One licence, unlimited access
Unlock a flexible, scalable, easy-to-use universal licencing model. Allocate or reallocate credits across 30+ Trend Vision One Solutions and capabilities – anytime, hassle-free.
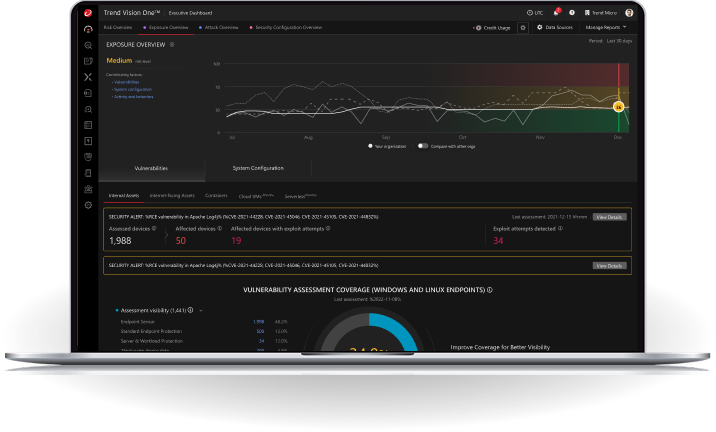
See it in action:
Experience the future of proactive security now
Get a personalised demonstration of how we’ll help you preempt security threats, reduce operational complexity, and align your security with your business objectives.
Measurable results. Measurable impact.
Leader in cloud security
Top performance in end-to-end cybersecurity



Ready to evolve your cybersecurity?
Go beyond reactive defence with Trend Vision One. Gain visibility, focus on what matters most, and accelerate proactive security outcomes.