
Network security basics are the critical elements of network or cyber security. They should be implemented within all networks including home, business, and internet.
Table of Contents
Network security basics
Network security is a complex topic that involves many different technologies with configurations that are sometimes complicated.
The security issue to address is the separation between what is on the network and the endpoints or host systems that are attached to it. The technology for both the network and the endpoints includes access control and encryption, but on the network, there is also segmentation and perimeter security.
Network security vs. endpoint security
Network security is only part of the security equation, and it is usually considered to apply to the devices that protect the network itself. A firewall can be a standalone device that sits beside networking equipment such as routers or switches, or software within the same physical box that also routes and/or switches. On the network there are firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), virtual private network (VPN) appliances, data leak prevention (DLP) systems, etc.
The network exists to connect systems to each other. It is what enables you to browse Amazon or shop online at your local grocery store. But end systems must also be protected; that is called endpoint security. These devices include laptops, tablets, phones, but also the internet of things (IoT) devices.
IoT includes devices such as connected thermostats, cameras, refrigerators, front door locks, light bulbs, pool pumps, smart duvets, etc. These devices require security controls as well, but not all devices are sophisticated enough to contain something like a host-based firewall or anti-malware agent. If the endpoint is a light bulb, then it probably relies on network security for its protection.
Access control
The first place to start is with access control. Businesses commonly referred to this as identity and access management (IAM). Controlling access is not new. Humans have controlled access to buildings since the first lock was installed on a door over six thousand years ago. Access control is now performed on networks, computers, phones, applications, websites, and files.
Fundamentally, access control is broken down into IAAA:
- Identification is the assertion of a user's name or identification such as a User ID or email address.
- Authentication provides proof that the user is who they claim to be. This is still most commonly done with passwords.
- Authorization is granting permissions to the user, or not. It could be that the user is not authorized and therefore has no permissions, or the user could be granted permissions for read, write, full control, etc.
- Accountability is tracking what happened. The log shows that a user attempted access or gained access. The log could also include all the actions the user takes.
Authentication types
Within IAAA, authentication might be the most important topic today. Passwords are still the most common authentication on most systems. They are typically not very secure, however, because they are easy to crack.
If a password is short enough, the hacker has little trouble figuring out what it is. Hackers use a password-guessing attack that entails brute force – trying all possible combinations. Or the attacker could use a password-cracking attack, which entails using a program to recreate passwords that hash to the same value.
There are three authentication types or factors in use today. They are:
- Something you know – a string of characters, numbers or a combination of those that are stored in your brain. Today they should be stored in a password manager.
- Something you have – a device or a piece of software on a device you need to have to authenticate. This includes devices such as an RSA token or the Google authenticator on a smart phone.
- Something you are – an aspect of your person. This is biometrics, either physiological like a fingerprint, or behavioral like a voice print.
The best choice is two-factor authentication (2FA), sometimes referred to as multi-factor authentication (MFA). We highly recommended it for your personal accounts such as Amazon or Facebook.
Applications such as the Google authenticator are free to use and a much better choice than receiving a text or short message service (SMS) message to your phone. The National Institute of Standards and Technology (NIST) recommends against SMS.
We also recommend 2FA for the office, but it is a decision at a policy or management level to require this or not. It depends on many factors such as the asset, its data classification, the risks, and the vulnerabilities.
Network segmentation
Network segmentation improves security by controlling the flow of data between different networks. This is most commonly accomplished with virtual local area networks (VLANs). There are many variations on this theme, such as private virtual LAN (PVLAN), virtual extensible LAN (VXLAN), and so on. A VLAN exists at the data link layer – layer 2 of the open system interconnect (OSI) model. Most network administrators map an internet protocol (IP) subnet to a VLAN.
Routers enable traffic to pass between VLANS according to the configuration. If you want control, router configuration is critical.
Another option found within the cloud is called a virtual private cloud (VPC). Traffic control to and from the VPC is also controlled by configurations.
Understanding the business requirements for the workload is essential to configure and control access to or from VLANs and VPCs.
Perimeter security
Perimeter security is based on the logic that there is a defined edge between an internal/trusted network and an external/untrusted network. This is traditional network design that dates to when the network and data center were confined within a single building. In this configuration, a router connects the internal and external networks. Basic configuration of an access control list (ACL) within the router controls the traffic that can pass through.
You can add security at the perimeter with firewalls, IDS, and IPS. For more information on these, see the Network Security Measures page.
Encryption
Encryption is essential to keep sensitive data and communications away from prying eyes. Encryption protects files on your computer’s hard drive, a banking session, data stored in the cloud, sensitive emails, and a long list of other applications. Cryptography also provides verification of data integrity and authentication of the data’s source.
Encryption falls into two basic types of cryptography: symmetric and asymmetric.
- Symmetric cryptography has a single key that encrypts and decrypts. As a result, it must be shared with someone else to complete the encrypted communication. Common algorithms include the Advanced Encryption Standard (AES), Blowfish, Triple-DES (Data Encryption Standard), and many more.
- Asymmetric cryptography has two distinct keys, one public and one private, that work as a matched set. The set of keys belongs to one user or one service: for example, a web server. One key is for encryption and the other is for decryption.
- If the public key encrypts the data, it keeps the data confidential. This is because the owner of the private key is the only one who can decrypt it.
- If the private key encrypts the data, it proves the authenticity of the source. When the data is successfully decrypted with the public key, it means that only the private key could have encrypted it. The public key is truly public, accessible to anyone.
A third topic is hashing. Even though it is not encryption, it needs to be included at this point in security discussions. Hashing runs an algorithm against a message that calculates a resultant answer, called the hash, that is based on the bits of that message. Bits can be data, voice, or video. Hashing does not change the value of the data in any way. In contrast, encryption alters the data to an unreadable state.
Hashing proves that the bits of the message have not changed. It ensures the data has integrity and that it is in its original format. Only hashing protects data from accidental changes.
If the hash is encrypted with an asymmetric private key, it proves that a hacker has not maliciously tampered with the data. Malicious changes cannot occur unless the private key is compromised.
If the key has not been compromised, then you know that the person who has the private key must be the person who calculated the hash. That key could be a symmetric key, which is sometimes referred to as a private key, or the asymmetric private key.
Wireless security
It is difficult to protect data, voice or video transmitted over a wireless network. Wireless transmissions are intended to emit a signal, and this makes it easier for a hacker within range to capture the transmission. There are encryption standards for wireless, but most have been broken in one way or another.
Encryption standards include WEP, WPA, WPA2, and now WPA3.
- Wired equivalent privacy (WEP) uses the RC4 symmetric algorithm to encrypt the wireless transmission. Hackers quickly broke it and there is now a handy hacking tool called WEP crack for that purpose.
- Wi-Fi Protected Access (WPA) replaced WEP but still used RC4. Hackers modified WEP crack to break WPA.
- WPA2, the second version of WPA, has two options.
- WPA2-personal uses a pre-shared key, sometime called a security key. It is essentially a password that is typed into a wireless device such as a laptop or phone, and into the wireless access point (WAP). Hackers found the first flaw in 2017, called a Key Reinstallation AttaCK (KRACK).
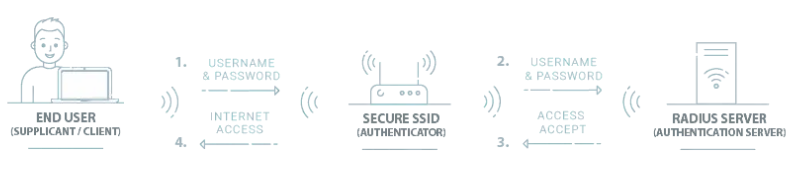
- WPA2-enterprise uses an additional layer of security by authenticating the user at a centralized remote authentication dial-in user service (RADIUS) server. It also uses the extensible authentication protocol (EAP) to pass the authentication information on the local wireless connection. The combination of RADIUS and EAP as a security protocol is called IEEE 802.1x.
- WPA3 also has two options.
- WPA3-personal gives users a higher level of protection using a 128-bit encryption key. This provides robust password authentication, even when user passwords are too simplistic for safety. WPA3-personal achieves this using simultaneous authentication of equals (SAE) instead of the pre-shared key in WPA2-personal.
- WPA3-enterprise[SM2] [TA(3] [SM4] uses a 192-bit encryption key for greater security. It is an enhancement of WPA2 that applies security protocols consistently throughout an organization’s network.
How Does Trend Vision One Enhance Network Security?
To strengthen network security beyond traditional measures, Trend Vision One™ Network Security offers a unified approach that combines Network Detection and Response (NDR), Zero Trust Secure Access (ZTSA), and Cyber Risk Exposure Management (CREM). This integration delivers:
Comprehensive Visibility across all network traffic, including encrypted flows.
Advanced Threat Detection powered by AI and machine learning for faster response.
Zero Trust Access Controls to secure remote and distributed environments.
Cross-Layer Correlation with endpoints, email, and cloud for holistic protection.
By consolidating these capabilities, Trend Vision One helps organizations reduce risk exposure, improve operational efficiency, and stay ahead of emerging threats.