When I first introduced the CISO Compass, it was designed as a strategic guide to help Chief Information Security Officers (CISOs) navigate the complex landscape of cybersecurity management. The compass provided a metaphorical framework that helped CISOs address various aspects of cybersecurity within their organizations, from risk assessment to incident response.
However, since its release, I've received numerous comments and insights from the broader cybersecurity community. Many have pointed out that the principles outlined in the CISO Compass are not exclusive to CISOs. Instead, they can be incredibly beneficial for a wide range of cybersecurity professionals and stakeholders, including SOC analysts, vulnerability management teams, cybersecurity strategists, cyber risk managers, compliance officers, pentesters, red, blue, and purple teams, and even C-suite executives like CIOs, CFOs, and CEOs.
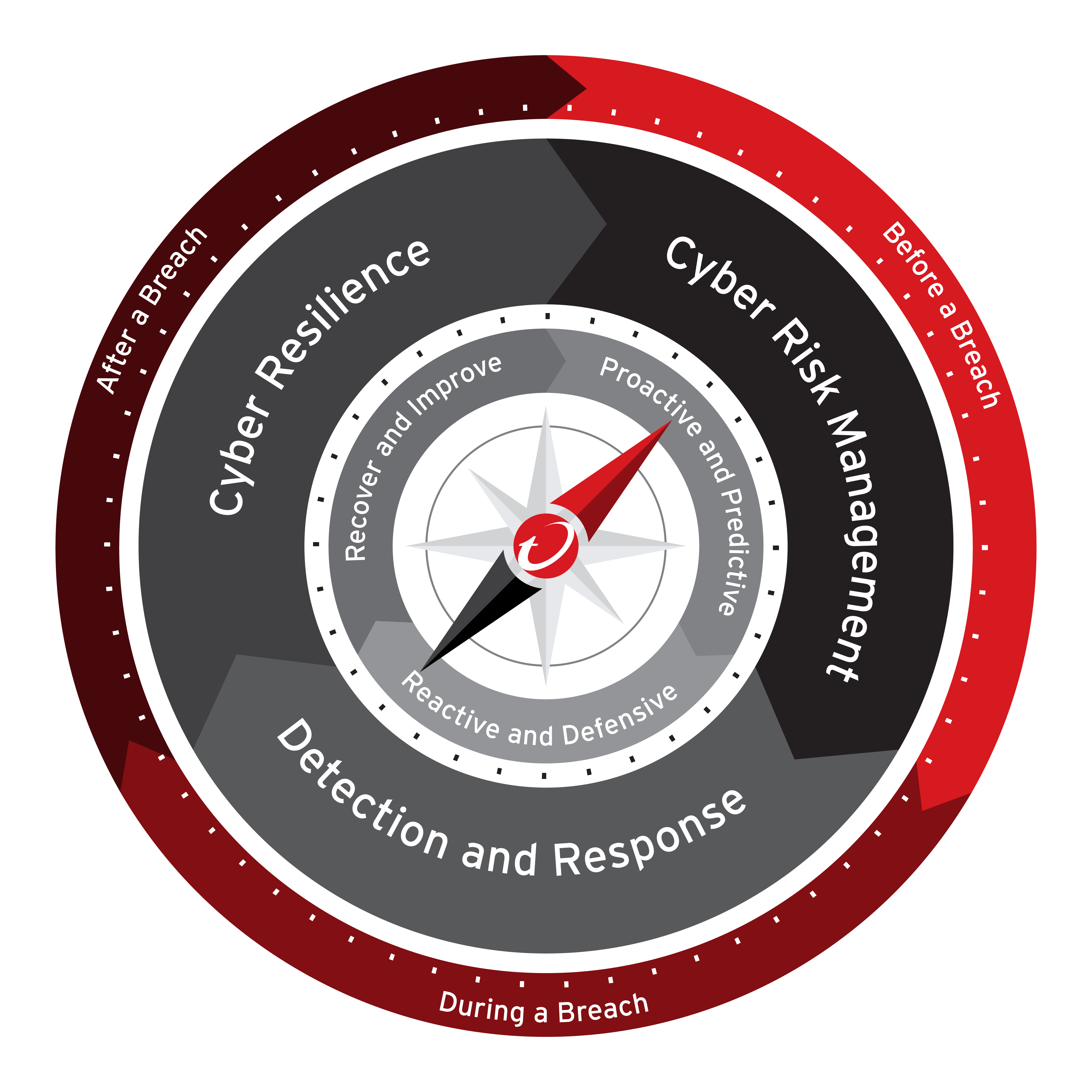
This feedback led to a key realization: the compass should be more inclusive and reflect its broader applicability. Therefore, I've decided to rebrand and expand the concept to what I now call the Cybersecurity Compass. This new version aims to serve as a broader guide for all cybersecurity practitioners and stakeholders, offering them direction, guidance, and strategy. It is a tool for all cyber defenders, providing the same strategic advantages that it initially provided to CISOs.
Why a Compass?
The invention of the compass revolutionized navigation. Before its creation, sailors and explorers relied on the stars, landmarks, and rudimentary maps to find their way. This often led to perilous journeys, navigational errors, and lost expeditions. The compass provided a reliable reference point, allowing for accurate and consistent navigation even in uncharted waters. It enabled explorers to venture further with confidence, opening up new trade routes and fostering global exploration.
Today, in the realm of cybersecurity, the Cybersecurity Compass serves a similar purpose. In a landscape fraught with complex threats and evolving challenges, having a strategic tool to guide decision-making is critical. The Cybersecurity Compass provides a consistent and reliable framework for navigating the intricate world of cyber threats and cyber risks, ensuring that cybersecurity professionals and stakeholders can chart a course toward robust defense and resilience.
The Cybersecurity Compass: A Tool for All
The Cybersecurity Compass retains its core structure but now covers a wider array of roles and responsibilities within the cybersecurity field. Here’s how various professionals and stakeholders can use this tool before, during, and after a breach:
CISOs: Before a breach, CISOs use the Cybersecurity Compass to fortify an organization’s digital assets against potential cyber threats by strategizing defenses, implementing robust security measures, and educating employees on best practices. During a breach, clear and decisive communication helps guide security teams respond to a cyberattack and keep external stakeholders appraised of the situation. After a breach, the compass guides them to be more resilient by reviewing and updating incident response plans and incorporating Zero Trust strategies to enhance detection and response capabilities. Read the full story here.
SOC Analysts: Before a breach, SOC analysts use the Cybersecurity Compass to identify critical threat vectors and prioritize alerts, enhancing their ability to detect and analyze threats effectively. During a breach, they structure their incident response protocols using the compass, ensuring timely and coordinated responses. After a breach, the compass assists in conducting thorough post-incident reviews to understand the root causes and improve future detection and response strategies.
Vulnerability Management Teams: Before a breach, the Cybersecurity Compass helps vulnerability management teams assess and prioritize vulnerabilities based on risk, reducing the organization's attack surface. During a breach, it provides a framework for quickly identifying and mitigating actively exploited vulnerabilities. After a breach, the compass guides the development of robust remediation plans, emphasizing a strategic approach to patch management and vulnerability mitigation to prevent future incidents.
Cybersecurity Strategists: Before a breach, cybersecurity strategists use the compass to align their security initiatives with broader organizational goals, mapping out long-term strategies that are adaptable to changing threats. During a breach, the compass provides strategic guidelines for crisis management, ensuring the response minimizes business impact and aligns with strategic objectives. After a breach, it helps review and adjust strategies to address any gaps or weaknesses, ensuring continuous improvement in security posture.
Cyber Risk Managers: Before a breach, cyber risk managers use the Cybersecurity Compass to conduct thorough risk assessments, providing a structured approach to identifying, evaluating, and prioritizing risks for informed decision-making. During a breach, the compass offers guidance on implementing immediate risk mitigation strategies tailored to the organization's specific risk profile. After a breach, it helps evaluate the effectiveness of these strategies and adjust them based on lessons learned to enhance future resilience.
Compliance Officers: Before a breach, compliance officers use the compass to ensure their organization meets all relevant regulatory requirements, providing a clear framework for interpreting and implementing regulations. During a breach, the compass helps ensure all actions taken comply with relevant regulations and standards, mitigating potential legal and regulatory repercussions. After a breach, it assists in preparing for post-incident audits by outlining the necessary steps and documentation required to demonstrate compliance with industry standards and regulations.
Cybersecurity Educators: Before a breach, educators incorporate the principles of the Cybersecurity Compass into their teaching materials, providing a comprehensive framework that covers all facets of cybersecurity. During a breach, the compass helps create realistic breach scenarios for training, enabling students and professionals to practice and refine their response skills. After a breach, it guides the development of training programs focused on lessons learned from actual incidents, ensuring that professionals are better prepared for future breaches.
Pentesters: Before a breach, pentesters use the Cybersecurity Compass to plan and execute comprehensive penetration testing, identifying vulnerabilities and potential attack vectors. During a breach, the compass aids in simulating real-world attacks to test the effectiveness of security measures and incident response plans. After a breach, it helps pentesters analyze breach data to refine their testing methodologies and improve overall security posture.
Red Team: Before a breach, red teams leverage the Cybersecurity Compass to design and plan attack simulations that mirror the tactics, techniques, and procedures of real adversaries. During a breach, the compass guides red teams in executing these simulations, providing valuable insights into the organization’s security defenses. After a breach, it assists in analyzing the results of these simulations to identify weaknesses and recommend improvements.
Blue Team: Before a breach, blue teams use the Cybersecurity Compass to strengthen defensive strategies, ensuring robust protection against potential threats. During a breach, the compass provides a structured approach for blue teams to detect, respond to, and mitigate attacks, maintaining the integrity of the organization’s systems. After a breach, it helps blue teams conduct detailed analyses of their response efforts, enhancing future defensive measures.
Purple Team: Before a breach, purple teams use the Cybersecurity Compass to integrate and align the efforts of both red and blue teams, fostering collaboration and enhancing overall security posture. During a breach, the compass facilitates coordinated attack and defense simulations, ensuring comprehensive evaluation of security measures. After a breach, it assists in synthesizing the findings from both teams to develop a holistic approach to improving security strategies.
CIOs: Before a breach, Chief Information Officers use the Cybersecurity Compass to ensure that the organization's IT infrastructure is robust, resilient, and aligned with the latest security standards and best practices. During a breach, the compass helps CIOs coordinate the IT response, ensuring that systems are maintained and downtime is minimized. After a breach, the compass guides CIOs in conducting post-incident reviews and implementing improvements to the IT infrastructure to prevent future breaches.
CFOs: Before a breach, Chief Financial Officers use the Cybersecurity Compass to understand and manage the financial risks associated with cybersecurity threats, including potential costs of breaches and investments in security measures. During a breach, the compass aids CFOs in assessing the financial impact and coordinating with other departments to manage the economic fallout. After a breach, it helps CFOs review the financial implications and adjust budgets and strategies to strengthen financial resilience against future incidents.
CEOs: Before a breach, Chief Executive Officers use the Cybersecurity Compass to ensure that the entire organization is aligned with a comprehensive cybersecurity strategy that supports business objectives and protects critical assets. During a breach, the compass helps CEOs lead the organization through the crisis, ensuring clear communication and decisive action. After a breach, it assists CEOs in reviewing the overall impact on the organization, implementing strategic changes, and reinforcing the importance of cybersecurity at all levels.
Broader Impact and Future Developments
The shift from a CISO-centric to a more inclusive Cybersecurity Compass marks a significant evolution in how we approach cybersecurity education and practice. This broader perspective not only opens access to strategic insights but also fosters a more cohesive and informed cybersecurity community.
Moving forward, I plan to develop tailored modules within the Cybersecurity Compass that address the specific needs of various roles. For instance, modules for SOC analysts, CIOs, CFOs, and CEOs might include detailed threat intelligence integration techniques, while those for vulnerability managers could focus on advanced risk quantification and prioritization methods.
In conclusion, the Cybersecurity Compass is a dynamic, evolving tool designed to empower all cybersecurity professionals and stakeholders. By expanding its scope and rebranding it to reflect its broader applicability, we can better equip our community to tackle the ever-evolving challenges of the digital threat landscape.

