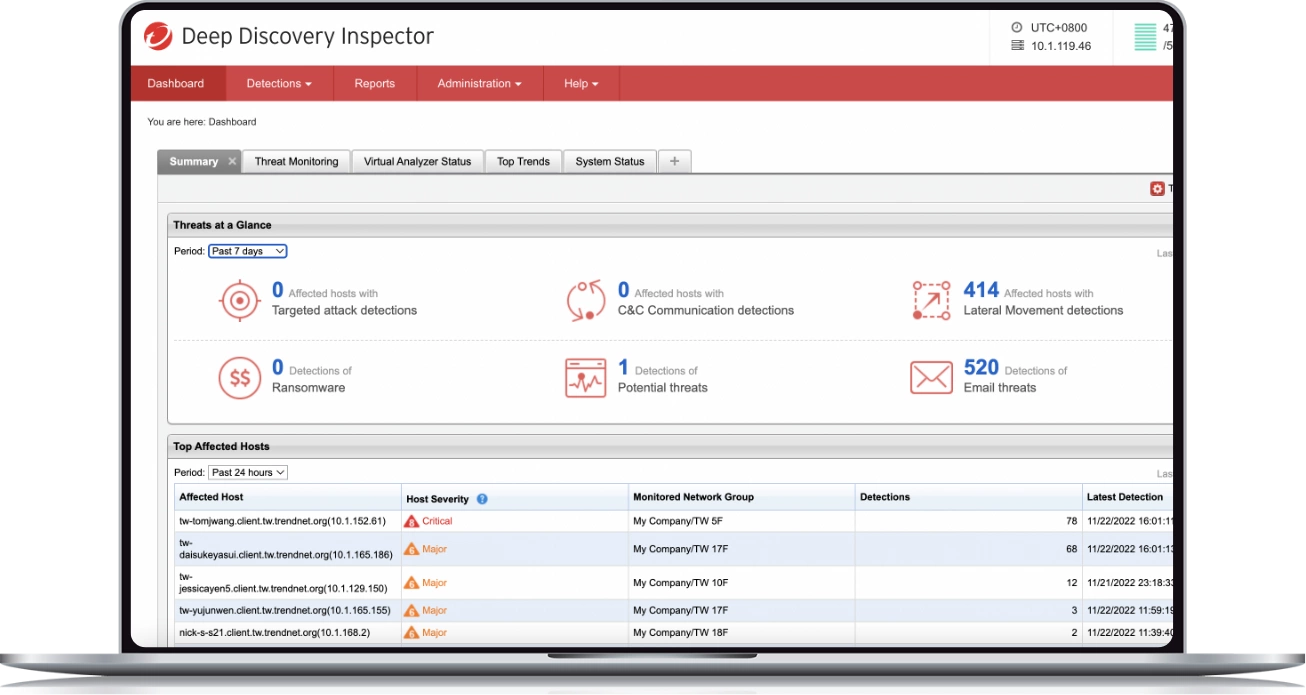
Monitor everything
Trend Micro™ Deep Discovery™ Inspector provides 360 degrees of visibility by monitoring all network ports and over 105 different protocols. A single Deep Discovery Inspector appliance monitors east-west traffic (or lateral movement) and north-south traffic.

Leverage custom sandboxing
Unlike other sandbox solutions, Deep Discovery uses custom sandboxes. Virtual images are used to match operating system configurations, drivers, installed applications, and language versions. Difficult for hackers to evade, they include a “safe live mode” and analyse multi-stage downloads, URLs, command-and-control, and more.

Advanced detection and response
Trend Micro Vision One gives you the ability to correlate advanced threat events and prioritise your response. Just press play and visualise the attack life cycle at the network layer, including managed and unmanaged devices – contractor/third-party systems, IoT and IIoT devices, printers, and BYOD systems.
WHY DEEP DISCOVERY INSPECTOR
Extensive detection techniques
Detect and prevent breaches
Deep Discovery Inspector is available as a physical or virtual network appliance. It’s designed to quickly detect advanced malware that typically bypasses traditional security defences and exfiltrates sensitive data. Specialised detection engines and custom sandbox analysis detect and prevent breaches.
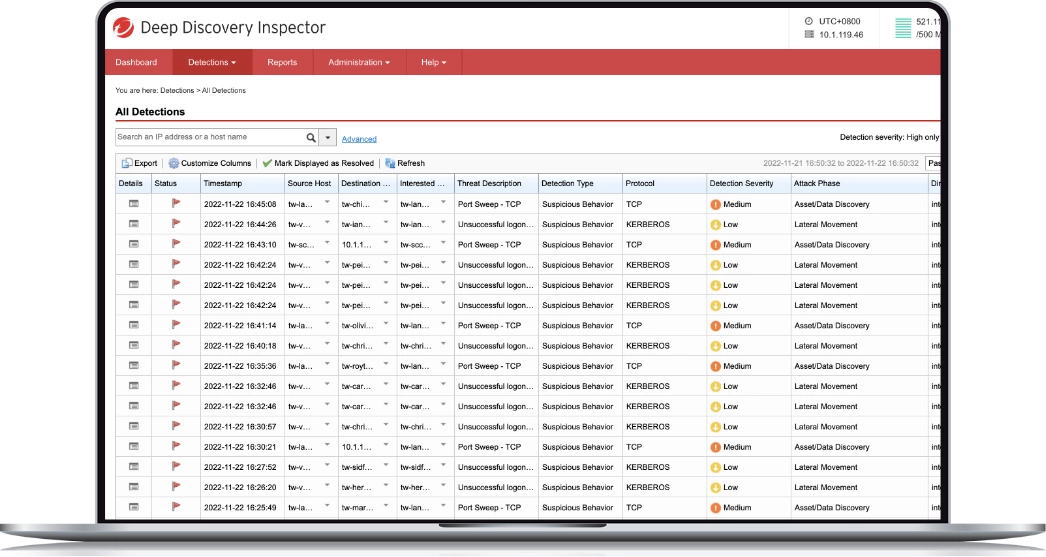
Glean actionable data from the flood of threat intelligence
Network analytics help prioritise threats and provide visibility into an attack. By looking back up to 180 days, you can see the point of entry and impact. And standards-based advanced threat intelligence sharing (e.g. STIX/TAXII and YARA) keeps you ahead of threats while Trend Micro™ Deep Discovery™ automates the sharing of threat information across security solutions, strengthening multiple links in the security chain simultaneously.
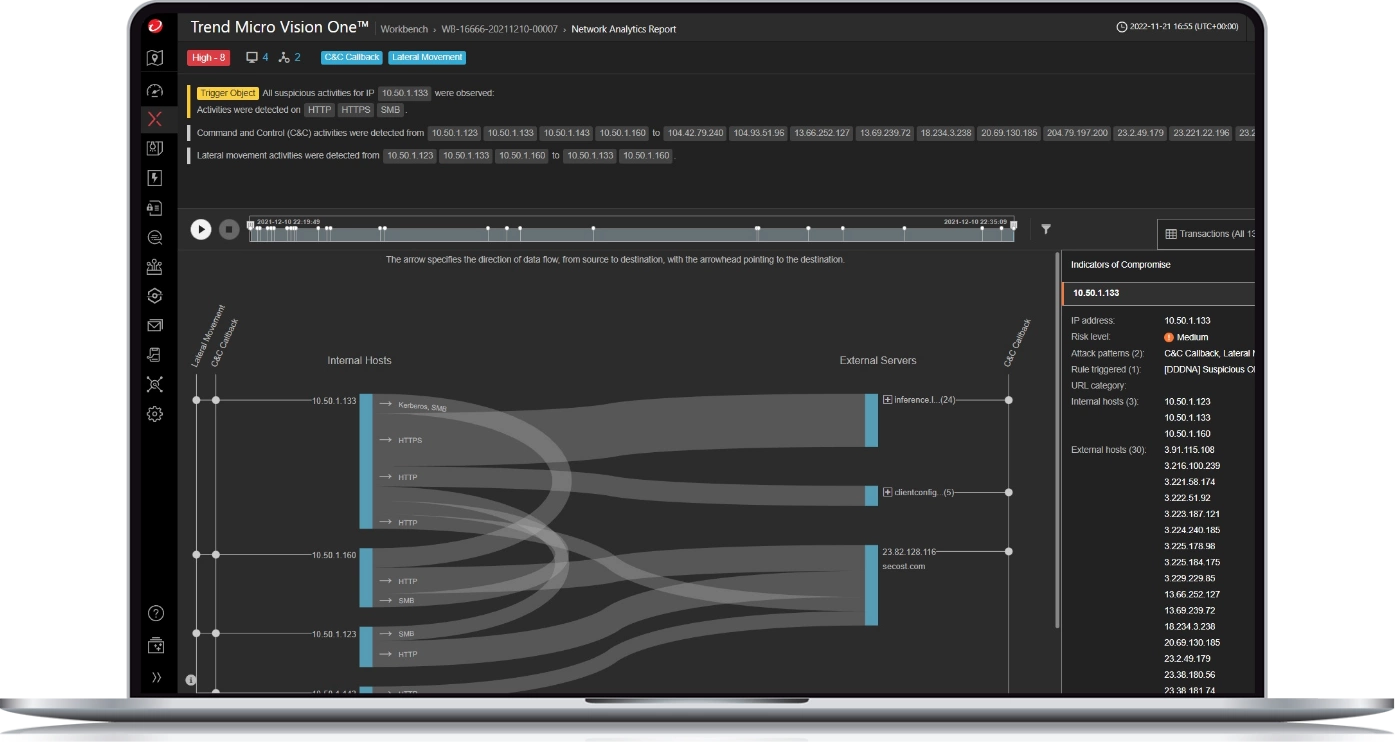
Detect targeted ransomware
Deep Discovery Inspector uses known and unknown patterns and reputation analysis to detect the latest ransomware attacks, including WannaCry. The customised sandbox detects mass file modifications, encryption behavior, and modifications to backup and restore processes.
Trend Micro™ Deep Discovery™ Email Inspector stops targeted ransomware attacks by blocking targeted spear phishing emails before they are delivered.
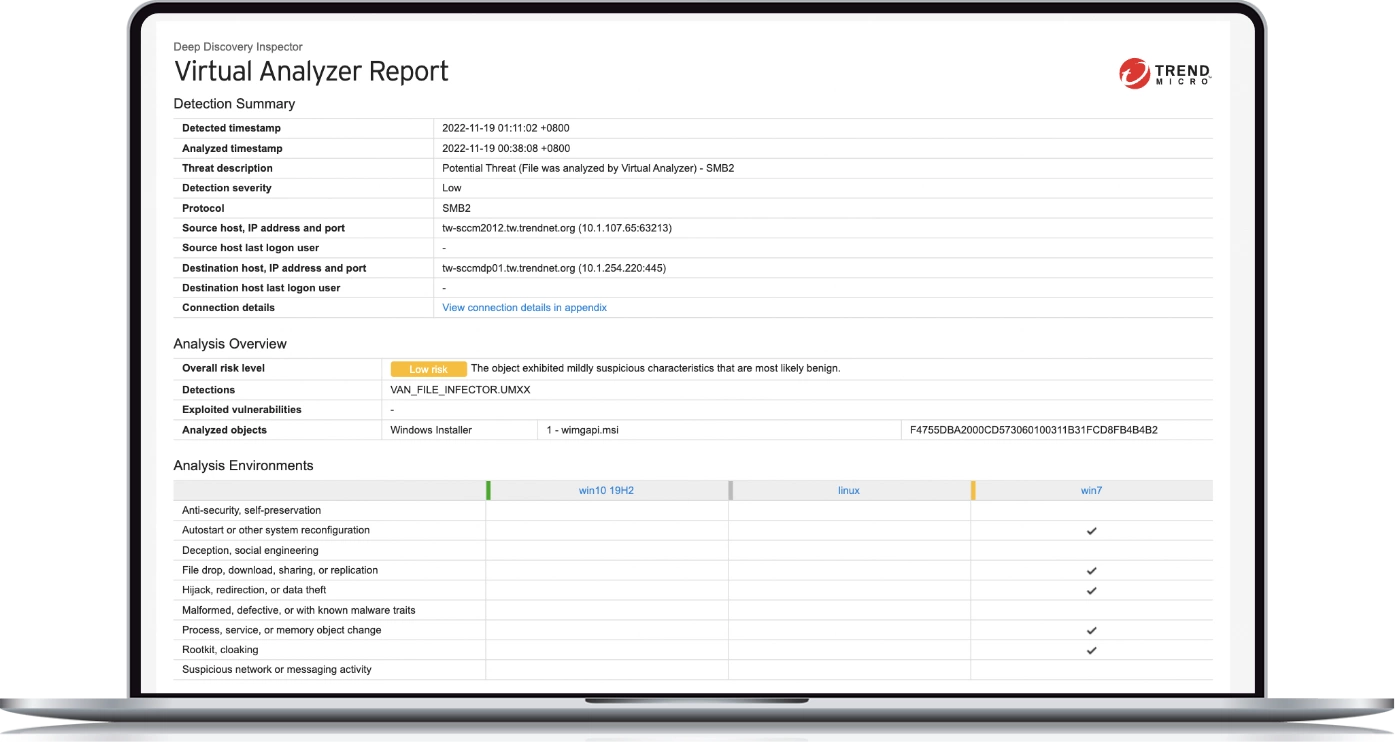
Extend your detection and response capabilities with managed XDR
We offer 24/7 alert monitoring, alert prioritisation, investigation, and threat hunting as a managed service. Trend Micro™ Managed XDR includes standard or advanced service packages across email, endpoints, servers, cloud workloads, and networks.
Other Network Security Products
Trend Micro™ TippingPoint™
Provides high-speed, inline intrusion prevention system inspection and comprehensive threat protection against known and undisclosed vulnerabilities.
Trend Vision One™ – Zero Trust Secure Access (ZTSA)
Enables a modern shift in access control through real-time insights, risk identification, and access controls.
Trend Vision One™ – XDR for Networks
Helps you stay ahead of any security threat with unified visibility, deep threat context, and decisive response.
Market-leading performance
Join 500 million users
Get started with Deep Discovery Inspector