
Operational Technology (OT) security is the practice of protecting systems and technologies that monitor and control physical processes in industrial and operational environments.
Table of Contents
Its purpose is to ensure the reliability, safety, and resilience of systems that directly affect the physical world.
OT (Operational Technology) refers to technologies that interact with the physical world. OT security means protecting the control systems and devices used to monitor and operate environments such as factory automation and plant operations, power generation facilities, steel refining operations, dam discharge control, port container handling, and hospital medical equipment.
The term “OT” is commonly used in contrast to IT security, which focuses on protecting information and systems in cyberspace.
What Is Operational Technology (OT)?
Operational Technology (OT) refers to systems and devices used to monitor, control, and operate physical processes. These technologies have long supported industrial and critical infrastructure environments, even before the term “OT” became widely used.
The term OT security emerged primarily as a way to distinguish OT from IT security. Long before “OT” became a common term, technologies for controlling and operating critical systems that support society and industrial infrastructure already existed.
Two representative examples of OT systems and devices widely used in manufacturing, power, oil, and gas industries are:
- SCADA (Supervisory Control and Data Acquisition) systems for remote monitoring and control
- PLCs (Programmable Logic Controllers) used for automation and process control
These systems monitor physical processes and events—such as train propulsion and operation, or temperature control in steel production—detect changes, and execute control actions accordingly. Where IT is primarily concerned with information and data processing, OT can be defined as technology that interacts with the physical environment.
The term OT often refers to traditional industrial control systems (ICS), but it may also include Industrial IoT (IIoT) systems that use newer technologies such as cloud services and 5G. OT security is expected to protect not only reliability and safety, but also resilience—the ability to recover quickly and return to normal operations after disruption.
What Are Examples of OT Systems?
OT systems include a wide range of technologies used to monitor and control real-world processes across industries. These systems are commonly found in critical infrastructure, manufacturing, healthcare, and operational environments.
OT System Examples:

Power plant monitoring and control room

Plant control system

PLCs on a factory floor

Hospital infusion pump
Note: A PLC (Programmable Logic Controller) is a device used in ICS (Industrial Control Systems) to control machinery. ICS refers to systems that control production facilities and industrial operations.
Why Is OT Security Gaining Attention?
OT security is gaining attention because cyber risks now have direct physical, operational, and safety consequences. As OT and IT systems become increasingly interconnected, cyber incidents can disrupt production and impact society.
In recent years, OT security has become a major focus due to several converging factors.
Convergence of the Cyber and Physical Worlds in Society and Industry
For example, Japan’s Society 5.0 vision aims to drive economic development and solve social challenges by integrating cyberspace and the physical world. In industry, OT and IT systems are increasingly interconnected as part of supply chain transformation and broader digital transformation (DX) initiatives.
As a result, cyber risk can directly impact physical operations—and physical incidents may also have cyber consequences.
Adoption of Open Technologies
Traditionally, OT systems were built using OT-specific—or vendor-specific—platforms and protocols. Today, OT environments are increasingly adopting the same open platforms and protocols used in IT, improving interoperability between IT and OT.
OT environments are already beginning to use technologies such as Windows- and Linux-based servers and endpoints, Ethernet, Wi-Fi, and cellular networks. This expands the attack surface: threats can exploit vulnerabilities unique to legacy OT designs as well as vulnerabilities common to open IT platforms—often with broad operational impact.
High-Impact Incidents and Strengthening Regulations
OT security incidents do not necessarily occur as frequently as IT incidents. However, when they do occur, the impact can be severe. Global examples have shown production stoppages in manufacturing and energy sectors causing significant societal disruption.
In response, governments and industry bodies worldwide have published regulations and guidelines to promote and strengthen OT security. In sectors designated as critical infrastructure, executive-level accountability and governance are increasingly expected.
Ultimately, OT security aims to protect not only traditional OT systems and devices, but also IIoT systems and IoT devices, safeguarding trust and safety across both cyber and physical domains.
How Should Organizations Structure and Drive OT Security?
OT security requires enterprise-wide coordination that spans leadership, headquarters functions, and plant-level execution. Effective programs align governance, implementation, monitoring, and incident response across the organization.
Organizational Structure for Driving OT Security
OT security requires enterprise-wide coordination—from executive leadership to plant-level execution. While structures vary by organization, a common model includes:
- Executive leadership (e.g., CISO / CSO)
- Strategy and planning (Headquarters IT security team)
- Execution (Plant / site security leads)
- Monitoring (OT-SOC)
- Reporting and coordination (OT-SIRT)
In this glossary-style article, key points are explained using two common scenarios:
- The HQ IT security team drives OT security across factory sites
- Plant / site OT security owners drive OT security locally
What Do IT Security Teams Need to Know About OT Security?
IT security teams must understand that OT environments operate under different priorities and constraints than IT systems. Applying traditional IT security approaches without adaptation can introduce operational and safety risks.
When a headquarters IT security team defines policies and deploys controls across factory sites, it must first understand OT-specific realities, assumptions, and constraints. A major difference from traditional IT security is that OT interacts with the physical world.
While IT security is typically centered on protecting the CIA triad—Confidentiality, Integrity, and Availability—OT environments often prioritize Availability above all else, because downtime can directly disrupt operations. OT security must also account for Health, Safety, and Environment (HSE) impacts.
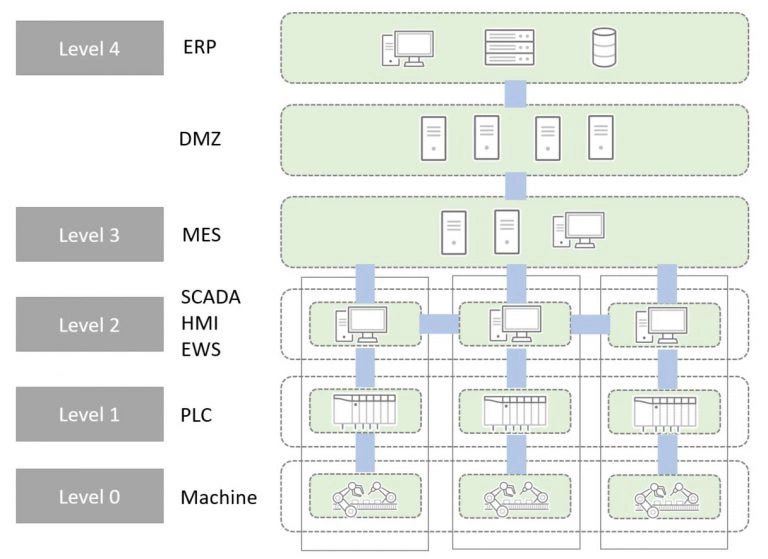
What Is the Purdue Model and How Is It Used in OT Security?
The Purdue Model is a layered architectural model used to understand and segment OT and IT systems. It helps organizations define security requirements based on system function and connectivity.
The Purdue Model describes a layered architecture, typically including:
- Levels 4–5: IT systems such as ERP
- Level 3.5: An OT / IT boundary layer such as a DMZ
- Level 3: Execution management systems such as MES
- Level 2: Control systems such as SCADA
- Levels 1–0: Physical processes and devices
The goal is to group security requirements by level and make it easier to define security requirements for connections between levels. This architecture is referenced in international standards such as IEC 62443 and NIST SP 800-82.
What Technical Controls Are Commonly Used in OT Security?
OT security controls are designed to reduce cyber risk while preserving operational stability. They must account for legacy systems, limited patching options, and production constraints.
Examples of common OT security challenges and associated controls include:
- Segregating IT and OT networks
- Protecting endpoints where patching is not feasible
- Validating the security of offline endpoints
- Detecting unauthorized devices
- Protecting Windows endpoints in OT environments
As digital transformation continues, IT security teams must also consider consistency across enterprise security governance and adaptation to new systems inside OT, including cloud and private 5G connectivity.
What Do OT Teams Need to Know About Cyber Risk?
OT teams must understand how cyber risk directly affects operational reliability, safety, and output. Cyber incidents in OT environments can disrupt production and create physical hazards.
Cyber risk in OT environments includes impacts on:
- Confidentiality
- Integrity
- Availability
- Health, Safety, and Environment (HSE)
It is also important to recognize that common IT security responses—such as isolating endpoints or blocking suspicious traffic—can sometimes introduce operational risks affecting availability and safety.
“Air-Gapped” Does Not Mean Risk-Free
Even OT environments without direct internet connectivity are still exposed to cyber risk. Security incidents frequently occur through offline pathways such as maintenance laptops, removable media, and contractor access.
Some OT environments are believed to be safe because they are not connected to the internet. However, incidents increasingly originate from internal or indirect connections, and organizations must be able to distinguish between equipment faults and cyberattacks.
Which Cybersecurity Standards and Frameworks Apply to OT Security?
Cybersecurity frameworks provide structured guidance for managing OT security risks. They help organizations balance prevention, detection, response, and recovery.
One of the most widely used frameworks is the NIST Cybersecurity Framework (CSF), which defines five core functions:
- Identify
- Protect
- Detect
- Respond
- Recover
Broadly, Identify and Protect reduce the likelihood of successful attacks, while Detect, Respond, and Recover minimize impact and restore operations.
The Full OT Security Lifecycle
OT security requires coordinated organizational and technical measures across the full security lifecycle. Effective programs address prevention, detection, response, and recovery together, rather than focusing solely on stopping attacks.
Using the NIST CSF as a reference, typical OT security measures span asset management, risk assessment, awareness and training, protective technologies, monitoring, incident response, and recovery. Both organizational readiness and technical controls are essential.
Where Can I Get Help With OT Security?
Trend Vision One™ delivers comprehensive capabilities to help organizations strengthen OT security and reduce operational risk. It combines advanced Attack Surface Management, Risk Insights, and Vulnerability Management with OT-aware protection strategies, enabling visibility and control across both IT and OT environments.
With Vision One™, you can identify and prioritize OT vulnerabilities, monitor for threats in real time, and implement compensating controls when patching is not feasible. This approach helps safeguard critical infrastructure and maintain operational continuity without compromising safety.
Trend Vision One™ can help you protect OT systems, reduce risk, and build resilience against evolving cyber threats.
Frequently Asked Questions (FAQs)
What is OT security in cybersecurity?
OT security protects systems that monitor and control physical processes. It focuses on safeguarding industrial and operational environments from cyber threats while maintaining safety, reliability, and continuous operations that directly affect physical assets.
How is OT security different from IT security?
OT security differs from IT security by prioritizing availability and safety. While IT security protects data and information systems, OT security protects systems that interact with the physical world, where downtime or malfunction can disrupt operations or cause harm.
What systems are considered OT systems?
OT systems include technologies used to control and monitor physical operations. Common examples are SCADA systems, PLCs, industrial control systems, and connected equipment used in manufacturing, energy, transportation, and healthcare environments.
Why is OT security important?
OT security is important because cyber incidents can impact physical operations and safety. Attacks on OT environments may cause production downtime, equipment damage, or safety incidents that affect people and critical infrastructure.
What cyber risks affect OT environments?
Cyber risks in OT environments affect confidentiality, integrity, availability, and safety. These include unauthorized access, manipulation of control data, system outages, and incidents that may lead to physical injury or operational disruption.