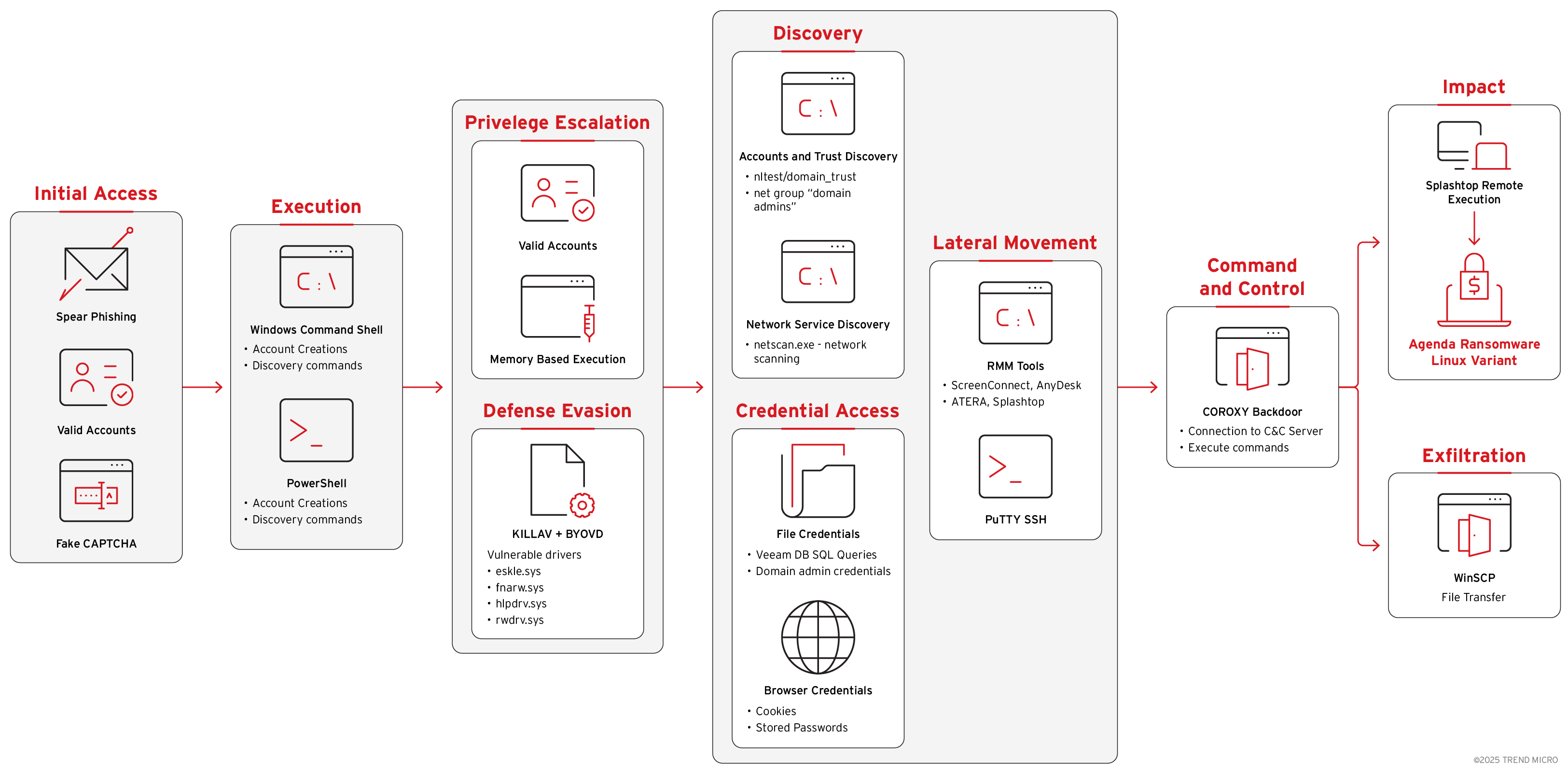
Ransomware
Agenda Ransomware Deploys Linux Variant on Windows Systems Through Remote Management Tools and BYOVD Techniques
Trend™ Research identified a sophisticated Agenda ransomware attack that deployed a Linux variant on Windows systems. This cross-platform execution can make detection challenging for enterprises.
Key takeaways:
- Trend™ Research identified Agenda ransomware group, known as Qilin, deploying a Linux-based ransomware binary on Windows hosts by abusing legitimate remote management and file transfer tools. The cross-platform execution sidesteps Windows-centric detections and security solutions, including conventional endpoint detection and response platforms.
- The technique enables low-noise operations that can disable recovery options through the targeted theft of backup credentials and neutralise endpoint defences via BYOVD attack.
- Agenda has affected more than 700 victims across 62 countries since 1 January 2025, primarily targeting organisations in developed markets and high-value industries. Most victims were in the United States, France, Canada, and the United Kingdom, with manufacturing, technology, financial services, and healthcare among the hardest hit.
- Any environment that uses remote access platforms, centralised backup solutions, or hybrid Windows/Linux infrastructures could be at risk. Enterprises are encouraged to limit the use of remote access tools to authorised hosts and continuously monitor for unusual activity.
- Trend Vision One™ detects and blocks the specific IoCs mentioned in this blog, and offers customers access to hunting queries, threat insights, and intelligence reports related to Agenda ransomware. For more security best practices, see the guidance below.
Trend™ Research identified a sophisticated ransomware attack by the Agenda group that deployed their Linux ransomware variant on Windows systems. This follows a similar attack observed last June 2025, where MeshAgent and MeshCentral was used for deployment. In this recent incident, the threat actors utilised a novel deployment method combining WinSCP for secure file transfer and Splashtop Remote for executing the Linux ransomware binary on Windows machines.
The attack chain demonstrated advanced techniques including usage of Bring Your Own Vulnerable Driver (BYOVD) for defence evasion and deployment of multiple SOCKS proxy instances across various system directories to obfuscate command-and-control (C&C) traffic. The attackers abused legitimate tools, specifically installing AnyDesk through ATERA Networks’ remote monitoring and management (RMM) platform and ScreenConnect for command execution. It abuses Splashtop for the final ransomware execution. They specifically targeted Veeam backup infrastructure using specialised credential extraction tools, systematically harvesting credentials from multiple backup databases to compromise the organisation’s disaster recovery capabilities before deploying the ransomware payload.
This attack challenges traditional Windows-focused security controls. The deployment of Linux ransomware on Windows systems demonstrates how threat actors are adapting to bypass endpoint detection systems not configured to detect or prevent Linux binaries executing through remote management channels.
The combination of BYOVD techniques, fake CAPTCHA social engineering, and the strategic targeting of backup infrastructure shows an approach of ensuring successful ransomware deployment while eliminating recovery options. The use of legitimate tools and cross-platform execution methods makes detection significantly more challenging. Organisations must urgently reassess their security posture to account for these unconventional attack vectors and implement enhanced monitoring of remote management tools and backup system access.
Impact and victimology
Agenda emerged as one of the top ransomware groups in 2025, demonstrating unprecedented operational tempo and global reach. Analysis of their data leak site since January reveals a ransomware-as-a-service (RaaS) operation that systematically targeted organisations across economically developed nations, with a particular focus on the United States, Western Europe, and Japan. The victimology pattern shows opportunistic targeting across multiple high-value sectors, particularly manufacturing, technology, financial services, and healthcare — industries characterised by operational sensitivity, data criticality, and higher likelihood of ransom payment.
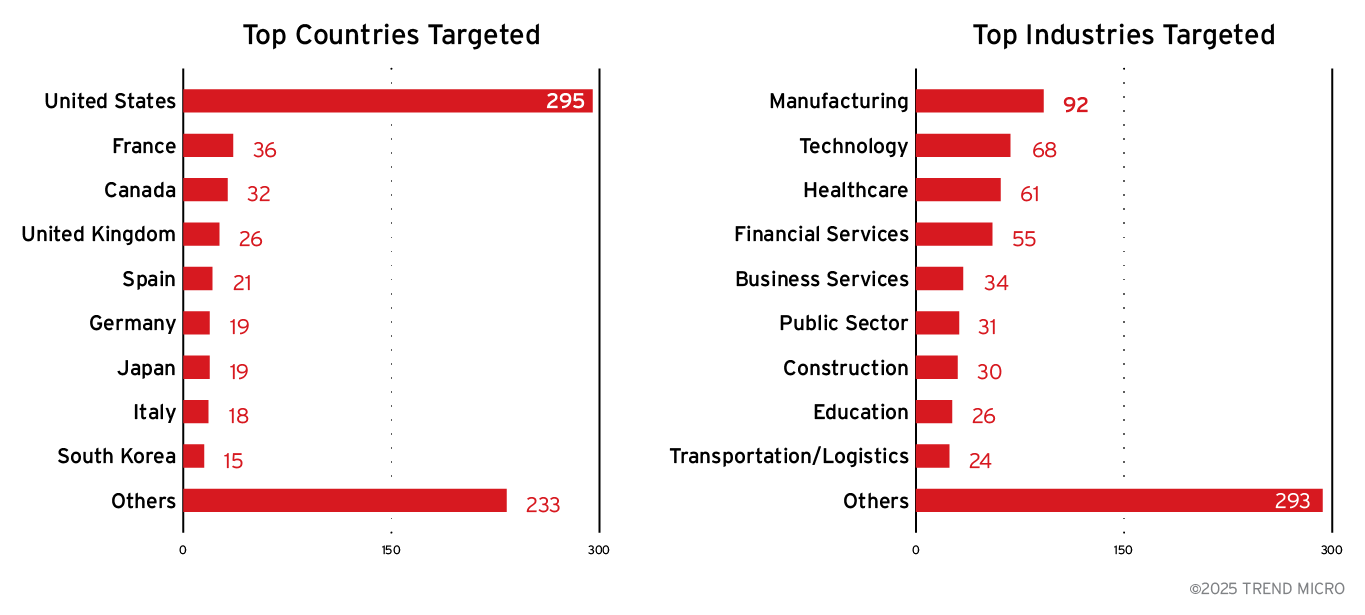
The group’s willingness to target critical infrastructure, including healthcare facilities and public sector entities, emphasises their lack of ethical constraints and prioritisation of financial gain over potential societal impact. Figure 1 illustrates the geographic and sectoral distribution of Agenda’s 2025 victims as documented on their data leak site, providing a visual representation of the threat actor's extensive global reach and multi-industry impact.
Attack chain
Initial Access
We identified that multiple endpoints within the compromised environment had connected to malicious fake CAPTCHA pages hosted on Cloudflare R2 storage infrastructure. These pages presented convincing replicas of legitimate Google CAPTCHA verification prompts:
- hxxps://pub-959ff112c2eb41ce8f7b24e38c9b4f94[.]r2[.]dev/Google-Captcha-Continue-Latest-J-KL-3[.]html
- hxxps://pub-2149a070e76f4ccabd67228f754768dc[.]r2[.]dev/I-Google-Captcha-Continue-Latest-27-L-1[.]html
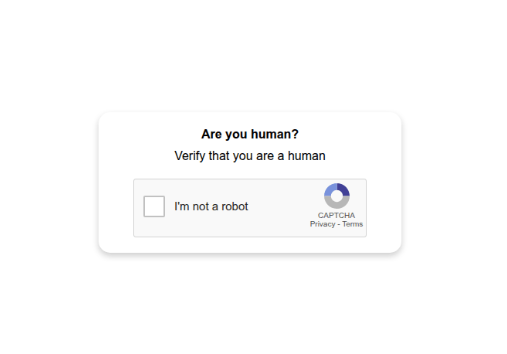
Analysis of the embedded obfuscated JavaScript within these fake CAPTCHA pages revealed a multistage payload delivery system that initiated downloads from secondary command-and-control servers:
- 45[.]221[.]64[.]245/mot/
- 104[.]164[.]55[.]7/231/means.d
We assess that the threat actors likely initiated their attack campaign through a sophisticated social engineering scheme involving these fake CAPTCHA pages. The pages appear to have delivered information stealers to the compromised endpoints, which subsequently harvested authentication tokens, browser cookies, and stored credentials from the infected systems. The presence of valid credentials used throughout the attack chain strongly suggests that these stolen credentials provided the Agenda threat actors with the valid accounts necessary for their initial access into the environment. This assessment is further supported by the attackers’ ability to bypass multifactor authentication (MFA) and move laterally using legitimate user sessions, indicating they possessed harvested credentials rather than relying on traditional exploitation techniques.
Privilege Escalation
The attackers deployed a SOCKS proxy DLL to facilitate remote access and command execution. This proxy was loaded directly into memory using Windows’ legitimate rundll32.exe process, making detection more difficult.
|── C:\Windows\System32\cmd.exe
└── C:\Windows\System32\rundll32.exe
└── rundll32.exe socks64.dll,rundll
└── C:\ProgramData\Veeam\socks64.dll
A backdoor administrative account named “Supportt” was created to ensure persistent elevated access. This account name was likely chosen to blend in with legitimate support accounts commonly found in enterprise environments.
- net user Supportt ***** /add
- net localgroup Administrators Supportt /add
The legitimate administrator account password was also reset to maintain control and prevent legitimate administrators from regaining access.
- net user Administrator *****
Discovery
Extensive reconnaissance was conducted to map the network infrastructure. The attackers abused ScreenConnect’s legitimate remote management capabilities to execute discovery commands through temporary command scripts, systematically enumerating domain trusts and identifying privileged accounts while appearing as normal administrative activity:
- nltest /domain_trusts
- net group "domain admins" /domain
Network scanning tools were deployed across multiple locations to discover additional systems, services, and potential lateral movement targets. The NetScan utility was executed from both the Desktop and Documents folders to perform comprehensive network enumeration.
- C:\Users\Administrator.<REDACTED>\Desktop\netscan.exe
- C:\Users\Administrator.<REDACTED>\Documents\netscan.exe
Remote management tools were strategically installed through legitimate RMM platforms to blend with normal IT operations. ATERA Networks’ agent was leveraged to deploy AnyDesk version 9.0.5, while ScreenConnect provided an additional command execution vector. This dual-RMM approach provided the attackers with redundant remote access capabilities that appeared legitimate to security monitoring systems, allowing them to maintain persistent access even if one tool was discovered and removed.
Credential Access
The attackers specifically targeted Veeam backup infrastructure to harvest credentials, recognising that backup systems often store credentials for accessing multiple systems across the enterprise. PowerShell scripts were executed with base64-encoded payloads to extract and decrypt stored credentials from Veeam databases, via powershell.exe -e [base64-encoded payload].
When decoded, these scripts revealed systematic targeting of multiple Veeam backup databases, each containing credentials for different segments of the infrastructure:
SQL Database Queries:
- SELECT [user_name], [password] FROM [VeeamBackup].[dbo].[Credentials]
- Targeted tables: Credentials, BackupRepositories, WinServers
Compromised Account Types:
- Domain administrator accounts: DOMAIN\admin-***, DOMAIN\da-backup-***
- Service accounts: svc-sql-***, DOMAIN\veeam-svc-***, svc-exchange-***
- Local administrators: SERVER01\Administrator, SERVER02\localadmin
Script Details:
- Decryption key found in script: 0jmz9Hrgy08rc0XrNpQ***[REDACTED]***
- Affected systems: Domain controllers, Exchange servers, SQL databases, file servers, backup repositories
This approach provided the attackers with a comprehensive set of credentials for remote systems, domain controllers, and critical servers stored within the backup infrastructure.
Defence Evasion
The attackers deployed sophisticated anti-analysis tools to evade security solutions. Further probe confirmed that both 2stX.exe and Or2.exe utilise the eskle.sys driver for anti-AV capabilities through a BYOVD attack:
- C:\Users\Administrator.<REDACTED>\Downloads\2stX.exe
- C:\Users\Administrator.<REDACTED>\Downloads\Or2.exe
- C:\Users\Administrator.<REDACTED>\Downloads\2stX\eskle.sys
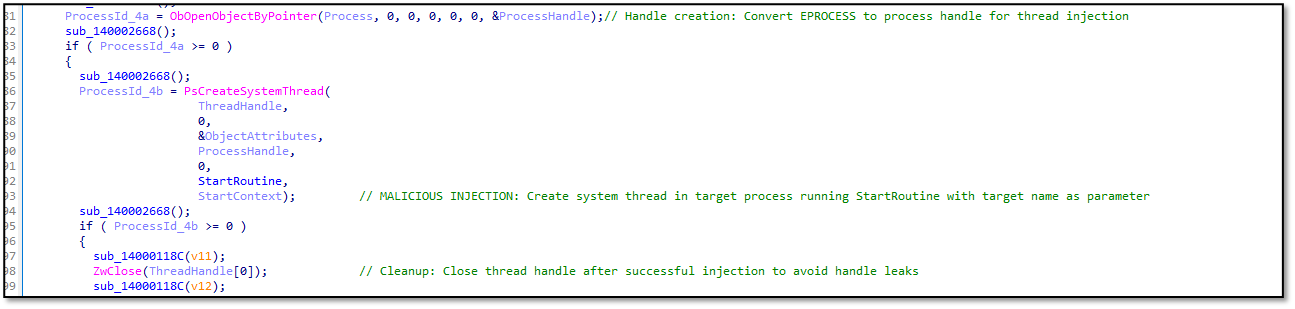
The eskle.sys driver was utilised to disable security solutions, terminate processes, and evade detection. Although these files could have been downloaded or copied onto the machine earlier, the origin of the eskle.sys driver is unclear. Its digital signature lists the vendor as “拇指世界(北京)网络科技有限公“ (translated: Thumb World (Beijing) Network Technology Co., Ltd.), which appears to be associated with the game.bb site. The driver likely belongs to a game-related package and is commonly used by cheat developers to evade anti-cheat systems; however, it could also be repurposed by advanced persistent threat actors.
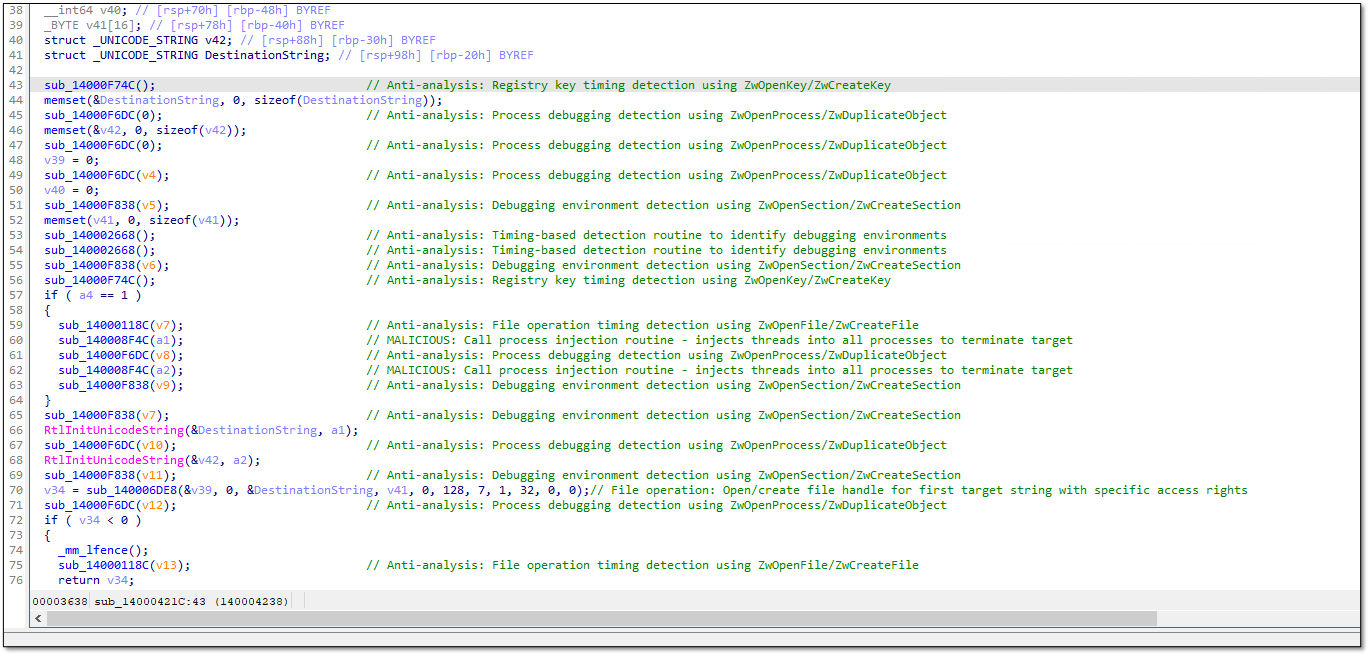
The eskle.sys driver forcibly stops programmes by creating a handle to the target process, starting a new thread to run a termination routine, and cleaning up the handle. This enables it to disable security software, disrupt system operations, and maintain persistence.
An additional component named msimg32.dll was identified in our internal telemetry alongside relations to ThrottleStop.sys. Further analysis through controlled testing revealed that msimg32.dll functions as a dropper that deploys two driver files when executed:
- C:\Users\Administrator.<REDACTED>\Downloads\msimg32.dll
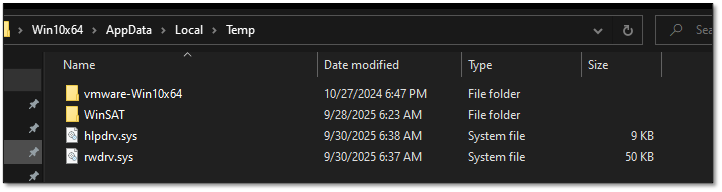
Upon successful execution, the following drivers were dropped:
- %TEMP%\rwdrv.sys
- %TEMP%\hlpdrv.sys
This connection is significant, as both rwdrv.sys and hlpdrv.sys have been previously documented in Akira campaigns for gaining kernel-level access and potentially terminating traditional endpoint detection and response (EDR) solutions. Analysis revealed that msimg32.dll employs a DLL sideloading technique, requiring a legitimate host executable for proper execution. The DLL failed to load through standard methods like regsvr32 or rundll32.
However, testing confirmed successful loading when placed alongside compatible binaries, such as FoxitPDFReader.exe, which imports msimg32.dll as a dependency. Upon execution, the application loads the malicious DLL, which then drops both driver files to the system’s temporary directory, as shown in Figure 5.
Additionally, we observed and analysed three other executables (cg6.exe, 44a.exe, aa.exe) that were identified as potential anti-AV tools based on their behavioural patterns and code similarities. Analysis revealed that these executables contain driver-loading routines and process manipulation capabilities consistent with BYOVD techniques. These tools are suspected to utilise a different vulnerable driver (fnarw.sys), though definitive confirmation remains pending as the driver was unavailable for complete analysis:
- C:\Users\<REDACTED>\Desktop\cg6.exe
- C:\Users\<REDACTED>\Desktop\44a.exe
- C:\Users\<REDACTED>\Desktop\aa.exe
Lateral Movement
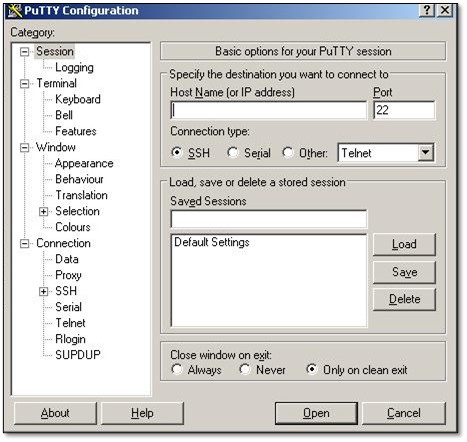
Multiple PuTTY SSH clients were systematically deployed on compromised systems to facilitate lateral movement to Linux systems within the environment. The attackers staged these tools with different filenames but identical functionality:
- C:\Users\<REDACTED>\Desktop\test.exe
- C:\Users\<REDACTED>\Desktop\1.exe
- C:\Users\<REDACTED>\Desktop\2.exe
- C:\Users\<REDACTED>\Desktop\3.exe
These renamed PuTTY executables enabled the attackers to establish SSH connections to Linux infrastructure, expanding their reach beyond Windows systems and demonstrating the cross-platform nature of the attack.
Command and Control
The threat actors established a C&C infrastructure through the deployment of multiple SOCKS proxy instances, identified as COROXY backdoor. These proxies were systematically placed across various system directories to create a distributed network of communication channels that obfuscated malicious traffic patterns and evaded network monitoring solutions.
The attackers positioned these SOCKS proxies in directories associated with legitimate enterprise software, including Veeam backup solutions, VMware virtualisation infrastructure, and Adobe applications. This placement strategy served a dual purpose: blending malicious C&C traffic with normal application communications while exploiting the trust typically afforded to these well-known software vendors in enterprise environments.
- C:\ProgramData\Veeam\socks64.dll
- C:\ProgramData\USOShared\socks64.dll
- C:\ProgramData\VMware\logs\socks64.dll
- C:\ProgramData\Adobe\socks64.dll
- C:\ProgramData\Veeam\Backup\OracleLogBackup\socks64.dll
The distributed nature of this SOCKS proxy deployment provided the attackers with redundant communication channels, ensuring persistent C&C capabilities even if individual proxies were discovered and removed. Each proxy instance functioned as an independent tunnel for encrypted communications, allowing the threat actors to maintain remote access, exfiltrate data, and orchestrate subsequent attack stages while remaining concealed within legitimate network traffic flows.
Impact
The final ransomware deployment showcased cross-platform execution. WinSCP was utilised for secure file transfer of the Linux ransomware binary to the Windows system:
C:\Users\<REDACTED>\AppData\Local\Programs\WinSCP\WinSCP.exe
└── C:\Users\<REDACTED>\Desktop\mmh_linux_x86-64.filepart
└── C:\Users\<REDACTED>\Desktop\mmh_linux_x86-64
Unique to the technique was the use of Splashtop Remote’s management service (SRManager.exe) to execute the Linux ransomware binary directly on Windows systems:
C:\Program Files (x86)\Splashtop\Splashtop Remote\Server\SRManager.exe
└── C:\Users\<REDACTED>\Desktop\mmh_linux_x86-64
To execute the Linux binary on Windows systems, the attackers likely enabled Windows Subsystem for Linux (WSL), which allows native Linux executables to run directly on Windows without requiring a full virtual machine. They may have enabled WSL through automated scripts or manually installed it via PowerShell or command line, ensuring the environment was ready for running Linux-based malware. Through the remote access provided by Splashtop, they could then deploy and execute the Linux ransomware binary within the WSL environment.
This unconventional approach appears to combine legitimate remote management tools with WSL to deploy cross-platform malware, potentially evading traditional Windows-focused security controls. The execution method is significant, as most endpoint detection systems might not be configured to monitor Linux binaries being executed through WSL, especially when initiated via legitimate remote management tools. The Linux ransomware binary possibly provided cross-platform capability, allowing the attackers to impact both Windows and Linux systems within the environment using a single payload.
Linux variant ransomware analysis
Analysis of the Linux ransomware binary revealed an advanced cross-platform payload with extensive configuration capabilities and platform-specific targeting.
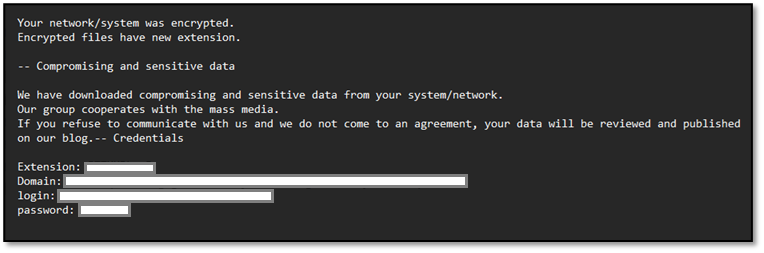
The ransomware deployed a standard Agenda ransom note threatening data publication and providing victim-specific credentials for negotiation. The note included file extension, and domain/login/password fields for accessing the threat actors’ communication portal.
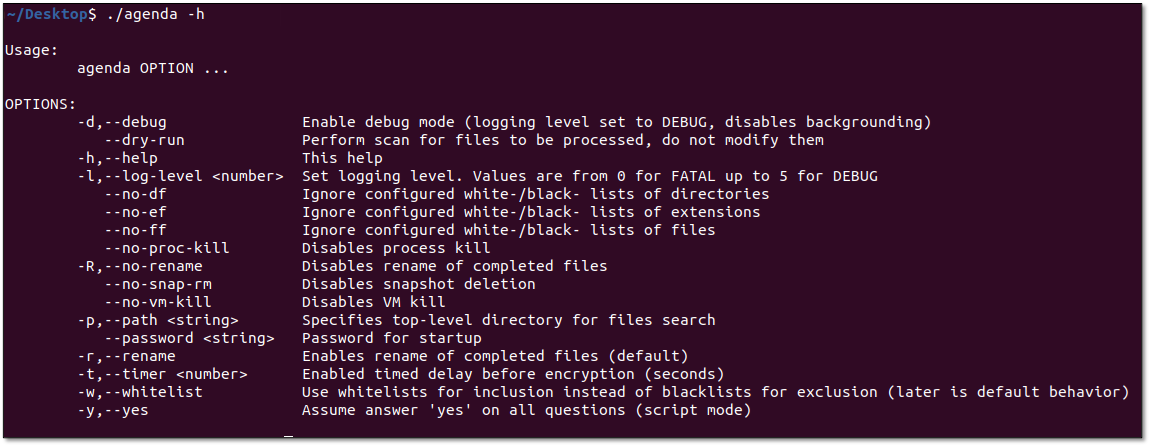
The binary implemented comprehensive command-line options including debug mode (-d), logging levels (-l), path specifications (-p), whitelist configurations, and encryption control parameters. Notable features included timer delays (-t) for delayed execution and a “yes” mode (-y) for automated operation without user prompts, indicating operational maturity.
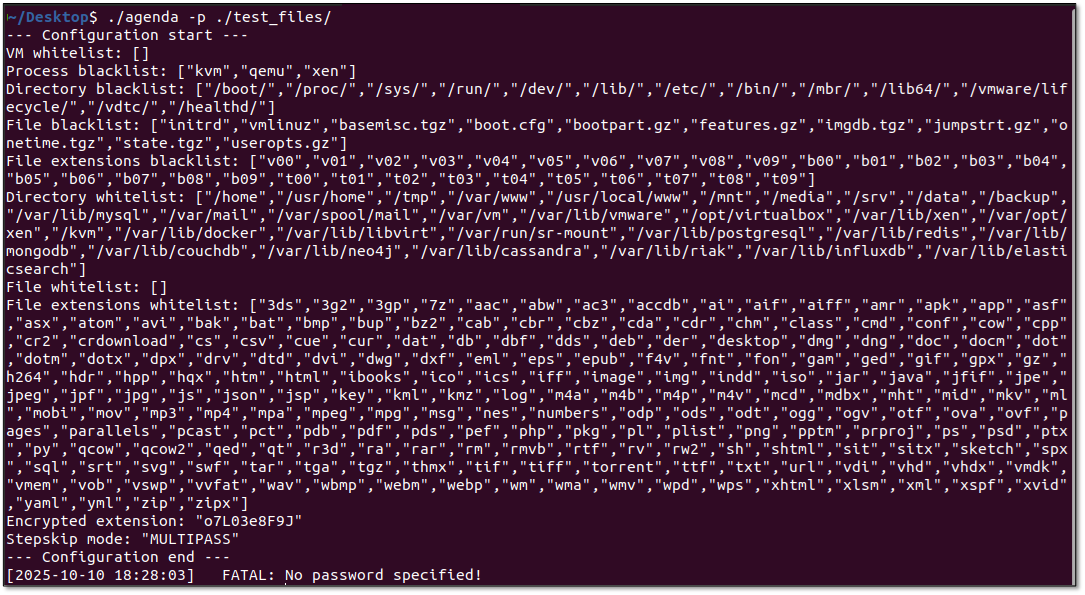
Execution required password authentication and displayed verbose configuration output including whitelisted processes, file extension blacklists, and path exclusions. The configuration showed extensive targeting of VMware ESXi paths (/vmfs/, /dev/, /lib64/) while excluding critical system directories, demonstrating hypervisor-focused deployment strategies.
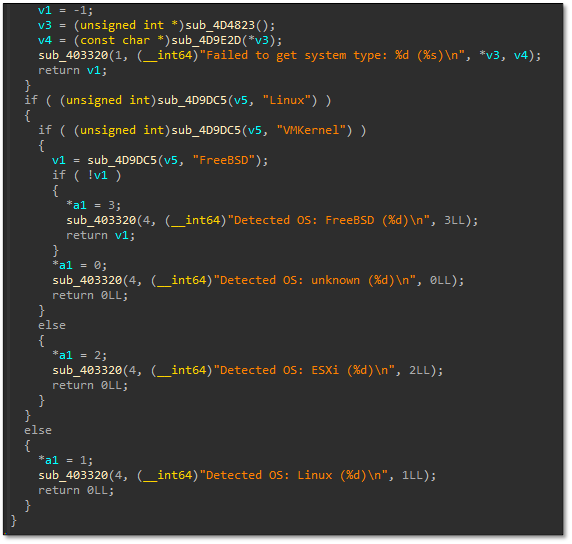
Earlier variants implemented OS detection for FreeBSD, VMkernel (ESXi), and standard Linux distributions, enabling platform-specific encryption behaviour, as shown in Figure 13.
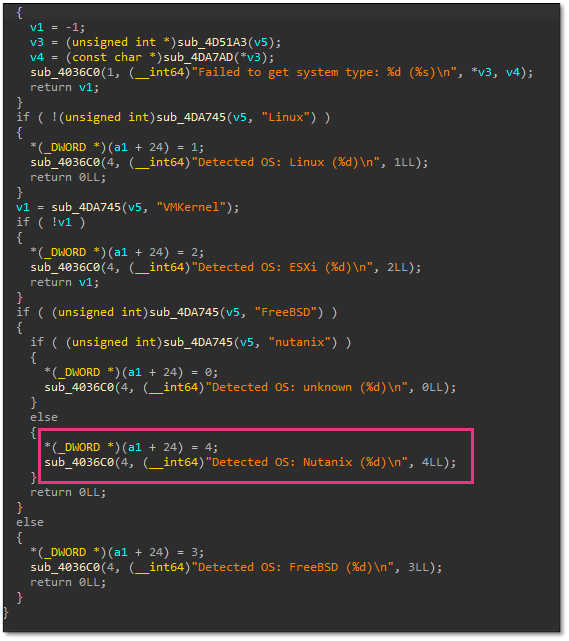
Updated samples incorporated Nutanix AHV detection, expanding targeting to include hyperconverged infrastructure platforms. This demonstrated the threat actors’ adaptation to modern enterprise virtualisation environments beyond traditional VMware deployments.
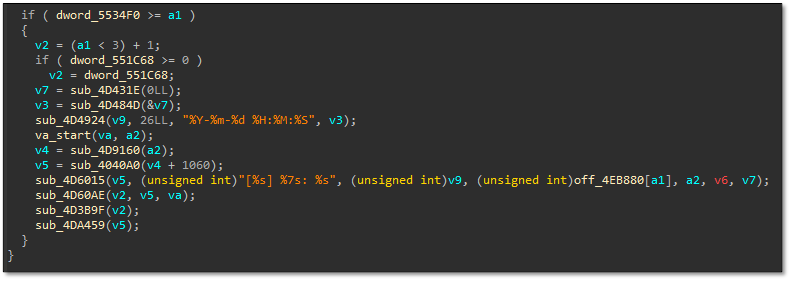
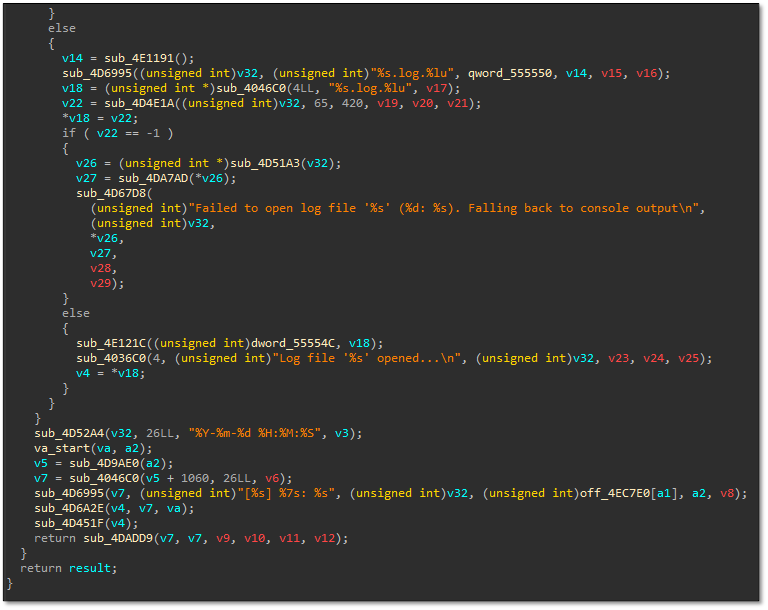
Comparison of logging routines revealed incremental improvements in error handling, with newer variants implementing enhanced file operation logging and fallback mechanisms for failed log file creation. The modifications included additional error messages and improved diagnostic output for troubleshooting deployment issues. The Linux variant’s advanced capability, combined with cross-platform deployment via Splashtop Remote, represented significant tactical evolution targeting hybrid infrastructure environments.
Security best practices
This Agenda attack shows how ransomware operators are further weaponising legitimate IT tools and hybrid environments to quietly bypass conventional security. Defences must address operational blind spots and strengthen visibility and control over critical assets. Here are some best practices:
- Secure remote access and RMM tools. Limit RMM platforms to authorised management hosts and enforce MFA. Monitor for abnormal activity, such as logins outside business hours or lateral movement between unexpected endpoints. Consider restricting what applications or scripts are allowed to run on specific systems to reduce the risk of abusing legitimate binaries for malicious activity.
- Harden the backup infrastructure. Targeted backup systems to steal credentials and disable recovery. Segment backup networks, enforce the principle of least privilege, rotate admin credentials as needed, and monitor for the suspicious use of administrative tools such as PowerShell or SQL queries interacting with backup credentials. Consider token or account revocation mechanisms to contain compromise if credentials are exposed.
- Account for detecting BYOVD and cross-platform threats. BYOVD attacks involve threat actors installing legitimate but vulnerable drivers to escalate privileges, disable security controls, or hide activity. These are risky because they exploit trusted components, often bypassing traditional AV/EDR. Monitor for unsigned or unexpected driver loads, DLL sideloading, and Linux binary execution on Windows through remote tools. Expand detection rules to cover payloads not native to the system.
- Extend visibility across hybrid environments. Ensure that the organisation’s EDR and SOC playbooks include both Windows and Linux telemetry and actively monitor internal lateral movement to detect early stages of hybrid ransomware attacks.
- Protect credentials and access tokens. Apply phishing-resistant MFA, strengthen conditional access policies, and monitor for abnormal use of privileged accounts or tokens.
Proactive Security with Trend Vision One™
Trend Vision One™ is the only AI-powered enterprise cybersecurity platform that centralises cyber risk exposure management and security operations, delivering robust layered protection across on-premises, hybrid, and multi-cloud environments.
Trend Vision One Threat Intelligence
To stay ahead of evolving threats, Trend customers can access Trend Vision One™ Threat Insights which provides the latest insights from Trend™ Research on emerging threats and threat actors.
Trend Vision One Threat Insights
Threat Actors: Water Galura
Emerging Threats: Agenda Ransomware Deploys Linux Variant on Windows Systems through Remote Management Tools and BYOVD Techniques
Trend Vision One Intelligence Reports (IOC Sweeping)
Hunting Queries
Trend Vision One Search App
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Outbound Connection to Suspicious Remote Host on Port 4396 - Agenda Ransomware
eventSubId: 204 AND dst: 146.70.104.163 AND dpt: 4396 AND LogType: detection
More hunting queries are available for Trend Vision One customers with Threat Insights entitlement enabled.
Indicators of Compromise
Indicators of compromise can be found here.