Phishing
Threat Actors Leverage File-Sharing Service and Reverse Proxies for Credential Harvesting
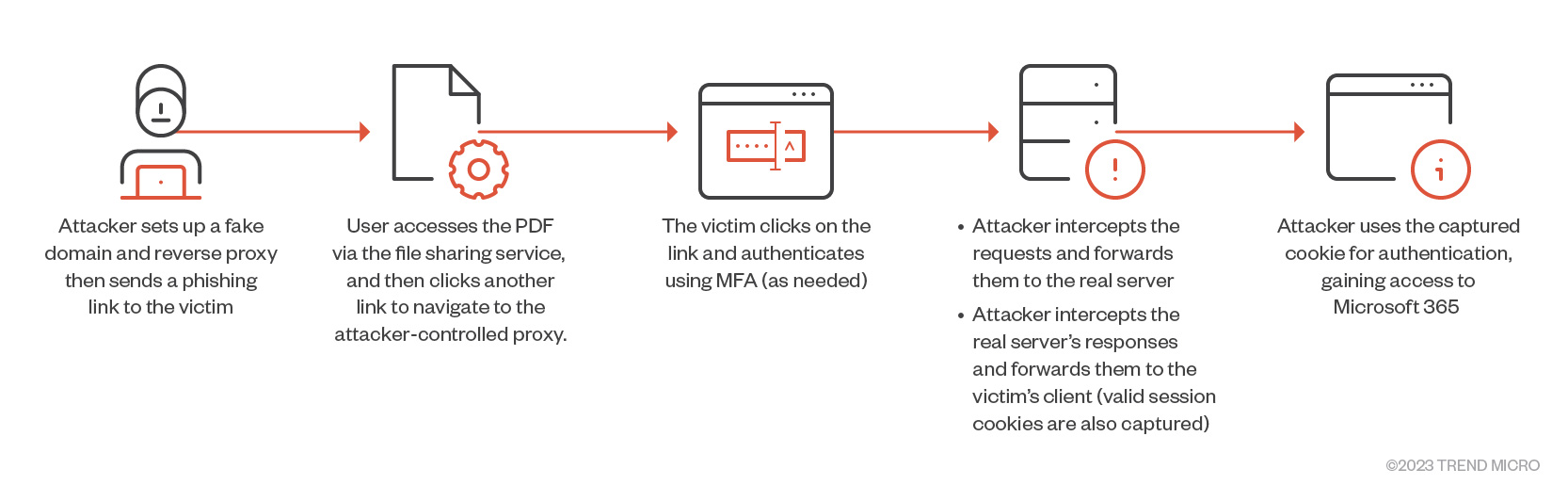
We analyzed a phishing campaign involving malicious emails containing a link to a file-sharing solution, which further leads to a PDF document with a secondary link designed to steal login info and session cookies.
We recently uncovered a phishing campaign involving threat actors sending socially engineered emails containing a link to DRACOON.team, a file-sharing solution known for its secure data storage, management, and file-sharing features. When a victim is tricked into accessing the link within the email, they are presented with a PDF document hosted on DRACOON. The document contains a secondary link that directs the victim to an attacker-controlled server that impersonates a Microsoft 365 login portal and acts as a reverse proxy to steal victims’ login information and session cookies. These stolen credentials and cookies can then be used to bypass multi-factor authentication (MFA).
The attacker-controlled reverse proxies function as intermediary servers positioned between the target and a legitimate authentication endpoint, such as the Microsoft 365 login page. When a victim interacts with the fake login page, the reverse proxy presents the genuine login form, manages incoming requests, and conveys responses from the legitimate Microsoft 365 login page.
We immediately observed logon activity using victim credentials via Microsoft 365 after these unsuspecting users entered them on the page. This activity includes automated access to the victim’s mailbox and further distribution of initial phishing emails. These emails contain the same links that were used to deceive the victim, and are sent to the contacts stored in their address book.
The reverse proxy functionality is believed to be related to the EvilProxy phishing suite. This has been extensively reported on by Microsoft, Proofpoint, and Menlo Security. However, the recent activity discussed here does not use redirects. Instead, it uses an intermediary link to files containing the links to adversary-controlled infrastructure. This new method can bypass email security mitigations since the initial link appears to be from a legitimate source and no files are delivered to the victim's endpoint as the hosted document containing the link can be interacted with via the file-sharing server within the browser.
We contacted the Dracoon team in response to these events and they have scanned and removed potential phishing attachments being hosted by their service. Additionally, the accounts identified to have been responsible for uploading the attachments have been marked for removal for breach of their terms of service.
Investigating the phishing email
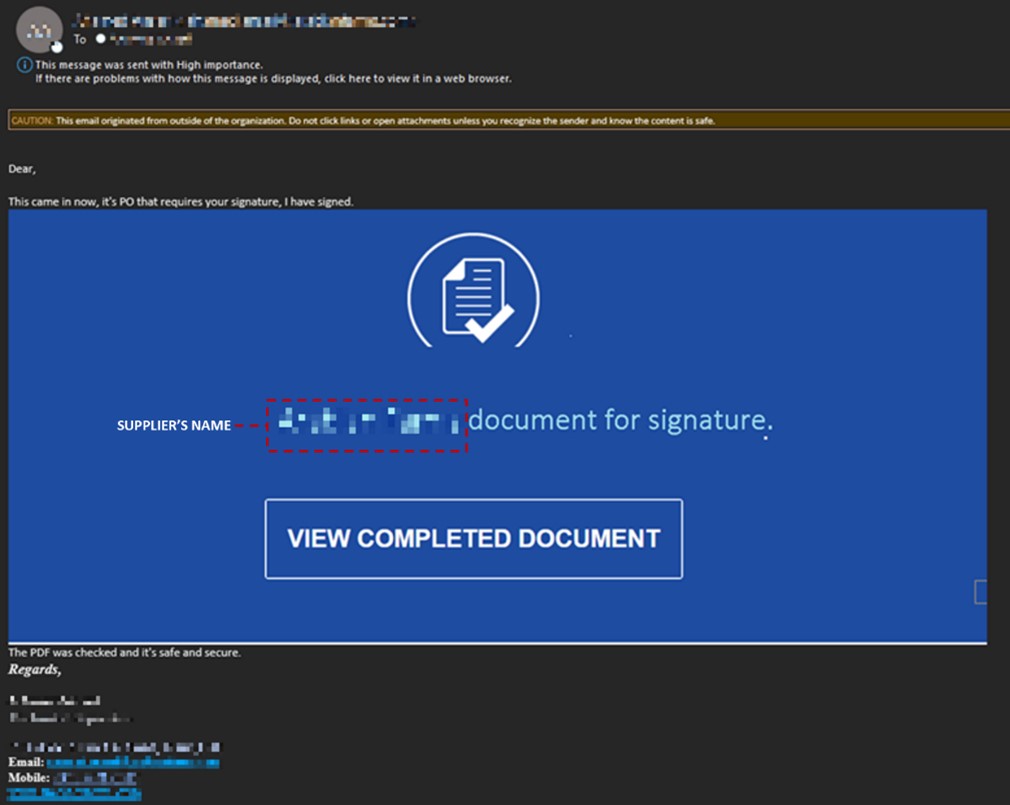
The phishing email originated from the victim's supplier, which provides them with specific goods and services. It is suspected that one of the users within the supplier's organization had their email compromised and used to send the phishing email to the victim. This makes the phishing email more convincing since it came from trusted or known accounts.
Figure 3 shows a screenshot of the sample phishing email received by the victim, cleverly disguised as a purchase order. It includes the supplier's name in the document link's caption, making it more legitimate.
The link redirects the user to the following URL:
https[:]//dracoon[.]team/public/download-shares/RjqetKkzebun7rB6OWWI3kPcpZ3RruPA
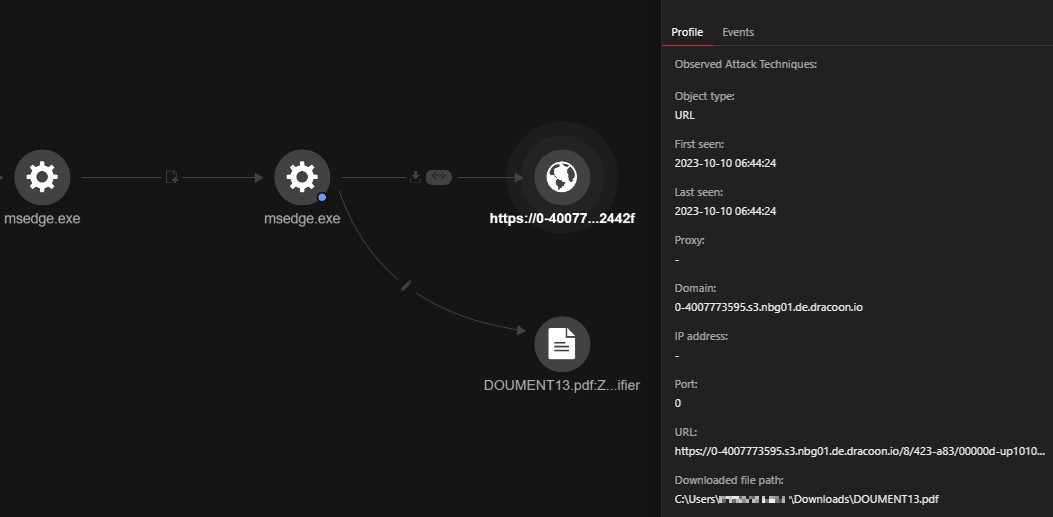
The redirected link leads to a publicly shared PDF file hosted on the Dracoon website. The user can interact directly with the PDF file without the need to download it, reducing the traceable evidence stored on the disk.

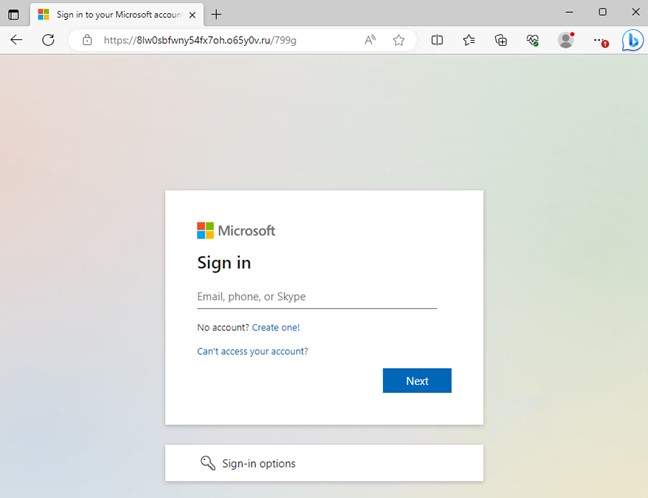
Clicking on the link redirects the user to a fake Microsoft 365 page, which acts as a reverse proxy for Microsoft 365 login requests, facilitating the theft of user credentials in the process. As can be identified through the URL, the site is clearly impersonating the Microsoft 365 login page, the legitimate Microsoft 365 login page should be https://login.microsoftonline.com/.
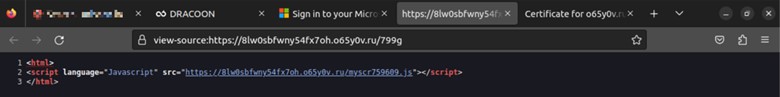
When inspecting the page source of the login page, there is a reference to a JavaScript file named myscr759609.js, which incorporates an array of mathematical functions and arithmetic operations.
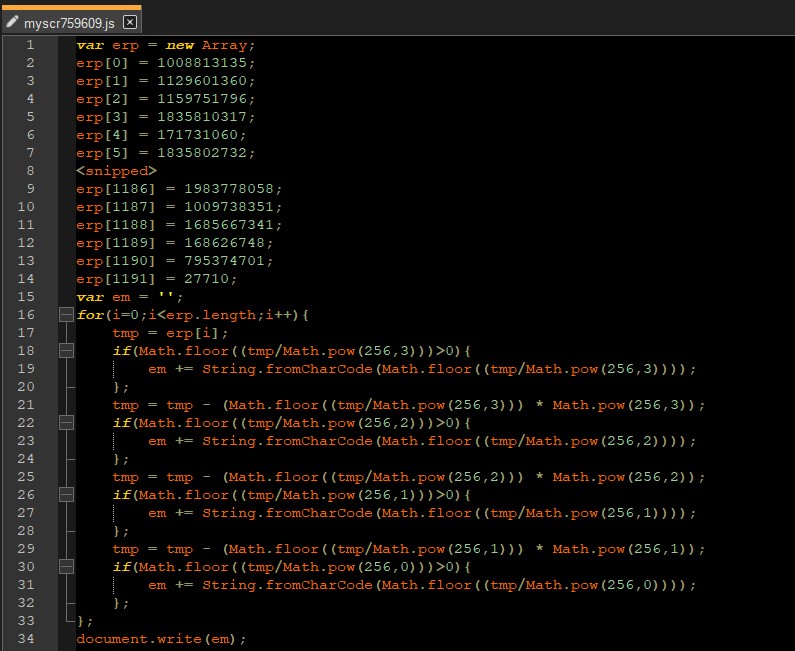
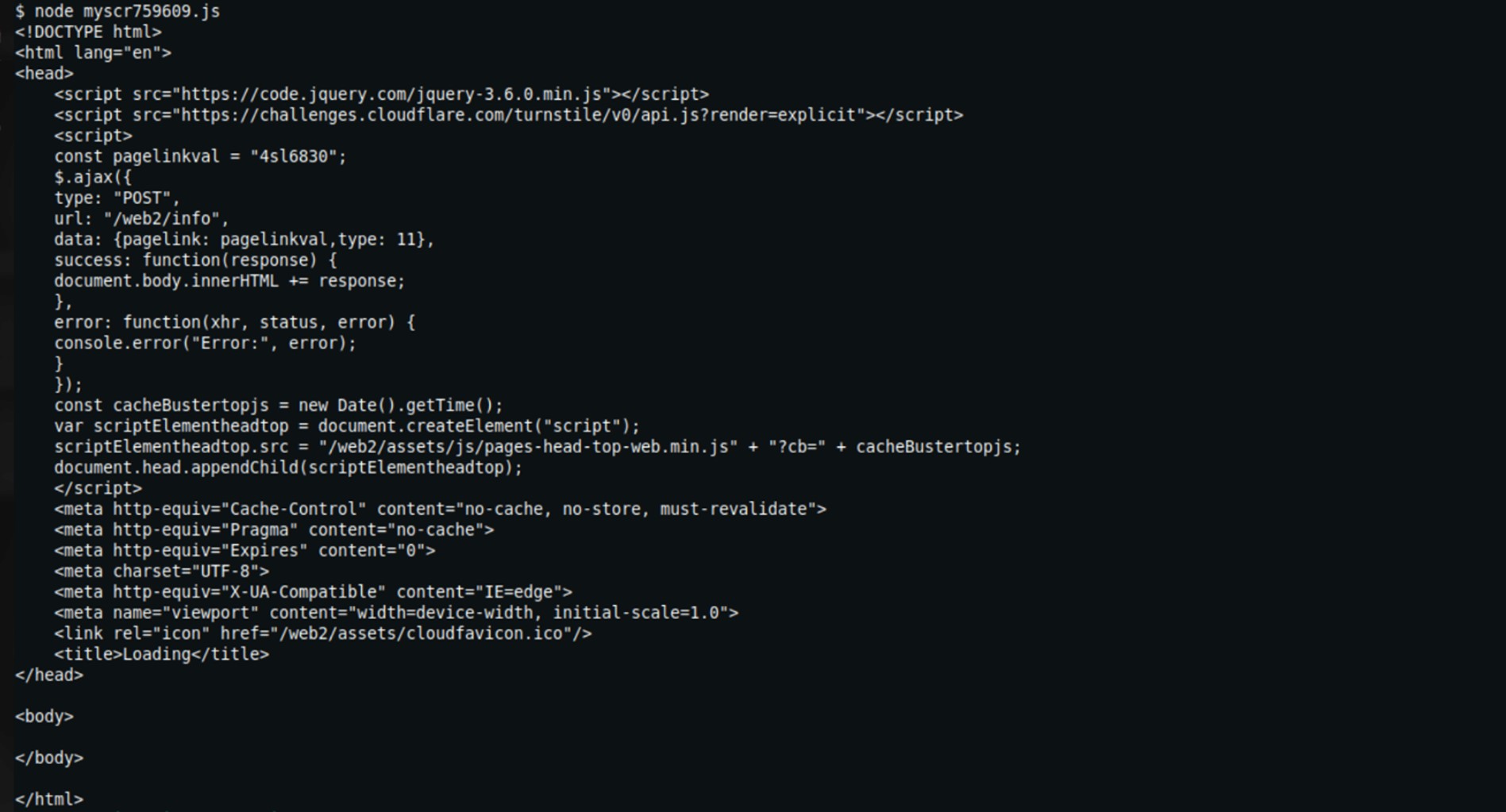
When executed locally using Node.js, myscr759609.js is deobfuscated, revealing the HTML code seen in Figure 8. The HTML content clearly indicates that myscr759609.js is responsible for credential harvesting, logging these credentials, and subsequently uploading the gathered information to an undisclosed webpage via a POST request.
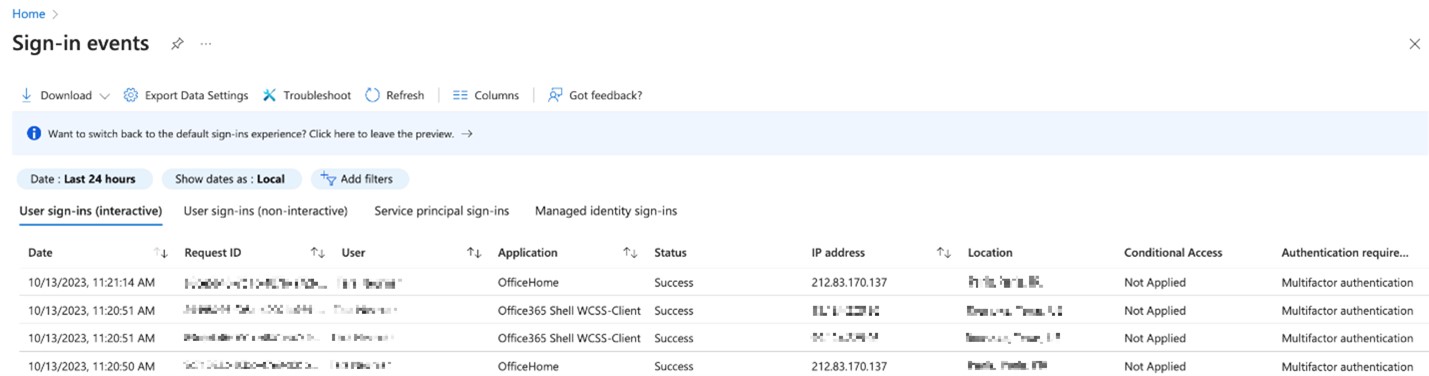
By examining the Microsoft 365 sign-in events and MFA logs, we can confirm the presence of a reverse proxy 212.83.170.137, as evidenced by the list of device sign-in events and the corresponding login locations. By cross-referencing Trend Micro Vision One data with Microsoft 365 sign-in events, we successfully identified the accounts that require immediate attention.
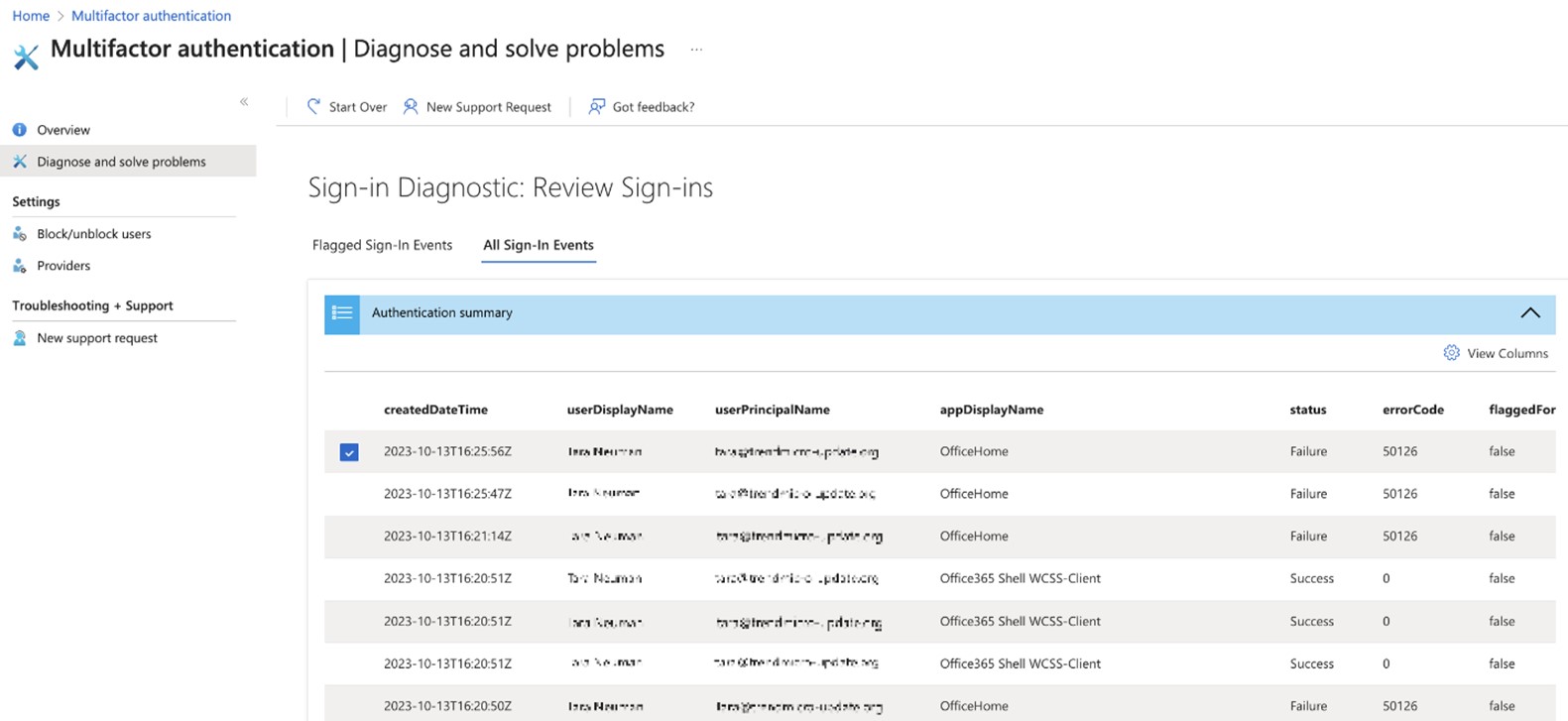
In addition, MFA events yielded valuable insights into the compromised accounts. This data allows us to investigate whether users inadvertently disclosed their credentials by comparing the timestamps of their interactions with the phishing page to the timestamps recorded in the MFAlogs.
Investigation by Trend Managed Extended Detection and Response (MxDR)
Using Vision One, a clear sequence of events becomes evident. From the captured screenshot, it's apparent that the phishing email was delivered to a Microsoft Outlook account, and the user proceeded to click on the embedded link, which then redirected them to the PDF file hosted on the Dracoon service.
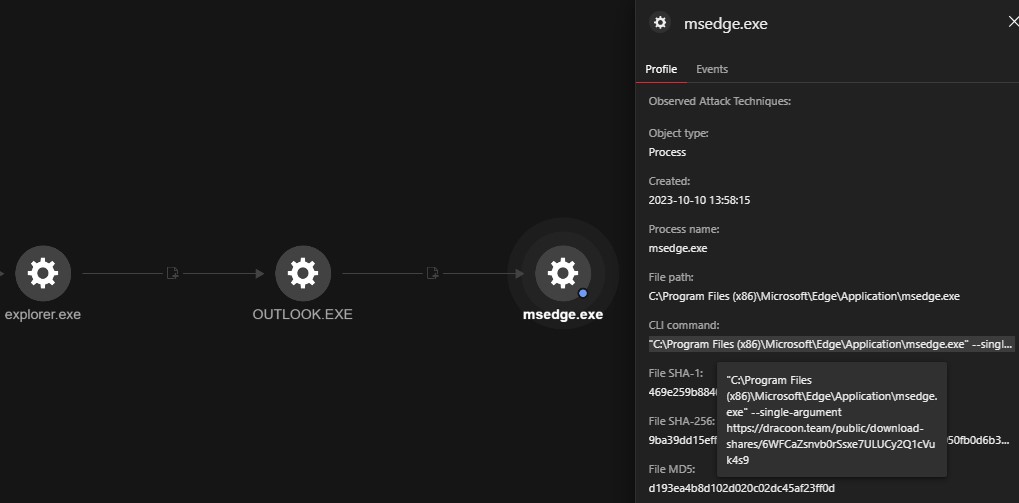
The PDF file contains an additional link, leading the user to the reverse proxy credential harvesting page, as illustrated by the events in Figure 12. The document hosted on the Dracoon service can either be downloaded or interacted within via the services in-built PDF viewer, which allows a user to interact with the document via the browser.
Assessing the impact of a phishing attack holds critical importance in incident response. This provides valuable insight into the extent of the affected accounts in the organization. Through the lens of Trend MxDR, we were able to thoroughly scope the recipients of the phishing emails and those who interacted with the phishing link, potentially disclosing their credentials.
Furthermore, our investigation unveiled a series of additional Dracoon links used within this phishing campaign. These links also impersonated Microsoft 365, with the aim of stealing credentials and bypassing MFA using session cookies. The attackers employed an array of message subject lines, such as “Shipping Document,” “New Brazil File,” “China Shippement,” and “Document from China.” The efforts of our MxDR team allowed us to successfully trace the compromised accounts and promptly recommend that the affected users change their passwords.
Conclusion and recommendations
MFA is often praised as a robust defense against credential theft and unauthorized access. While it is undoubtedly a powerful security tool, it's important to recognize that MFA is not a silver bullet when it comes to safeguarding online accounts and sensitive information.
As we've discussed in this blog, the limitations of MFA become evident when considering threats like EvilProxy attacks. These malicious actors can intercept and manipulate network traffic, effectively bypassing the added layer of security that MFA offers.
The use of DRACOON.team to host the PDF file provided threat actors with an effective means to circumvent email security measures. By abusing legitimate file-sharing services, the attackers were able to significantly improve their success rates while evading detection. Legitimate services can often bypass most of the security measures in place, making them attractive tools for threat actors.
Incidents like the one discussed in this blog entry also serves as a reminder that emails from known or trusted senders do not guarantee that they are wholly legitimate. Users must remain vigilant and exercise caution when clicking on links or downloading attachments, even from trusted sources.
Trend MxDR can prove to be highly efficient in detecting phishing attacks that involve the use of reverse proxies like EvilProxy. By continuously monitoring network traffic, analyzing patterns, and leveraging threat intelligence, MxDR can promptly identify such attacks and alert affected customers.
Here are several proactive measures and mitigation strategies that organizations can implement:
- Security Awareness: Conduct regular awareness sessions and comprehensive training programs to educate users. By providing detailed information and practical guidance, users can develop a strong understanding of potential risks and how to mitigate them. Furthermore, it is essential to emphasize the importance of verifying the legitimacy of target URLs before accessing them. Rather than assuming all URLs are safe, users should be encouraged to exercise caution and employ reliable methods to confirm the authenticity and security of the websites they visit. Conducting regular phishing attack simulation exercises serves as a proactive approach to raising awareness among employees.
- Implement Phishing Resistant MFA: One of the recommended measures to enhance security is the use of phishing-resistant MFA. By implementing MFA methods that are resilient against phishing attacks, such as FIDO-based authentication with devices like YubiKey or password-less MFA, organizations can significantly strengthen their authentication processes and protect against credential theft.
- Email Security: Organizations can protect their employees and users from malicious email threats by implementing an email security solution like Trend Email Security. Implementing Domain-based Message Authentication, Reporting and Conformance (DMARC), Sender Policy Framework (SPF), and Domain Keys Identified Mail (DKIM) will also enhance email security.
- Continuous Monitoring: It is highly recommended to establish a robust system for continuous monitoring by centrally collecting and closely monitoring logs, particularly Microsoft 365 access and MFA logs to promptly identify, investigate and respond to any suspicious access activities. Automation should also be considered to swiftly disable or lock account access in response to suspicious indicators such as impossible travel or brute-force attempts.
Indicators of Compromise
The indicators of compromise for this entry can be found here.

