GenAI security simplified
Confidently embrace generative AI tools to unlock business value. Control AI usage, prevent data leakage, mitigate manipulation risks and secure the user access journey with continuous risk assessment.

Enforce access control
Businesses run on SaaS apps accessed via the internet. Obtain real-time insights, identify risks, and implement least privilege access control for both sanctioned and unsanctioned apps to protect sensitive data.

Secure work-from-anywhere
Adapt to the work-from-anywhere model by securely connecting virtual workforces to private apps. Replace legacy VPNs with least-privilege, just-in-time access control to manage corporate resources efficiently.
Securing your Zero Trust Journey by strengthening access control to:
GenAI services
Organizations need to confidently embrace generative AI to unlock business value.
- Gain visibility and apply continuous risk-based rule to control the AI service usage
- Inspect the GenAI services’ prompt/response, to avoid potential data leakage and unpredicted response
- Run advanced prompt injection detection to mitigate risk of potential manipulation from GenAI services

Internet applications
More than ever, businesses run on SaaS apps accessed over the internet.
- Obtain real-time insights into sensitive data processed and stored in SaaS apps
- Identify risks and apply access control for sanctioned and unsanctioned apps
- Implement trust-based, least privilege access control across the internet

Cloud applications
Digital transformation includes migrating apps to public cloud environments.
- Reduce the risk of unauthorised access to data and critical information
- Deliver secure access to SaaS apps, checking for policy violations and security risks
- Monitor application activity and remain secure with continuous risk assessment

Business-critical resources
The work from anywhere (WFA) movement has become a reality for many organisations.
- Securely connect your virtual workforce to private apps and corporate resources
- Retire legacy VPN and bulky virtual desktop solutions
- Introduce least-privilege, just-in-time access control

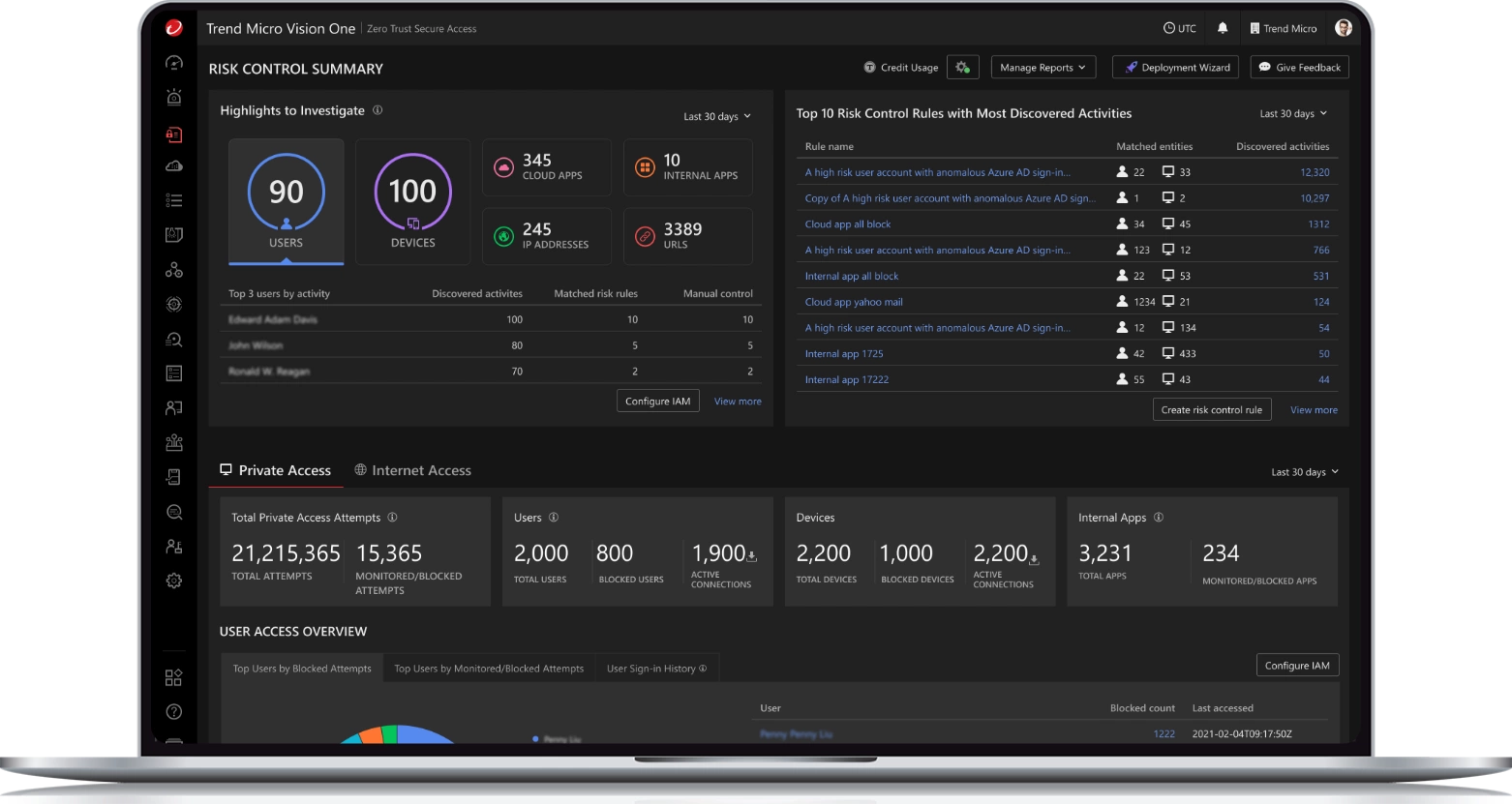
Gain Insight. Enforce Control. Reduce Risk.
Cloud-native platform
Integrate cyber risk exposure management (CREM), extended detection and response (XDR), and Secure Access (ZTSA) in a cloud-native platform. Enrich continuous adaptive risk and trust assessment to drive zero-trust architectures that support business objectives. Eliminate the inherent trust formerly placed upon unverified users and devices.
Gain visibility through all user and device behaviors.
Continuous risk assessment
Single point-in-time assessment of an asset’s risk gives a false sense of security. Analyse threat factors of identity, device, applications by implementing CREM-powered continuous risk assessment. Change access to specific resources based on increases or decreases in risk. Gather and correlate telemetry data to automate decisions by leveraging Trend Threat Research and Intelligence.

Full Secure Access capabilities
Enable access control, real-time data, and threat protection capabilities across your network, web, cloud, private apps, devices, and users – all from your Trend Vision One™ platform. Utilise Secure Access’ advanced capabilities, including Trend Vision One™– Zero Trust Secure Access – Private Access, Internet Access and AI Service Access.
Native part of your zero-trust strategy
As part of the Trend Vision One™ platform, leverage our native integration to feed telemetry and context to your XDR operations. Reveal and prioritise risks for better decision making with our Trend Micro™ Zero Trust Risk Insights.
Secure the AI journey
- Gain visibility and control AI app usage
- Apply continuous risk-based access rule
- Detect prompt injection attacks to safeguard the user access journey
- Inspect the GenAI services’ prompt/response to avoid potential data leakage

Leverage continuous risk assessment
- Implement micro-segmentation to specific resources
- Respond to threats fast with dynamic access control powered by continuous risk assessments
- Enforce least privilege access
- Enable work from anywhere

A native part of your XDR strategy
Delivered as a part of the Trend Micro Vision One™ platform, this native integration feeds telemetry and context to XDR operations, revealing and prioritising risks for better decision-making with Zero Trust Risk Insights.
JOIN 500K+ GLOBAL CUSTOMERS
Get started with Secure Access