Malware
Mac Malware MacStealer Spreads as Fake P2E Apps
We detected Mac malware MacStealer spreading via websites, social media, and messaging platforms Twitter, Discord, and Telegram. Cybercriminals lure victims to download it by plagiarizing legitimate play-to-earn (P2E) apps’ images and offering jobs as beta testers.
We analyzed a Mac malware called MacStealer (detected by Trend Micro as TrojanSpy.MacOS.CpypwdStealer.A), a cryptocurrency wallet and information stealer disguised as a plagiarized version of a legitimate play-to-earn (P2E) game app. We posted a warning for users to avoid this threat early; this article discusses the technical details of the malware and the distribution techniques that threat actors use to infect devices and steal users’ information.
Our analysis was done on the original reported sample. We have since discovered that MacStealer's source code has been leaked via an online public scanning service. The malware is currently spreading via third party websites using images and graphics ripped off from real P2E applications, and promoted on social media and messaging platforms Twitter, Discord, and Telegram. The threat actors behind the malware pose as a legitimate game company looking for testers and enticing potential victims to download their app.
Infection routine
Luring new gamers
Unlike other fake app routines that redirect users while infecting devices, the cybercriminals took no pretense to create a game and simply copied from existing P2Es. The Twitter account and the websites are just fronts to entice users to download MacStealer. Once the malware executes, specific pieces of information stored in the device are stolen as soon as the user inputs their respective password in the GUI prompt.
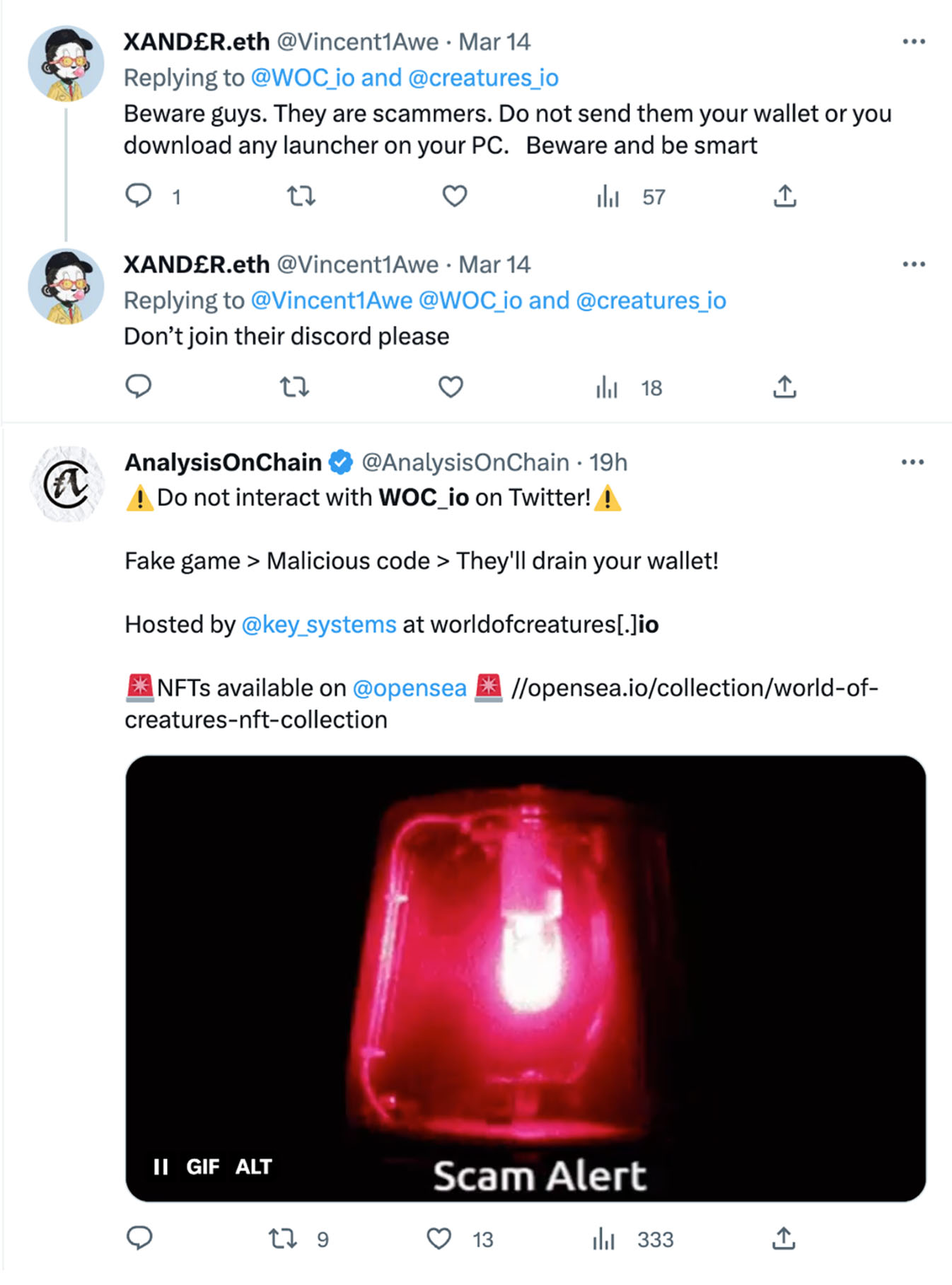
Our sensors picked up on the high-risk samples for analysis during a routine check; a closer inspection revealed the website worldofcreatures[.]io connected to the sample. A quick search online showed the website being heavily promoted on Twitter.
We checked the website’s background and found that the fake app’s page was only created in January 2023, and all the graphics and text were lifted directly from a different P2E app’s website. Some of the fake app’s Twitter page images were also directly taken from the legitimate app’s social media page, and was just created in October 2022 — relatively new compared to the legitimate app’s account, which was created in 2021. Unwitting victims who might not have heard of the game could easily mistake the fake page as the legitimate app’s original game and official social media account.
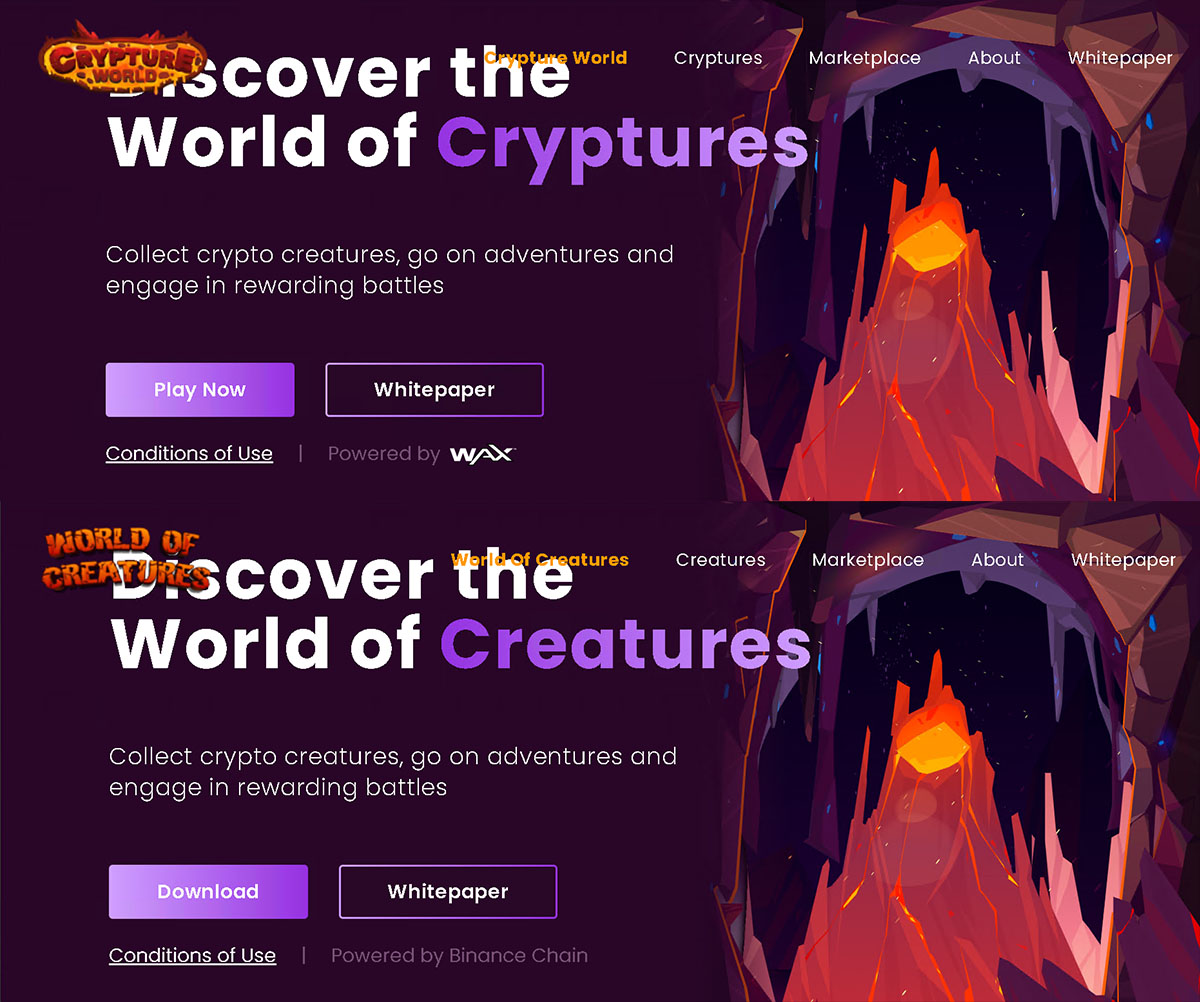
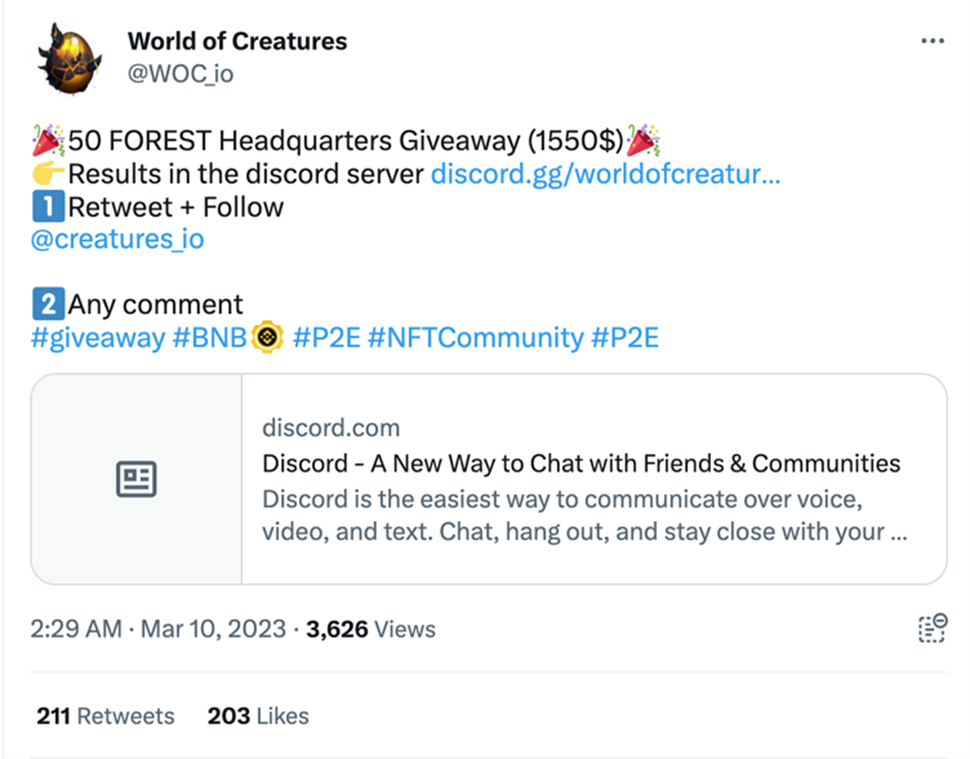
These websites differ in many ways (such as the graphics, name, and company), and are still discernible if the interested user was aware of these details. Social media posts include promotions for downloading the app to make it seem like new players can receive freebies once they connect to the Discord channel and download the game. Once the user joins the threat actor's channel, the threat actor convinces the user via chat to click the malicious link or download a malware file.
Technical details
Once the victim downloads the game, a .dmg file named LauncherMacOS.dmg (SHA256: 8ea33c34647578b79dd8bb7dcf01a8ad1c79e7ada3fd61aca397ed0a2ac57276, detected by Trend Micro as TrojanSpy.MacOS.CpypwdStealer.A) executes in the system. The ad hoc signature is as follows:
➜ MacOS jtool2 --sig -vvv Launcher
An embedded signature of 140064 bytes, with 4 blobs:
Blob 0: Type: 0 @44: Code Directory (53878 bytes)
Version: 20400
Flags: adhoc (0x2)
CodeLimit: 0xa7b430
Identifier: Launcher-5555494433ac846113c4377a91a35c11864c6938 (@0x58)
Executable Segment: Base 0x00000000 Limit: 0x00000000 Flags: 0x00000000
CDHash: 2af323c4d425283c9a7103d8966b0f4e9311fef7 (computed)
# of hashes: 2684 code (4K pages) + 3 special
Hashes @198 size: 20 Type: SHA-1
Blob 1: Type: 2 @53922: Empty requirement set (12 bytes)
Blob 2: Type: 1000 @53934: Code Directory (86122 bytes)
Version: 20400
Flags: adhoc (0x2)
CodeLimit: 0xa7b430
Identifier: Launcher-5555494433ac846113c4377a91a35c11864c6938 (@0x58)
Executable Segment: Base 0x00000000 Limit: 0x00000000 Flags: 0x00000000
CDHash: a575679ef003ee28b6698f40ef7874390ce3817dc5211d31ecff0b2859d6f444 (computed)
# of hashes: 2684 code (4K pages) + 3 special
Hashes @234 size: 32 Type: SHA-256
Blob 3: Type: 10000 @140056: Blob Wrapper (8 bytes) (0x10000 is CMS (RFC3852) signature)
Ad-hoc signing is especially important on ARM64 M1 Apple processors. It requires all native code to have valid signatures (if only ad-hoc), or the operating system (OS) will not execute it. It instead kills the native code on launch.
On inspecting the app bundle inside the dmg, we observed that it contains the following Mach-O binary compiled using Python compiler Nuitka:
Launcher (SHA256: 5e8f37420efb738a820e70b55a6b6a669222f03e4a8a408a7d4306b3257e12ff, detected by Trend Micro as TrojanSpy.MacOS.CpypwdStealer.A)
Nuitka is an uncommon compiler, and during testing, the main Mach-O showed suspicious network activity. We also noted that Nuitka can compile Python scripts into a Mach-O binary.
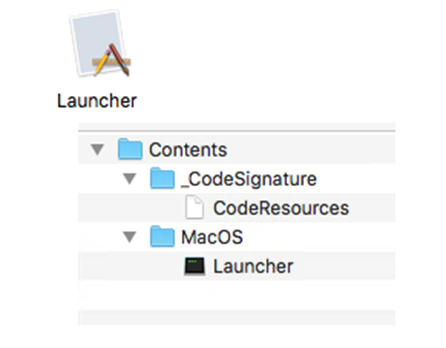
The routine itself is divided into two stages. The first stage is an execution of a Nuitka bootstrap. On its own, the logic itself is harmless, but drops the malicious payload to a target path, while the second stage is the execution of the malicious payload.
The first stage of the malware implements the following routine:
1. It reads content from a special section named “payload.”
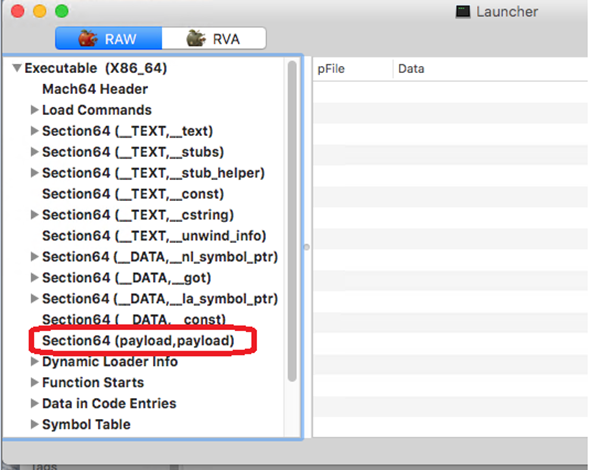
2. It writes the content to several files at the path: <%TEMP%/onefile_%PID%_%TIME%>. We observed several Python libraries and the second stage Mach-O file (Launcher SHA256: 15d1afca780e2ea6ffec8c4862a3401e003b5e79ce5f9076b4eea4ab599bc4ce, detected by Trend Micro as TrojanSpy.MacOS.CpypwdStealer.A) written here:
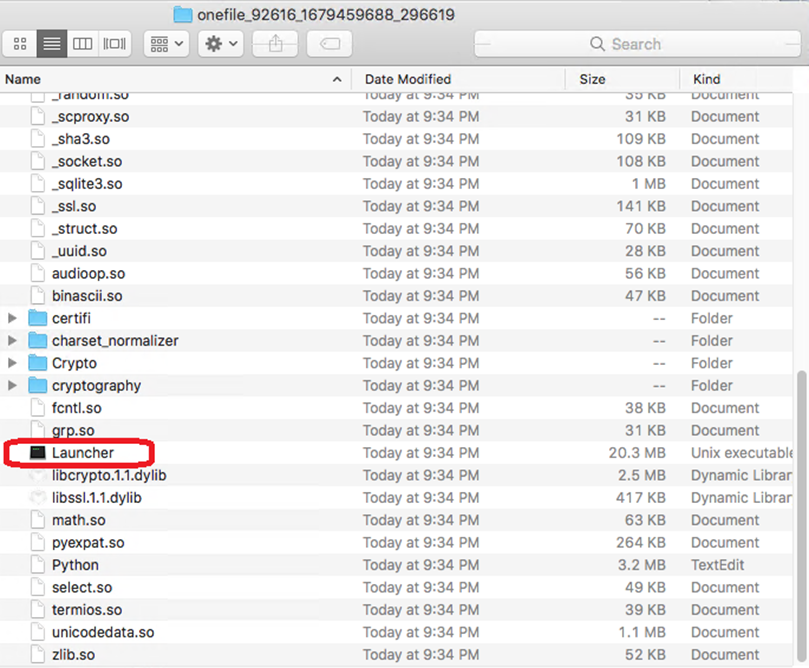
3. It changes the environment variable NUITKA_ONEFILE_PARENT to the current process number.
4. It executes the main executable file of the extracted content and cleans up the bootstrapped version itself.
The second stage executable is a program based on a CPython implementation, which is compiled by Nuitka from Python. In the process of compilation, the compiler loses part of the information to improve the execution efficiency of the program, and the Python code converted by Nuitka completely loses the original bytecode and cannot be recovered. Because of the irreversible compilation process, we were unable to analyze it from the perspective of the Python source code, but the function names and the dynamic behavior logs provide a lot of information.
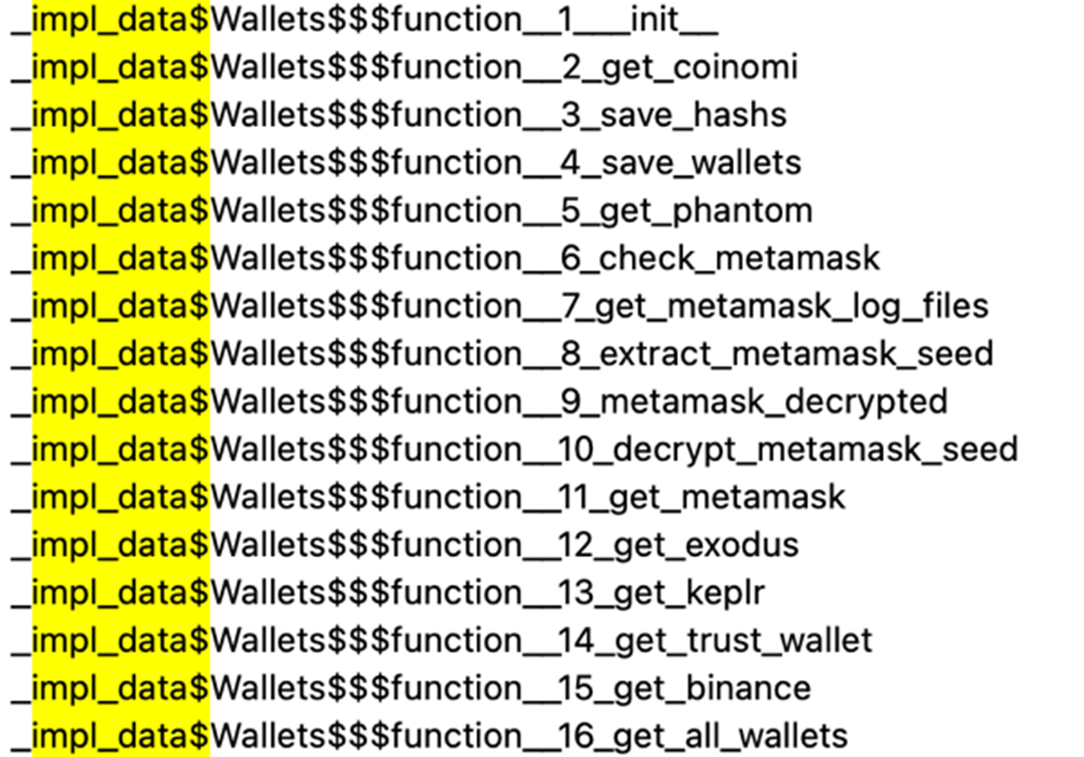
1. It tries to steal data from the following wallets:
- Binance
- Exodus
- Keplr
- Metamask
- Phantom
- Trust wallet
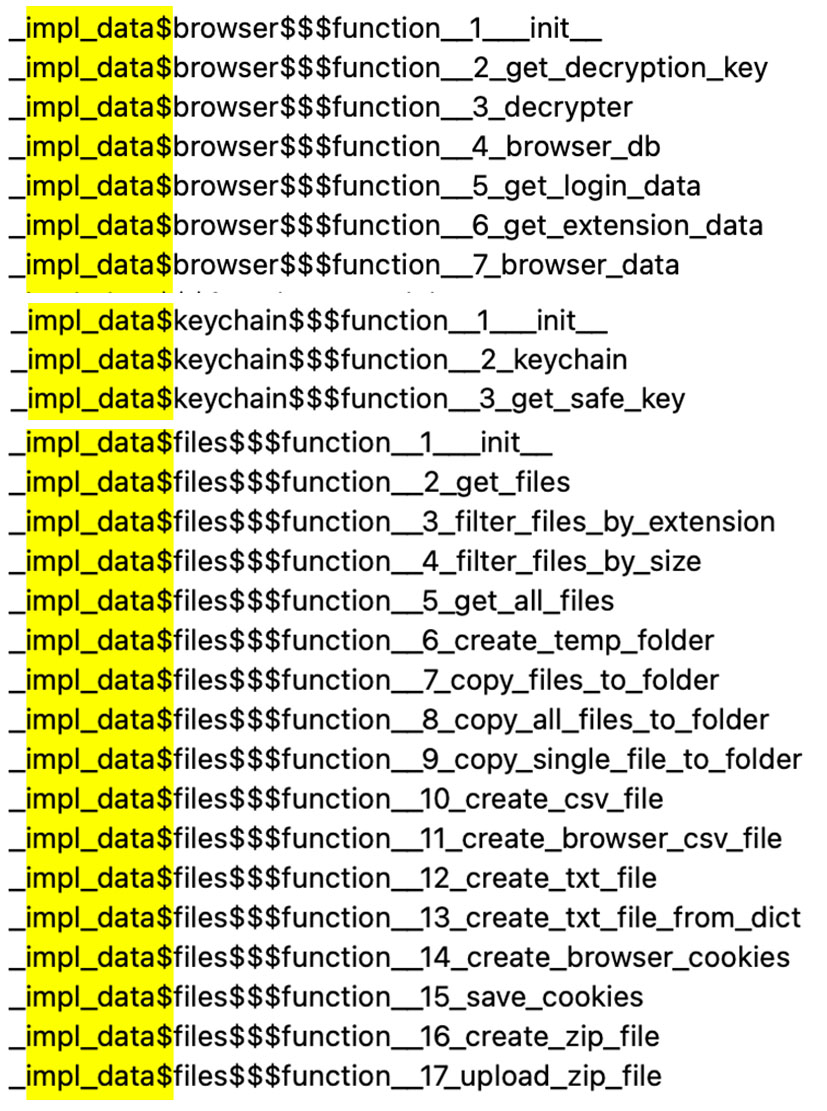
2. It tries to steal browser data and keychain. During our testing, we found the sample using the following commands on the system for file/directory discovery and system information collection:
- /bin/sh -c uname -p 2> dev/null
- /bin/sh -c security default-keychain
3. It uses chainbreaker to dump the keychain.
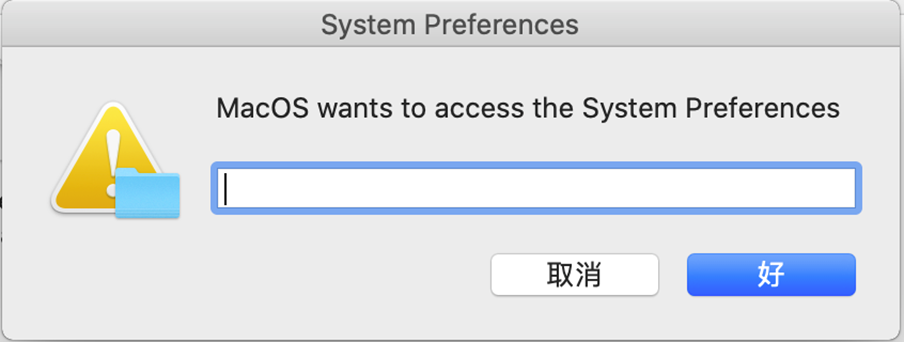
4. It pops a dialog box to defraud the user's password using osascript with the command:
osascript -e display dialog 'MacOS wants to access the System Preferences'
The dialog box is titled “System Preferences”, with icon caution default answer “with hidden answer.”
5. It tries to send the information collected to the command and control (C&C) server mac[.]cracked23[.]site in a Zip file.
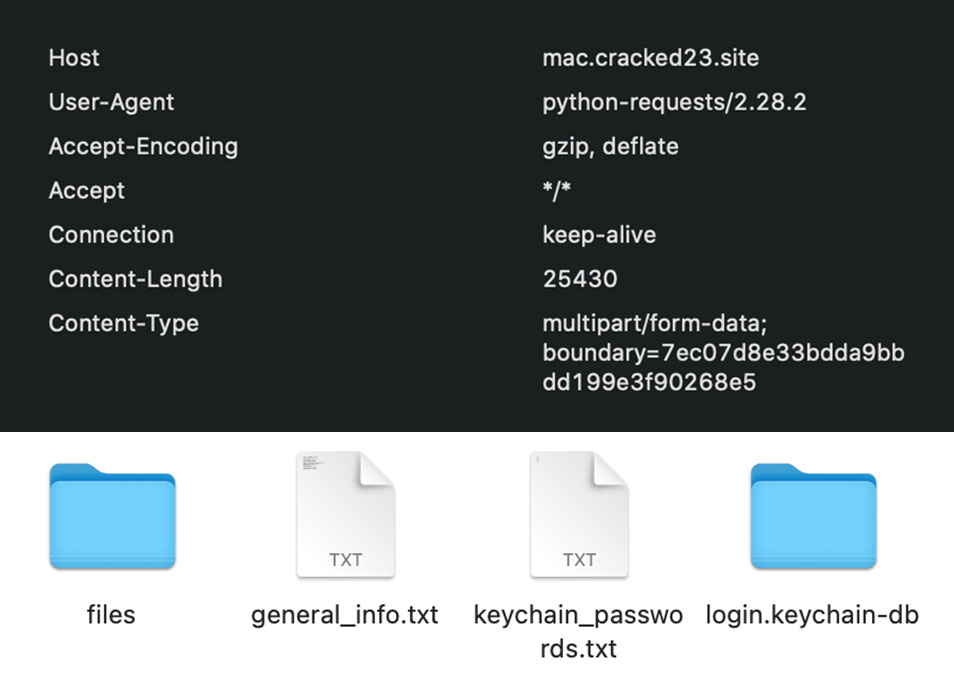
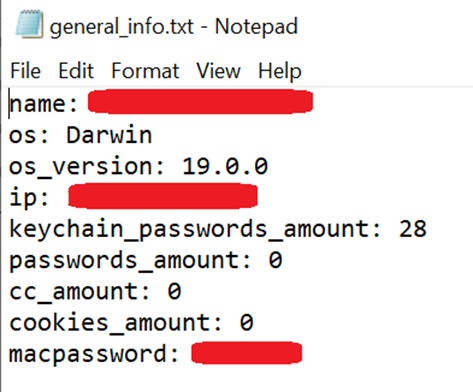
Once downloaded and running in the victim’s system, MacStealer steals the victim’s wallet data and proceeds to empty the cryptocurrency wallets. If the victim does not have a cryptocurrency wallet, the malware steals user information and the keychain. We were able to find tweets from the victims warning others of this campaign.
Spread via social media, other platforms
While scanning other social media posts, we found the threat actors’ efforts to spread MacStealer malware. Considering the tactics, techniques, and procedures (TTPs) used were similar, this sample and deployment could be the work of a single group. In this section, we use the Impulse Flow fake app as an example.
The cybercriminals create a Twitter account and related websites to advertise a fake game app. Here is a sample Twitter account with the verified icon. They then advertise the game as a free P2E online game based on blockchain technology.
There is a Linktree link (https[://]linktr[.]ee/impulseflow), which contains links to their other channels:
- Website: https[:]//play-impulseflow[.]com/
- Website: https[:]//impulse-flow[.]gitbook[.]io/impulse_flow-whitepaper/
- Website: https[:]//github[.]com/ImpulseFlowBeta/1[.]0[.]3
- Discord: https[:]//discord[.]gg/Impulse-flow
- Twitter: https[:]//twitter[.]com/lmpulse_Flow
- Telegram: https[:]//t[.]me/impulseflow_official
An image search query showed the media (images and videos) used in the Twitter and other social media accounts were plagiarized from the game Ember Sword. The cybercriminals leverage these platforms to entice potential victims to execute the malware executable. Some of the methods observed are as follows:
a) They advertise it as an open beta game and entice people to participate in their beta testing program in exchange for rewards. These beta testers are invited to join the threat actor's Discord or Telegram channel where they are given the malware binary or a link to download the malware binary. In some instances, the link or file will require a password which they receive through the Discord or Telegram channel: https[://]twitter.com/lmpulse_Flow/status/1633735911782400000
b) They send a direct message to content creators to help them promote their game. It is suspected to be a social engineering tactic targeting these influencers.
- https[://]twitter.com/powrdragn/status/1638024217412390913
- https[://]twitter.com/ender_thien/status/1637659072379101185
- https[://]twitter.com/naerycrypto/status/1637226997817692161
- https[://]twitter.com/CiervoKing/status/1637220583736762370
c) They post fake job vacancies and entice job hunters to download their malware binary: https[://]twitter.com/witty_taeil/status/1631654308218298368
| Website | Twitter account | App name | Confirmed downloaded file (SHA256) | Original game website |
|---|---|---|---|---|
| ryzex[.]io/ | https[://]twitter.com/RyzeX_web3 | RYZEX | https[://]drunk-robots.com/ | |
| pearlmetaverse[.]io/ | https[://]twitter.com/MetaversePearl | Pearl Land | ||
| mysteriangame[.]com | https[://]twitter.com/MysterianGame | Mysterian | ||
| worldofcreatures[.]io | https[://]twitter.com/WOC_io/ | World of Creatures | 8ea33c34647578b79dd8bb7dcf01a8ad1c79e7ada3fd61aca397ed0a2ac57276 | https[://]cryptureworld.com/ |
| toncap[.]io | https[://]twitter.com/neuromaster9/status/1614074785289437184?s=61
|
Ton Caps | 7bb7b51494c60401c8535baaa30cddb1c41c436e778092f30db5260c42cc70f6 | |
| play-impulseflow[.]com | https[://]twitter.com/lmpulse_Flow | Impulse Flow | 02e1d9ea3a0c16106d173b0e6349a18a9aeafacc38650e359cfe1ee2298aaa45 | https[://]embersword.com |
| https[://]twitter.com/PureMetaverse https[://]twitter.com/MetaPureLand |
Pureland |
Some people have posted on Twitter accounts warning about the malicious activities associated with the fake game apps and websites.
Conclusion
While not new, P2E games are enjoying a renewed interest and rise in popularity, and so will the efforts of threat actors aiming to take advantage of this growing trend. MacStealer malware is just one of many to take advantage of P2Es’ traction. P2E gamers, in particular, are lucrative targets because the economic model of these games requires them to adopt cryptocurrencies and wallets.
Security researchers can find investigating the delivery of the malware sample a challenge considering the threat actors used uncommon means to deliver their malware with the use of Discord and Telegram to directly communicate with their victims. Although this requires more effort, the victim’s profile (i.e., the user owns a crypto wallet) makes it worthwhile.
The malware doesn’t appear to be highly sophisticated, with a routine that requires a low skillset since the original code is a Python script. The main sample itself is not intricate, given the original code is a Python script compiled to a Mach-O binary using Nuitka, though it makes it difficult to decompile. This can be challenging for analysts to reverse engineer because, despite its simplicity, the compilation to a Mach-O binary using Nuitka shows how a well-placed attack on a good target could reap big rewards. In this case, they targeted P2E gamers who regularly use crypto wallets. Most of the profits collected by the cybercriminals are due to stolen cryptocurrencies siphoned off via social engineering techniques to deliver the malware to users’ devices (i.e., websites, Twitter accounts, and other related channels).
Discord enables channels for various purposes, among them P2E games and users. As a platform that evolved to become a gamer's haven to exchange information, downloading a link in Discord for access to a game — either as a user or tester — might not have immediately raised red flags among the victims. This also increases the likelihood of why the cybercriminals chose the platform to spread the malware. One victim noted, however, that there was a significant lack of interactions in the cybercriminals’ channel and flagged those details as a warning to others. Other users warned that as soon as they requested for screenshots or posted cautionary tweets, they were immediately banned from the channels.
Moreover, due to the recent disruptions in the Twitter’s ownership and changes in policies for account verification, it appears the cybercriminals abused it to easily get a verified account. This provides an illusion of legitimacy to improve fake apps’ and accounts’ social engineering capabilities. Using this technique can also easily be advertised using other platforms such as TikTok, YouTube, and Facebook. We may expect more of these trends in code/script compiling and malware delivery in the future.
To avoid and defend against threats like MacStealer, we strongly advise being wary of installing apps from unofficial sources and app platforms. Enabling the latest security solutions for devices can also help detect, block, and mitigate the risks of these kinds of threats.
Indicators of Compromise (IOCs)
You can download the full list of IOCs here.
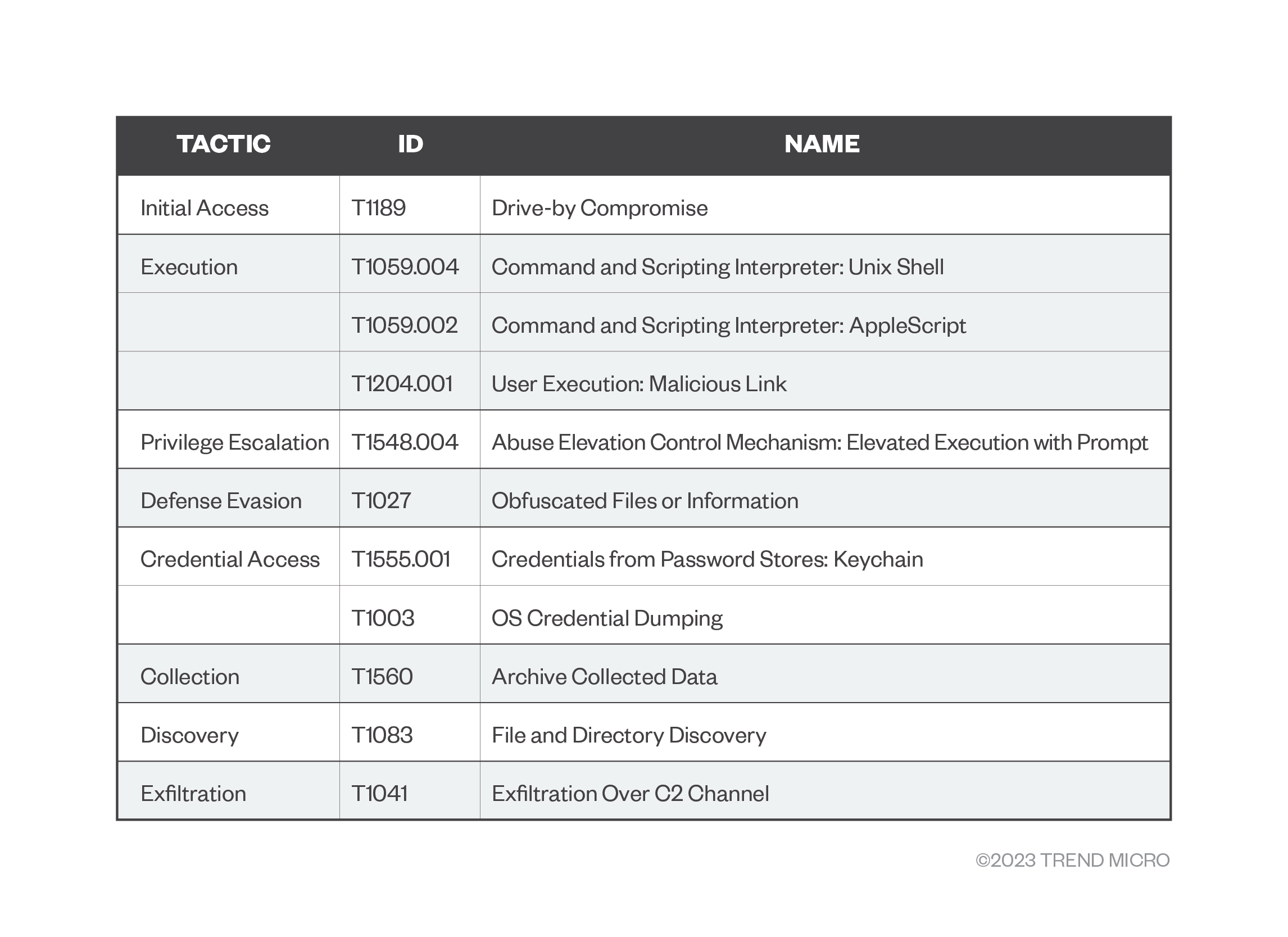
MITRE TTPs