Navigating New Frontiers: Trend Micro 2021 Annual Cybersecurity Report
The digital migrations and transformations that had enabled organizations to continue their operations amid the Covid-19 pandemic continued to usher in significant shifts in the threat landscape in 2021. Squarely positioned in these complex transitions were cybercriminals who were intent on exploring channels they could abuse and were only too eager to exploit security gaps.
Malicious actors pulled in higher profits with both tried-and-true and novel methods. They teamed up to maximize their skills and arsenals, and an evaluation on the impact of these attacks showed these incidents to be more costly and devastating for the victims. They also rode on developments related to the pandemic, around which they fashioned lures and themes for their campaigns. And the exploitation of old and new vulnerabilities continued to overwhelm security teams, in addition to the challenges of keeping organizations’ overall security postures intact in view of remote work arrangements.
Our annual cybersecurity report looks back at the most critical security concerns that emerged and persisted in 2021, with insights and recommendations aimed at helping organizations contend with the ever-evolving threat landscape.
Ransomware-as-a-service (RaaS) groups take their time during infiltration and reconnaissance before executing payloads, a marked contrast to the indiscriminate spray-and-pray approach of premodern ransomware operators. These groups of modern ransomware operators are also known to deliberately favor big-game targets. In 2021, the decrease in nonspecific attacks was noticeable, and critical industries such as government, banking, and healthcare bore the brunt of targeted ransomware attacks.
2021
The top three industries in terms of ransomware file detections in 2021
Source: Trend Micro™ Smart Protection Network™
Double extortion — whereby ransomware actors demand payment from victims in exchange for the restoration of access to encrypted data and simultaneously threaten to publicize sensitive information if the victims fail to pay — also helps produce maximum profits for cybercriminal groups. This tactic not only increases the likelihood of a higher payoff, but also financially supports the affiliates these groups recruit in the underground. Their affiliate programs allow members with limited technical knowledge to hone their existing skills and at the same time receive a percentage of the profit for their participation in attacking high-value victims. REvil (aka Sodinokibi) and Conti made headlines last year as the RaaS groups that notoriously plagued organizations around the world in the healthcare, insurance, manufacturing, transportation, and oil and gas industries with their weaponized mix of malware, exploits, and tools.
There was a 21% decrease in overall ransomware detections in 2021, but we see this not as an indication that threat actors launched fewer ransomware attacks. Rather, we view it as an effect of our early detection and blocking of infection and payload delivery tools used by modern ransomware operators, such as the Cobalt Strike beacon CoBeacon, the trojan Trickbot, and the information stealer BazarLoader. Our blocking of larger numbers of these tools, the presence of which is an early indicator of infection, might have hindered ransomware operators from bringing their attacks to fruition.
As more organizations moved to the cloud for digitization and business continuity, malicious actors were quick to take advantage of the inherent complexities in securing cloud environments. The hacking group TeamTNT eyed infrastructure misconfigurations as its attack vector of choice in 2021. It abused misconfigured servers to steal cloud service providers’ environmental metadata. And, in a cryptocurrency-mining and credential theft campaign, the group abused a role-based access control misconfiguration in Kubernetes to take control of multiple clusters, resulting in the compromise of nearly 50,000 IP addresses in China and the US.
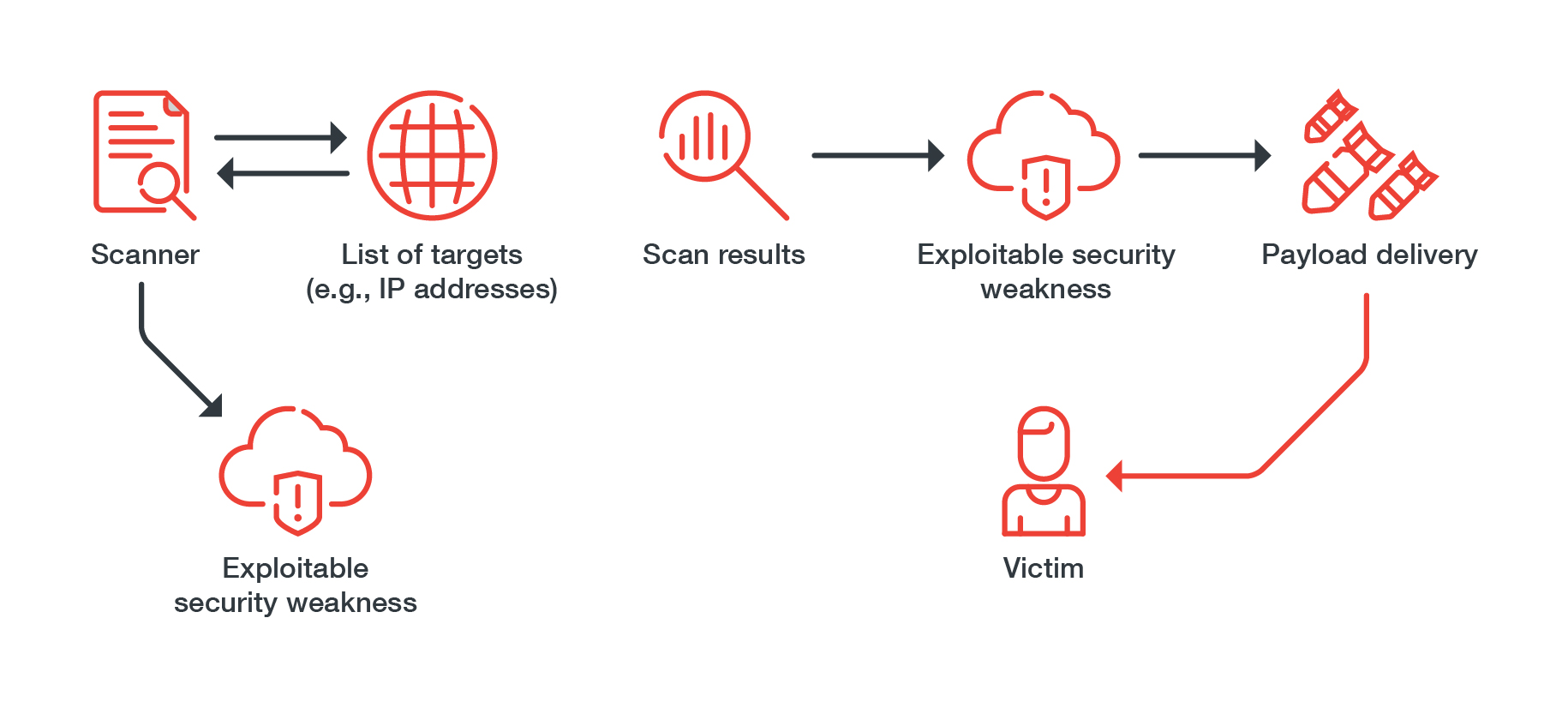
TeamTNT’s attack chain
Recognizing employees’ increased dependence on email for communication, malicious actors took a renewed interest in phishing campaigns as an effective means of spreading malware such as Emotet. Malicious actors also took advantage of the abundance of information on the pandemic and vaccine development by using Covid-19 as an overarching theme for phishing emails. Phishing attempts that were detected and blocked by Trend Micro Cloud App Security, an API-based solution that protects both users and organizations from threats to their cloud-based apps and services, nearly doubled from those in 2020. Nearly two-thirds of these were spam emails, while the rest were credential-phishing attempts. (Credential phishing involves cybercriminals’ use of fake login pages to trick potential victims into handing over their account credentials, whereas phishing by spam emails is a broader category that aims to get user information.)
2021
A comparison of the detections of spam phishing and credential-phishing attempts in 2021
Source: Trend Micro Cloud App Security
While phishing attempts increased, attempts at business email compromise (BEC) decreased. But we do not simply attribute this drop to a decline in cybercriminals’ interest or activity. Rather, it could be a result of the increased sophistication of BEC emails in evading antispam rules, with which we were able to keep pace: Trend Micro Cloud App Security detected and blocked a greater proportion of BEC attempts through authorship analysis — that is, by comparing the spoofing email with the writing style of the supposed sender — in 2021 than in the previous year.
A comparison of the proportions of BEC attempts blocked based on authorship analysis (white) and BEC attempts blocked based on behavior and intention analysis (black) in 2020 and 2021
Source: Trend Micro Cloud App Security
Trend Micro’s Zero Day Initiative™ (ZDI) released advisories for 1,604 vulnerabilities in 2021, 10% higher than in the previous year. Over a thousand of these were rated with high severity and more than 50 were rated critical.
| Severity | 2020 | 2021 |
| Critical | 173 | 54 |
| High | 983 | 1,138 |
| Medium | 187 | 148 |
| Low | 110 | 264 |
| Total | 1,453 | 1,604 |
A comparison of the proportions of Common Vulnerability Scoring System (CVSS) ratings among vulnerabilities disclosed by Trend Micro’s ZDI program in 2020 and 2021
Source: Trend Micro™ Zero Day Initiative™
Despite the availability of patches for them, many vulnerabilities that could be rightly described as old continued to dodge obsolescence. In the cybercriminal underground, demand persisted for exploits of legacy vulnerabilities, including those from as far back as 2005. Our 2021 study found that nearly a quarter of the exploits sold in the underground were of vulnerabilities that were at least three years old.
Unpatched security flaws led to some noteworthy incidents in 2021. One such flaw was Log4Shell (CVE-2021-44228), a high-severity vulnerability in Apache Log4j, a Java-based logging tool, that could allow attackers to send crafted log messages that execute arbitrary code. First reported privately to Apache in November, Log4Shell drew attention from the security and tech industries for the breadth of remediation that it warranted. Although the open-source Apache community had released a patch for it in December, it was still exploited in various illicit activities, including data theft, cryptocurrency mining, and ransomware attacks.
Vulnerabilities in Microsoft Exchange Server also made waves in 2021. Even though patches for them had been released, ProxyLogon (CVE-2021-26855) and ProxyShell (CVE-2021-34473 and CVE-2021-34523) were still abused for malicious activities. Most notably, they were used by the operators of the Squirrelwaffle loader to gain access to and hijack the email accounts of their victims.
Overall blocked threats in 2021
94,289,585,240
Blocked email threats
Blocked malicious URLs
Blocked malicious files
Email reputation queries
URL reputation queries
File reputation queries
Blocked mobile app threats
Blocked IoT threats
Blocked Smart Home Network threats
A comparison of the numbers of blocked email, URL, and file threats, of email, URL, and file reputation queries, and of blocked mobile app, IoT, and Smart Home Network threats in 2020 and 2021
Source: Trend Micro Smart Protection Network, including Mobile App Reputation Service, IoT Reputation Service, and Smart Home Network
Download and read our full report for more insights on the cybersecurity landscape of 2021 and for recommendations on how to build an effective defense strategy against current and emergent threats.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One