
Ransomware brings about bigger global outbreaks despite fewer major players
The number of new ransomware families rose 32 percent from 2016 to 327, showing that there were still active ransomware developers trying to take advantage of a plateauing trend. However, the ransomware-related threats detected by the Trend Micro™ Smart Protection Network™ security infrastructure went in the opposite direction and dipped 41 percent. Apparently, only a select few of these new families actually made an impact in 2017.
More ransomware families emerged in 2017: Comparison of total number of new ransomware families seen
Fewer major players despite increase in new ransomware families: Comparison of total number of detected ransomware-related threats
1,078,091,703
2016 Ransomware-related threats
631,128,278
2017 Ransomware-related threats
But the ransomware events that did affect users were significantly larger. These widespread attacks struck multiple countries and reportedly resulted in billions of U.S. dollars in damage. In addition to WannaCry and Petya, the two most notorious, there was the more recent case of Bad Rabbit: In October, the ransomware hit a number of enterprises across Russia, Eastern Europe and the U.S.
This was a marked difference from 2016, in which more ransomware incidents were reported, but the scale of the damage was typically contained to local offices and the ransom demanded was just in the tens of thousands of dollars.
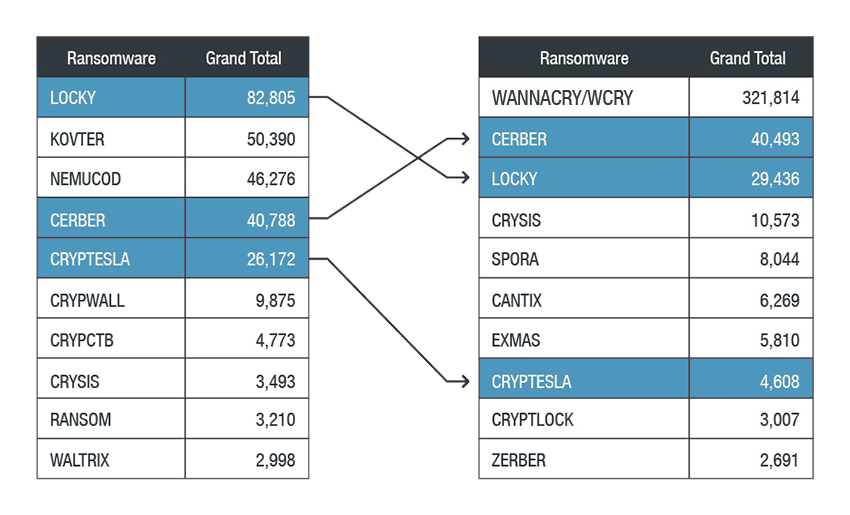
Prevailing ransomware families: Top ransomware families in 2017 remaining from 2016
Ransomware remains a clear and steady threat as many old families still affect users worldwide. Meanwhile, the more recent virulent outbreaks show that the new families are growing more sophisticated and hitting larger targets. Developers are constantly experimenting, trying to find profitable strategies. In 2017, they used diverse new methods; for example, more had been using fileless infection and pre-execution machine learning evasion techniques in addition to taking advantage of old vulnerabilities.
Effective ransomware typically abuses known exploits and techniques. Enterprises should then be diligent and employ proper patching policies, while securing their systems with multilayered solutions.





 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One