Security 101: Digital Extortion in 2018
 View Infographic: Digital Extortion in 2018
View Infographic: Digital Extortion in 2018
Digital extortion is one of the most lucrative ways cybercriminals can profit in today’s threat landscape. Many have fallen victim to this particular scheme and been bilked of their money — from ordinary users to big enterprises.
Everyone is a potential target, which is why being informed about what digital extortion is, how it’s carried out and how to protect against it is critical. This is especially relevant in 2018, where we predict that digital extortion efforts will involve other methods besides the tried and tested ransomware attack.
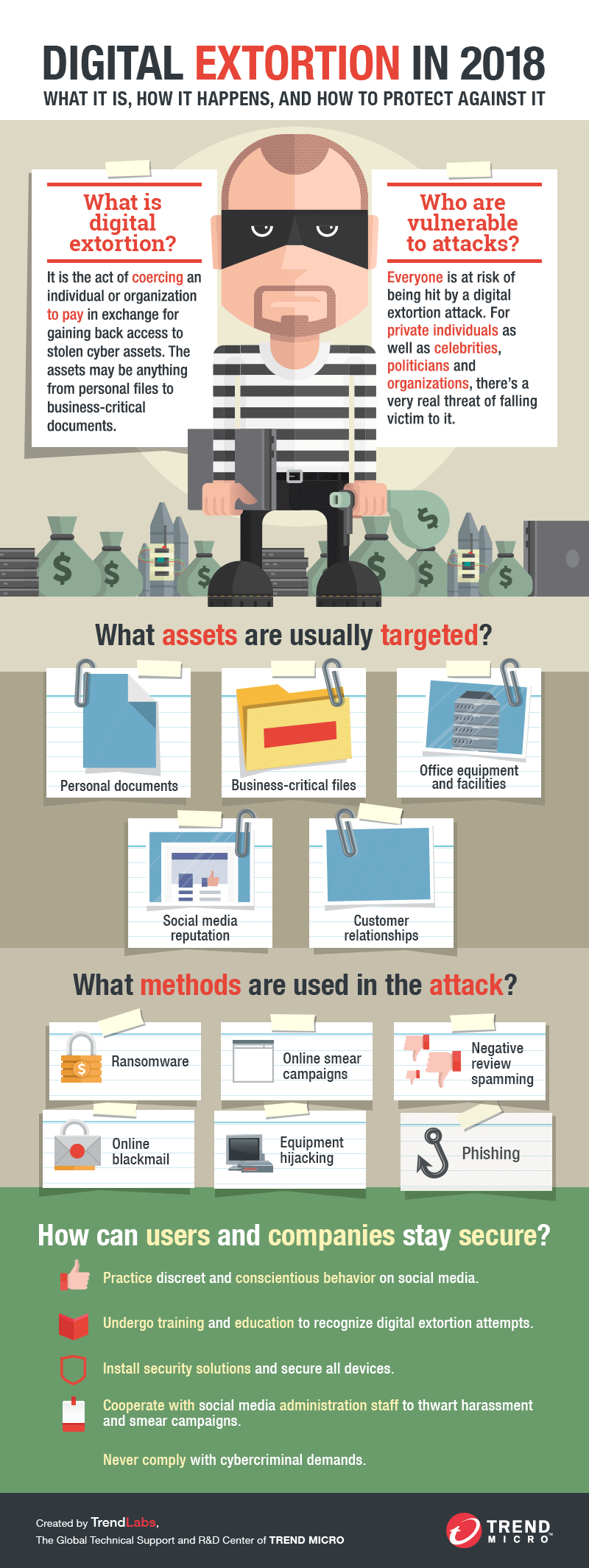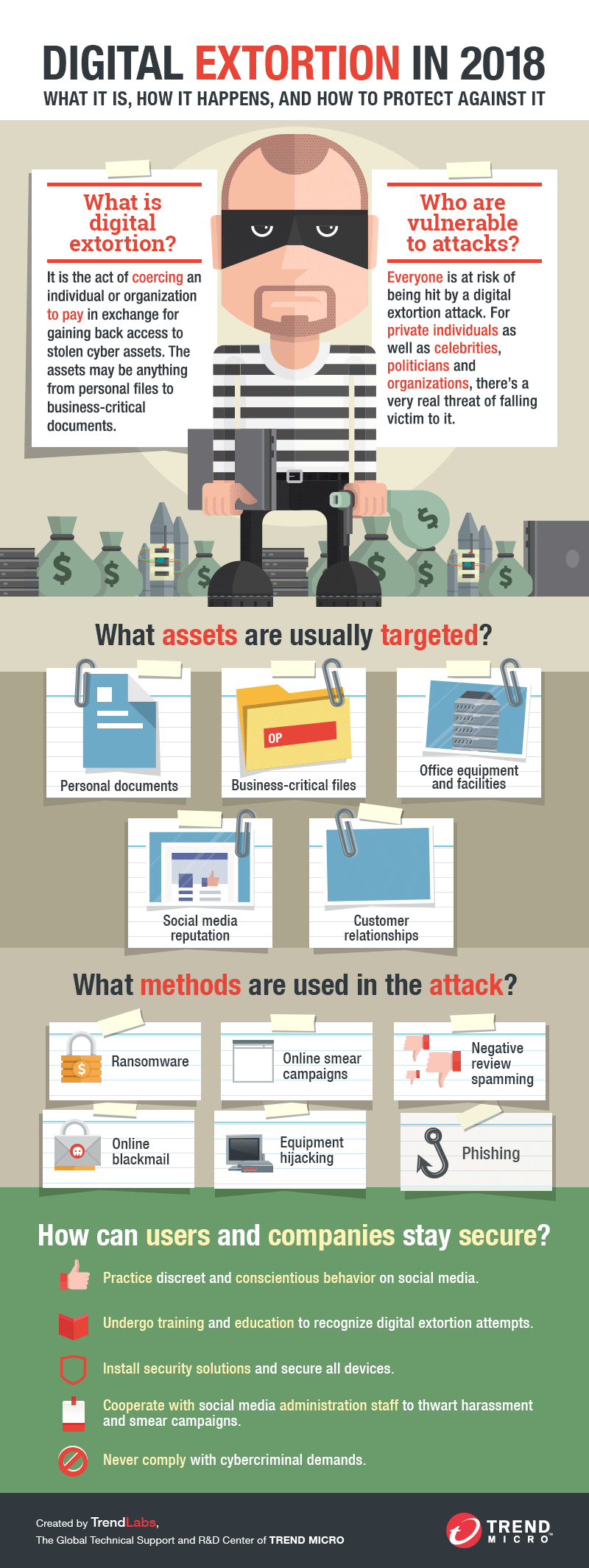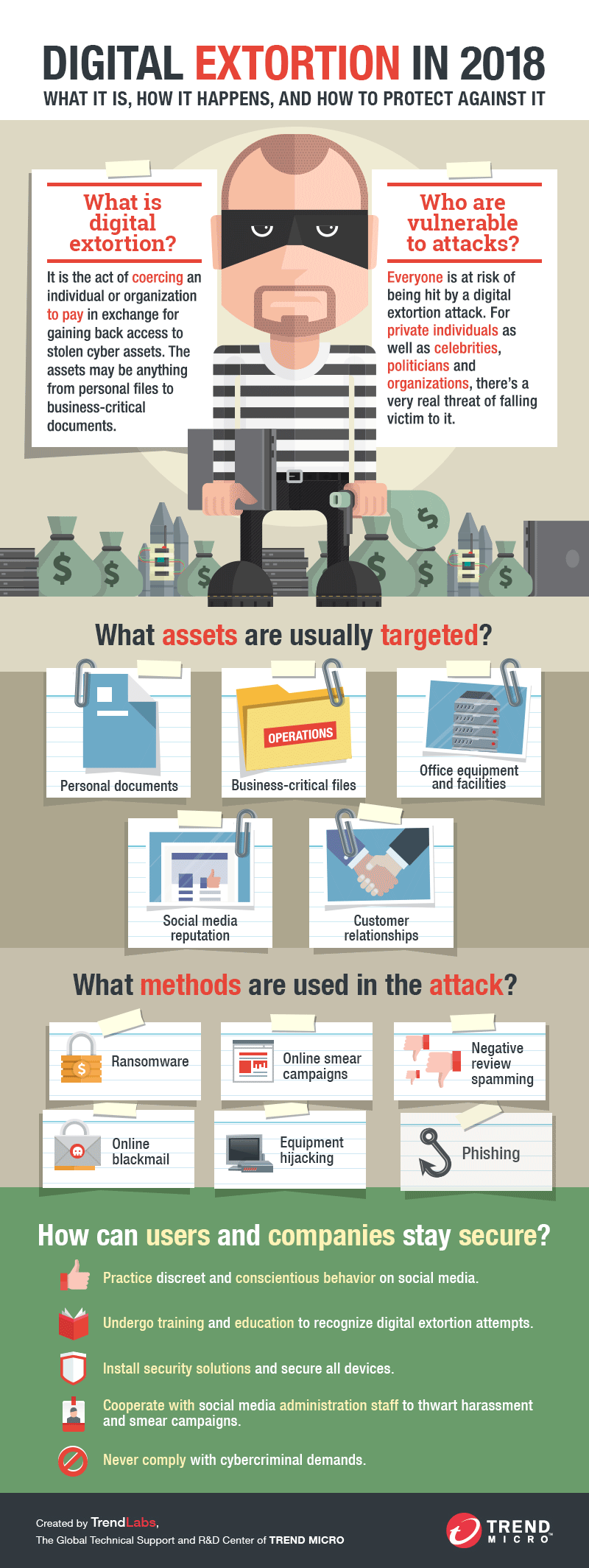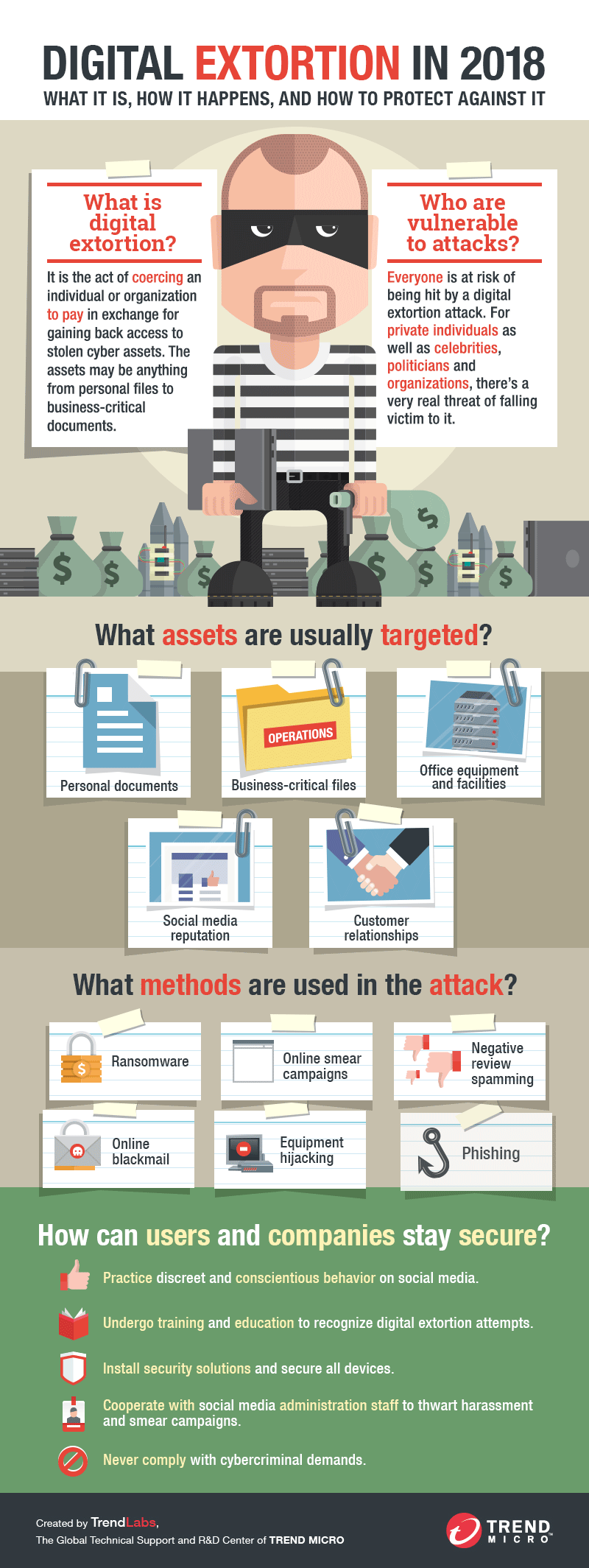
What is digital extortion?
Digital extortion is the act of coercing an individual or organization to pay in exchange for gaining back access to stolen cyber assets. The assets may be anything that directly ties in to the victim’s personal information, business operations, or financial interests. Examples of these include document files, database files, access to servers, etc.
How is digital extortion carried out?
Currently, the bulk of digital extortion is done with ransomware attacks. A ransomware attack involves malware that, upon infecting a user’s system, encrypts the files stored in the hard drives, thereby rendering them inaccessible. It typically compromises the personal documents that the user may have stored in those drives. In any case, the user is then asked, either through a text file or a message window, to send an amount of money to the culprit in order to have the files decrypted. Should the user pay, the act of digital extortion is deemed complete.
Given the success of ransomware campaigns, cybercriminals are likely to use other methods of digital extortion, including the following:
- Online smear campaigns. Cybercriminals may engage in online smear campaigns against public figures, such as celebrities and politicians, which may go further into humiliation or harassment campaigns against the individuals. Once enough damage has been done to the targets’ online presence on social media, the cybercriminals may offer to stop the campaign for a fee.
- Negative review spamming or black propaganda. Companies with upcoming new releases such as movies and devices may find the review pages of their products being spammed with negative reviews, in an attempt to bring the public perception of the products down. Once enough damage has been done, the cybercriminals may offer to retract the reviews for a price.
- Online blackmail. Cybercriminals may blackmail public figures such as celebrities and politicians with compromising images or details they may have obtained through hacking.
- Equipment or machinery hijacking. Cybercriminals may hack into assembly line manufacturing equipment, industrial robots, or public utility management systems and deactivate them/render them inaccessible. They will then demand money from the owners in return for giving back access to the equipment.
- Phishing. Users may find themselves being subjected to phishing, wherein their online credentials and other details are stolen through spoofed login websites. This can then result in unauthorized access to personal or even corporate files.
It should be noted that while most of these threats may seem geared toward public figures and companies, the fact remains that cybercriminals commonly carry out their attacks indiscriminately. This means that even private individuals or people who are not in the public spotlight may also become victims of digital extortion.
What safeguards can be used against digital extortion?
Users and public individuals can mitigate most digital extortion attacks by doing the following:
- Refrain from posting too many details on social media.
- Avoid taking compromising or embarrassing pictures and saving them in an online archive or storage service, as these may be hacked by cybercriminals.
- Secure devices, accounts, and computers with strong passwords and security software.
- Report all instances of digital extortion to the proper authorities. Refuse to cooperate with the extortionist’s demands.
- Seek the help of social network staff for harassment and smear campaigns on social media.
Companies can do the following to be secure from digital extortion attacks:
- Educate employees and officers on how to recognize digital extortion attempts.
- Have contingency communication channels and plans for official financial transactions in case of staff unavailability.
- Always verify identities of business contacts through trusted secondary sources.
- Deploy security solutions for all online technologies used in business. Apply critical patch updates to all software as soon as they are available.
- Adopt security strategies and solutions to comply with global data protection initiatives and regulations.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Messages récents
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One