Defending Against PoS RAM Scrapers: Current Strategies and Next-Gen Technologies
 View research paper: Defending Against PoS RAM Scrapers
View research paper: Defending Against PoS RAM Scrapers
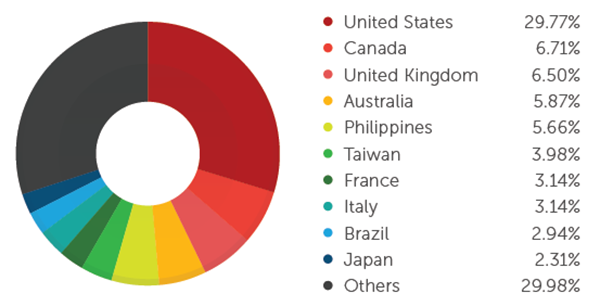
Stealing payment card data has become an everyday crime that yields quick monetary gains. Attackers aim to steal data stored in the magnetic stripe of payment cards, optionally clone the cards, and run charges on the accounts associated with them. In the past, attackers physically skimmed payment cards. Today, they have resorted to using malicious software to steal payment card data, primarily from credit cards. They found low-hanging fruit within the layered payment card security framework—unencrypted credit card data. They prey on vulnerable systems to get inside their targets’ networks, including the networks of third-party vendors who have access to partner networks with stronger security.
2014: Just the Tip of the Iceberg for PoS Threats?
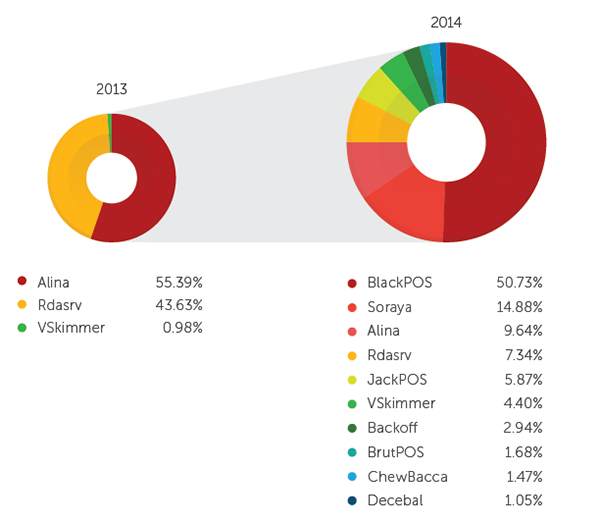
The year 2014 showed that point-of-sale (PoS) threats took the spotlight with the Target data breach in January, and several other incidents throughout the year that followed. By the end of the third quarter of 2014, six new PoS RAM scraper malware variants were found. The number of PoS RAM scraper families we are detecting has increased from three in 2013 to 10 in 2014.
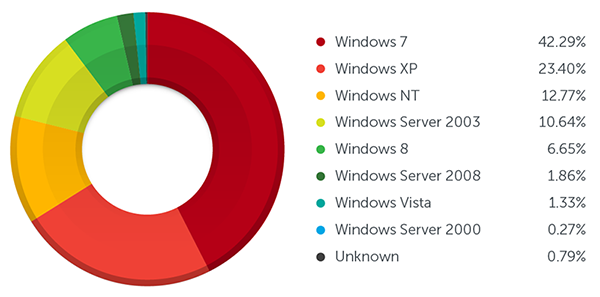
To make matters worse, a lot of existing PoS systems still run on older operating systems such as Windows XP and Windows Server 2000, even after Microsoft ended support. These operating systems are more vulnerable to potential attacks, as they will no longer receive patches for new vulnerabilities. Newer systems running the latest OS aren't entirely safe either, and still needs to be regularly patched and updated to reduce the risk.
The attached research paper discusses how PoS RAM scrapers infect systems and exfiltrate stolen data. It also provides a list of defense technologies and strategies that can be used to defend against the threat, recommendations for small businesses and medium and large enterprises, and new technologies that PoS system vendors and credit card brands are introducing to protect businesses and consumers.
[More: See how Endpoint Application Control protects PoS devices]
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One