Dwindling FAKEAV Business Spurs Ransomware Infections in Europe
The recent increase of ransomware infections in Europe illustrates the fluid nature of cybercrime. Cybercriminals seemed to have recouped and looked for alternative means of income because of the initiatives done by law enforcements against FAKEAV. One of these alternatives was ransomware, a threat that was origainally rampant in Russia. We believe that the sudden increase of ransomware incidents outside Russia and across Europe is a by-product of the dwindling FAKEAV business.
What is ransomware?
Ransomware refers to a class of malware that holds a computer "hostage" until the user pays a particular amount or abides by specific instructions . The ransomware then restricts access to the system when executed. Some cases of ransomware also repeatedly show messages that force users into paying the “ransom” or performing the desired action. There are even ransomware variants that may encrypt files found on the system's hard drive. Users are then forced to pay up because the system becomes rendered useless because of the file encryption.
Recently, the cybercriminals behind this threat also made use of online payment methods such as Ukash and PaySafeCard as a way for users to pay the ransom. Ransomware attacks were also frequent in Russia.
How prevalent is ransomware in Europe?
Incidents of ransomware infection were previously concentrated in Russia. However, we recently uncovered several attacks that targeted other European countries as well.
The website of a well-known sweet shop in France was injected with a ransomware variant. Users who visited the site were infected with TROJ_RANSOM.BOV, a ransomware that displays a window that spoofs the French Gendarmerie and holds the system “captive”. Similar incidents also sprouted on other European countries with ransomware spoofing the Belgian eCops and the German Bundespolizei.
The gathered data from Trend Micro Smart Protection Network™ also confirms ransomware attacks spreading across Europe.

Why are ransomware infections spreading across other parts of Europe?
One reason for the spread of ransomware attacks in Europe is the increasing difficulty with using several payment methods and the continuous noose tightening happening with the FAKEAV industry. In fact, last June 23, the Russian police arrested ChronoPay co-founder Pavel Vrublevsky as the popular online payment company was touted a key player in the FAKEAV market. Several reports spoke of Vrublevsky's involvement with the FAKEAV industry. Police reports showed that ChronoPay supported several FAKEAV brands, including the infamous MacDefender.
Ransomware’s use of alternative online payment methods like Ukash and PaySafeCard may have contributed to the increase in ransomware infection as both methods are convenient ways to extract money from European victims.
Is the increase in ransomware connected with the decrease in FAKEAV?
The FAKEAV industry is an economic ecosystem composed of leaders, developers, and middle men. The arrest of major FAKEAV key players and the continuous efforts of law enforcements poses challenges to FAKEAV as a criminal business today.
Given its profitability, this blow to the FAKEAV market may have prompted a number cybercriminals to shift to other underground businesses. This could have contributed to the growth of ransomware market, hence, the spread of ransomware infection to other parts of Europe.
Why did cybercriminals shift from FAKEAV to ransomware attacks?
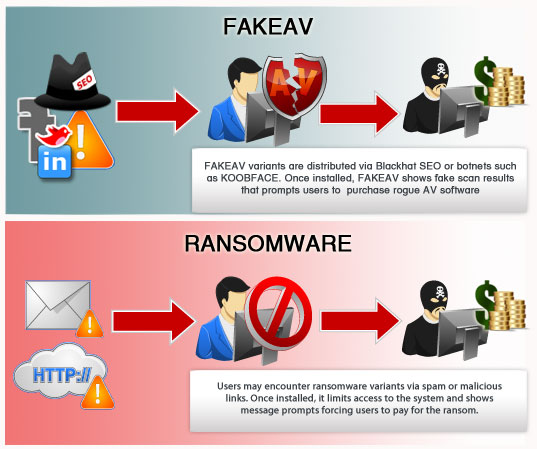
Both FAKEAV and ransomware are known lucrative enterprises in the cybercrime underground economy. FAKEAV and ransomware have differences that may or may not be an advantage. As cited previously, the recent use of payment methods like UKash and PaySafeCard by ransomware attacks provide a level of anonymity that was not present on FAKEAV attacks. Below is a side-by-side comparison of the FAKEAV and ransomware business models, routines, and distribution.
|
FAKEAV |
Ransomware |
|
|
Routines |
Shows infection warning, fake scanning results. Prompts affected users to purchase the fake antivirus product. |
Displays warning messages on the desktop and restricts access to the system. In some cases ransomware encrypts files found on users’ hard drives. Forces users to pay or register for a service |
|
Business model |
Pay-per-install (PPI). FAKEAV affiliates have a specific PPI network that differs from traditional PPI networks. FAKEAV affiliates are paid per user purchase and not per installation, which is typical with traditional PPI. |
Ransomware follows the traditional PPI network, where ransomware agents are paid per installation of ransomware variant. |
|
Distribution model |
FAKEAV affiliates work with other known botnets like KOOBFACE to distribute FAKEAV variats. Blackhat SEO is another form of distributing this malware. |
Ransomware are distributed through sites such as pornographic sites or legitimate sites injected with ransomware. |
What is the implication of this increase in ransomware infection?
The increase in the number of ransomware attacks amid the of slowing of FAKEAV business shows that cybercriminals have other schemes to tap. Though commendable, successful initiatives of law enforcements against FAKEAV do not spell the end of cybercrime. Users must remain vigilant and practice proper computing behavior to avoid the other traps on the Internet.
What can users do to prevent this threat from infecting their computers?
Always be wary of possible malicious links. Ransomware is typically encountered via malicious sites. Users should avoid clicking dubious-looking links found on common infection vectors like spam. Make it common practice to copy and paste URLs onto the address bar instead of directly clicking links. Better yet, bookmark trusted and reputable sites.
Update systems regularly. As with the ransomware case that uses the Blackhole Exploit kit, users should apply the latest security patch to protect their systems from exploits abusing known vulnerabilities.
Keep updated with the latest security trends. Education is key. Make it a habit to read security news to see the current trends in threat landscape and to know how to avoid becoming victims of emerging ones.
Are Trend Micro users protected from this threat?
Yes. Trend Micro Web Reputation Technology blocks verified sites hosting ransomware, while the File Reputation Technology detects and promptly deletes ransomware variants.