Blackhole Exploit Kit Spam Run Using Microsoft as Bait
Data de publicação: 12 setembro 2012
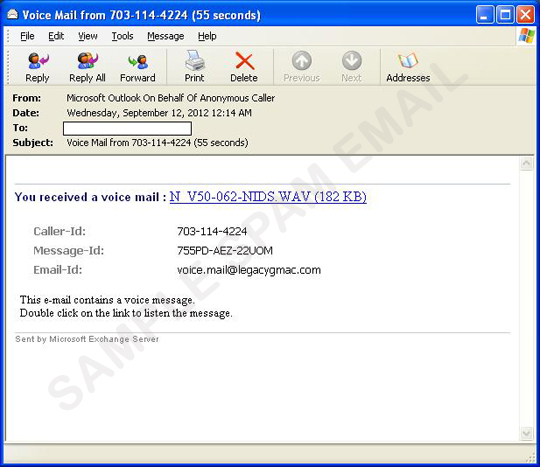
This spam run attempts to trick its recipients into thinking that it is from Microsoft Outlook. The message asks the recipient to click on a link to retrieve a voicemail message. Once the link is clicked, it redirects to a site hosting a malicious JavaScript:
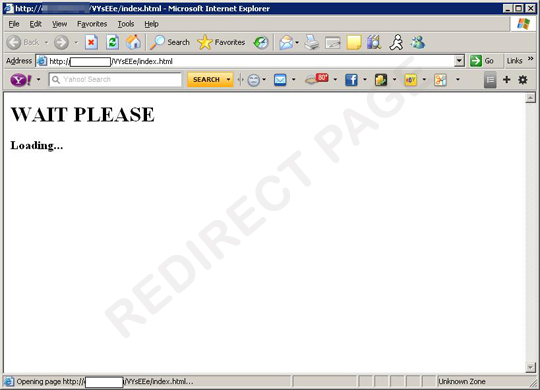
The script points the user to a blackhole exploit kit server hosting a .JAR file. The said file is executed, and downloads other malicious files on the affected computer.
Trend Micro™ Smart Protection Network™ protects users from this threat by blocking the spam mail samples, as well as any related malicious URLs and malware.
Data/Hora do bloqueio de spam: 12 setembro 2012 GMT-8
TMASE
- Versão do mecan
- Patrón TMASE: 9180