The Rise of XHTML Attachment in Phishing Emails
May 18, 2023
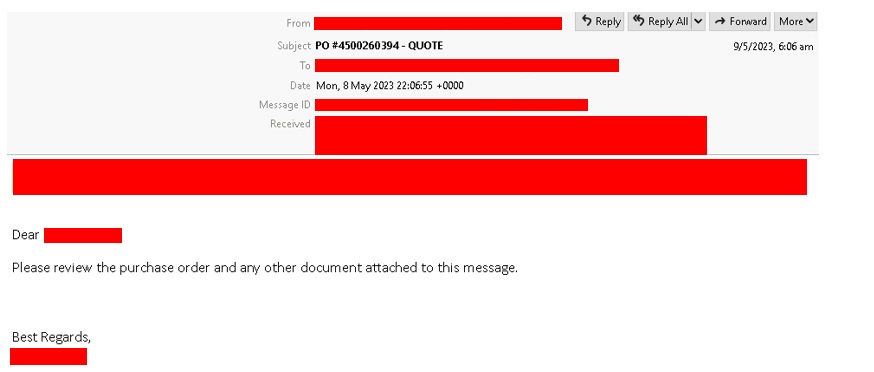
Attackers have commonly use HTML attachments for phishing due to its capability of designing a webpage. They would need a webpage in order to mimic login pages of well-known companies, which in turn will trick the user to input their credentials thinking that they are in a legitimate website. However, we have recently observed that more attackers now use .xhtml to substitute for the usual html attachments.
In emails:

In attachments:
Inside .xhtml attachment:

This is unusual since first of all, XHTML format is not entirely new. In fact, it was first introduced in the year 2000. This begs the question, why are attackers considering this file format to distribute their phishing emails?
Well, it is crucial to note that .xhtml and .html are not so different from each other. It is just that the former uses a stricter syntax than its counterpart. In fact, .html is very much preferred over .xhtml due to how flexible it is in web development, and it also supported by numerous web browsers, whereas .xhtml has limited support and is much more difficult to use.
One conclusion that can be drawn here is that attackers are continuously reinventing themselves by trying to use uncommon file attachments to bypass spam filters while still achieving their intended purpose. Since .xhtml and .html can both display webpages, they are still successful in delivering their phishing attacks. As a reminder, phishing attacks will always be there when you least expect it so always be on the lookout.
SPAM BLOCKING DATE / TIME: May 18, 2023 GMT-8
TMASE INFO
- ENGINE:9.0.1004
- PATTERN:2.7634.000
