Backdoor.Win32.FUPORPLEX.C
HEUR:Trojan.Win32.Perkiler.vho (Kaspersky), Trojan-Downloader.Win32.Delf, Trojan-Downloader.Win32.Delf (Ikarus)
Windows


Threat Type: Backdoor
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
This Backdoor arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
TECHNICAL DETAILS
Arrival Details
This Backdoor arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Backdoor drops the following files:
- %Windows%\winupdate32.log if OS is x32
- %Windows%\winupdate64.log if OS is x64
- One of the following:
- %Windows%\sens.dll
- %Windows%\cscdll.dll
- One of the following:
- %Windows%\AppPatch\Acpsens.dll -> copy of legit %Windows%\sens.dll
- %Windows%\AppPatch\Acpcscdll.dll -> copy of legit %Windows%\cscdll.dll
- %Windows%\AppPatch\Ke{6 random numbers}.xsl
- %Windows%\AppPatch\Ac{Characters based on C: volume serial number}.sdb -> copy of %Windows%\AppPatch\Ke5{6 random numbers}.xsl
- %Windows%\AppPatch\Custom\{7 random characters}.tmp -> copies of its components
- %System%\Ms{Characters based on C: volume serial number}App.dll
- %System%\drivers\dump_{random hex strings}.sys
(Note: %Windows% is the Windows folder, where it usually is C:\Windows on all Windows operating system versions.. %System% is the Windows system folder, where it usually is C:\Windows\System32 on all Windows operating system versions.)
It adds the following processes:
- netsh interface ipv6 install
- netsh.exe ipsec static add policy name=qianye
- netsh.exe ipsec static add filterlist name=Filter1
- netsh.exe ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=445 protocol=TCP
- netsh.exe ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=135 protocol=TCP
- netsh.exe ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=139 protocol=TCP
- netsh.exe ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=445 protocol=UDP
- netsh.exe ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=135 protocol=UDP
- netsh.exe ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=139 protocol=UDP
- netsh.exe ipsec static add filteraction name=FilteraAtion1 action=block
- netsh.exe ipsec static add rule name=Rule1 policy=qianye filterlist=Filter1 filteraction=FilteraAtion1
- netsh.exe ipsec static set policy name=qianye assign=y
- %System%\svchost.exe -k NetworkService
- %System%\svchost.exe -k LocalService
(Note: %System% is the Windows system folder, where it usually is C:\Windows\System32 on all Windows operating system versions.)
It creates the following folders:
- %System Root%\RECYCLER
- %Windows%\AppPatch
- %Windows%\AppPatch\Custom
- %Program Files%\OTFDXCNEJDKCODPNIZZRXFWJIBKVCIHFNGXU\OTFDXCNEJDKCODPNIZZRXFWJIBKVCIHFNGXU\
- %Program Files%\OTFDXCNEJDKCODPNIZZRXFWJIBKVCIHFNGXU\
(Note: %System Root% is the Windows root folder, where it usually is C:\ on all Windows operating system versions.. %Windows% is the Windows folder, where it usually is C:\Windows on all Windows operating system versions.. %Program Files% is the default Program Files folder, usually C:\Program Files in Windows 2000(32-bit), Server 2003(32-bit), XP, Vista(64-bit), 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit) , or C:\Program Files (x86) in Windows XP(64-bit), Vista(64-bit), 7(64-bit), 8(64-bit), 8.1(64-bit), 2008(64-bit), 2012(64-bit) and 10(64-bit).)
Other System Modifications
This Backdoor deletes the following files:
- %System%\Ms{Characters based on C: volume serial number}App.dll
- One of the following:
- %Windows%\sens.dll
- %Windows%\cscdll.dll
- One of the following:
- %Windows%\AppPatch\Acpsens.dll
- %Windows%\AppPatch\Acpcscdll.dll
- .tmp files in %Windows%\AppPatch\Custom\
- .tmp files in %Windows%\AppPatch\
- .xsl files in %Windows%\AppPatch\
(Note: %System% is the Windows system folder, where it usually is C:\Windows\System32 on all Windows operating system versions.. %Windows% is the Windows folder, where it usually is C:\Windows on all Windows operating system versions.)
It deletes the following folders:
- %System Root%\RECYCLER
(Note: %System Root% is the Windows root folder, where it usually is C:\ on all Windows operating system versions.)
It adds the following registry entries:
HKEY_LOCAL_MACHINE\SOFTWARE\SoundResearch
UpdaterLastTimeChecked1 = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Installer\
Folders
%Program Files%\OTFDXCNEJDKCODPNIZZRXFWJIBKVCIHFNGXU\OTFDXCNEJDKCODPNIZZRXFWJIBKVCIHFNGXU\ = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Installer\
Folders
%Program Files%\OTFDXCNEJDKCODPNIZZRXFWJIBKVCIHFNGXU\ = 1
HKEY_LOCAL_MACHINE\SYSTEM\{ControlSet001 or CurrentControlSet}\
services\Ms{Characters based on C: volume serial number}App\Parameters
ServiceDll = %System%\Ms{Characters based on C: volume serial number}App.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows NT\CurrentVersion\Svchost
netsvcs = {add "Ms{Characters based on C: volume serial number}App" to the list}
HKEY_LOCAL_MACHINE\SYSTEM\{ControlSet001 or CurrentControlSet}\
services\Ms{Characters based on C: volume serial number}App
ImagePath = %System%\svchost.exe -k netsvcs
HKEY_CURRENT_USER\Software\Policies\
Microsoft\Windows Defender
DisableAntiSpyware = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\
Microsoft\Windows Defender
DisableAntiSpyware = 1
HKEY_CURRENT_USER\Software\Microsoft\
Windows Script\Settings
JITDebug = 0
Information Theft
This Backdoor gathers the following data:
- Current Date
- MAC Address
- System's service pack
- Volume Serial-ID
Other Details
This Backdoor adds the following registry keys:
HKEY_LOCAL_MACHINE\SYSTEM\{ControlSet001 or CurrentControlSet}\
services\Ms{Characters based on C: volume serial number}App\Parameters
HKEY_LOCAL_MACHINE\SYSTEM\{ControlSet001 or CurrentControlSet}\
services\Ms{Characters based on C: volume serial number}App
HKEY_LOCAL_MACHINE\SOFTWARE\SoundResearch
It does the following:
- Prompts user to restart the machine after its installation:
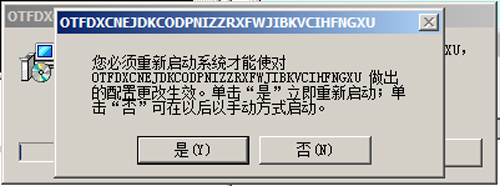
- The added process "svchost.exe -k LocalService" acts as watchdog for "svchost.exe -k NetworkService" and vise-versa.
- Loads shellcode into its memory by searching for the following files:
- %System%\svchost.exe -k LocalService:
- %Windows%\AppPatch\Ac{8 random characters}.sdb
- %Windows%\AppPatch\Ke{6 random characters}.xsl
- %System%\svchost.exe -k NetworkService:
- %Windows%\AppPatch\Custom\{random hex}.moe
- %Windows%\AppPatch\Custom\{random hex}.mow
- Does not proceed to its payload if current process is not "winlogon.exe" or "svchost.exe"
- Accesses the following URLs to get actual time:
- time.windows.com
- www.microsoft.com
- www.baidu.com
- Accesses the following URLs to download different modules:
- {BLOCKED}.{BLOCKED}.53.202:12941/{random hex}.moe
- {BLOCKED}.{BLOCKED}.192.42:10944/{random hex}.moe
- {BLOCKED}.{BLOCKED}.14.111:14215/{random hex}.moe
- {BLOCKED}.{BLOCKED}.221.229:14711/{random hex}.moe
- {BLOCKED}.{BLOCKED}.192.84:10848/{random hex}.moe
- {BLOCKED}.{BLOCKED}.192.41:10688/{random hex}.moe
- {BLOCKED}.{BLOCKED}.245.206:13245/{random hex}.moe
- {BLOCKED}.{BLOCKED}.148.190:12197/{random hex}.moe
- {BLOCKED}.{BLOCKED}.176.112:14424/{random hex}.moe
- {BLOCKED}.{BLOCKED}.240.7:16263/{random hex}.moe
- {BLOCKED}.{BLOCKED}.48.223:14284/{random hex}.moe
- {BLOCKED}.{BLOCKED}.101.29:15050/{random hex}.moe
- {BLOCKED}.{BLOCKED}.90.54:13914/{random hex}.moe
- {BLOCKED}.{BLOCKED}.176.19:20181/{random hex}.moe
- {BLOCKED}.{BLOCKED}.218.112:13921/{random hex}.moe
- {BLOCKED}.{BLOCKED}.35.126:25739/{random hex}.moe
- {BLOCKED}.{BLOCKED}.96.106:32139/{random hex}.moe
- {BLOCKED}.{BLOCKED}.158.0:25739/{random hex}.moe
- {BLOCKED}.{BLOCKED}.56.95:25739/{random hex}.moe
- {BLOCKED}.{BLOCKED}.150.126:16203/{random hex}.moe
- {BLOCKED}.{BLOCKED}.221.216:13879/{random hex}.moe
- {BLOCKED}.{BLOCKED}.192.84:10848/{random hex}.moe
- {BLOCKED}.{BLOCKED}.191.193:12399/{random hex}.moe
- {BLOCKED}.{BLOCKED}.28.45:12820/{random hex}.moe
- {BLOCKED}.{BLOCKED}.125.106:20187/{random hex}.moe
- {BLOCKED}.{BLOCKED}.154.13:11605/{random hex}.moe
- {BLOCKED}.{BLOCKED}.55.8:17116/{random hex}.moe
- {BLOCKED}.{BLOCKED}.55.7:18488/{random hex}.moe
- {BLOCKED}.{BLOCKED}.194.122:11627/{random hex}.moe
- {BLOCKED}.{BLOCKED}.194.121:11532/{random hex}.moe
- {BLOCKED}.{BLOCKED}.200.63:18126/{random hex}.moe
- {BLOCKED}.{BLOCKED}.32.126:11946/{random hex}.moe
- {BLOCKED}.{BLOCKED}.93.106:20175/{random hex}.moe
- {BLOCKED}.{BLOCKED}.155.0:14217/{random hex}.moe
- {BLOCKED}.{BLOCKED}.98.140:17969/{random hex}.moe
- {BLOCKED}.{BLOCKED}.31.45:11551/{random hex}.moe
- {BLOCKED}.{BLOCKED}.196.152:14469/{random hex}.moe
- {BLOCKED}.{BLOCKED}.184.178:11438/{random hex}.moe
- {BLOCKED}.{BLOCKED}.128.106:13632/{random hex}.moe
- {BLOCKED}.{BLOCKED}.78.9:19063/{random hex}.moe
- {BLOCKED}.{BLOCKED}.78.8:17015/{random hex}.moe
- {BLOCKED}.{BLOCKED}.200.226:17260/{random hex}.moe
- {BLOCKED}.{BLOCKED}.86.137:13008/{random hex}.moe
- {BLOCKED}.{BLOCKED}.120.35:20181/{random hex}.moe
- {BLOCKED}.{BLOCKED}.157.13:13941/{random hex}.moe
- {BLOCKED}.{BLOCKED}.58.8:16855/{random hex}.moe
- {BLOCKED}.{BLOCKED}.58.7:14807/{random hex}.moe
- {BLOCKED}.{BLOCKED}.197.122:15714/{random hex}.moe
- {BLOCKED}.{BLOCKED}.197.121:15586/{random hex}.moe
- {BLOCKED}.{BLOCKED}.203.63:16331/{random hex}.moe
- {BLOCKED}.{BLOCKED}.73.166:10642/{random hex}.moe
- {BLOCKED}.{BLOCKED}.56.173:11086/{random hex}.moe
- {BLOCKED}.{BLOCKED}.199.152:19555/{random hex}.moe
- {BLOCKED}.{BLOCKED}.13.58:14861/{random hex}.moe
- {BLOCKED}.{BLOCKED}.203.226:14514/{random hex}.moe
- {BLOCKED}.{BLOCKED}.89.137:17580/{random hex}.moe
- {BLOCKED}.{BLOCKED}.123.35:32139/{random hex}.moe
- {BLOCKED}.{BLOCKED}.32.32:19232/{random hex}.moe
- {BLOCKED}.{BLOCKED}.243.103:13305/{random hex}.moe
- {BLOCKED}.{BLOCKED}.86.10:10586/{random hex}.moe
- {BLOCKED}.{BLOCKED}.193.205:19487/{random hex}.moe
- {BLOCKED}.{BLOCKED}.27.140:13270/{random hex}.moe
- {BLOCKED}.{BLOCKED}.85.250:16021/{random hex}.moe
- {BLOCKED}.{BLOCKED}.95.140:13295/{random hex}.moe
- {BLOCKED}.{BLOCKED}.35.32:21396/{random hex}.moe
- {BLOCKED}.{BLOCKED}.50.202:19150/{random hex}.moe
- {BLOCKED}.{BLOCKED}.189.42:12147/{random hex}.moe
- {BLOCKED}.{BLOCKED}.218.229:17357/{random hex}.moe
- {BLOCKED}.{BLOCKED}.189.84:18127/{random hex}.moe
- {BLOCKED}.{BLOCKED}.145.190:18049/{random hex}.moe
- {BLOCKED}.{BLOCKED}.173.112:10672/{random hex}.moe
- {BLOCKED}.{BLOCKED}.237.7:16869/{random hex}.moe
- {BLOCKED}.{BLOCKED}.45.223:17146/{random hex}.moe
- {BLOCKED}.{BLOCKED}.87.54:15442/{random hex}.moe
- {BLOCKED}.{BLOCKED}.196.205:10273/{random hex}.moe
- {BLOCKED}.{BLOCKED}.215.112:10688/{random hex}.moe
- {BLOCKED}.{BLOCKED}.31.140:17935/{random hex}.moe
- {BLOCKED}.{BLOCKED}.53.95:19119/{random hex}.moe
- {BLOCKED}.{BLOCKED}.218.216:16947/{random hex}.moe
- {BLOCKED}.{BLOCKED}.75.9:18035/{random hex}.moe
- {BLOCKED}.{BLOCKED}.75.8:17182/{random hex}.moe
- Downloaded modules are saved as %Windows%\AppPatch\Custom\{random hex}.moe
- It adds the following mutex to avoid re-running certain malicious routines:
- Global\RunWord{random characters} ? for shellcode routine
- Global\{Characters based on C: volume serial number}CSS ? for registry creation routine
- Global\{Characters based on C: volume serial number}SetServiceX ? for "%System%\svchost.exe -k LocalService" process execution routine
- Global\{Characters based on C: volume serial number}SetService ? for "%System%\svchost.exe -k LocalService" process execution routine
- Global\{Characters based on C: volume serial number}AppService ? for "%System%\svchost.exe -k NetworkService" process execution routine
SOLUTION
Step 1
Before doing any scans, Windows 7, Windows 8, Windows 8.1, and Windows 10 users must disable System Restore to allow full scanning of their computers.
Step 2
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 3
Identify and terminate files detected as Backdoor.Win32.FUPORPLEX.C
- Windows Task Manager may not display all running processes. In this case, please use a third-party process viewer, preferably Process Explorer, to terminate the malware/grayware/spyware file. You may download the said tool here.
- If the detected file is displayed in either Windows Task Manager or Process Explorer but you cannot delete it, restart your computer in safe mode. To do this, refer to this link for the complete steps.
- If the detected file is not displayed in either Windows Task Manager or Process Explorer, continue doing the next steps.
Step 4
Delete this registry key
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_LOCAL_MACHINE\SYSTEM\{ControlSet001 or CurrentControlSet}\
- services\Ms{Characters based on C: volume serial number}App\Parameters
- services\Ms{Characters based on C: volume serial number}App\Parameters
- In HKEY_LOCAL_MACHINE\SYSTEM\{ControlSet001 or CurrentControlSet}\
- services\Ms{Characters based on C: volume serial number}App
- services\Ms{Characters based on C: volume serial number}App
- In HKEY_LOCAL_MACHINE\SOFTWARE\SoundResearch
Step 5
Delete this registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_LOCAL_MACHINE\SOFTWARE\SoundResearch
- UpdaterLastTimeChecked1 = 1
- UpdaterLastTimeChecked1 = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders
- %Program Files%\OTFDXCNEJDKCODPNIZZRXFWJIBKVCIHFNGXU\OTFDXCNEJDKCODPNIZZRXFWJIBKVCIHFNGXU\ = 1
- %Program Files%\OTFDXCNEJDKCODPNIZZRXFWJIBKVCIHFNGXU\OTFDXCNEJDKCODPNIZZRXFWJIBKVCIHFNGXU\ = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders
- %Program Files%\OTFDXCNEJDKCODPNIZZRXFWJIBKVCIHFNGXU\ = 1
- %Program Files%\OTFDXCNEJDKCODPNIZZRXFWJIBKVCIHFNGXU\ = 1
- In HKEY_LOCAL_MACHINE\SYSTEM\{ControlSet001 or CurrentControlSet}\services\Ms{Characters based on C: volume serial number}App\Parameters
- ServiceDll = %System%\Ms{Characters based on C: volume serial number}App.dll
- ServiceDll = %System%\Ms{Characters based on C: volume serial number}App.dll
- In HKEY_LOCAL_MACHINE\SYSTEM\{ControlSet001 or CurrentControlSet}\services\Ms{Characters based on C: volume serial number}App
- ImagePath = %System%\svchost.exe -k netsvcs
- ImagePath = %System%\svchost.exe -k netsvcs
- In HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows Defender
- DisableAntiSpyware = 1
- DisableAntiSpyware = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender
- DisableAntiSpyware = 1
- DisableAntiSpyware = 1
- In HKEY_CURRENT_USER\Software\Microsoft\Windows Script\Settings
- JITDebug = 0
- JITDebug = 0
Step 6
Search and delete this file
- %Windows%\AppPatch\Ke{6 random numbers}.xsl
- %Windows%\AppPatch\Ac{Characters based on C: volume serial number}.sdb
- %Windows%\AppPatch\Custom\{7 random characters}.tmp
- %System%\Ms{Characters based on C: volume serial number}App.dll
- %System%\drivers\dump_{random hex strings}.sys
- %Windows%\winupdate32.log if OS is x32
- %Windows%\winupdate64.log if OS is x64
Step 7
Search and delete these folders
- %System Root%\RECYCLER
- %Windows%\AppPatch
- %Windows%\AppPatch\Custom
- %Program Files%\OTFDXCNEJDKCODPNIZZRXFWJIBKVCIHFNGXU\OTFDXCNEJDKCODPNIZZRXFWJIBKVCIHFNGXU\
- %Program Files%\OTFDXCNEJDKCODPNIZZRXFWJIBKVCIHFNGXU\
Step 8
Restore this file from backup only Microsoft-related files will be restored. If this malware/grayware also deleted files related to programs that are not from Microsoft, please reinstall those programs on you computer again.
- if %Windows%\AppPatch\Acpsens.dll exists:
- restore %Windows%\sens.dll
- if %Windows%\AppPatch\Acpcscdll.dll exists:
- restore %Windows%\cscdll.dll
Step 9
Scan your computer with your Trend Micro product to delete files detected as Backdoor.Win32.FUPORPLEX.C. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check the following Trend Micro Support pages for more information:
Did this description help? Tell us how we did.


