ANDROIDOS_ROOTRAZR.A
Rooting Tool
Android OS


Threat Type: Hacking Tool
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
This hacking tool may be manually installed by a user.
TECHNICAL DETAILS
Arrival Details
This hacking tool may be manually installed by a user.
NOTES:
This malware is part of a tool used for rooting Android devices.
It exploits an Android vulnerability (CVE-2012-6422) to gain root privilege. It then proceeds to install busybox and su to /system/xbin/.
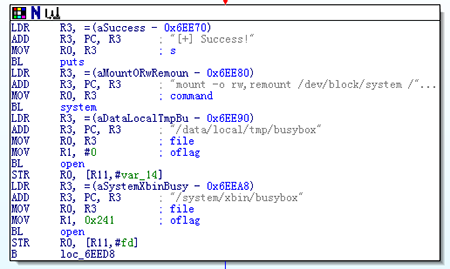
Figure 1. Installing busybox
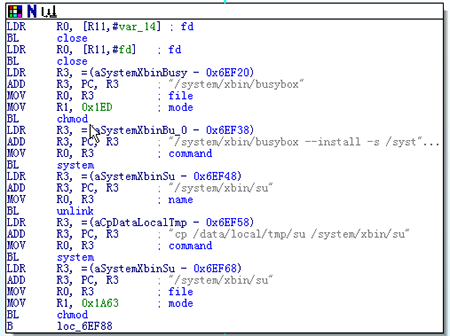
Figure 2. Installing su
Installation allows other apps on the affected device to gain root privilege by executing /syste/xbin/su.
While this can be used by the user to root their own devices, this can also be exploited by malicious users.
SOLUTION
Step 1
Scan your computer with your Trend Micro product to delete files detected as ANDROIDOS_ROOTRAZR.A. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Step 2
Remove unwanted apps on your Android mobile device
Did this description help? Tell us how we did.


