Rischi di Privacy
Unlocking the Power of Amazon Security Lake for Proactive Security
Security is a central challenge in modern application development and maintenance, requiring not just traditional practices but also a deep understanding of application architecture and data flow. While organizations now have access to rich data like logs and telemetry, the real challenge lies in translating this information into actionable insights. This article explores how leveraging those insights can help detect genuine security incidents and prevent their recurrence.
Introduction
It’s no secret that security is one of the main challenges of application development and modernization. It plays a main role not only in how we build our applications, but also in how we maintain them.
There are many ways to protect our applications, from the way we write our code to the way we deploy it. But all these different approaches meet the same challenge: How do we use data to identify real security incidents and, if they already occurred, how do we prevent them from happening again?
Achieving this in modern applications often goes beyond traditional security boundaries. Security practitioners must not only understand core security principles, but also how applications are built, how they function, and how data flows through them.
There is access to rich data including application logs, usage telemetry, and relationships between resources. However, the challenges lie not in collecting it, but in translating diverse data formats into a common language and surfacing actionable insights amid the noise of everyday application behavior.
This article explores how those insights can be used to detect real security incidents and prevent them from happening again.
What is Amazon Security Lake?
Amazon Security Lake is trying to solve these challenges by making fragmented security logs and data into a centralized data lake system for a better visibility, searching, investigation, and consolidation. It offers a way to collect, store and analyze data from different regions and sources, including AWS services such as Amazon EKS, AWS Security Hub, Amazon Route53, AWS WAF, and third-party sources such as SaaS providers and on-premises alternatives. This helps to identify security incidents quicker and to prevent them from happening again, providing security operations (SecOps) teams with one place where they can find all the relevant information needed to identify security incidents in the cloud infrastructure.
One of the biggest challenges in monitoring cloud application logs is normalizing the data into a unified schema based on Open Cybersecurity Schema Framework (OCSF), a vendor-agnostic framework allowing for analysis and correlation with a common language, often requiring complex parsing and data pipelining processes.
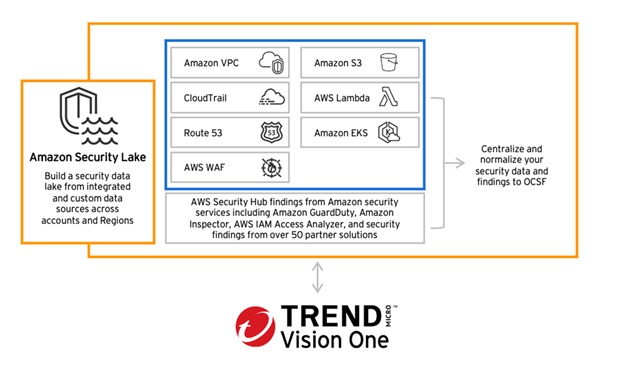
By adopting OCSF, Amazon Security Lake helps create a unified ecosystem where all security vendors can benefit from simplified integration and standardized data. With a common schema, partners can onboard data sources faster, reduce reliance on custom parsers, and enable smoother interoperability across tools. This consistency enhances collaboration, improves threat detection at scale, and allows analytics and machine learning to operate more efficiently. For vendors, OCSF means broader compatibility, faster development, and more actionable insights for customers.
This level of normalization and interoperability is one of the key reasons we are adopting this format, fully embracing Amazon Security Lake as a core integration within our
Trend Vision One™ AI-powered enterprise cybersecurity platform. It empowers us to deliver broader visibility, faster detection, and deeper insights by unifying diverse telemetry across the cloud and hybrid environments—driving more effective and proactive security outcomes for our customers.
How we can take advantage of this data
But how can we transform this from data points into actionable security alerts and incidents? This is where Trend Vision One comes in. The platform allows you to ingest the data from Amazon Security Lake and immediately benefit from hundreds of threat detection and correlation rules. These XDR detections are provided by Trend Micro global threat research; we continuously research, refine, and tune the detection models to help proactively identify suspicious and malicious activity in the cloud environment. Customers can also create their own detection models based on the Amazon Security Lake data.
Amazon Security Lake logs can also be correlated with Trend Micro™ Threat Intelligence Feed, enabling customers to sweep for indicators of compromise (IOCs) and leveraging our leading threat insights.
The Trend™ Research team continuously develops and refines detection models to help identity suspicious and malicious activities on those logs ingested from different sources. These are based on various research insights to understand—and counter—bad actor behavior around the globe. To help adapt and make things flexible for customers, we enable you to create your own detection models based on data from Amazon Security Lake logs.
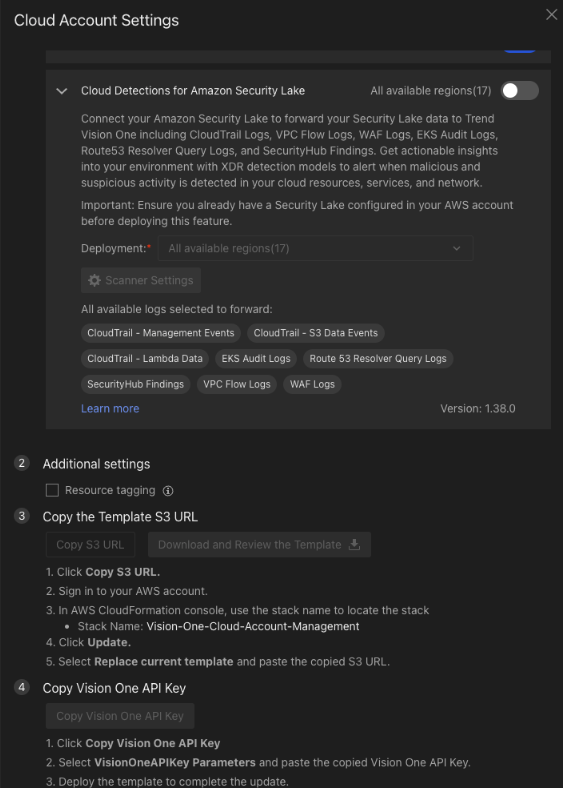
Trend Vision One also extends these capabilities, allowing customers to expand beyond cloud environments by enabling data ingestion from on-premises environments, such as your network, endpoints, and applications. This data is then correlated against that which you have in Amazon Security Lake. Trend Vision One complements this by providing efficient data analysis and threat detection, ensuring that your security operations are both effective and cost-efficient.
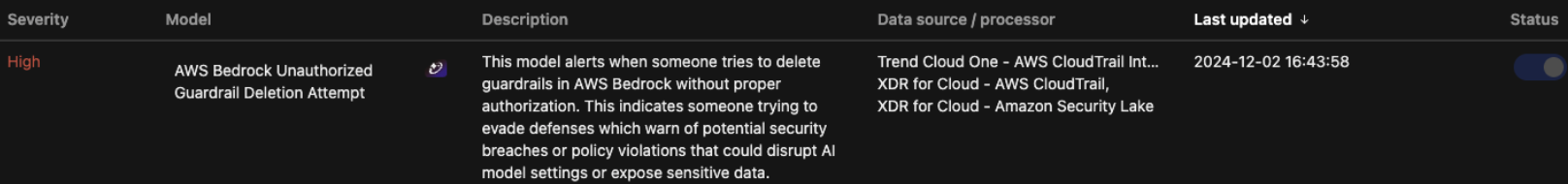
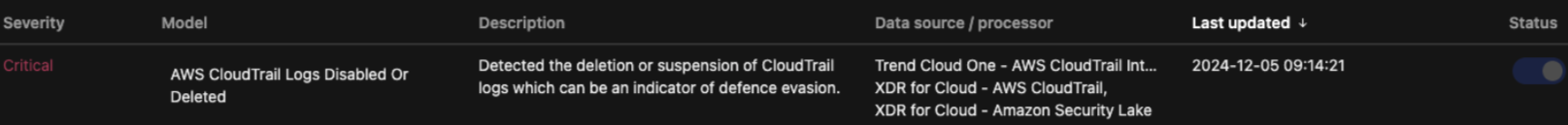
For example, a blog we recently published demonstrates how to detect suspicious activities on AI services on AWS using log ingestion within Trend Vision One logs—specifically, AWS CloudTrail data. This can be pulled from Amazon Security Lake with detection models applied for customers via our platform, quickly and seamlessly.
Some of these models include:
- Enumeration of services such as Amazon Bedrock and Amazon SageMaker
- Delete or modify AI guardrails without proper authorization
- Disable crucial services such as AWS Security Hub or AWS CloudTrail
- Data extraction and ransomware activity
These are just some examples of how you can take advantage of Amazon Security Lake data to identify security incidents and proactively prevent future occurences.
How to get started
Sign up for Trend Vision One either via AWS Marketplace or by booking a meeting with us. Once signed up, you can connect Trend Vision One to your active Amazon Security Lake via our cloud connector, then enable data ingestion and detection models to start analyzing threats right away. If you’re already in the console, go to Cloud Security, Cloud Accounts, and then Stack Update.
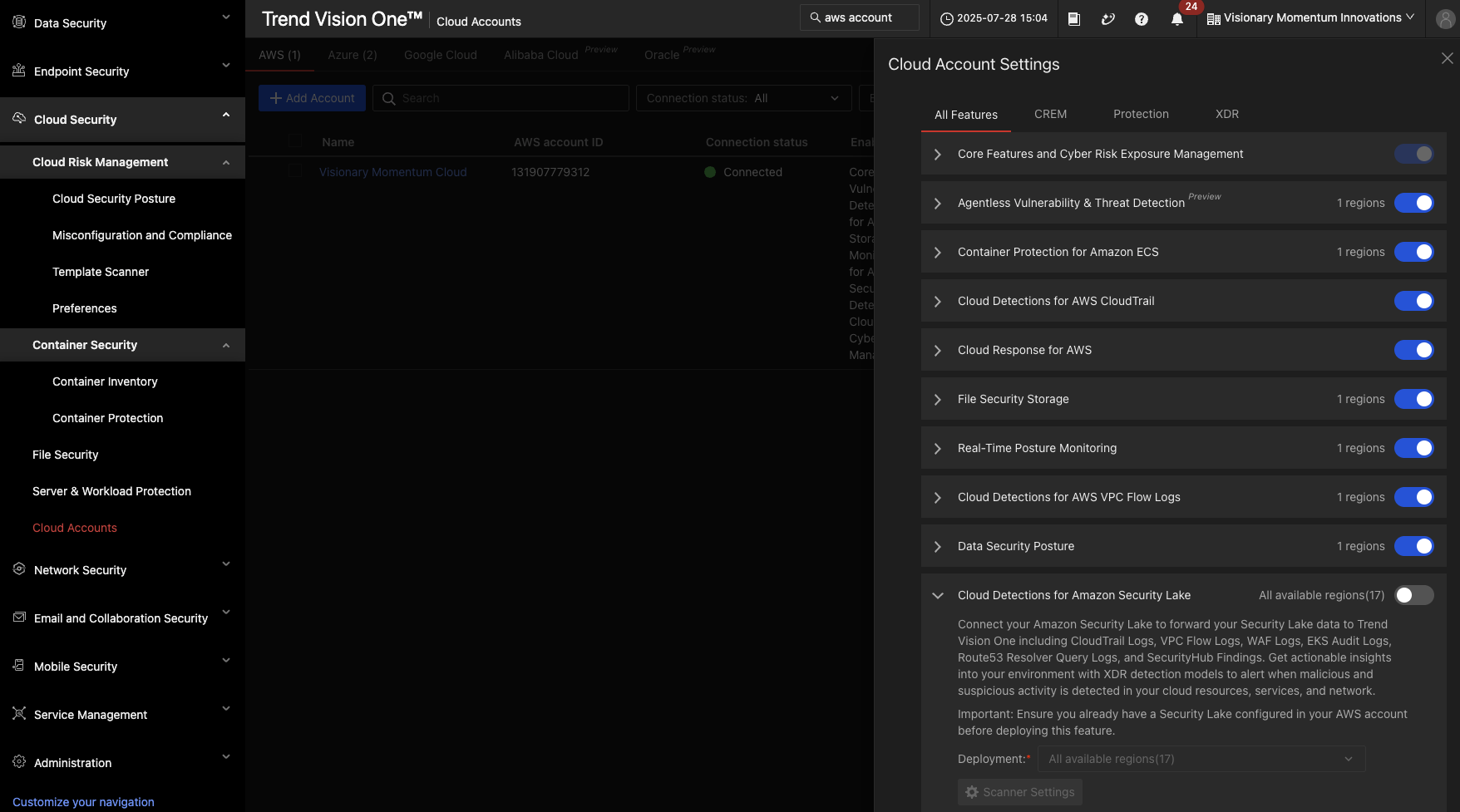
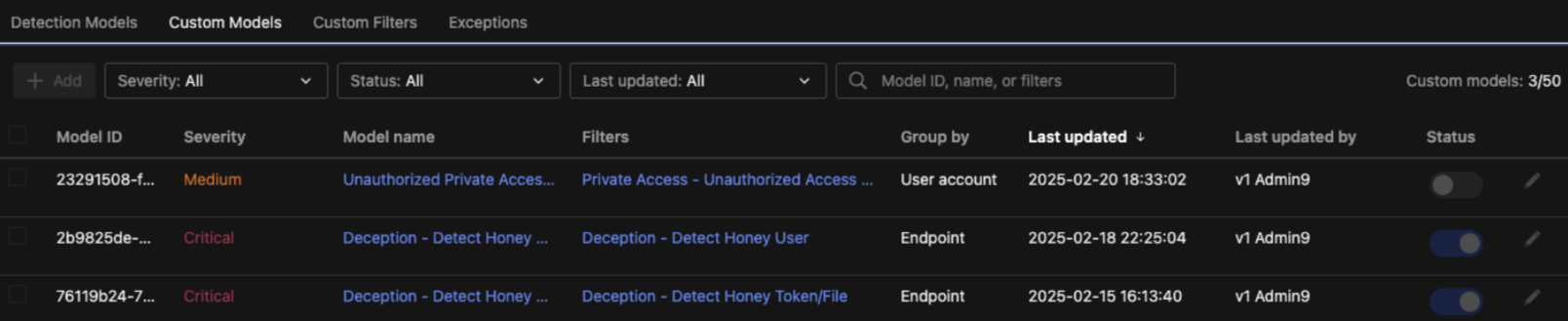
The integration between Trend Vision One and Amazon Security Lake allows companies to combine our security intelligence with the scalability and flexibility of our platform and the Amazon Data Lake. This integration brings many benefits, including proactive detection, automated orchestration, and intelligent data storage—complete with more than 180 detection models applied through detection model management.
For example, a financial services organization can use custom detection models to correlate and identify high-risk actions—such as modifications to AWS Identity and Access Management (IAM) policies or unusual access to Amazon Simple Storage Service (Amazon S3) audit logs—performed during sensitive trading hours. These patterns are specific to their operational context and help surface true threats without overwhelming the team with generic alerts.
Alternatively, a healthcare provider could detect unexpected access to HIPAA-sensitive Amazon S3 buckets during off-hours or by roles not typically involved in patient care workflows. By aligning detection with customer context and data access norms, security teams can flag potentially malicious behavior that would otherwise go unnoticed.
These custom models add critical customer context to the detection process—tailoring logic to match how applications, data, and users behave in each unique environment. When combined with the detection models developed by our global threat research teams, this hybrid approach enables more precise, contextualized, and scalable threat detection in the cloud.
Conclusion
Amazon Security Lake helps you with the critical challenge of fragmented security data by providing a centralization and normalization, that enhances visibility and streamlines data collection. When paired with platforms like Trend Vision One and our powerful integrated solutions, this data transforms into actionable insights, enabling security teams to not only identify incidents across cloud, on-premises, and hybrid environments but also prevent them from reoccurring.
By leveraging standardized schemas like OCSF, advanced detection models, and comprehensive telemetry correlation, you can stay ahead of threats, adapt to new risks, and build a truly proactive security posture. Ultimately, the integration of Amazon Security Lake empowers your teams to turn data into real threat intelligence. This integration not only enhances the detection of incidents across diverse environments; it’s also a common format for easier queries and sharing, offers centralized data for full visibility, and provides additional alerts with the context you need to face evolving threats—and stay ahead of adversaries.

