The 2024 survey highlights a growing maturity in threat-hunting methodologies, with a significant increase in organizations adopting formal processes.
This marks a shift towards a more standardized approach in cybersecurity strategies despite challenges such as skill shortages and tool limitations. Additionally, the survey reveals evolving practices in sourcing intelligence and an increase in outsourcing threat hunting, raising questions about the efficiency and alignment with organizational goals. This summary encapsulates the essential findings and trends, emphasizing the critical role of threat hunting in contemporary cybersecurity frameworks.
Participants
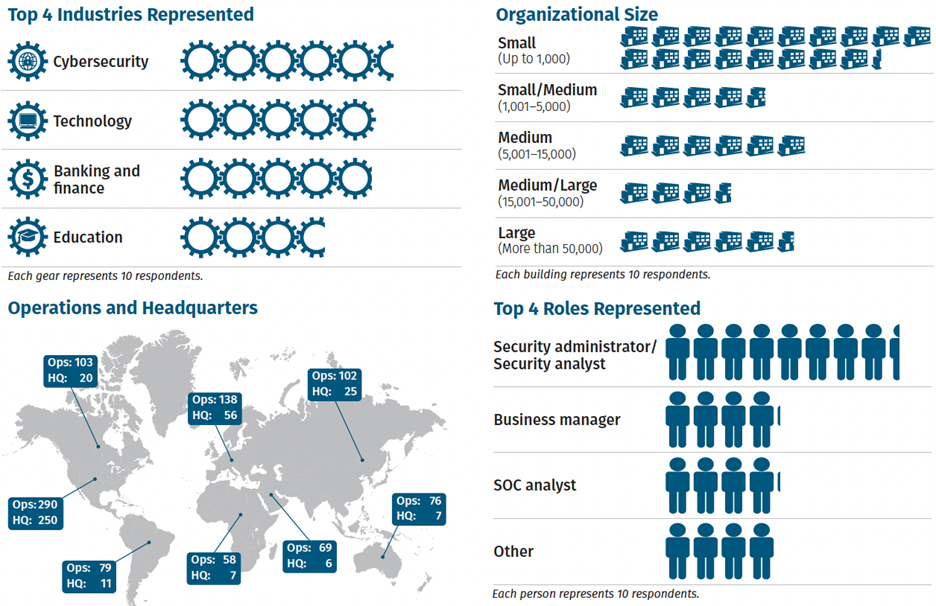
This year's survey attracted participants from a wide array of industries, with cybersecurity leading at 15% and 9% of respondents from the manufacturing sector, which has recently faced significant challenges from ransomware attacks. The survey participants varied in organization size, too, ranging from those working in small entities with less than 100 employees (24%) to large corporations with over 100,000 employees (9%).
The respondents play diverse roles within their organizations, highlighting the multidisciplinary nature of threat hunting. Twenty-two percent are security administrators or analysts, while 11% hold business manager positions, showcasing a balance between technical, financial, and personnel perspectives in threat-hunting practices.
However, the survey does note a geographical bias, with 65% of participants coming from organizations based in the United States, which could influence the findings related to staffing and organizational practices, though it's believed not to affect the technical aspects of threat hunting.
Significant findings and implications
The survey examines the dynamic landscape of cyber threats and the strategies deployed by threat hunters to identify and counteract these risks. Notably, it sheds light on the prevalent types of attacks encountered:
- Business email compromise (BEC): BEC emerges as the foremost concern, with approximately 68% of respondents reporting its detection. BEC involves malicious actors infiltrating legitimate email accounts to coerce individuals into transferring funds through social engineering tactics.
- Ransomware: Following closely behind is ransomware, detected by 64% of participants. Ransomware operations encrypt data and demand payment for decryption, constituting a significant threat in the cybersecurity landscape.
- Tactics, techniques, and procedures (TTPs): The survey found that TTPS are employed in different attack scenarios. In ransomware incidents, threat actors often deploy custom malware, target specific data for exfiltration, utilize off-the-shelf tools like Cobalt Strike, attempt to delete traces, and sometimes resort to physical intrusion into target companies.
Evolving threat-hunting practices
SANS also found that organizations have significantly evolved their threat-hunting practices, with changes in methodologies occurring as needed, monthly, quarterly, or annually.
Outsourced threat hunting is now used by 37% of organizations, and over half have adopted clearly defined methodologies for threat hunting, marking a notable advancement.
Additionally, 64% of organizations formally evaluate the effectiveness of their threat-hunting efforts, showing a decrease in those without formal methodologies from 7% to 2%. The selection of methods is increasingly influenced by available human resources, recognized by 47% of organizations.
The chief information security officer (CISO) plays a key role in developing threat-hunting methodologies, with significant involvement in 40% of cases.
Benefits of better threat-hunting efforts
Significant benefits from threat hunting include improved attack surface and endpoint security, more accurate detections with fewer false positives, and reduced remediation resources.
About 30% of organizations use vendor information as supplemental threat intelligence, with 14% depending solely on it. Incident response teams' involvement in developing threat-hunting methodologies rose to 33% in 2024, indicating better integration within security functions.
Challenges such as data quality and standardization issues are increasing, underscoring the complexities of managing expanding cybersecurity data.
Final thoughts
The SANS 2024 Threat Hunting Survey highlights the cybersecurity industry's evolution and focuses on improving cyber defense capabilities. Organizations aim to enhance threat hunting with better contextual awareness and data tools, with 51% looking to improve response to nuanced threats.
Nearly half (47%) plan to implement AI and ML to tackle the increasing complexity and volume of threats. There's a significant planned investment in both staff and tools, with some organizations intending to increase their investment by over 10% or even 25% in the next 24 months, emphasizing threat hunting's strategic importance.
However, a small minority anticipate reducing their investment, hinting at a potential shift in security strategy.

